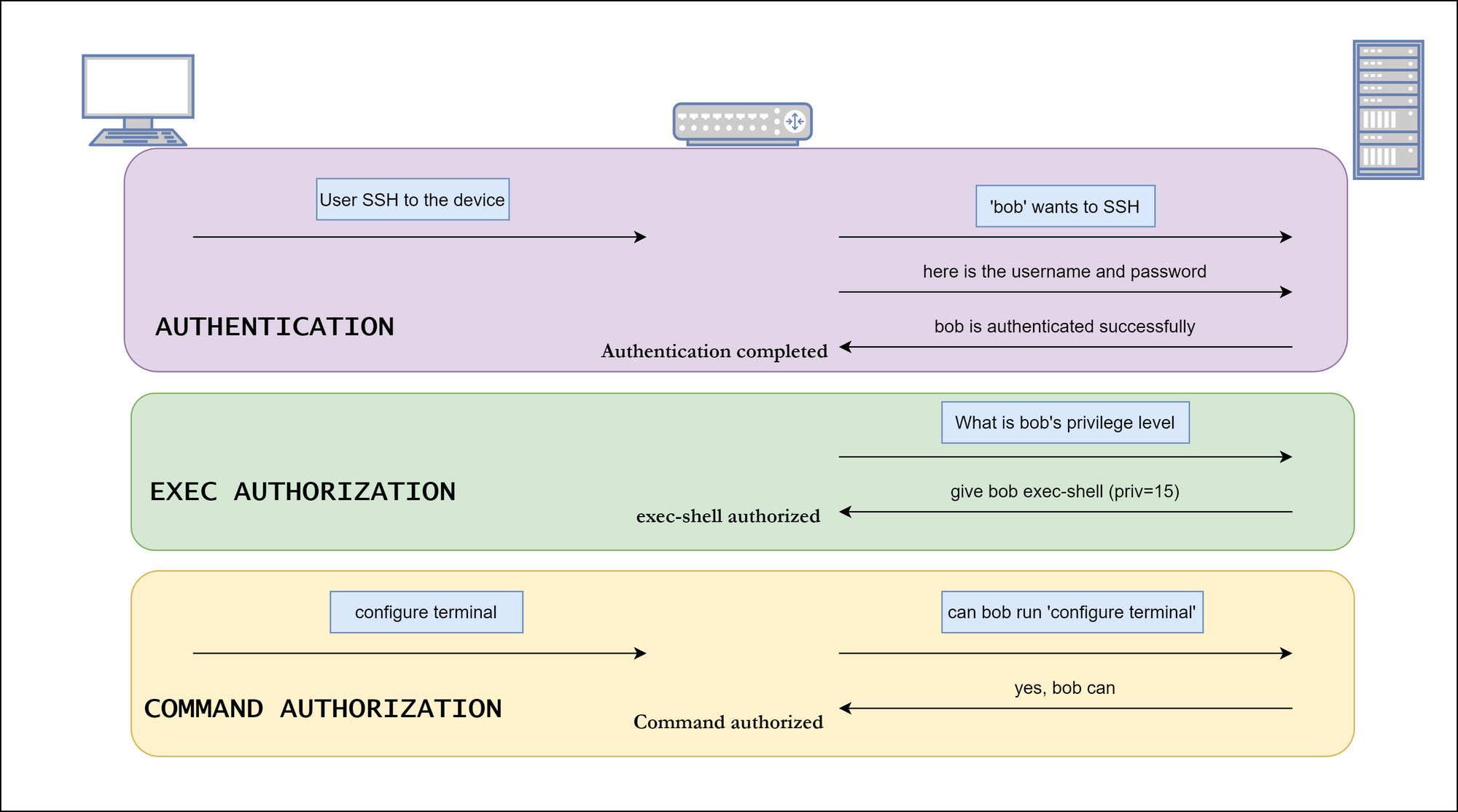
In this blog post, we will discuss how to configure authentication, authorization and accounting on Cisco devices using the TACACS+ protocol.
Authentication using the local database (without AAA)
When you configure a new Cisco device, you are most likely to use the local user database for authentication, the configuration would look something like the one shown below. This method works well if you only have a couple of devices to manage and have a very small team with one or two Network admins.
The following shows a local user called bob has been configured with privilege 15. Local enable password has also been configured.
username bob privilege 15 secret 5 $1$zOdg$tZE95Hmo8wcCtnMtIgirg0
enable secret 5 $1$rbdc$J2SyY04imHcbCivFgi3gb0
line con 0
login local
line vty 0 4
transport input ssh
login local
line vty 5 15
transport input ssh
login local
This doesn't work very well if you have more than 10 devices and a big team. Ideally, what you want is to authenticate the logins against a centralised server such as Cisco ISE using TACACS+. You don't necessarily need to have ISE for this to work, you can also use open-source TACACS+ servers such as tac_plus
aaa new-model
To enable AAA on your Cisco device, all you have to do is run aaa new-model command. This command activates AAA on the device. You can still log in to the router using your existing local database user account bob at this point.
AAA TACACS+ server configuration
The next step is to define the TACACS+ servers and then group them into AAA server groups. We can also configure which interface should be used for sourcing the TACACS+ packets. The key configured on the router has to match the key configured on the TACACS+ server.
tacacs server ISE-01
address ipv4 10.10.0.100
key Cisco123
tacacs server ISE-02
address ipv4 10.10.0.200
key Cisco123
aaa group server tacacs+ TACACS-SERVER-GROUP
server name ISE-01
server name ISE-02
ip tacacs source-interface Ethernet0/0Authentication
So far we have configured aaa new-model and then defined the TACACS+ servers. The next step is to define a method list that defines the ways AAA is performed and the sequence in which these methods are performed.
A method list is simply a named list describing the AAA methods to be queried (such as Local, Radius, or Tacacs+), in sequence. Method lists enable one or more security protocols to be used for AAA, thus ensuring a backup system in case the initial method fails. In our example, we will be using TACACS+ as the primary method and local database as the fallback method.
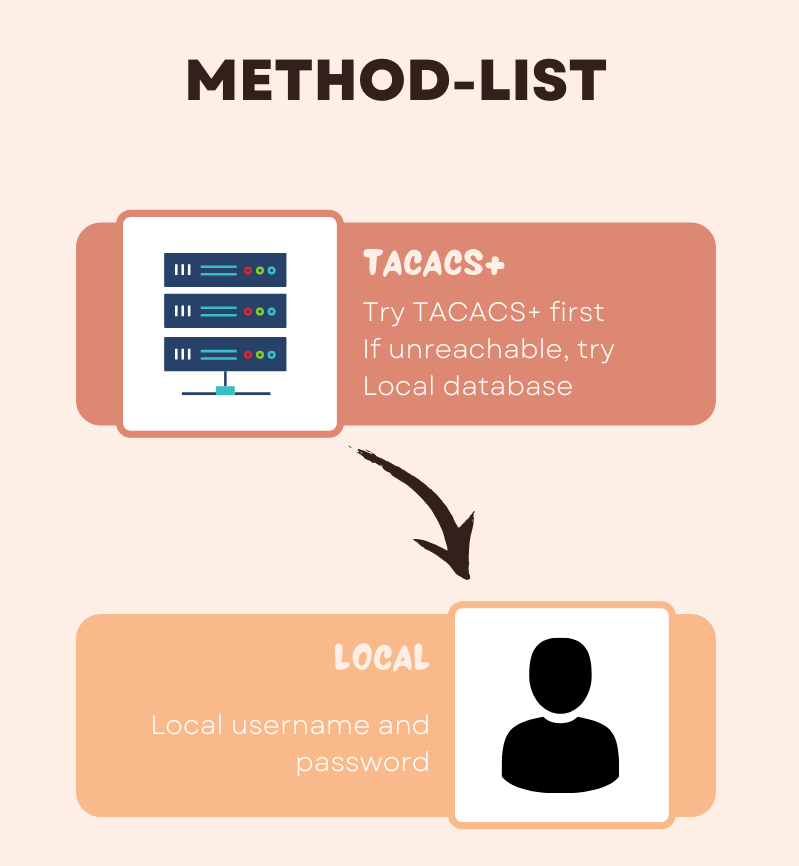
Once the method list is created, that needs to be applied to one or more lines (VTY, Console) to take effect. The only exception is the default method list (which is named 'default'). The default method list is automatically applied to all interfaces except those that have a named method list explicitly defined.
aaa authentication login default group TACACS-SERVER-GROUP localLet's break down the commands one by one.
- aaa authentication - We are configuring authentication
- login - The following method list is for user 'logins'
- default - We are using a 'default' method list (You can use a named list if you want but make sure to apply that to all the line interfaces (vty, console))
- group TACACS-SERVER-GROUP - Use all the configured TACACS+ servers within this group.
- local - If the TACACS+ servers are unreachable, use the local database as the fallback.
At this point, you should be able to log in to the router with your 'TACACS+' credentials. If at least one of the TACACS+ servers is reachable then you won't be able to log in with your local credentials. There are a couple of things to note after configuring 'authentication'
- When you log in, you are placed into the user-exec shell
- You need to use the 'local' enable password to go into the exec-privilege mode
Enable password from the TACACS+ server
As we have seen in the previous step, a local enable password is still required. Let's make one more change so, that the enable password is also authenticated against the TACACS+ server.
aaa authentication enable default group TACACS-SERVER-GROUP enableMost part of the configuration is self-explanatory. The first 'enable' keyword means this configuration is for 'enable' authentication. The second 'enable' keyword has also been configured, so if the TACACS+ server is unreachable, the locally configured enable password will be used.
Log in directly to exec-privilege mode
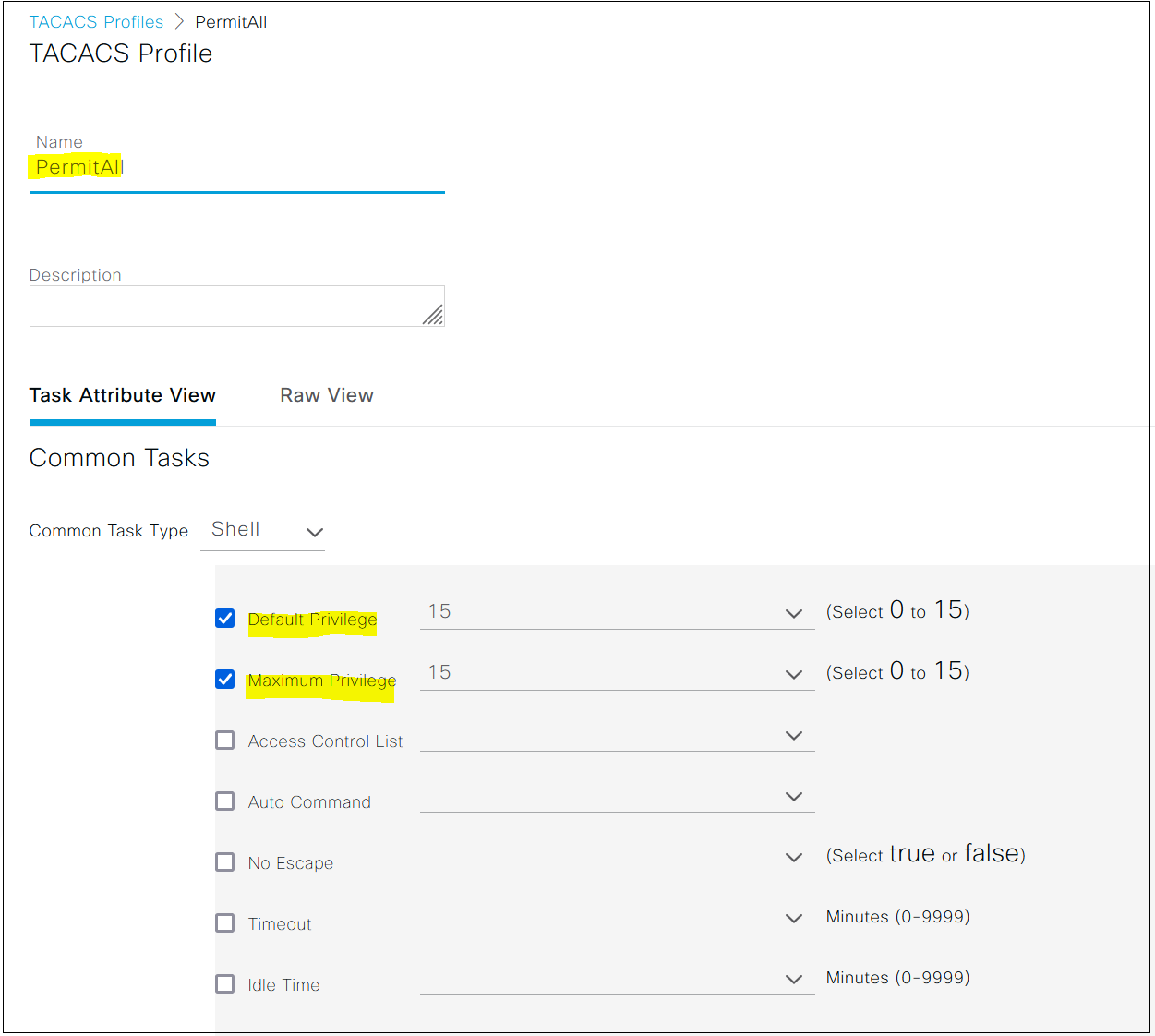
aaa authorization exec default group TACACS-SERVER-GROUP localWhen aaa authorization exec is being used, the router consults the TACACS+ server to determine the privilege level of the just authenticated user. So, following a successful authentication, the router assigns the user privilege level specified by the TACACS+ server. (Using the priv-lvl attribute)
As I mentioned earlier, I'm using Cisco ISE as the TACACS+ server in this example. I'm going to assign privilege level 15 for the user 'net-admin' user as shown below.
cisco#who
Line User Host(s) Idle Location
* 2 vty 0 net-admin idle 00:00:00 10.10.0.10
Interface User Mode Idle Peer Address
cisco#show privilege
Current privilege level is 15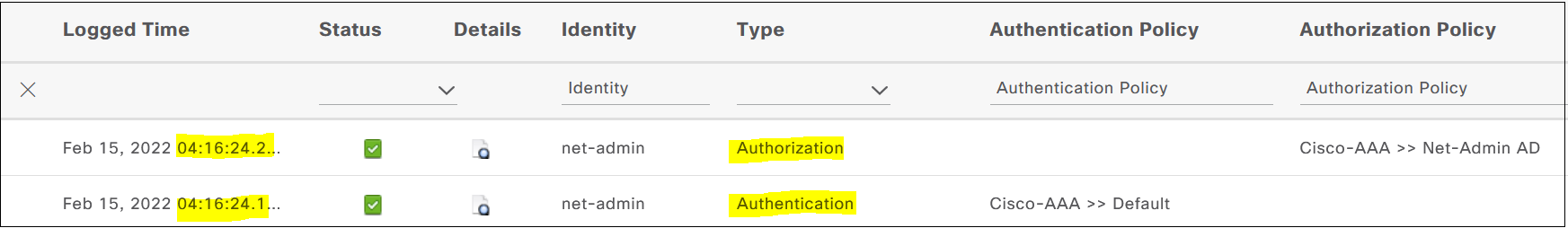
As you can see above, the router sent an 'authorization request' to ISE as soon as the 'authentication' is completed. ISE in return sent an 'authorization response' to the router indicating that the user should be granted priv-lvl=15 permissions.
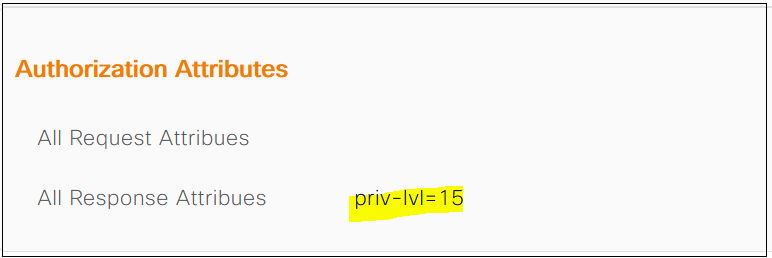
Command Authorization
Just to recap, at this point our configuration looks like the following.
aaa authentication login default group TACACS-SERVER-GROUP local
aaa authentication enable default group TACACS-SERVER-GROUP enable
aaa authorization exec default group TACACS-SERVER-GROUP local When the 'net-admin' user logins to the router, they are placed directly into the privilege-exec mode which means the user can run pretty much any command. The router doesn't consult the TACACS+ server whether or not the user is authorized to run the commands. Let's enable command authorization so, each and every privilege level 15 command is authorized.
For this example, let's deny all the 'debug' commands and permit everything else. Please note that for this example, we are only authorizing privilege 15 commands and not 0 or 1 commands.
aaa authorization commands 15 default group TACACS-SERVER-GROUP local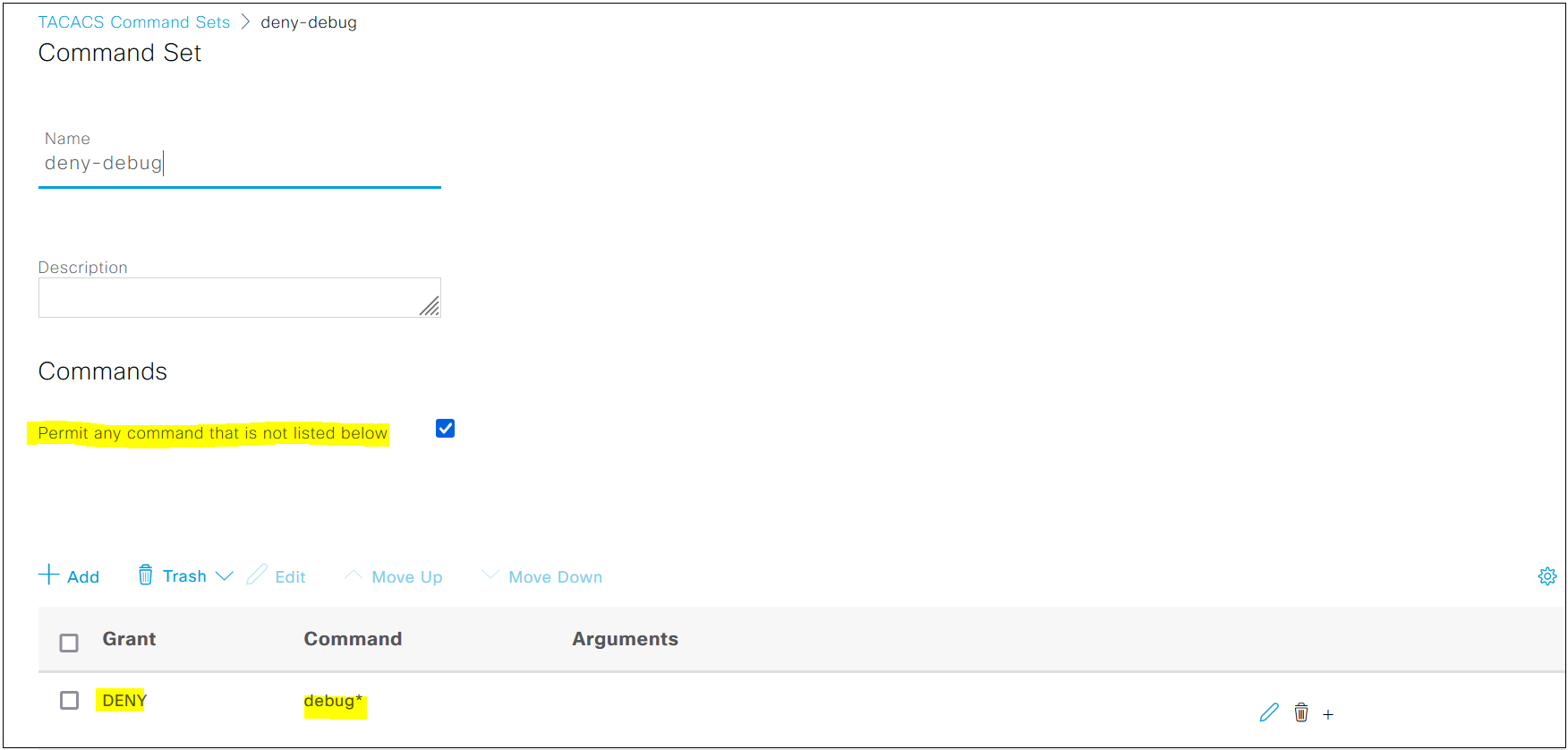
cisco#debug aaa authentication
Command authorization failed.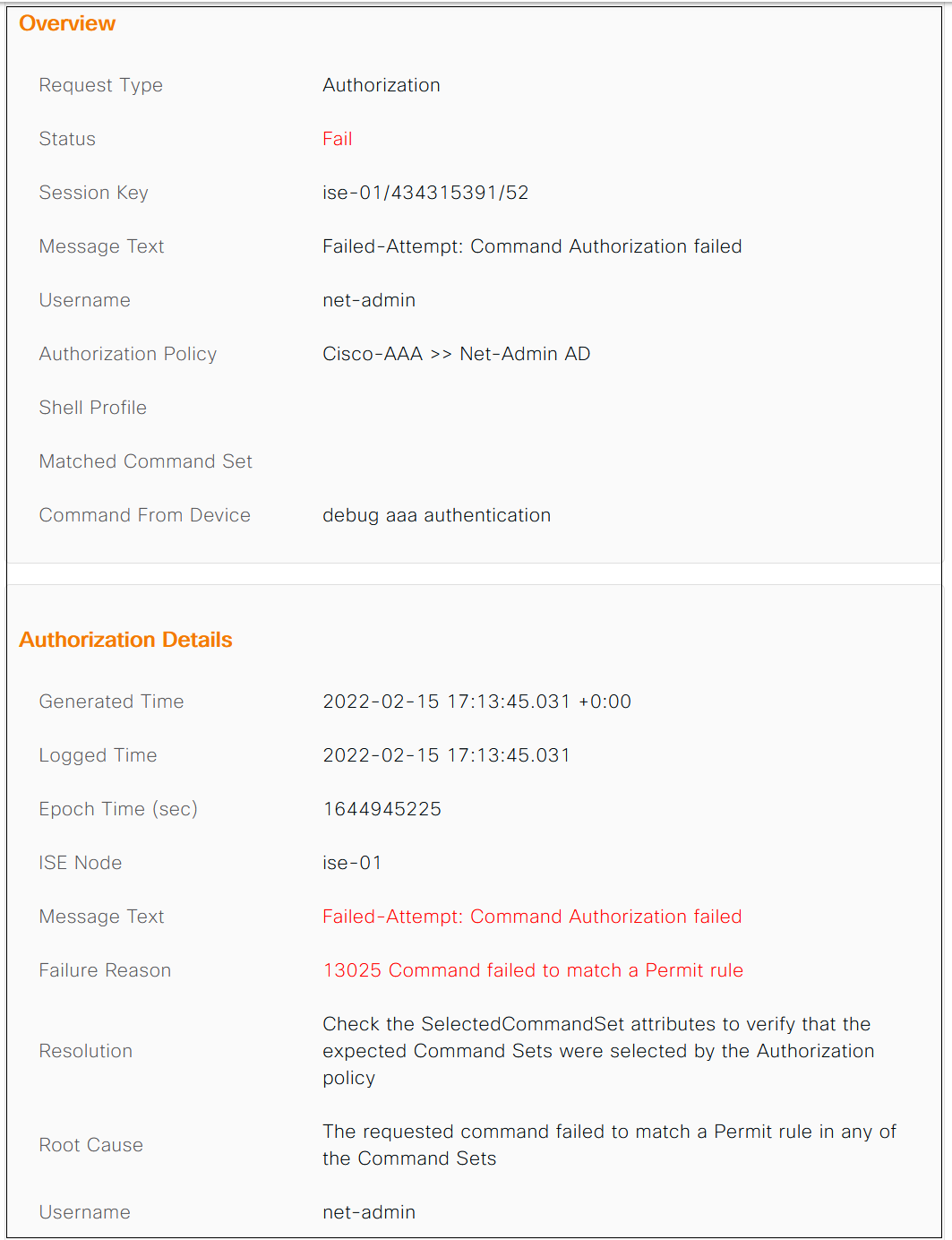
As you can see above, the user is unable to run the 'debug' commands anymore.
aaa authorization console to perform authorization. if-authenticated
Let's look at a scenario where the user is successfully authenticated to the router but during the SSH session, all the TACACS+ servers went down. What is going to happen to the command authorization now? Well, they will fail by default and the user will not be able to run any privilege 15 commands.
Of course, the user can close the current SSH session and then re-login with the local credentials however, you can use if-authenticated in conjunction with the authorization configuration.
The below is the default behaviour if the TACACS+ server goes down 'after' a user is authenticated.
cisco#conf ter
% Authorization failed.Let's configure if-authenticated for authorization and see what happens. I'm going to log in with TACACS+ credentials and then shut down the link to the ISE.
aaa authentication login default group TACACS-SERVER-GROUP local
aaa authentication enable default group TACACS-SERVER-GROUP enable
aaa authorization exec default group TACACS-SERVER-GROUP local if-authenticated
aaa authorization commands 15 default group TACACS-SERVER-GROUP local if-authenticatedcisco#conf ter
Enter configuration commands, one per line. End with CNTL/Z.
cisco(config)#exitAs you can see above, I was able to run the commands successfully even though ISE was unreachable. The debug log shows the authorization was successful due to the if-authenticated configuration.
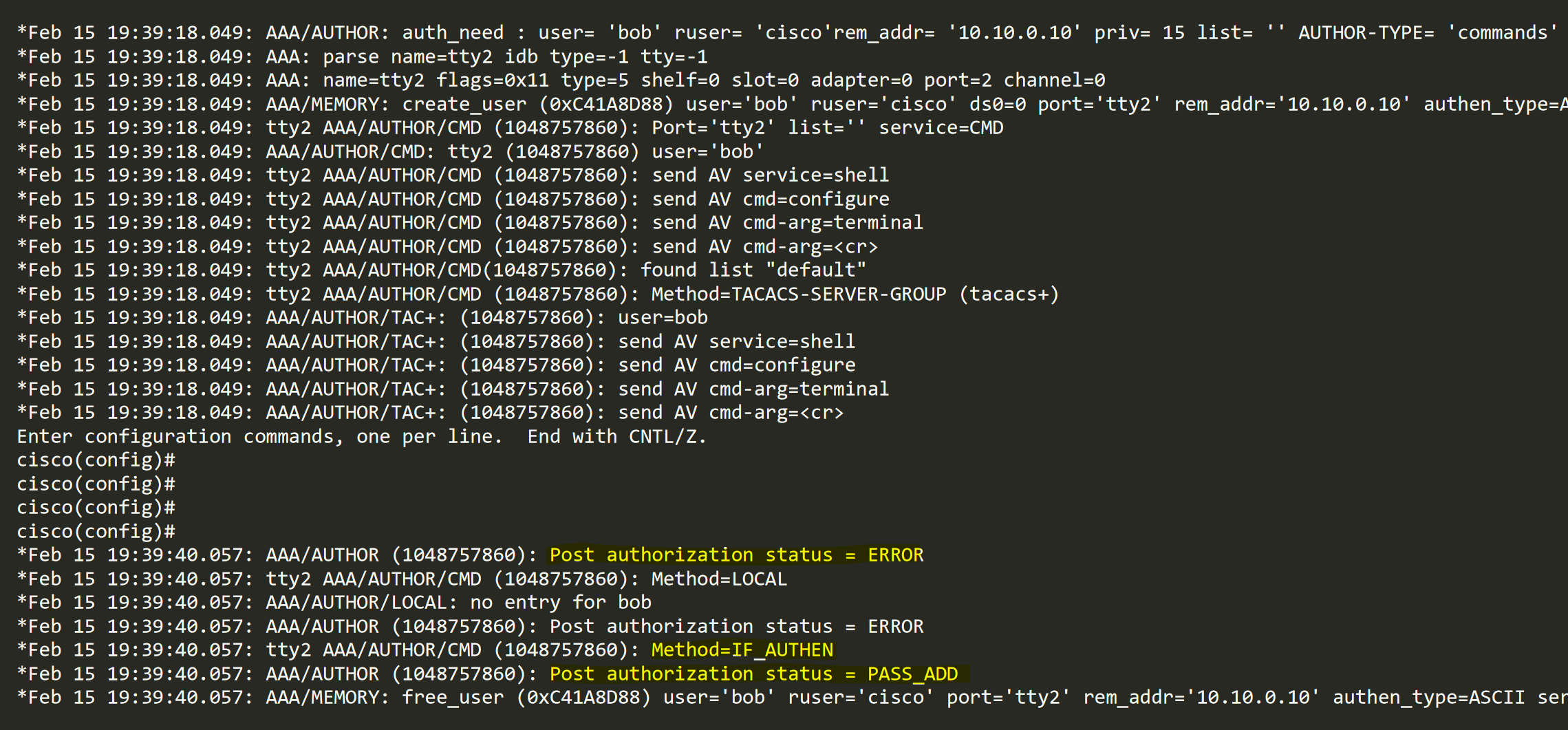
Accounting
You can configure accounting using the following commands. Each and every command a user types is recorded and can be viewed.
aaa accounting exec default start-stop group TACACS-SERVER-GROUP
aaa accounting commands 15 default start-stop group TACACS-SERVER-GROUP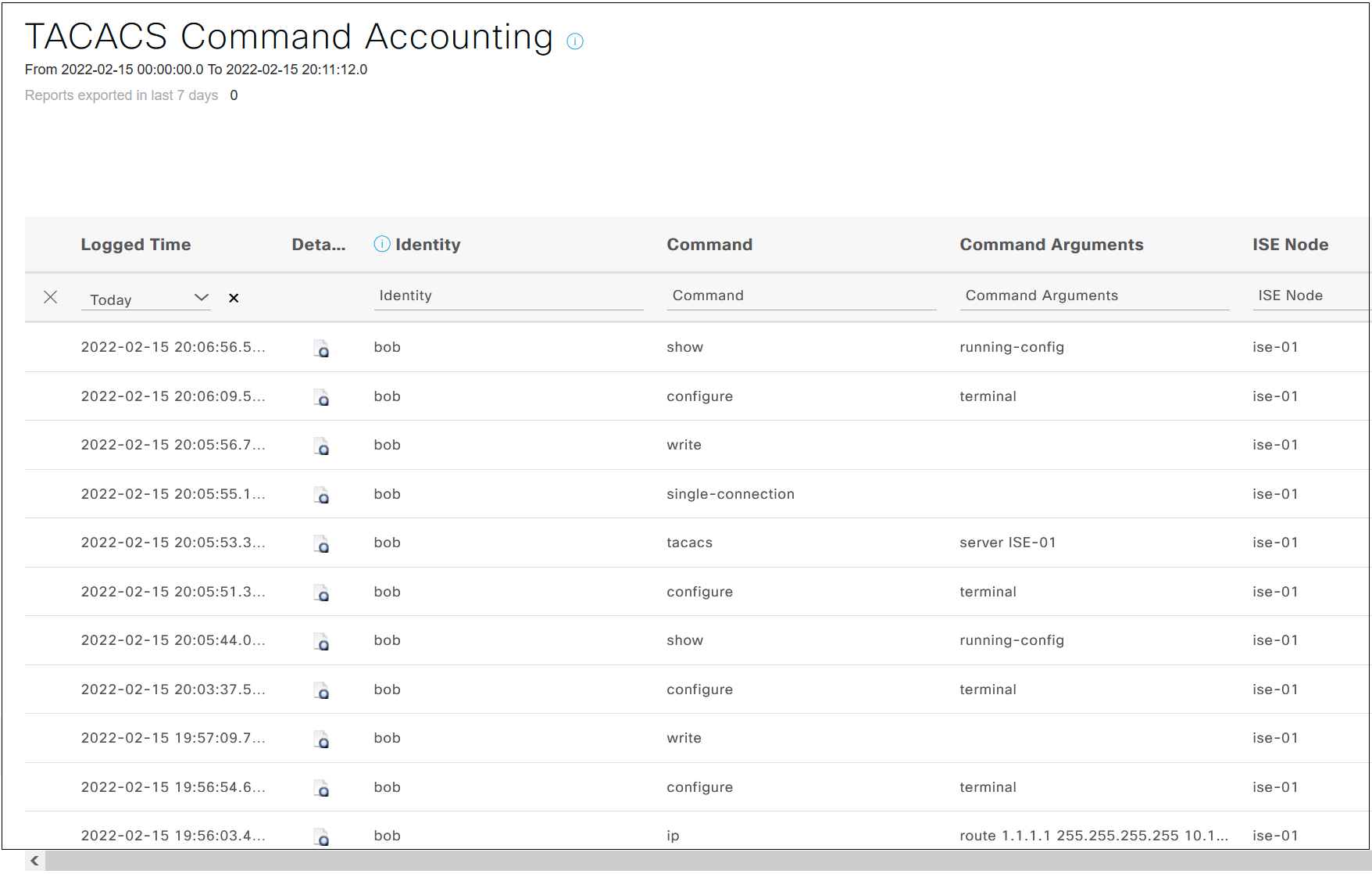
Closing up
Once you have finished configuring AAA, the complete configuration may look like the below.
aaa authentication login default group TACACS-SERVER-GROUP local
aaa authentication enable default group TACACS-SERVER-GROUP enable
aaa authorization exec default group TACACS-SERVER-GROUP local if-authenticated
aaa authorization commands 15 default group TACACS-SERVER-GROUP local if-authenticated
aaa accounting exec default start-stop group TACACS-SERVER-GROUP
aaa accounting commands 15 default start-stop group TACACS-SERVER-GROUP
username cisco privilege 15 secret 5 $1$zOdg$tZE95Hmo8wcCtnMtIgirg0
!
tacacs server ISE-01
address ipv4 10.10.0.100
key Cisco123
tacacs server ISE-02
address ipv4 10.10.0.200
key Cisco123
!
aaa group server tacacs+ TACACS-SERVER-GROUP
server name ISE-01
server name ISE-02
ip tacacs source-interface Ethernet0/0
!
aaa new-model