This blog post focuses on how to configure Logging/Syslog on the Cisco ASA firewalls. Having relevant logs sent out to the appropriate location is one of the crucial parts of the firewall operation. ASA can send logs to various locations such as local buffer, ASDM, terminal-sessions and external syslog servers.
You only need 5 or 6 lines of commands to enable logging and send the logs to relevant locations. Let's have a look at the required commands step-by-step.
Syslog messages are structured as follows:
%ASA Severity_Level Syslog_ID: Log_Message
- Begin with a percentage sign (%)
- Keyword 'ASA'
- Severity level 1-7
- A unique six-digit syslog-id
- Log message
!! Syslog example
%ASA-4-411004: Interface GigabitEthernet0/6, changed state to administratively downAlert - Severity 1
Critical - Severity 2
Error - Severity 3
Warning - Severity 4
Notification - Severity 5
Informational - Severity 6
Debugging - Severity 7Enable Logging
As you can see below, logging is disabled by default so, the first thing you need to do is enable it by running logging enablecommand.
asa-log# show logging
Syslog logging: disabled
Facility: 20
Timestamp logging: disabled
Hide Username logging: enabled
Standby logging: disabled
Debug-trace logging: disabled
Console logging: disabled
Monitor logging: disabled
Buffer logging: disabled
Trap logging: disabled
Permit-hostdown logging: disabled
History logging: disabled
Device ID: disabled
Mail logging: disabled
ASDM logging: disabledlogging enableInternal Logging
Enabling logging doesn't mean you can view the logs on the CLI or ASDM because ASA only generates messages but does not save them to a location from which you can view them, for that you need to specify which locations the ASA should send the logs to.
Let's say I want to view logs with severity level warnings and lower on the CLI and informational and lower on the ASDM. Run the following commands to send syslogs to the internal buffer and to the ASDM. Default internal buffer size is 4KB, you can increase the size by using the logging buffer-size command. Once you applied the configuration, you can view the logs from both the CLI (by issuing show logging) and ASDM (via live logs)
logging buffered warnings
logging asdm informational
logging buffer-size 102400show logging
%ASA-4-411004: Interface OUTSIDE, changed state to administratively down
%ASA-4-411004: Interface GigabitEthernet0/6, changed state to administratively down
%ASA-4-411003: Interface GigabitEthernet0/6, changed state to administratively up
%ASA-4-411003: Interface OUTSIDE, changed state to administratively up
%ASA-3-106014: Deny inbound icmp src OUTSIDE:8.8.8.8 dst INSIDE:192.168.1.10 (type 0, code 0)
%ASA-3-106014: Deny inbound icmp src OUTSIDE:8.8.8.8 dst INSIDE:192.168.1.10 (type 0, code 0)
%ASA-2-106001: Inbound TCP connection denied from 13.225.39.47/443 to 192.168.1.10/59474 flags ACK on interface OUTSIDE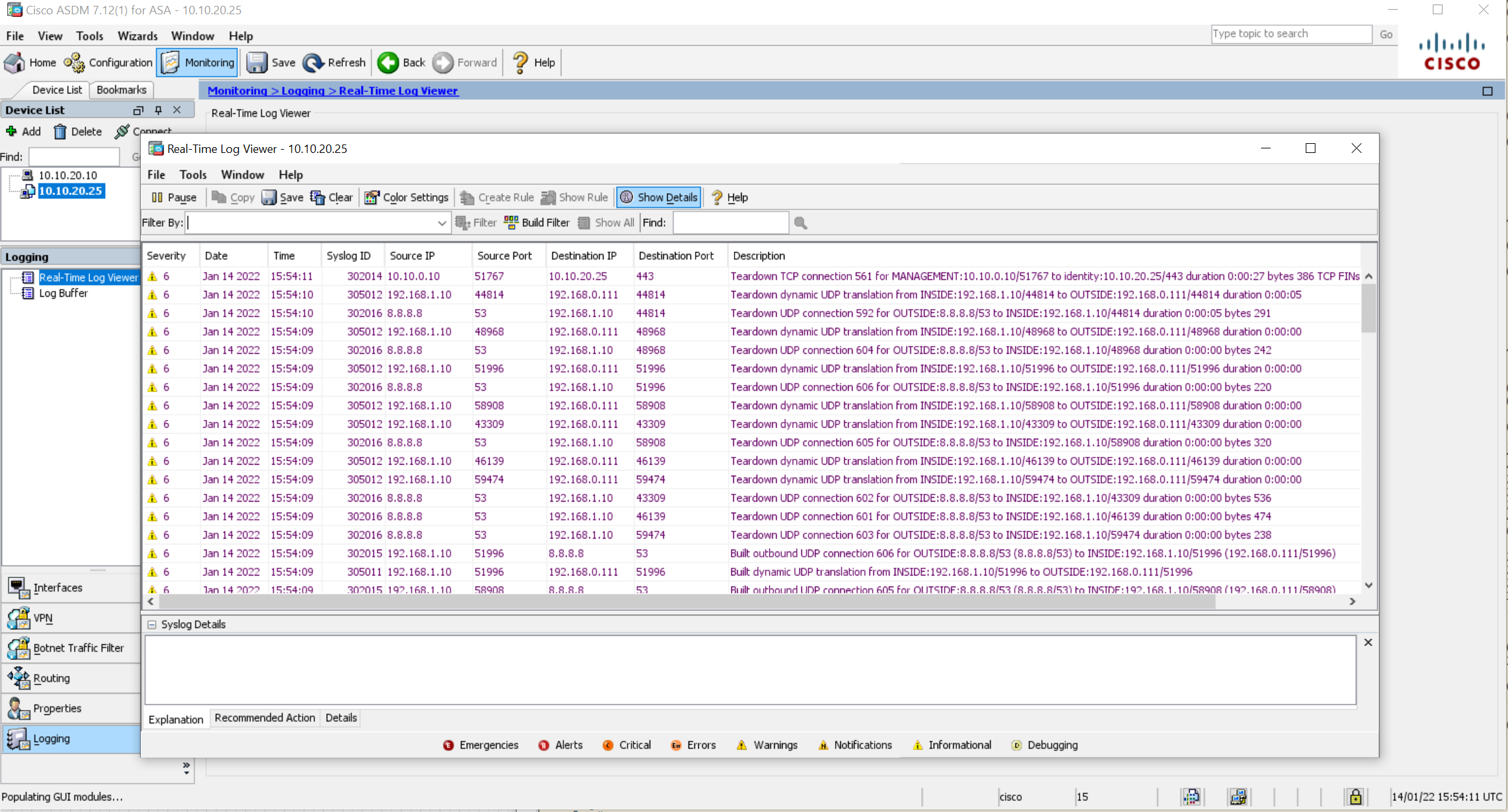
As you can see above, the logs are appearing both on the CLI and ASDM.
External Syslog Server
Internal buffer and ASDM have a limited amount of storage so, the logs will be overridden very quickly. To view the historic logs and to keep the logs for audit purposes, you can send them to an external syslog server. By default, ASA sends syslog on UDP/514 port, but you can change it if you wish. I'm using Kiwi syslog Server for this example which can be downloaded from their website. The IP address of the syslog server is 10.10.0.10
logging permit-hostdown Please take precautions before starting using TCPYou need to specify the IP address of the syslog server and on which level syslog messages should be logged. The following two commands instruct ASA to log messages on the informational level and lower send send them to 10.10.0.10 (our syslog server)
logging trap informational
logging host MANAGEMENT 10.10.0.10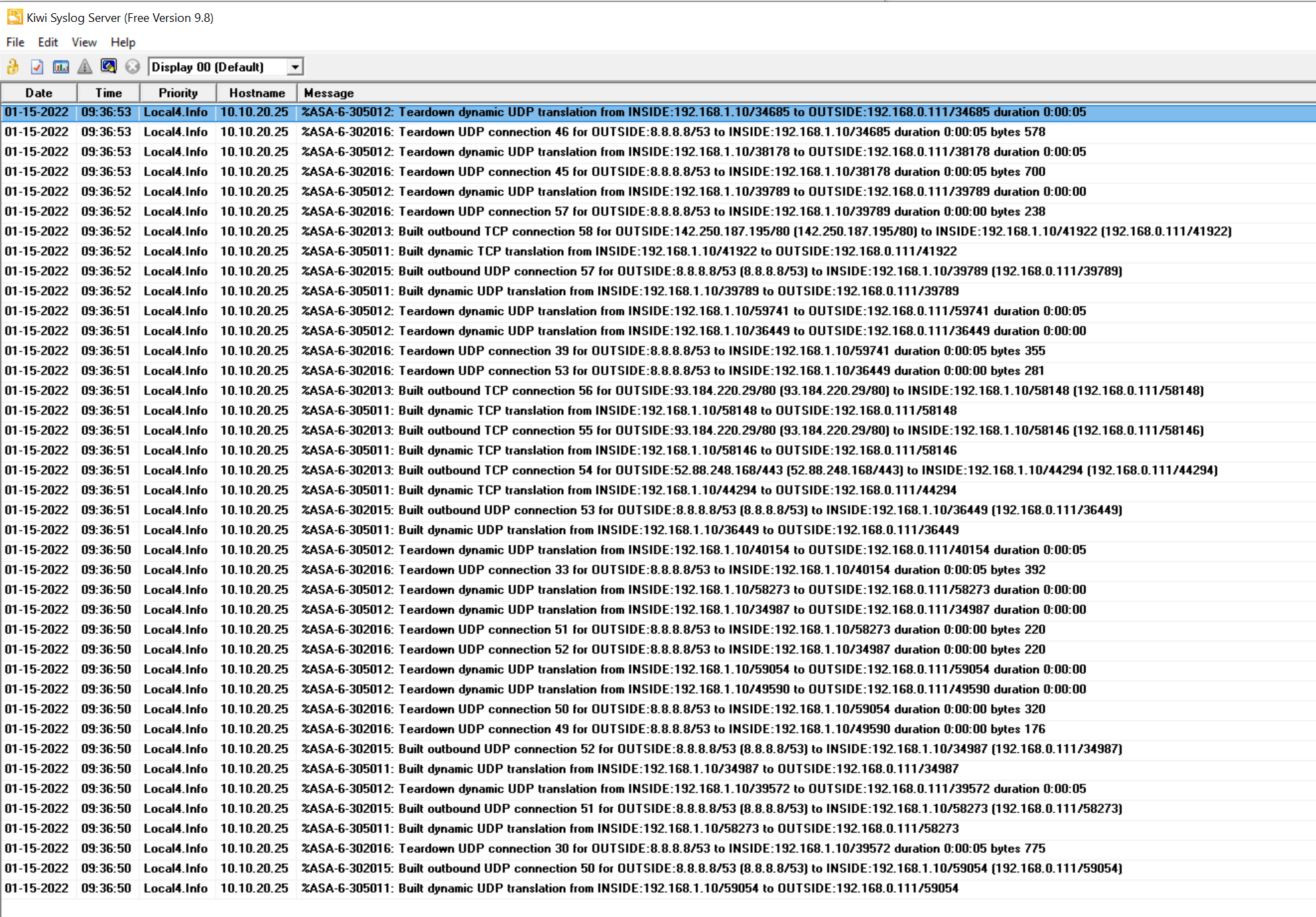
As you can see above, the syslog server is receiving the logs from the ASA.
Omit unwanted logs
If you have a large volume of traffic traverses the firewall, you may want to disable specific logs being generated and sent out. You can use no logging message syslog_id command to omit unwanted logs. For example, let's say you don't want to log ICMP built and teardown messages (302020 and 302021), you can do so by using the following commands.
no logging message 302021
no logging message 302020This is will result in the specific log messages are not being logged to 'all' the locations. You won't be able to instruct ASA to omit the logs in one location and not in the other locations using this method.
Message Class
The Syslog Message Class categorizes the syslog messages by type, for example, the vpn class denotes IKE and IPSec functions of the ASA. The following are the currently available Message Classes on the ASA.
snmp class start with the syslog-id of 212. auth User Authentication
bridge Transparent Firewall
ca PKI Certificate Authority
citrix Citrix Client
config Command Interface
csd Secure Desktop
cts Cisco TrustSec
dap Dynamic Access Policy
eigrp EIGRP Routing
email Email Proxy
ha Failover
ids Intrusion Detection System
ip IP Stack
ipaa IP Address Assignment
np Network Processor
ospf OSPF Routing
rip RIP Routing
rm Resource Manager
rule-engine Rule Engine
session User Session
snmp SNMP
ssl SSL stack
svc SSL VPN Client
sys System
tag-switching Service Tag Switching
vm VLAN Mapping
vpdn PPTP and L2TP session
vpn IKE and IPSec
vpnc VPN client
vpnfo VPN Failover
vpnlb VPN Load Balancing
webfo WebVPN Failover
webvpn WebVPN clientLet's say you only want to see the message class config on the internal buffer and nothing else. You can also specify a severity threshold within the message class configuration to limit the number of messages being received.
no logging buffered
logging class config buffered informational show logging
%ASA-5-111008: User 'enable_15' executed the 'clear logging buffer' command.
%ASA-5-111010: User 'enable_15', running 'CLI' from IP 10.10.0.10, executed 'clear logging buffer'
%ASA-5-111001: Begin configuration: 10.10.0.10 writing to memory
%ASA-5-111004: 10.10.0.10 end configuration: OK
%ASA-5-111008: User 'enable_15' executed the 'write' command.
%ASA-5-111010: User 'enable_15', running 'CLI' from IP 10.10.0.10, executed 'write'
%ASA-5-111008: User 'enable_15' executed the 'ping 8.8.8.8' command.
%ASA-5-111010: User 'enable_15', running 'CLI' from IP 10.10.0.10, executed 'ping 8.8.8.8'As you can see above, we are no longer seeing other logs such as VPN or traffic.
Message List
You can use the Message List functionality to group only interested logs and send them to your desired destination. This comes very handily if you only want to send very specific logs to a destination. Let's say you only want to send TCP built (302013) and ICMP built (302020) messages and nothing else to the internal buffer.
no logging class config buffered informational
logging list TCP_ICMP message 302013
logging list TCP_ICMP message 302020
logging buffered TCP_ICMPshow logging
%ASA-6-302020: Built outbound ICMP connection for faddr 1.1.1.1/0 gaddr 192.168.0.111/1706 laddr 192.168.1.10/1706 type 8 code 0
%ASA-6-302020: Built outbound ICMP connection for faddr 1.1.1.1/0 gaddr 192.168.0.111/1706 laddr 192.168.1.10/1706 type 8 code 0
%ASA-6-302020: Built outbound ICMP connection for faddr 1.1.1.1/0 gaddr 192.168.0.111/1706 laddr 192.168.1.10/1706 type 8 code 0
%ASA-6-302013: Built outbound TCP connection 933 for OUTSIDE:172.217.169.68/443 (172.217.169.68/443) to INSIDE:192.168.1.10/37610 (192.168.0.111/37610)
%ASA-6-302013: Built outbound TCP connection 935 for OUTSIDE:23.40.43.75/80 (23.40.43.75/80) to INSIDE:192.168.1.10/47780 (192.168.0.111/47780)
%ASA-6-302013: Built outbound TCP connection 936 for OUTSIDE:23.40.43.75/80 (23.40.43.75/80) to INSIDE:192.168.1.10/47782 (192.168.0.111/47782)
%ASA-6-302013: Built outbound TCP connection 937 for OUTSIDE:23.40.43.75/443 (23.40.43.75/443) to INSIDE:192.168.1.10/54396 (192.168.0.111/54396)Send Debug Messages to a Syslog Server
When you enable debug during troubleshooting, it can produce a huge amount of information on the CLI which can be overwhelming. Optionally, you have the option to re-direct all the debug messages to your desired destination similar to any other syslog message (buffer, ASDM or external syslog server)
For this example, I'm going to enable 'DNS' debugging.
debug dns
debug dns enabled at level 1.
asa-log# ping google.com
DNS: get global group DefaultDNS handle 35e4d01
DNS: Resolve request for 'google.com' group DefaultDNS
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 142.250.187.206, timeout is 2 seconds:
DNS: Message Validated
DNS: Converting Response to DNS Cache Entry
DNS: ** Answer Section **
AN(0): Name: google.com, RR type=1, class=1, ttl=168, datalen=4
DNS: Entry not found in cache, so create one
DNS: namelen 11, txtlen 0
DNS: Reparsing for adding to cache
DNS: hostname is google.com, RR type=1, class=1, ttl=168, n=4
DNS: Added New Cache Entry
DNS: Added Response to cache
DNS: get global group DefaultDNS handle 35e4d01
DNS: Resolve request for 'google.com' group DefaultDNS
DNS: Found Cache Entry
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 10/18/20 msAs you can see above, the debug messages are being displayed on the CLI. Let's re-direct the debug messages to our external syslog server.
logging trap debugging
logging debug-trace
INFO: 'logging debug-trace' is enabled. All debug messages are currently being redirected to syslog:711001 and will not appear in any monitor session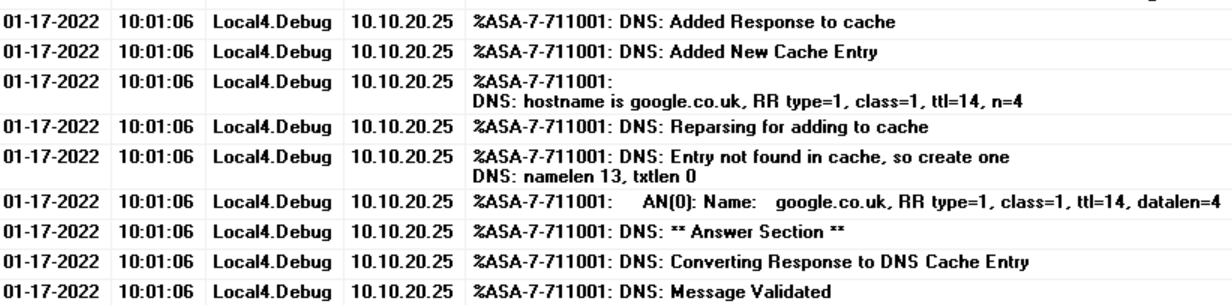
As you can see, ASA sends the debugs messages to the syslog server and not to the CLI.
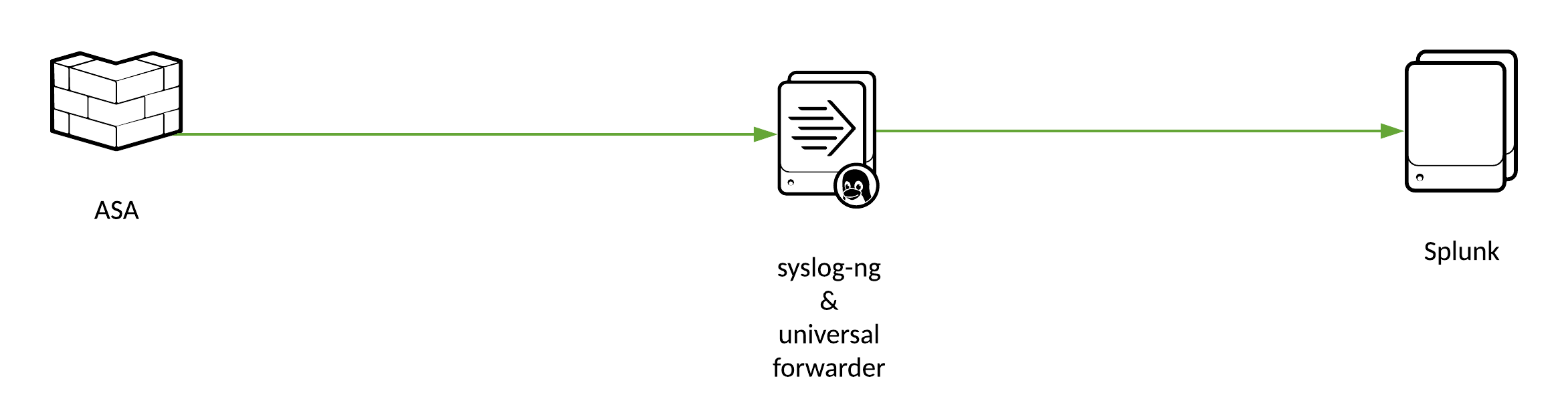
Cisco ASA syslog with Splunk
If you want to learn more about integrating ASA syslogs with Splunk, please check out my other blog post here.
Closing up
ASA logging is something that falls into the 'one doesn't fit all' category. Each environment has its own specific requirements. You could send informational and lower logs to both ASDM and external syslog servers but keep the CLI logs to a minimum.




