If you are looking for an MFA solution for Cisco AnyConnect then there is a good chance that you have heard of Duo and Azure AD. In this blog post, I will guide you through the configuration steps required to set up Azure MFA with Cisco AnyConnect. Having Cisco ISE is optional for this to work.
Scenario
- You want to authenticate the AnyConnect users against Azure SSO/SAML to enforce MFA.
- Authorization should happen against Cisco ISE to provide role-based access using SGT tags << optional
Assumptions
- You already have a working ASA AnyConnect setup
- Authentication and authorization works with ISE
- Users and groups are already synced with Azure AD
- Cisco ISE is configured with Authorization policies for each AD group.
- ISE advertises SGT mappings to ASA via SXP
- ACLs are configured on ASA with SGs
- ASA running 9.8 or later code, and AnyConnect clients will be 4.6+
Adding Cisco AnyConnect from the gallery
To configure the integration of Cisco AnyConnect into Azure AD, you need to add Cisco AnyConnect from the gallery to your list of managed SaaS apps.
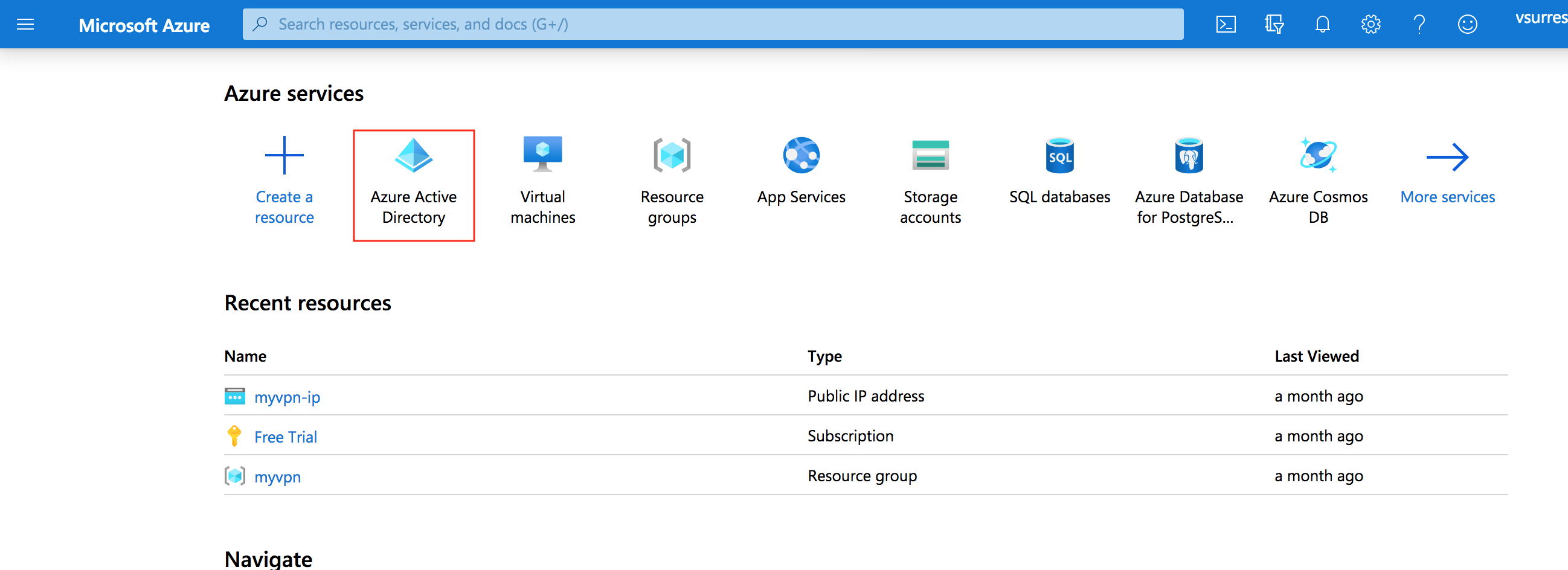
- Sign in to the Azure portal
- On the left navigation pane, select the Azure Active Directory service.
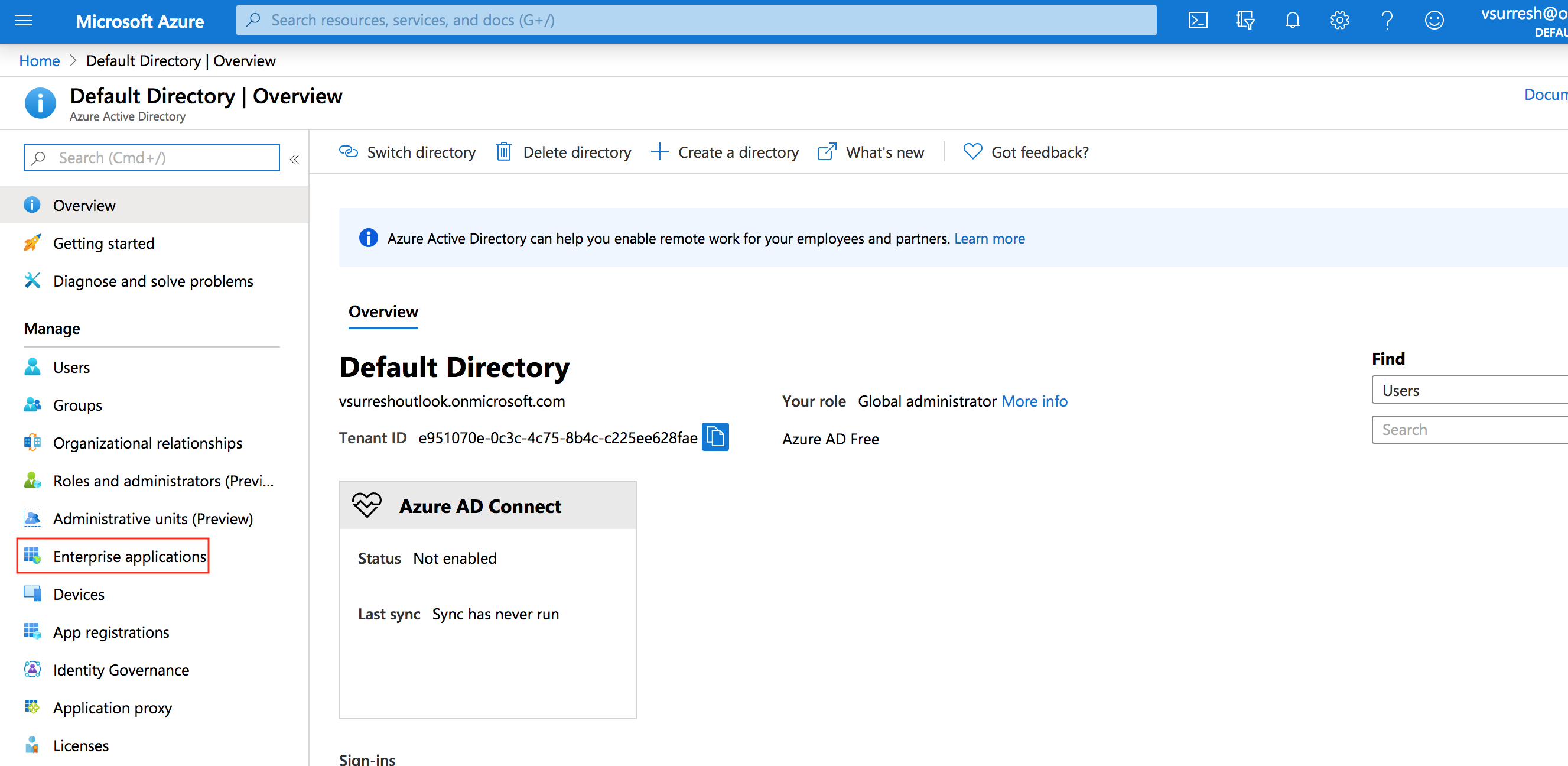
- Navigate to Enterprise Applications and then select All Applications.
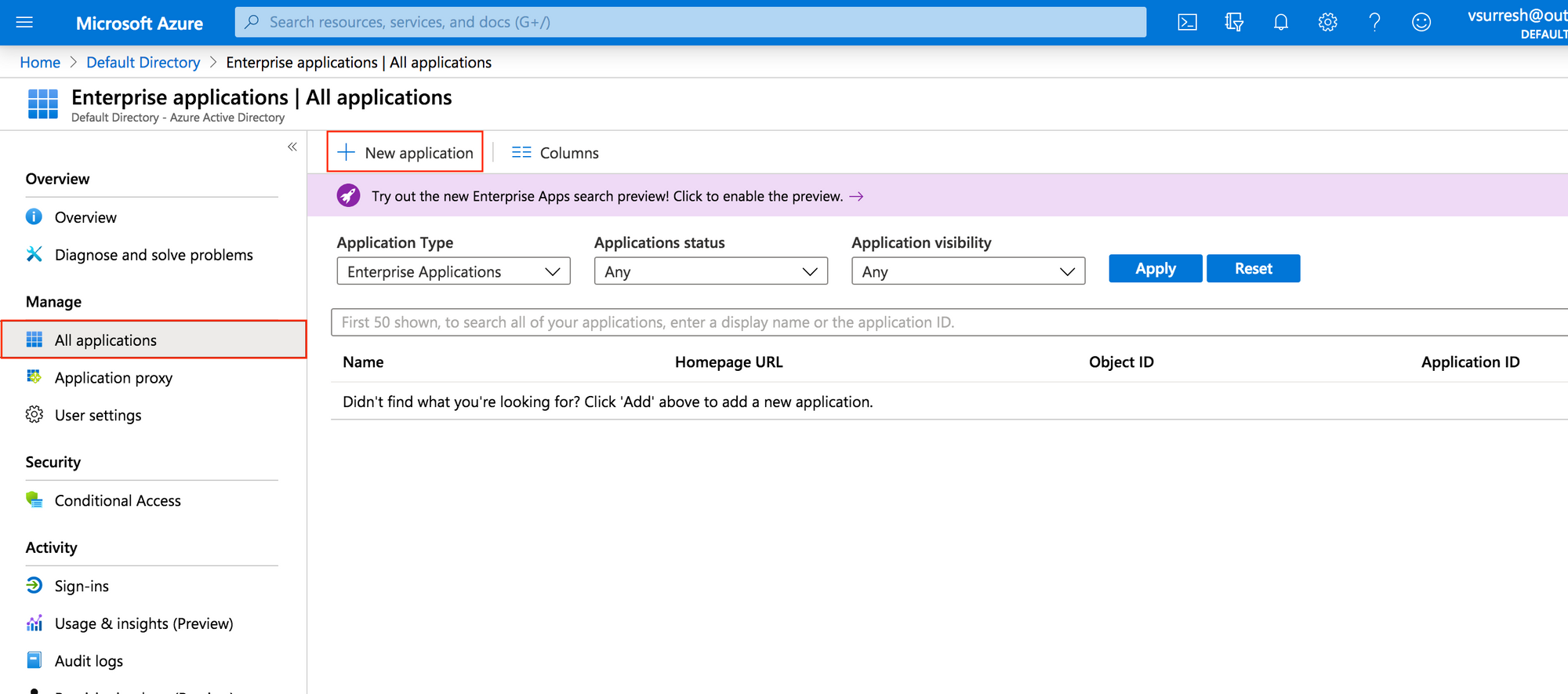
- Select New Application
- type Cisco AnyConnect in the search box.
- Select Cisco AnyConnect from results
Configure Azure AD SSO
Configure Azure AD SSO
-
Go to AnyConnect application and then select Set up single sign on
-
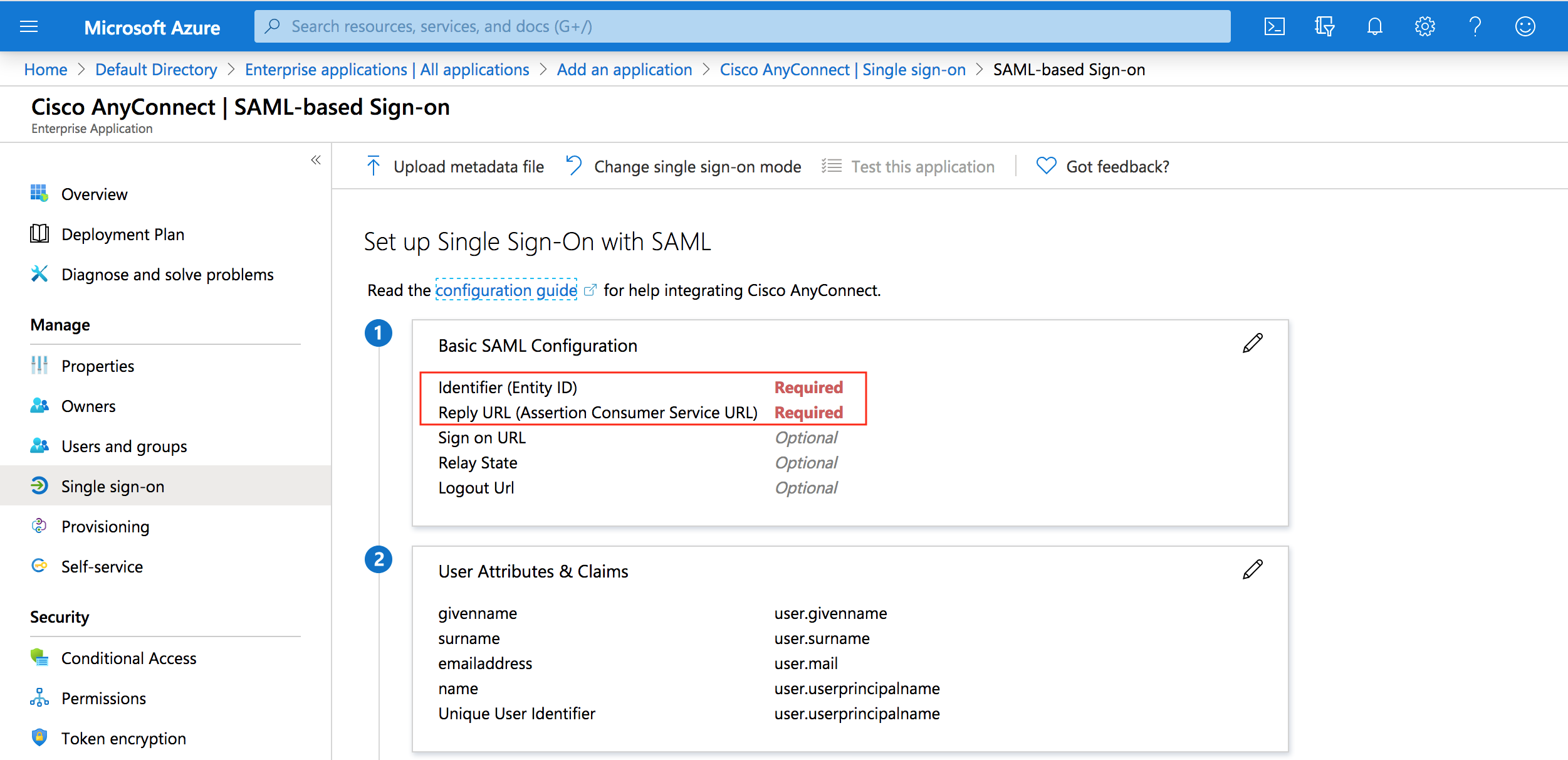
Set up single sign-on with SAML page, enter the values for the following fields:
In the Identifier text box, type Cisco ASA RA VPN "Tunnel group" name
In the Reply URL text box, type Cisco ASA RA VPN "Tunnel group" name
-
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and select Download to download the certificate file and save it on your computer.
-
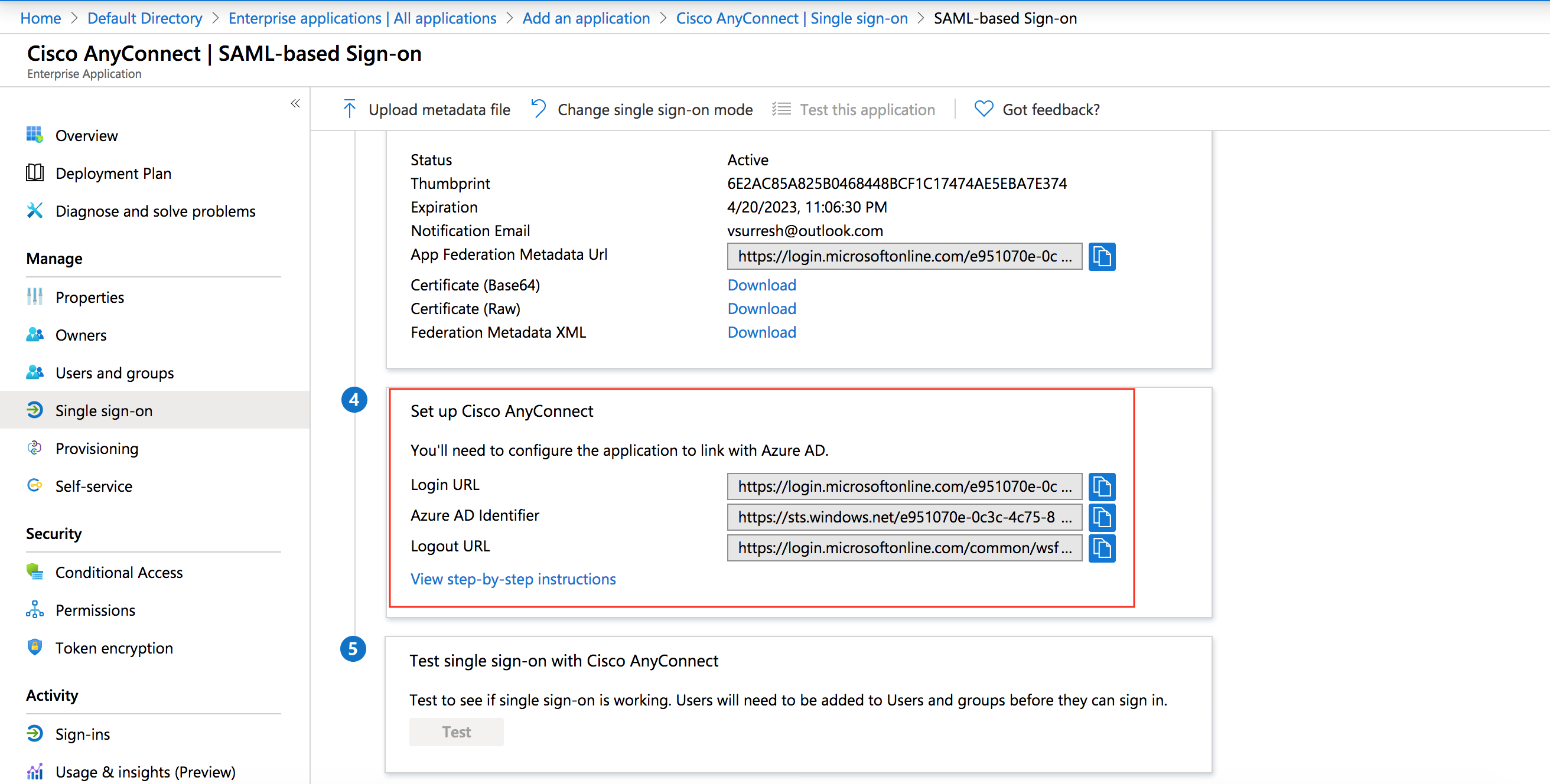
On the Set up Cisco AnyConnect section, copy all three URLs.
Cisco ASA configuration
Assume the tunnel-group name is "company-vpn" , VPN url is "vpn.mycompany.com" and the trust-point of the identity certificate is "my-public-cert"
VPN Identity Certificate - Usually a wild card certificate for *.mycompany.com that you buy from a CA.
Create a trust-point and import the SAML certificate you downloaded in the previous step.
crypto ca trustpoint Azure-saml
revocation-check none
no id-usage
no ca-check
enrollment terminal
crypto ca authenticate Azure-saml
-----BEGIN CERTIFICATE-----
***certificate goes here***
-----END CERTIFICATE-----
quitConfigure SAML IdP
webvpn
enable OUTSIDE
anyconnect-essentials
anyconnect image disk0:/anyconnect-win-4.5.04029-webdeploy-k9.pkg 1
anyconnect image disk0:/anyconnect-linux64-4.5.04029-webdeploy-k9.pkg 5
anyconnect image disk0:/anyconnect-macos-4.5.04029-webdeploy-k9.pkg 6
anyconnect enable
tunnel-group-list enable
cache
disable
error-recovery disable
saml idp https://sts.windows.net/fgg54-4fdd-ac56-3ad156472a14/
url sign-in https://login.microsoftonline.com/3d-ac563/saml2
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0
base-url https://vpn.mycompany.com
trustpoint idp Azure-saml
trustpoint sp my-public-cert
no signature
force re-authenticationFor Service Provider (SP) certificate you can use the identity or wild card certificate associated with your VPN url (vpn.mycompany.com) This certificate is usually issued by public CA.
Apply SAML authentication to the VPN tunnel group
tunnel-group mycompany-vpn webvpn-attributes
authentication saml
group-alias mycompany-vpn enable
saml identity-provider https://sts.windows.net/fgg54-4fdd-ac56-3ad156472a14/Now users should be able to login to AnyConnect via SSO. But we want to make sure that ISE is performing the Authorization.
To achieve this we need to use the authorization feature on the ASA. This will enable ASA to authenticate users against Azure AD and authorize against ISE.
When the authorization request comes to ISE, it tries to process a full authentication + authorization. There is no password (because Azure handled it already) in the packet so the authentication fails.
To get around the issue we need to set the ISE authentication source to Internal Users, and told ISE to continue on both Auth fail and user not found. This allows ISE to process just authorization.
ASA configuration
tunnel-group mycompany-vpn general-attributes
authorization-server-group ISECisco ISE configuration
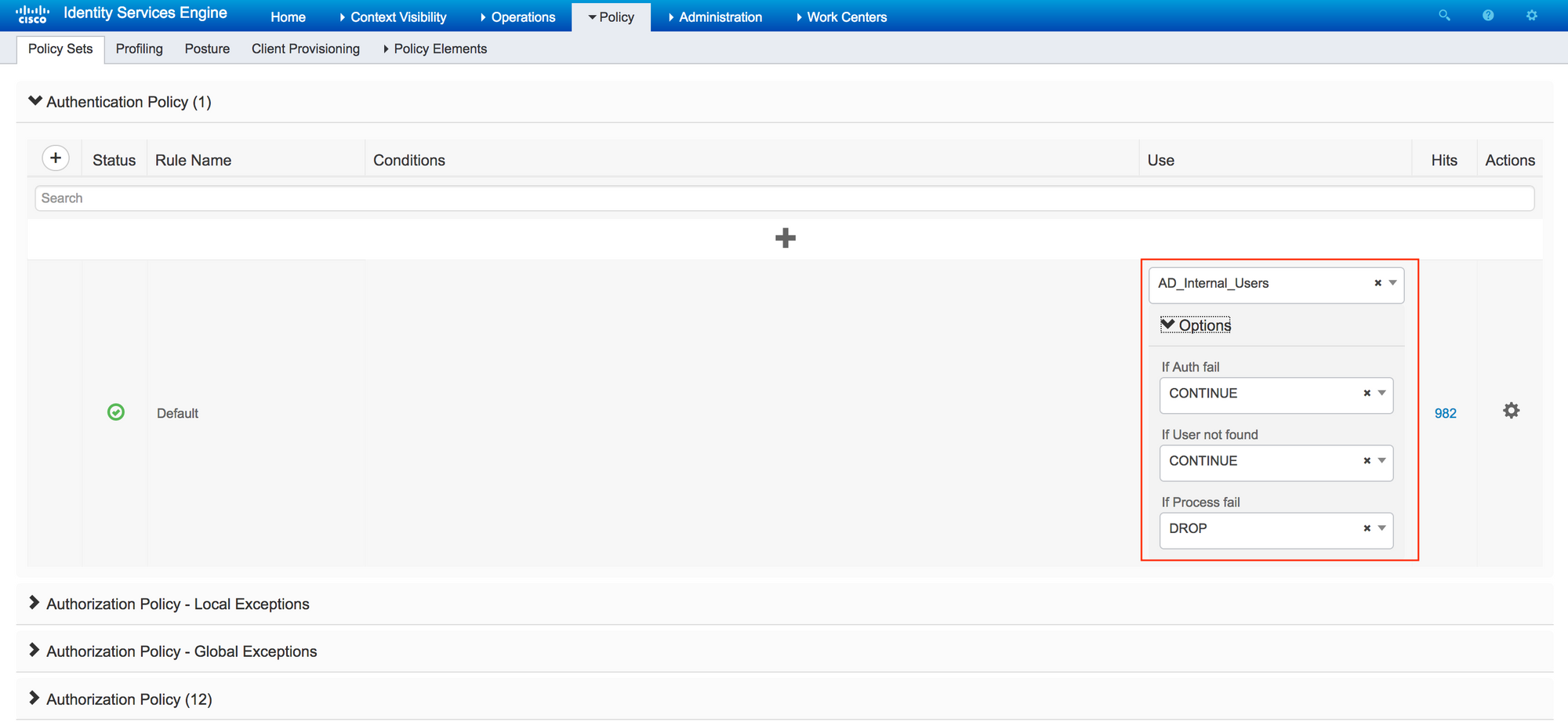
This would allow ISE to process the authorization and everything should work correctly. You can enforce MFA using Azure "Conditional Access".
Reference