When I started my home lab, I used a Raspberry Pi 4 that functioned as a router/firewall, and I was pretty happy with it. Then, I needed something solid and cost-effective. There were multiple options like VyOS, PfSense, UniFi, etc, but MikroTik, specifically the hAP ax2, stood out for me. I've been using this for almost a year now, and I absolutely love it. It works as a switch, and firewall and runs my WireGuard VPN, and it has never let me down even once.
Why Palo Alto?
Fast forward to today, I started adding more and more devices to the lab, so I was looking for an upgrade. After debating between FortiGate and Palo Alto, I finally settled on buying a Palo Alto PA-440 firewall.

But I would say the main reason behind this decision is that I write a lot of content on Palo Alto, and not having a dedicated device was such a pain. Every time I wanted to write a post, I had to start the lab, and try things out, and not having licenses was preventing me from trying new features and sharing them via a post. Now, with a dedicated unit and licenses, it's so much easier to share my findings.
PA-440 Lab Unit
The MSRP of the PA-440 with licenses is quite expensive, but I purchased the lab unit with a lab license bundle. My understanding is that this unit is not meant for production use, it's for lab purposes, but I believe you still need a business address and name. Palo Alto may not ship the unit to residential addresses. I'm in the UK, and it cost me just under £800 for the hardware and one year of licenses (Lab bundle). I need to renew my license each year. Here are the SKUs
PAN-PA-440-LAB
PAN-PA-440-BND-LAB4PA-440 Specs
I wasn’t looking for a big, beefy firewall, I just needed something that could handle 1Gb/s with threat prevention turned on. The PA-440 seemed like a better option. Here are some of the specs
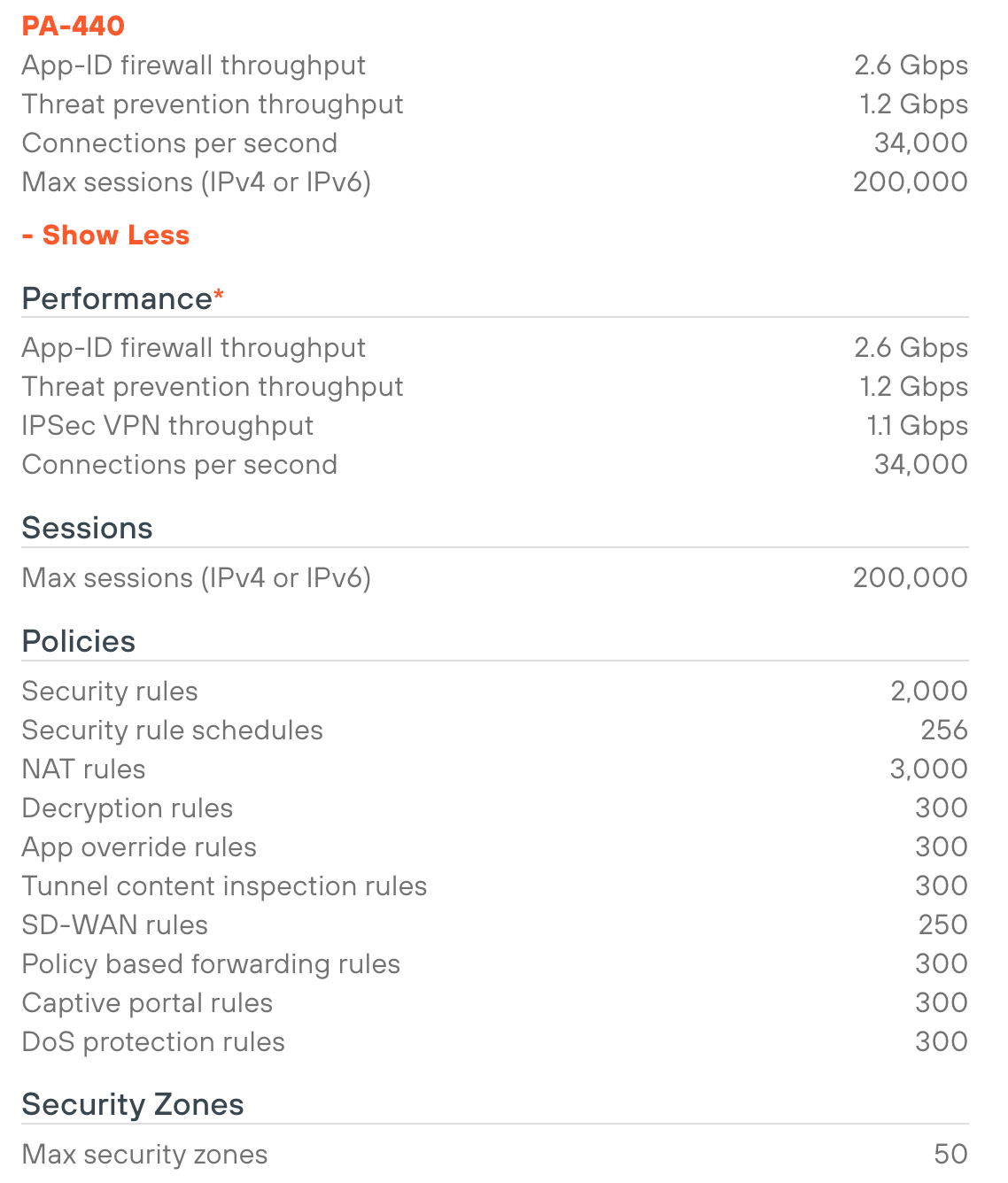
The firewall is built very solidly and weighs just over 2 kilograms. It's a fanless design and comes with a massive heat sink on top. The PA-440 features four CPU cores, one of which is dedicated to the management plane. On the front, it has eight 1 Gb/s copper RJ45 ports and one dedicated management port.
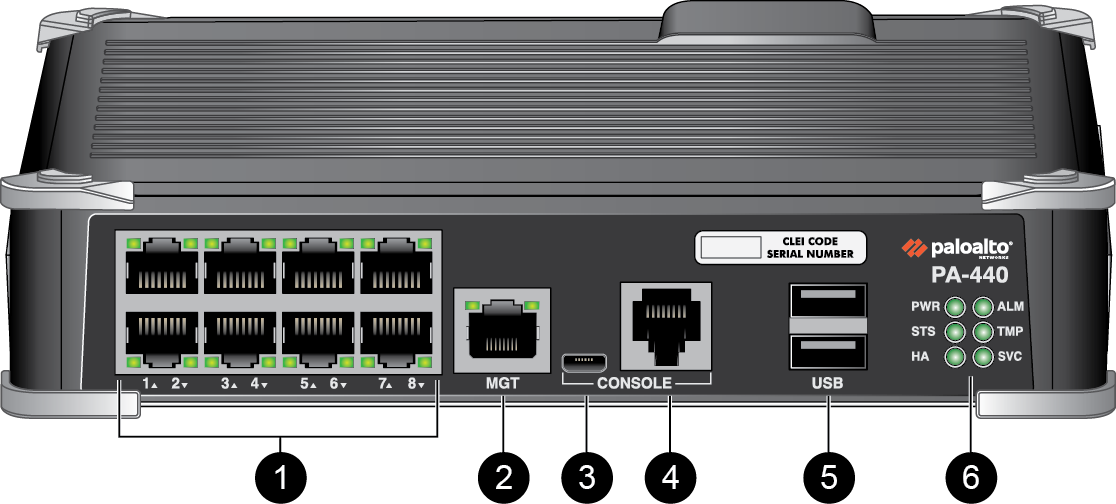
On the back, it has dual power ports, but it only comes with one power cord in the box, though you have the option to buy an additional cord.
My Homelab Network Setup
Prior to adding the firewall, I had a very simple network and was using the router from my ISP for WiFi. But as soon as I put the ISP router into modem mode, it turns off the WiFi. For the time being, I'm using a TP-Link router in AP mode for WiFi. I've also had an old Cisco AP lying around, so I put that in my kitchen to ensure full coverage. However, it's not as good an experience compared to UniFi, for example. I'm planning to add UniFi APs in the near future.
Anyway, now, I have a simple network with two LAN subnets, one is for general use, such as phones, laptops, TVs, or any other normal device. I have another subnet where I run all my home-lab devices like DNS servers, EVE-NG, Linux workstations, etc and of course, I have Internet access. I put my ISP’s router into modem mode, so it just transparently forwards the packets to my Palo Alto firewall, and the public IP is on the Palo Alto. The default gateways for the two LAN subnets are also on the Palo Alto. This way, I can route between the LAN subnets and then inspect traffic going out to the Internet.
The initial setup was straightforward, the firewall came with PAN-OS 10.2.7-h8, and I plan to upgrade to 10.2.9-h1 at some point. I had to create a Palo Alto portal account to register the device and activate the licenses. At the moment, I turned on all the default security profiles (URL Filtering, Anti-Spyware, etc.)
As I mentioned before, I was using WireGuard as my remote access VPN, which worked very well. But now that I have the Palo Alto, I just configured GlobalProtect VPN but am still keeping WireGuard just in case.
Closing Thoughts
So far, I'm very happy with my purchase. I already wrote a blog post on using Threat Signature Indicators to manage App-ID changes, which wouldn't be possible without the licenses as I wouldn’t get any application updates. You can expect to see more Palo Alto content now.
If you are looking for anything specific, please let me know in the comments, and I will try to cover it.





