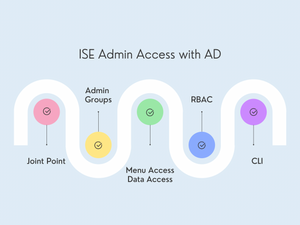
What if I tell you that only 3 out of 10 ISE admins use AD for ISE admin login (trust me, I just didn't make that up)
Generally, local admin account is used to log in to the ISE web GUI and CLI. In this blog post, I will explain how to use Active Directory credentials to log in to both the management GUI and the CLI.
Join Cisco ISE to Active Directory
Before you start using AD groups in your policies, you need to join ISE to the domain. An AD account with permissions to create a machine account is required initially. This account is only needed once and will never be used again (unless you store the credentials). ISE will use this account to create its own computer account in AD and use that account moving forward to perform AD lookups.
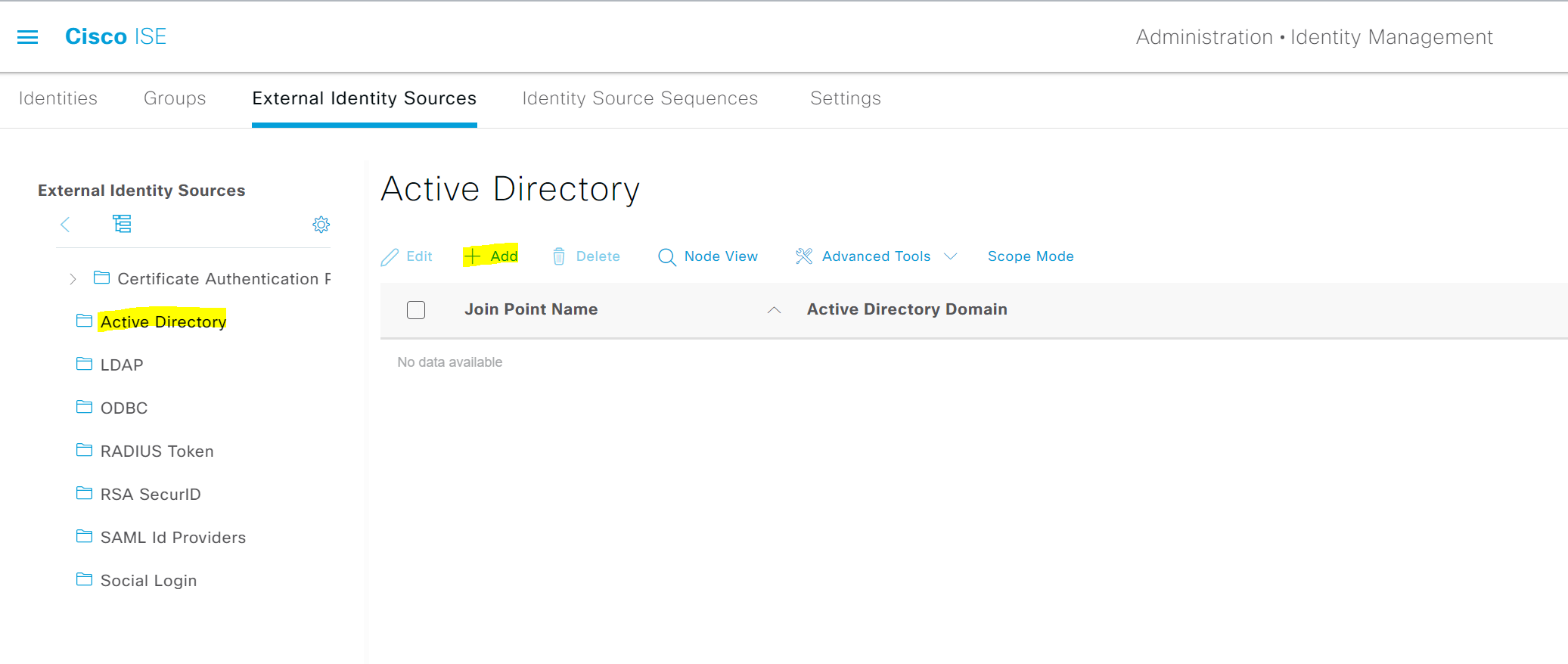
1. Navigate to Administration > Identity Management > External Identity Sources > Active Directory > Add and fill in your Joint Point Name (can be anything) and the AD domain.
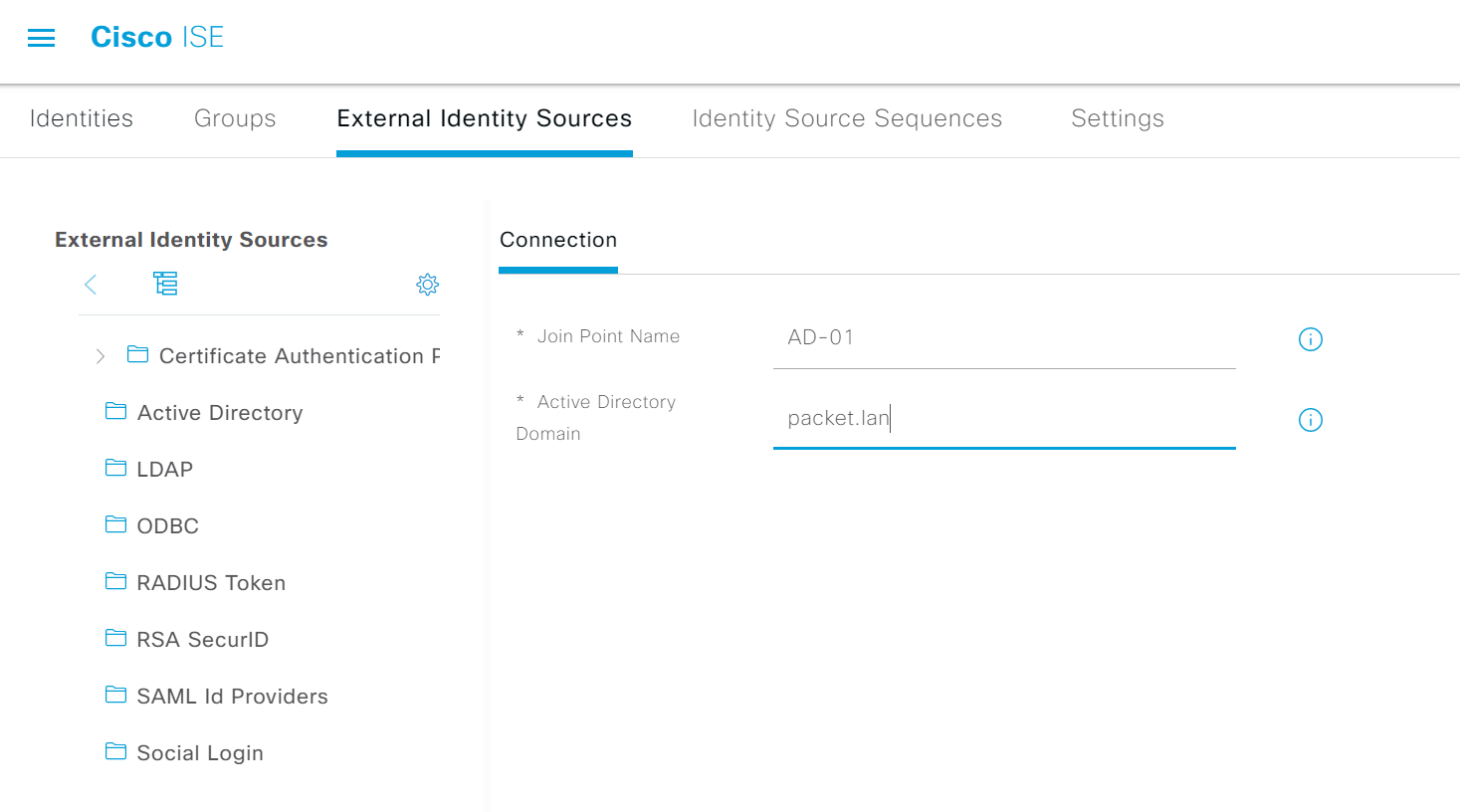
2. Join the domain by supplying the account which can create computer accounts. I'm using the Administrator account for this example.
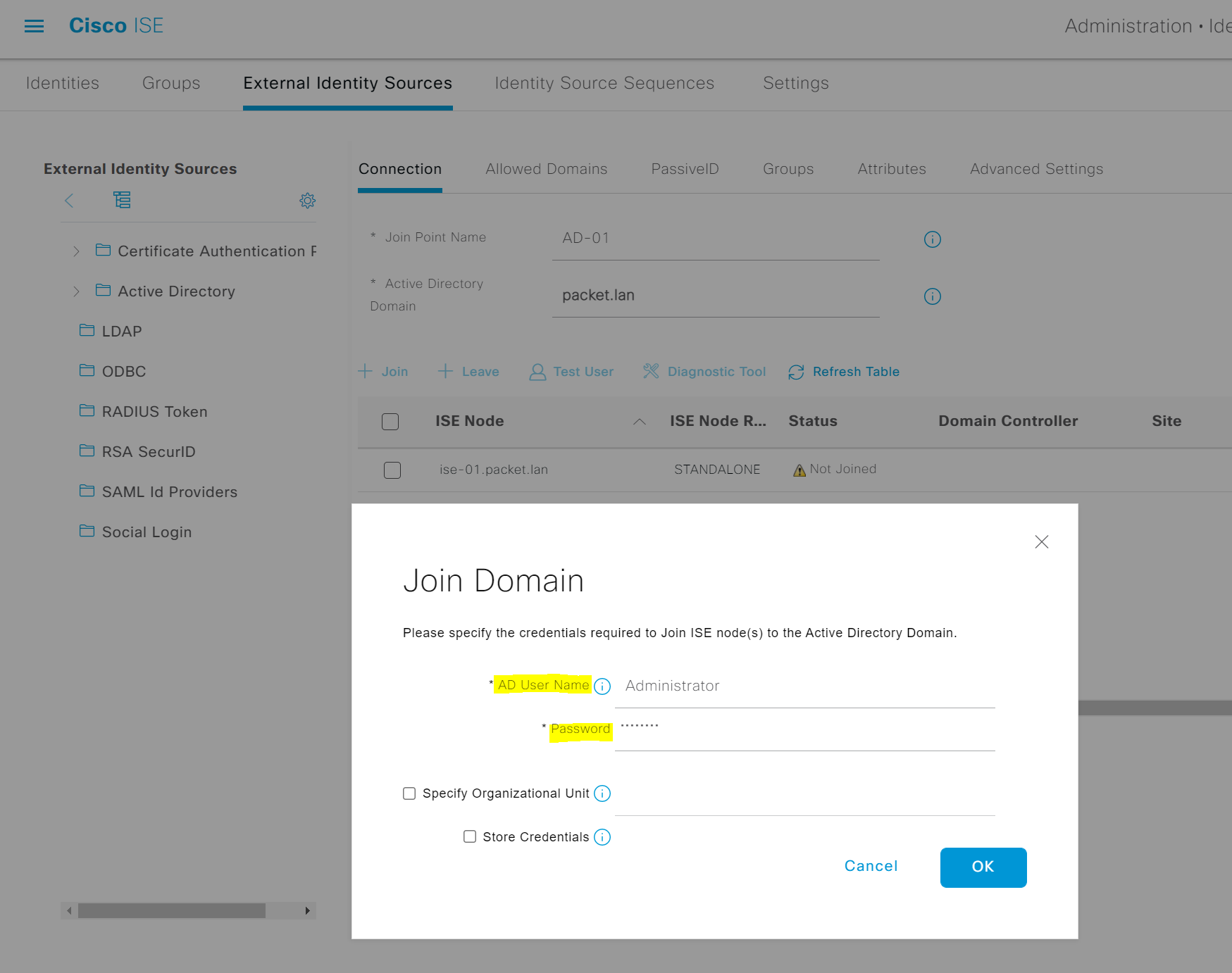
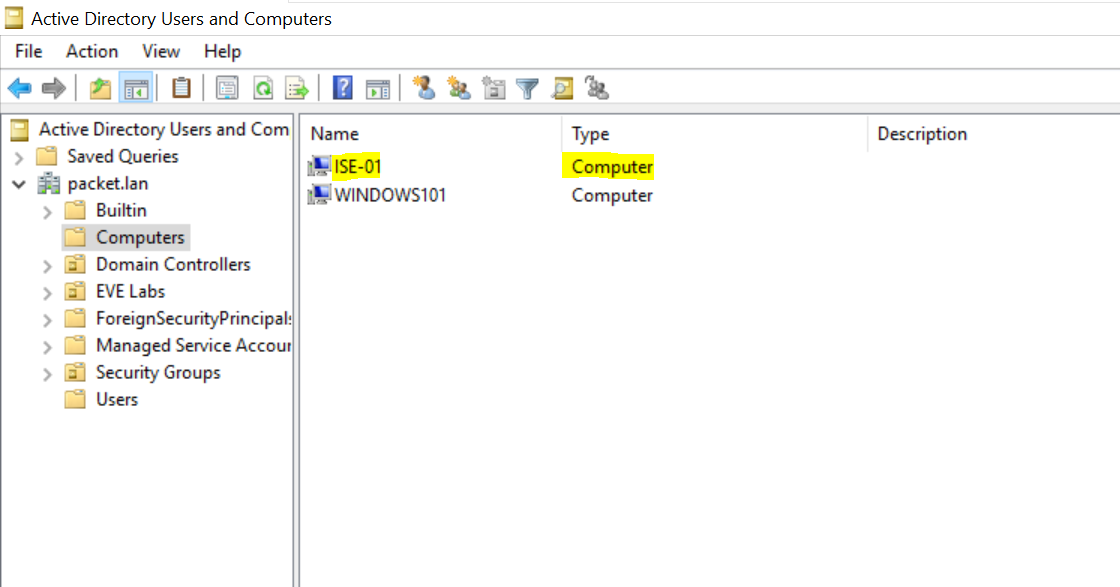
3. Once ISE is joined to the domain, you should see the status as 'operational'. If you go to AD, you will see that ISE is added as a computer account. This ISE account is used to perform all the AD lookups moving forward.
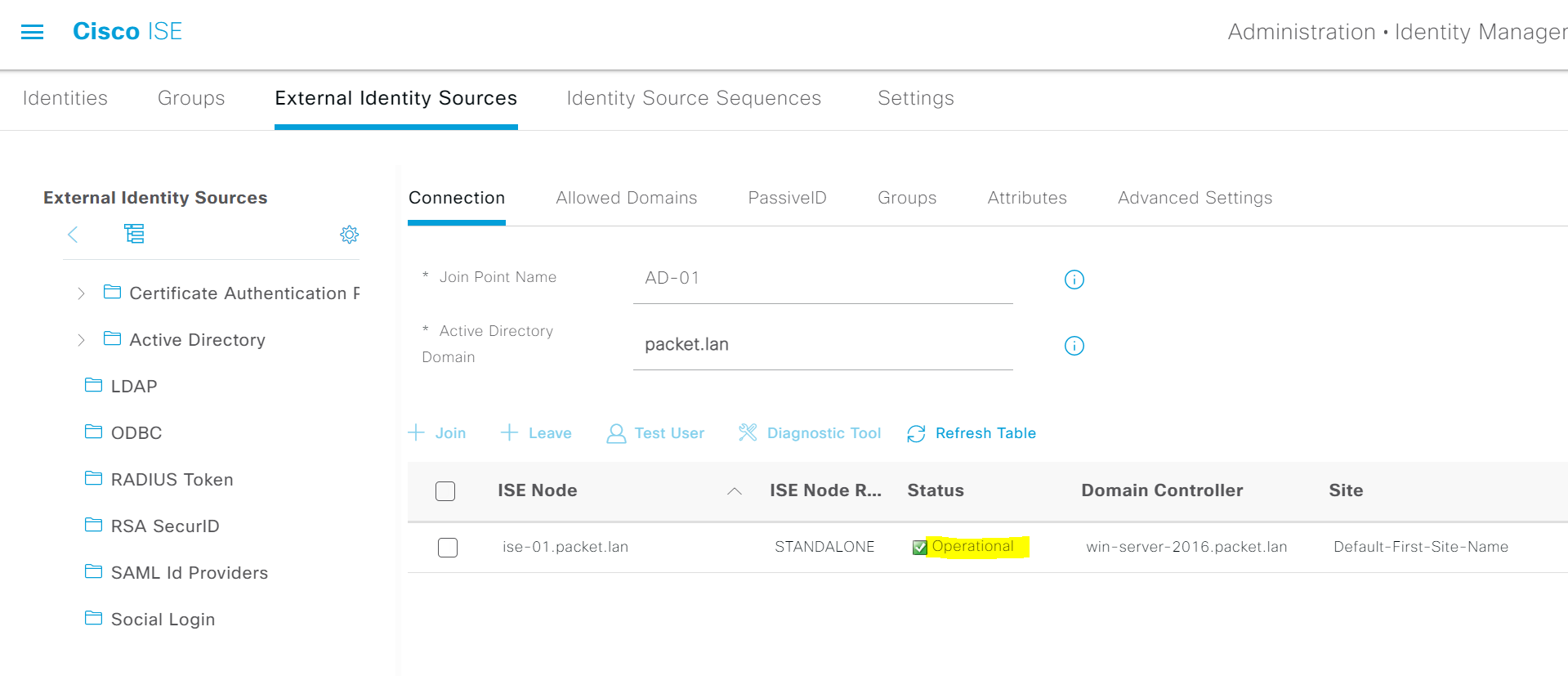
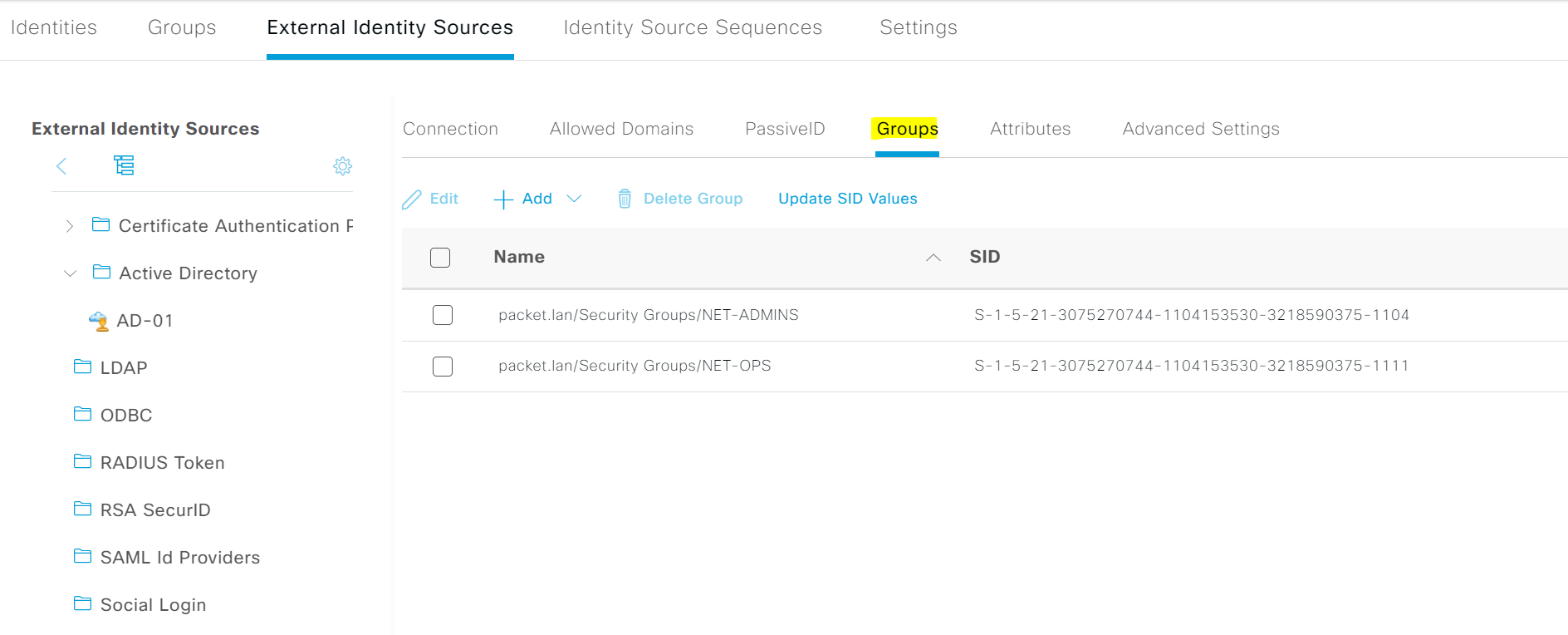
4. You need to import the relevant groups to ISE before using them in the policies. I've added two groups for this example, Net-Admins and Net-Ops.
ISE Admin Access
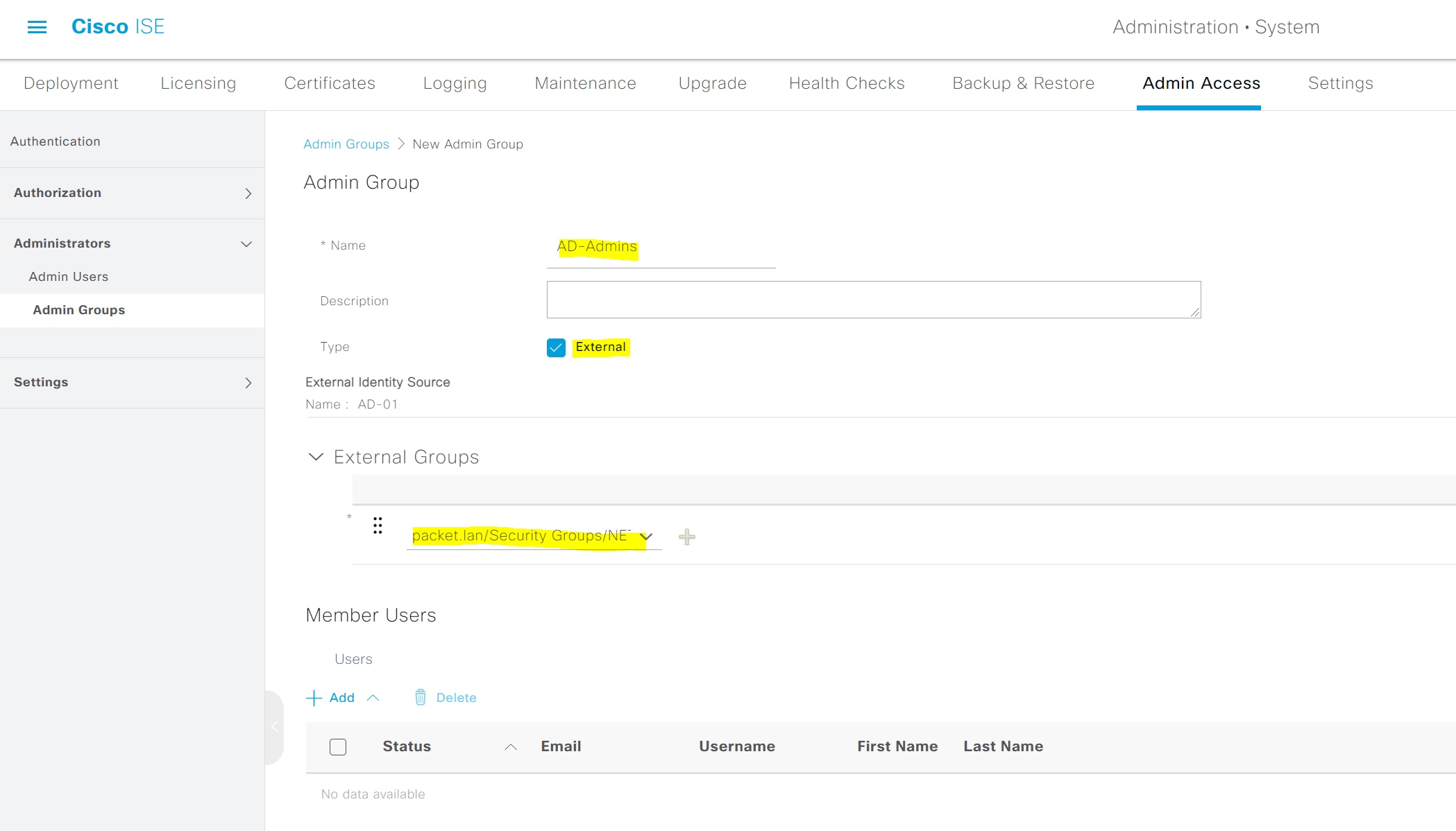
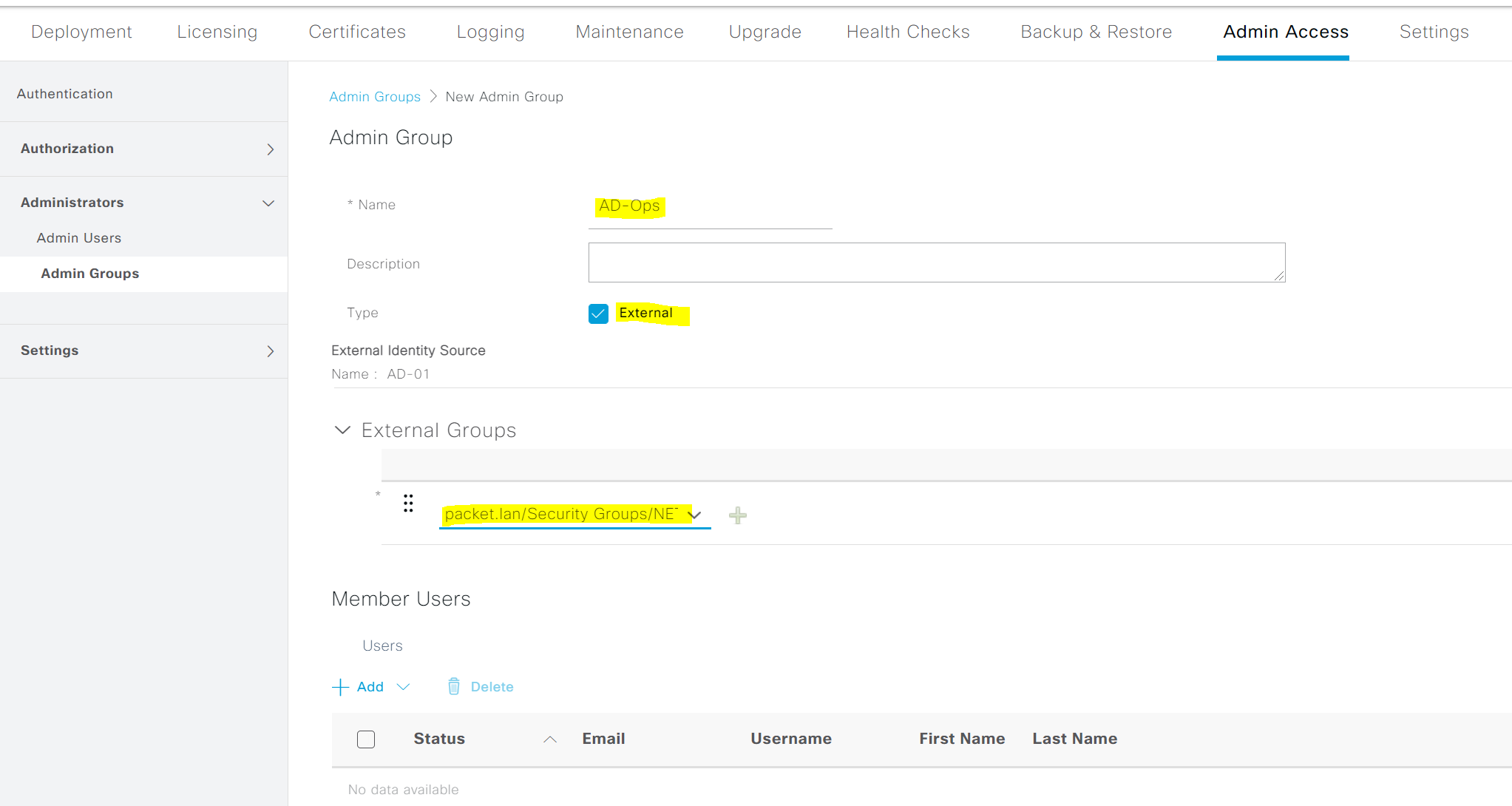
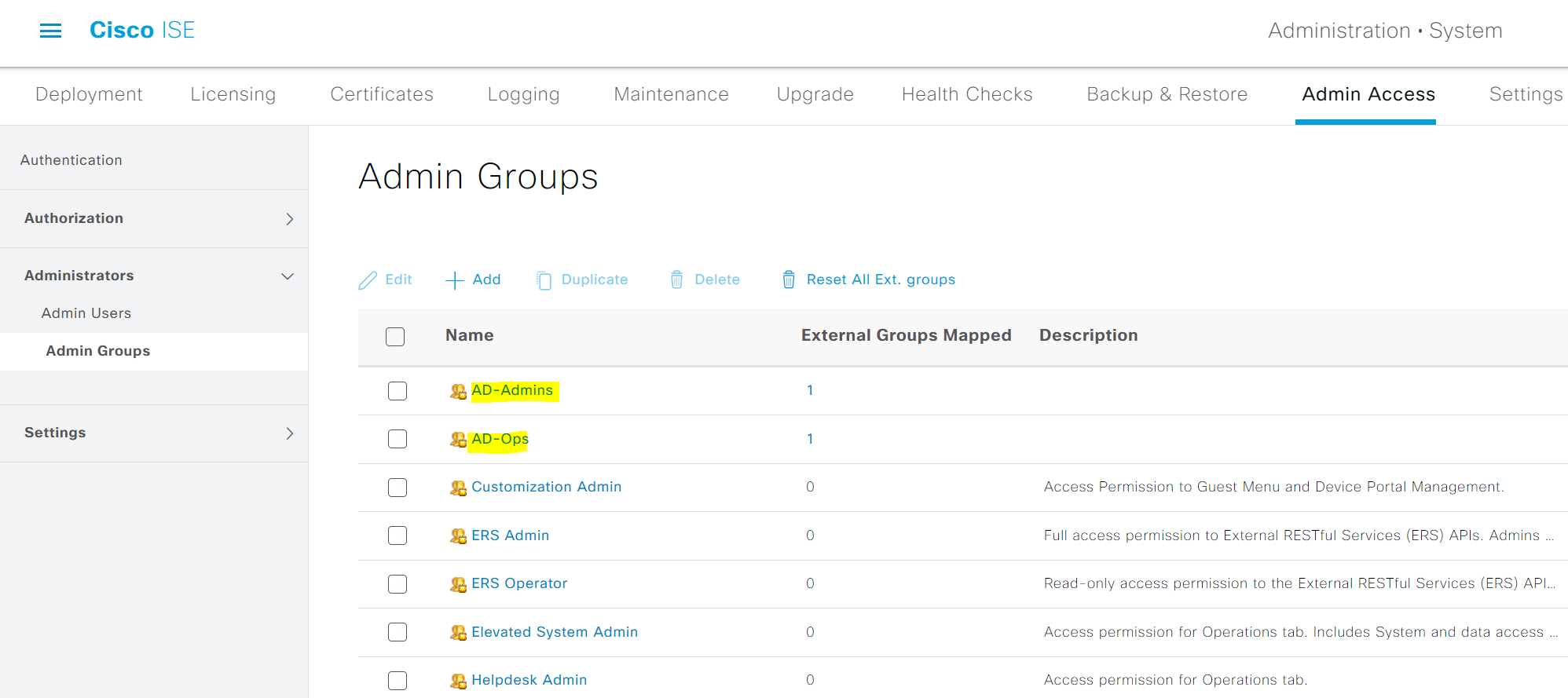
1. Create Admin Groups with appropriate AD groups. I created two Admin groups, 'AD Admins' and 'AD Ops' and added both AD groups into it. The Admins Group name doesn't need to match the AD groups.
2. Menu Access
The 'Menu Access' permissions allow you to show or hide the specific menu and submenu items of the management GUI. You can create permissions to restrict or enable access at the menu level.
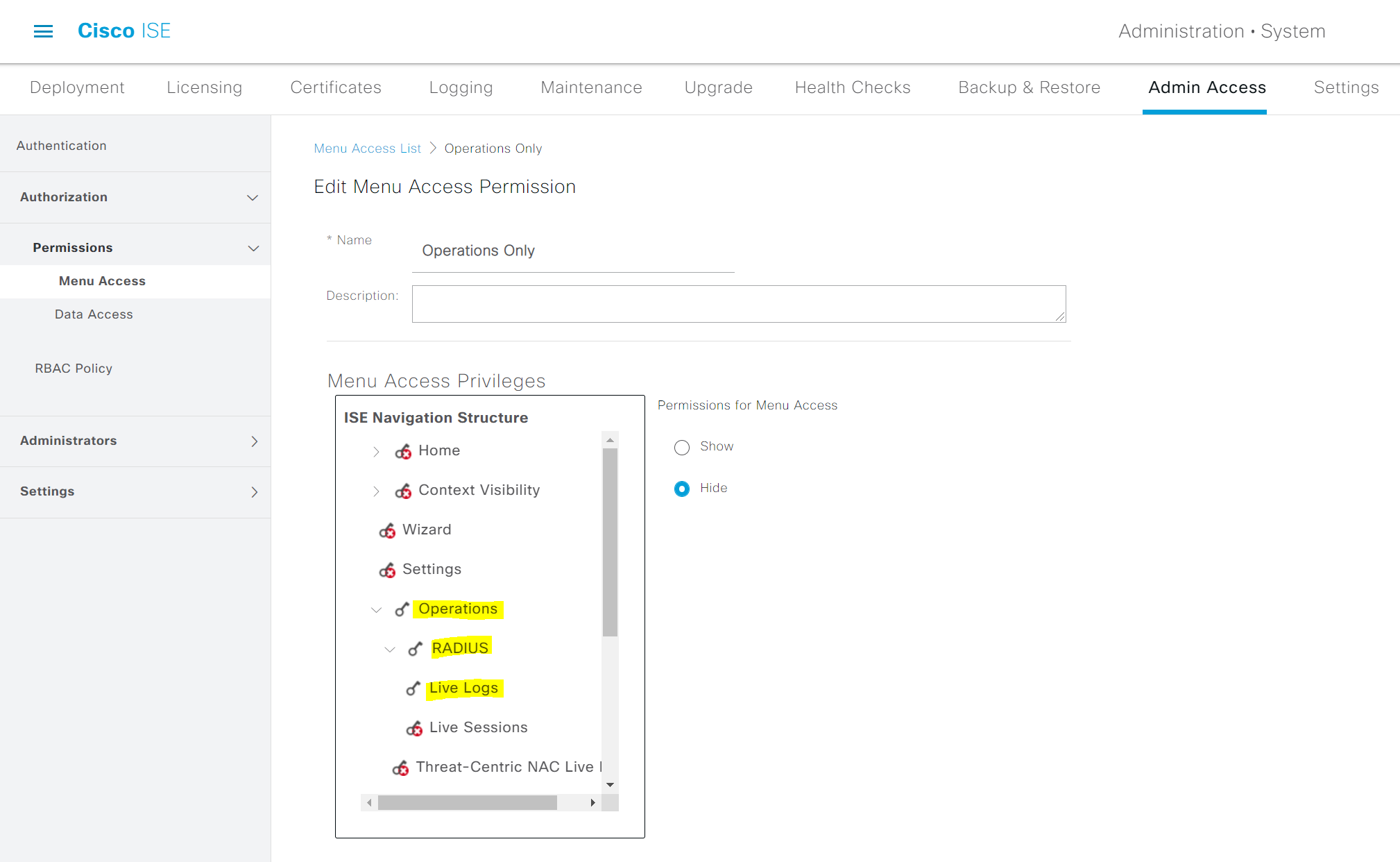
Users who are part of the Net-Admin AD group will have 'Super Admin Access. Menu Access for super admin is pre-configured. Users who are part of the Net-Ops AD group will have access to Radius Live Logs only, so you will need to create a custom 'Menu Access' for NetOps users. I call this 'Operations Only' menu access.
You can also use the 'Data Access' permissions to grant read and write, read-only, or no access to the Admin Groups, User Identity Groups, Endpoint Identity Groups, Locations/Device Types data in the management GUI.
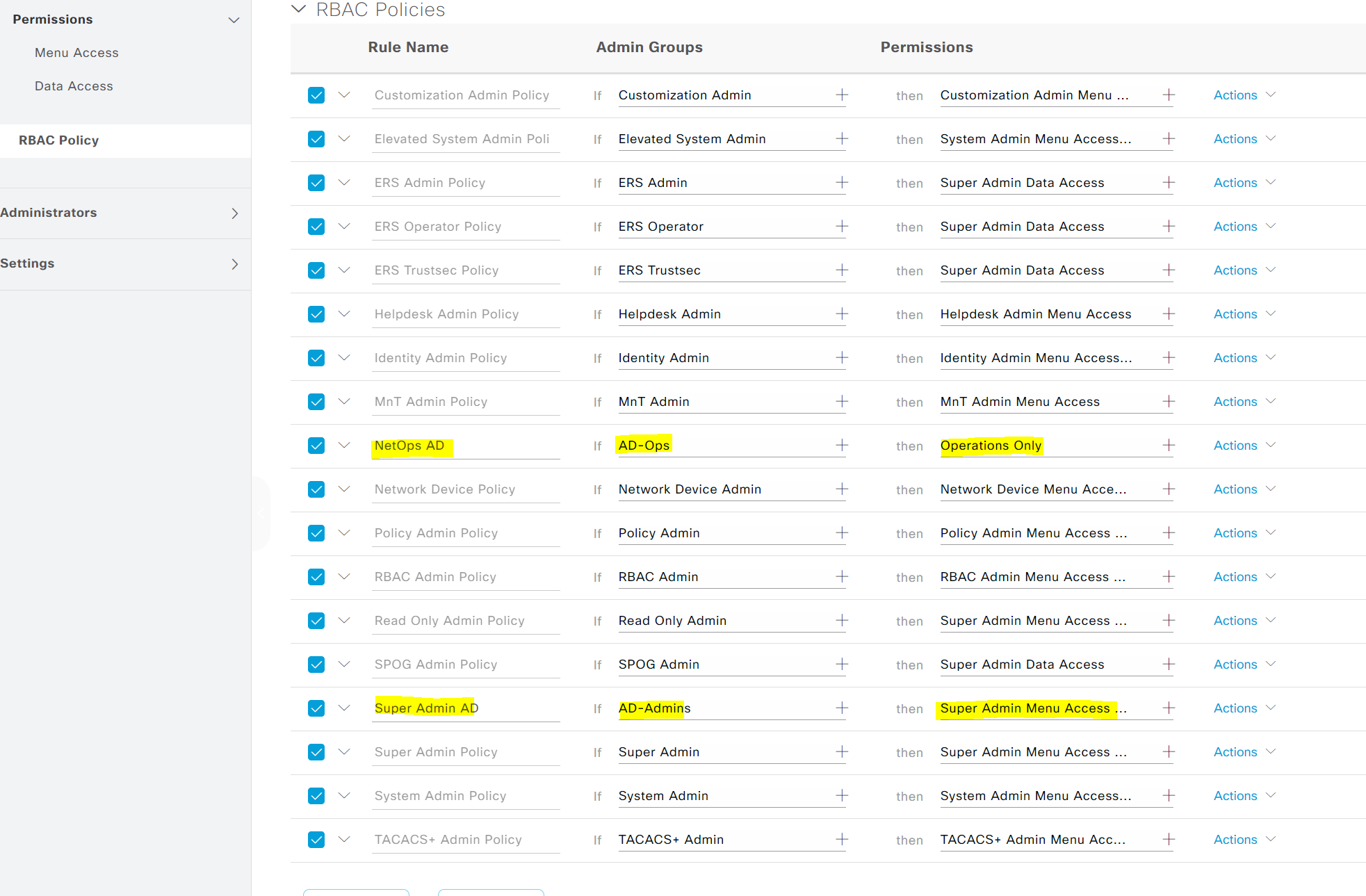
3. Configure Role-Based Access Policies (RBAC) for both Admin Groups as shown below.
4. Let's login with the user account which is part of the Net-Ops AD group. The user should only have access to 'Radius Live Logs' and nothing else.
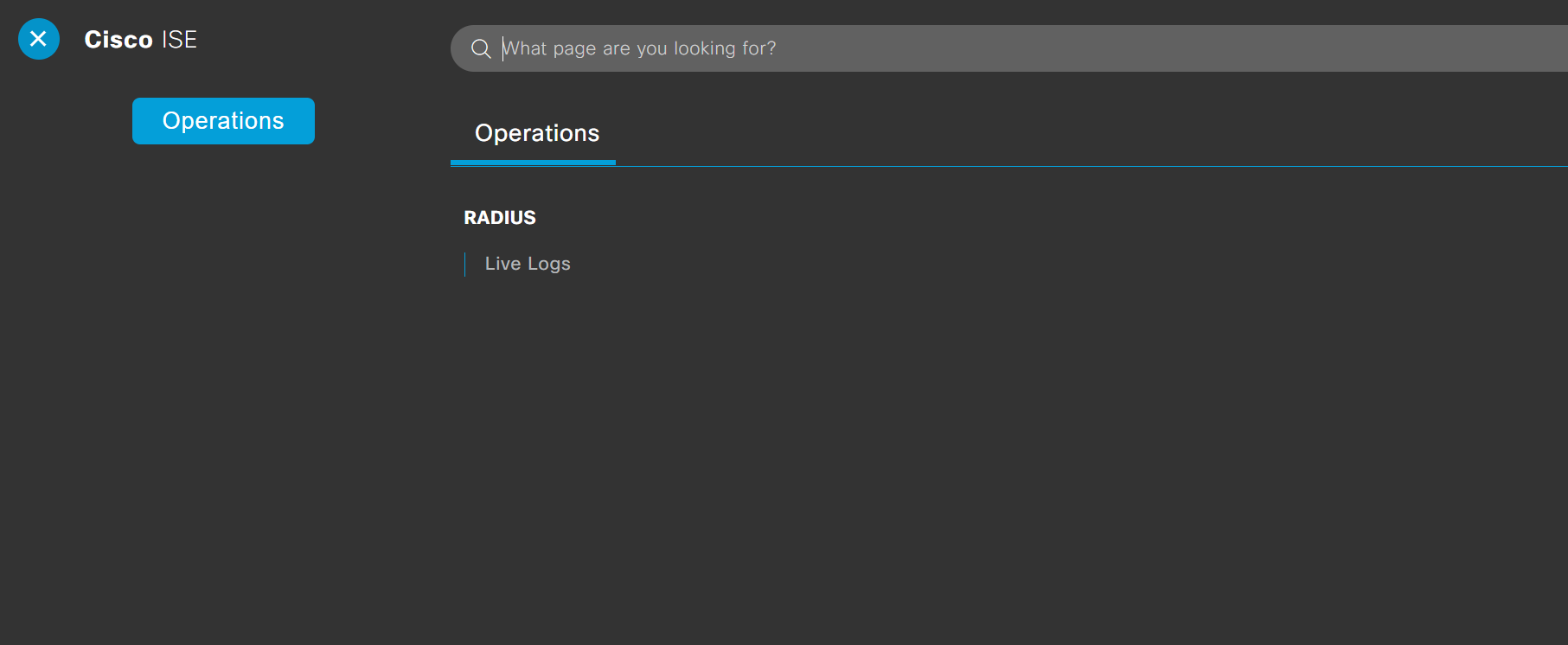
As you can see above, the user has access to Live Logs only.
ISE CLI Access using AD Credentials
Let me preface by saying that I always prefer to use local credentials for the CLI access as only a very limited number of people may need to log in. If you are someone who wants to use AD for CLI login then go for it. The important thing to note here is that during the configuration, the AD joint point you configured via the GUI will break and you will have to re-join ISE to the domain which can be catastrophic in the production environments.
Active Directory User Attributes
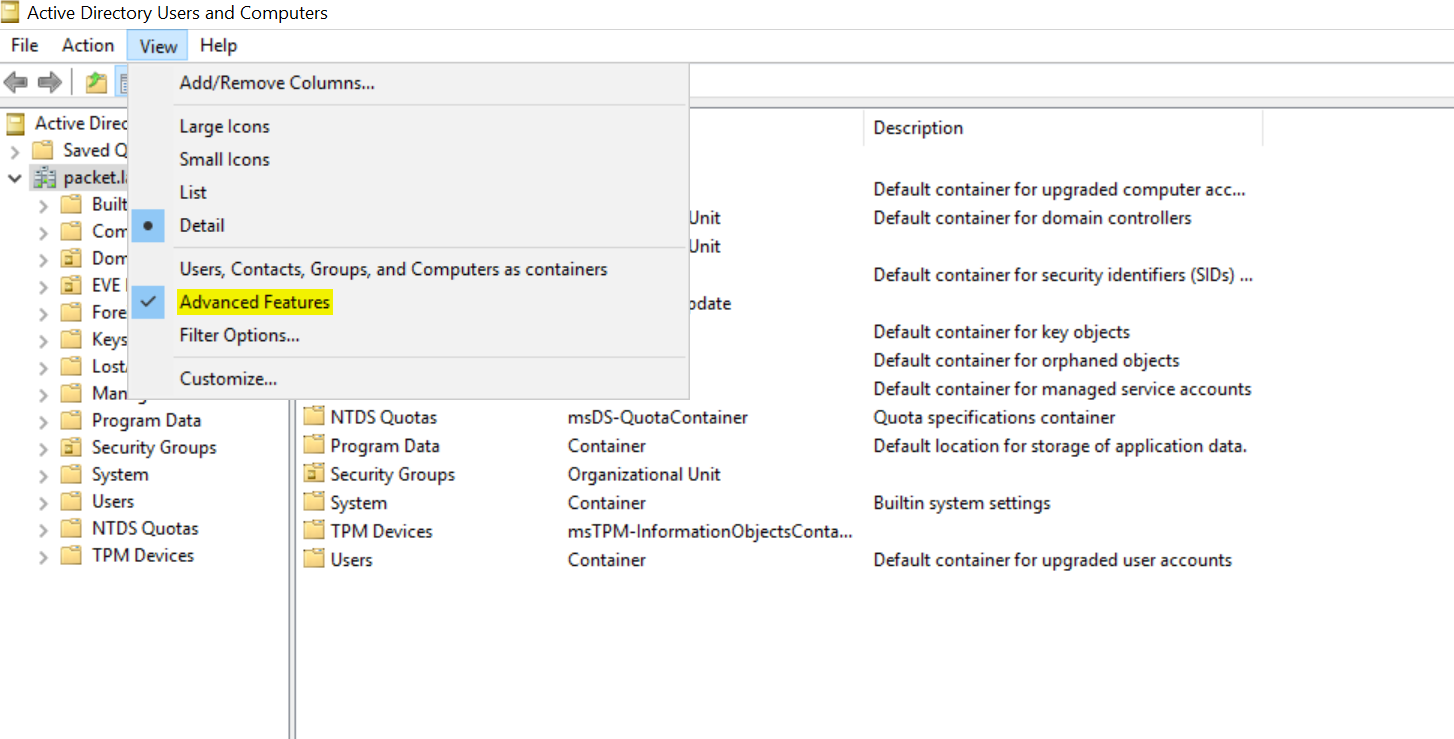
You need to modify the attributes for each user that will use AD credentials to log in to the CLI. First, enable Advanced Features under the view menu.
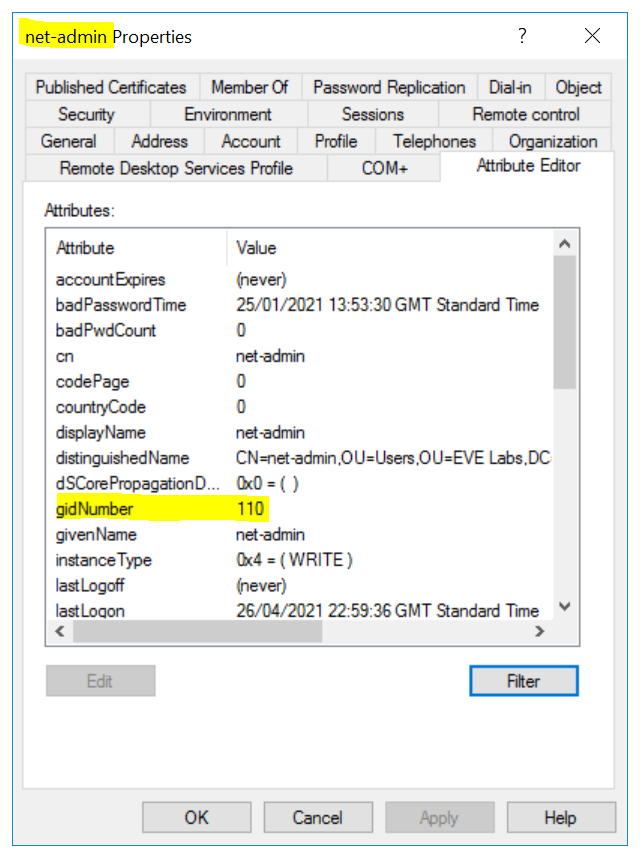
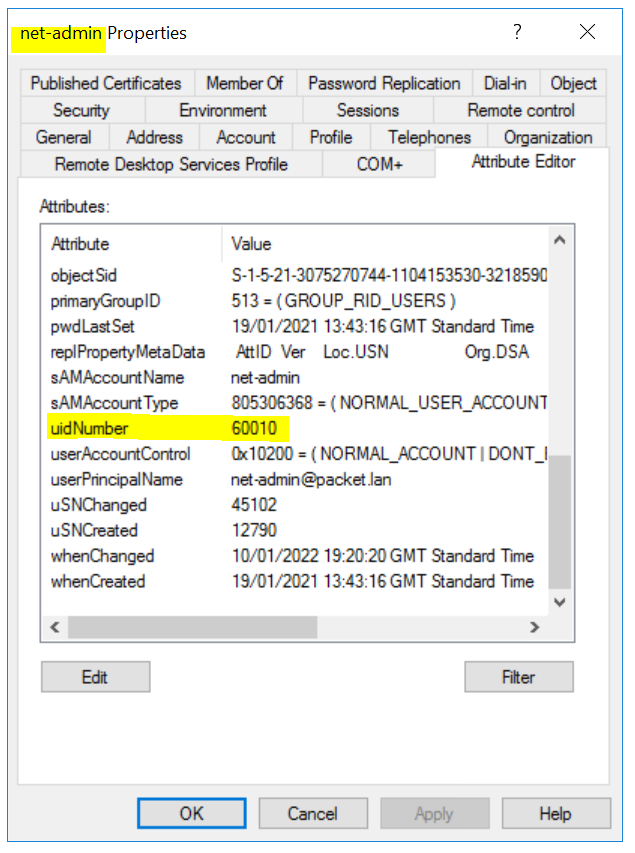
Open the user account (net-admin for this example) and go to Attribute Editor, edit the following attributes:
- gidNumber - 110 for admin user or 111 for the read-only user
- uidNumber - any number greater than 60000 and make sure the number is unique amongst the users.
Join the CLI users to Active Directory Domain
ise-01/admin(config)# identity-store active-directory domain-name packet.lan user net-admin
If the domain packet.lan is already joined via UI, then you must rejoin the domain packet.lan from UI after this configuration. Until the rejoin happens, authentications to packet.lan will fail
Do you want to proceed? Y/N [N]: Y
Password for net-admin:
Joined to domain packet.lan successfullyI can now log in to the ISE CLI using an AD account.
ise-01/net-admin#Finishing up
ISE AD integration is one of the important parts of ISE deployment. By combining AD with RBAC, you can fine-tune the Admin access to the Management GUI.