If you want to use EAP-TLS, EAP-FAST or TEAP as your authentication method for 802.1X then you may need to have the certificates issued to the user or computer (or both for EAP-Chaining)
This blog post explains the necessary steps required to successfully deploy the certificates to both user and computer using Active Directory Certificate Services. The blog post assumes that the CA server has been correctly configured and the computers have already been joined to the domain.
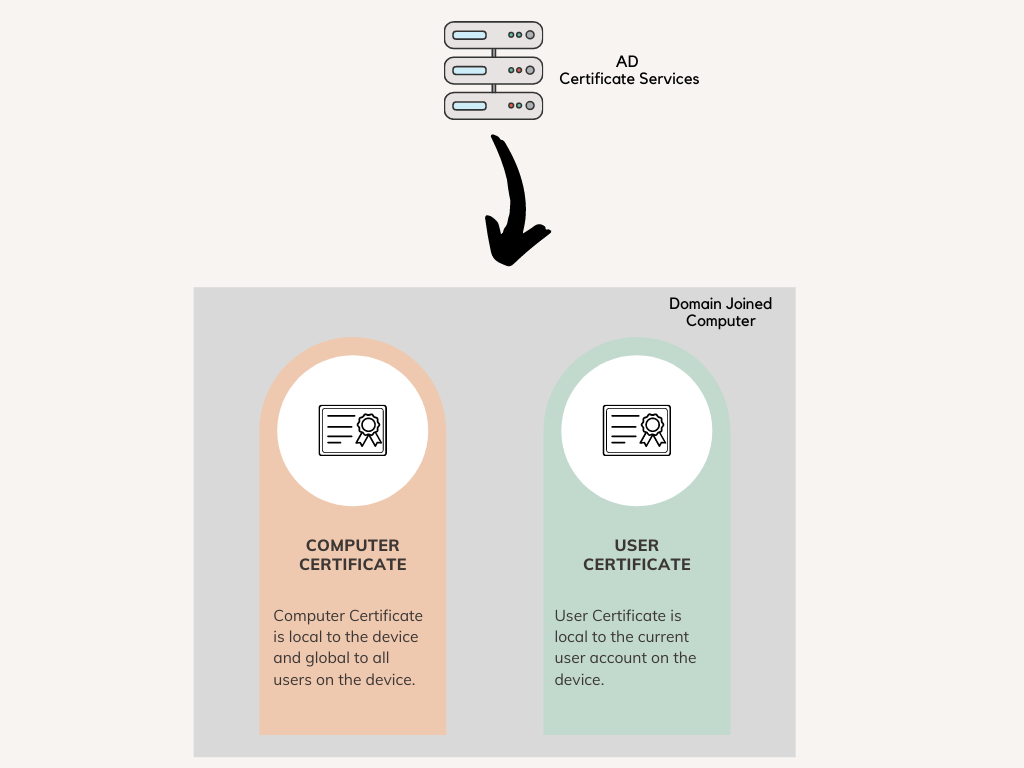
Certificate Authority (CA)
The first step is to configure a certificate template that AD Certification Services (AD CS) uses as the starting point for device certificates that are automatically enrolled and deployed to workstations in the domain.
The below procedure shows how to create a copy of a template, and then configure the newly created template to enable auto-enrollment.
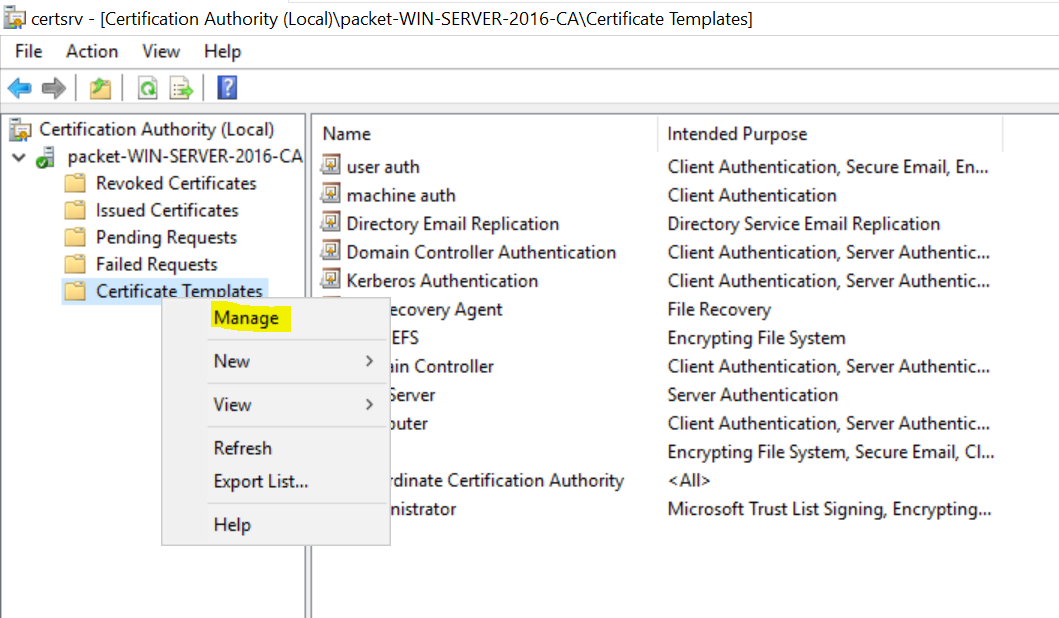
- Navigate to Certificate Authority > Certificate Templates > Manage
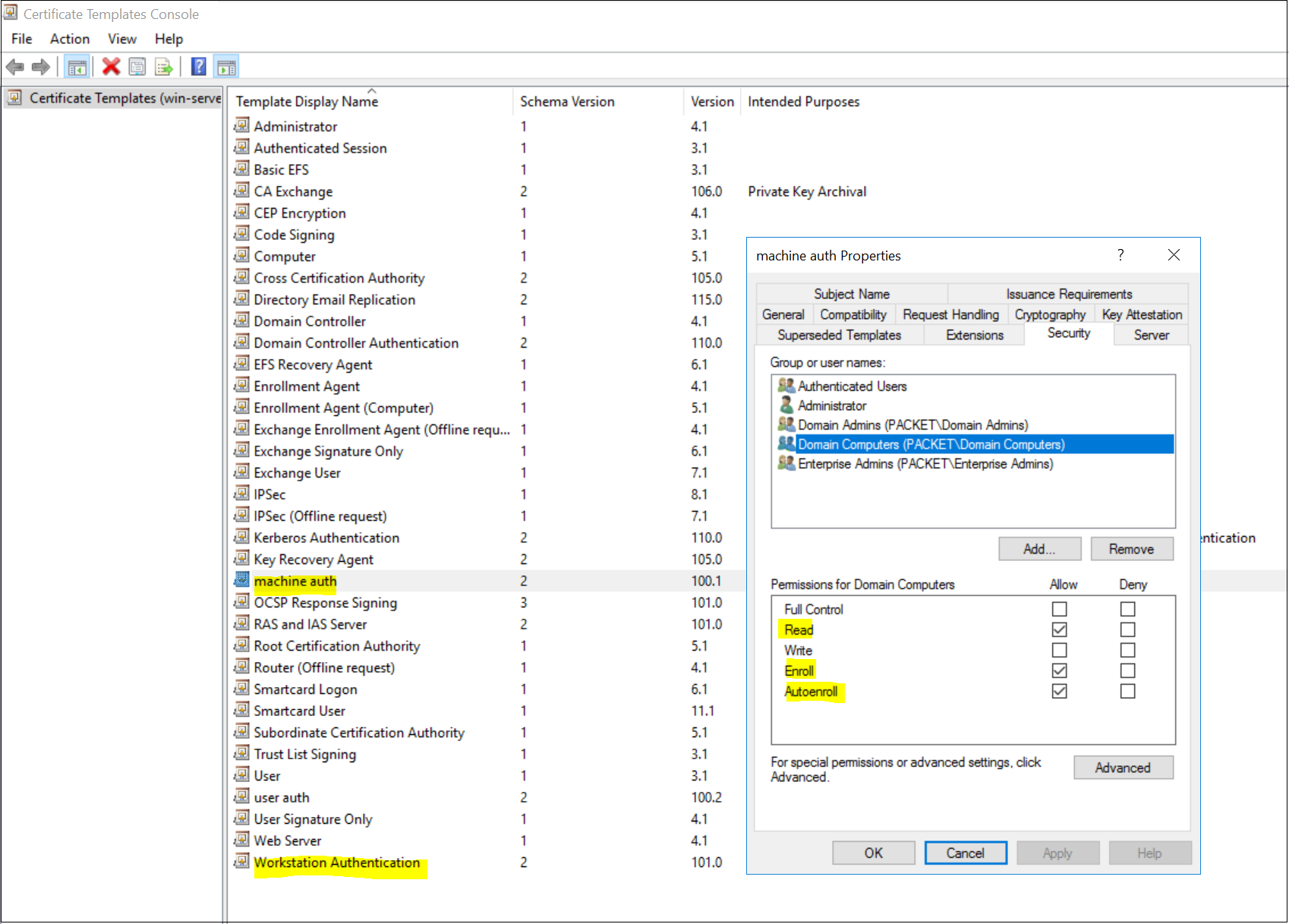
- For machine certificates, duplicate the 'Workstation Authentication' template and give a suitable name ('machine auth' in this example)
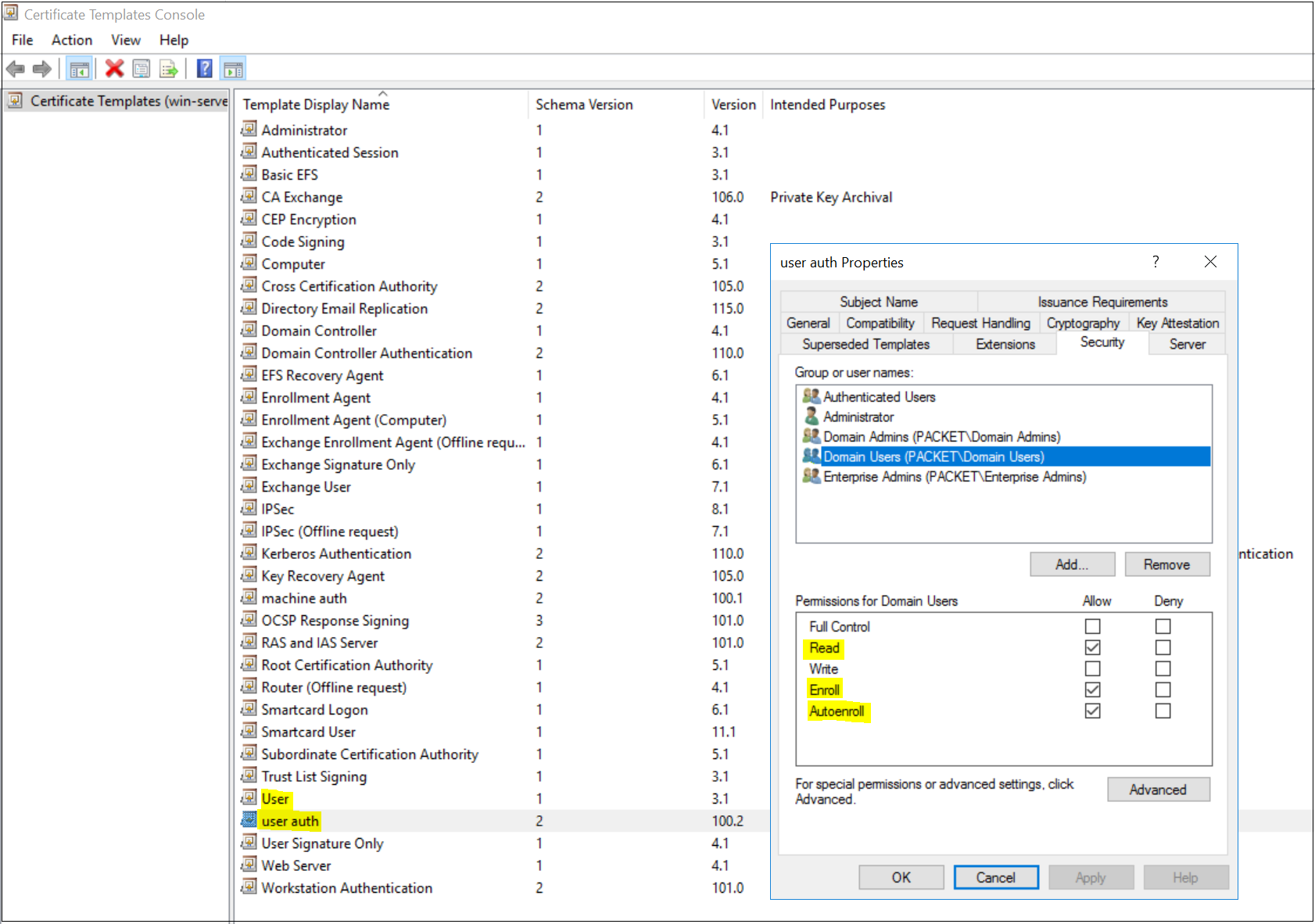
- Under Security tab, Allow Read, Enroll and Autoenroll for 'Domain Computers'
- For user certificates, duplicate the 'User' template and give a suitable name ('user auth' in this example)
- Under Security tab, Allow Read, Enroll and Autoenroll for 'Domain Users'
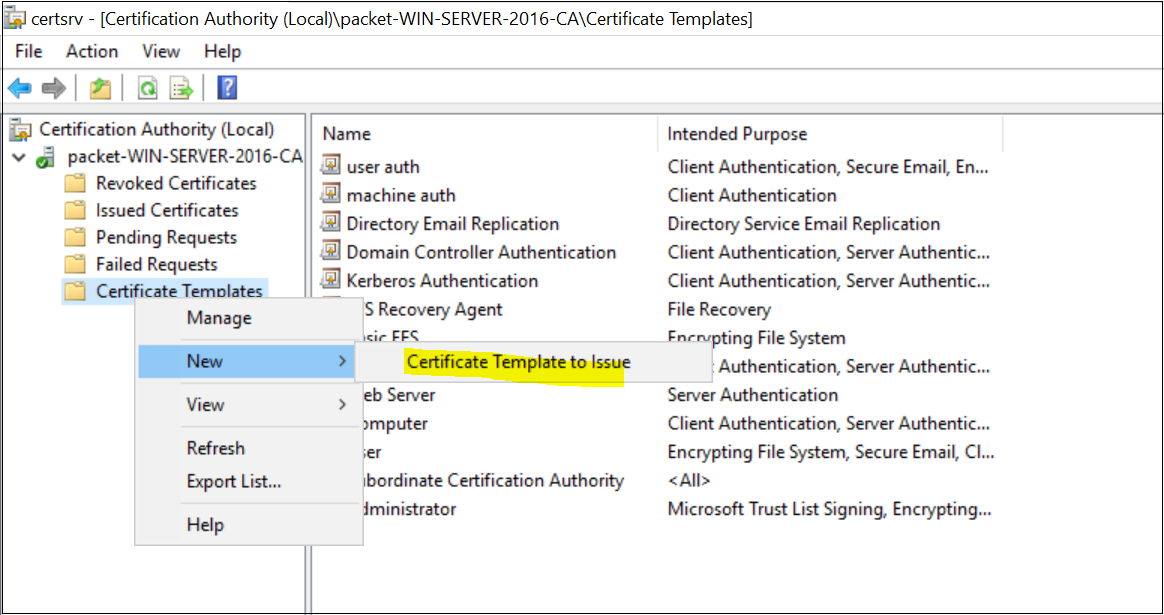
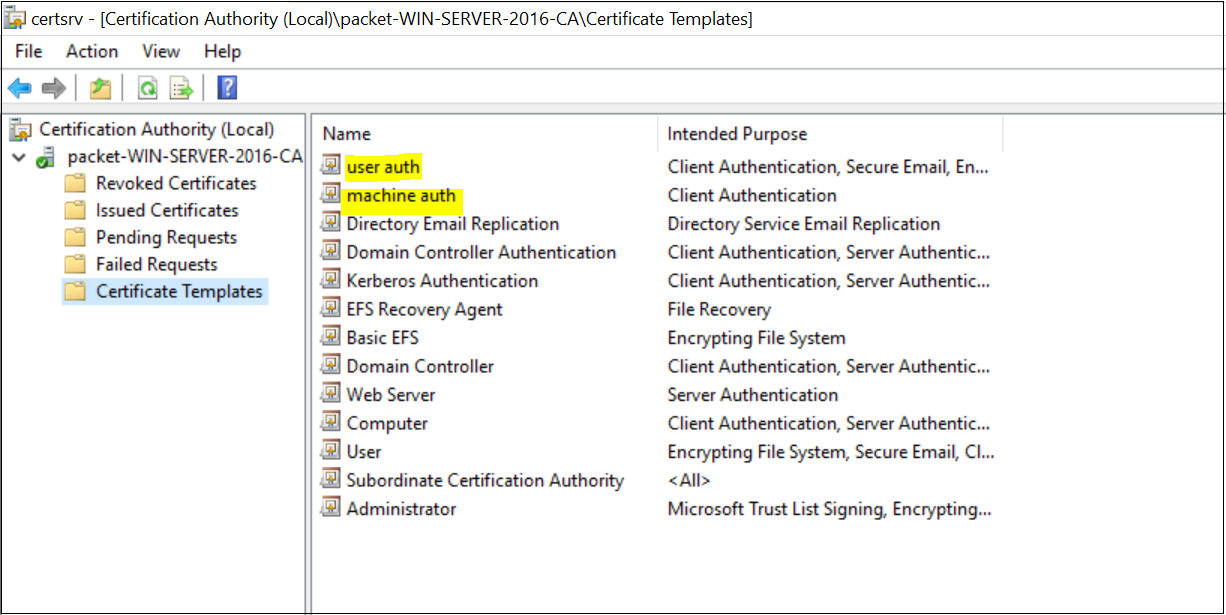
The next step is to Publish the newly created certificate templates as shown below. Once you added the certificates, they are available for enrollment.
Group Policy
You can use Group Policy to automatically enroll both computer and user certificates and deploy them to the workstations.
- Open the Group Policy Management console.
- Edit the GPO that you want to modify (using the Default Domain Policy in this example)
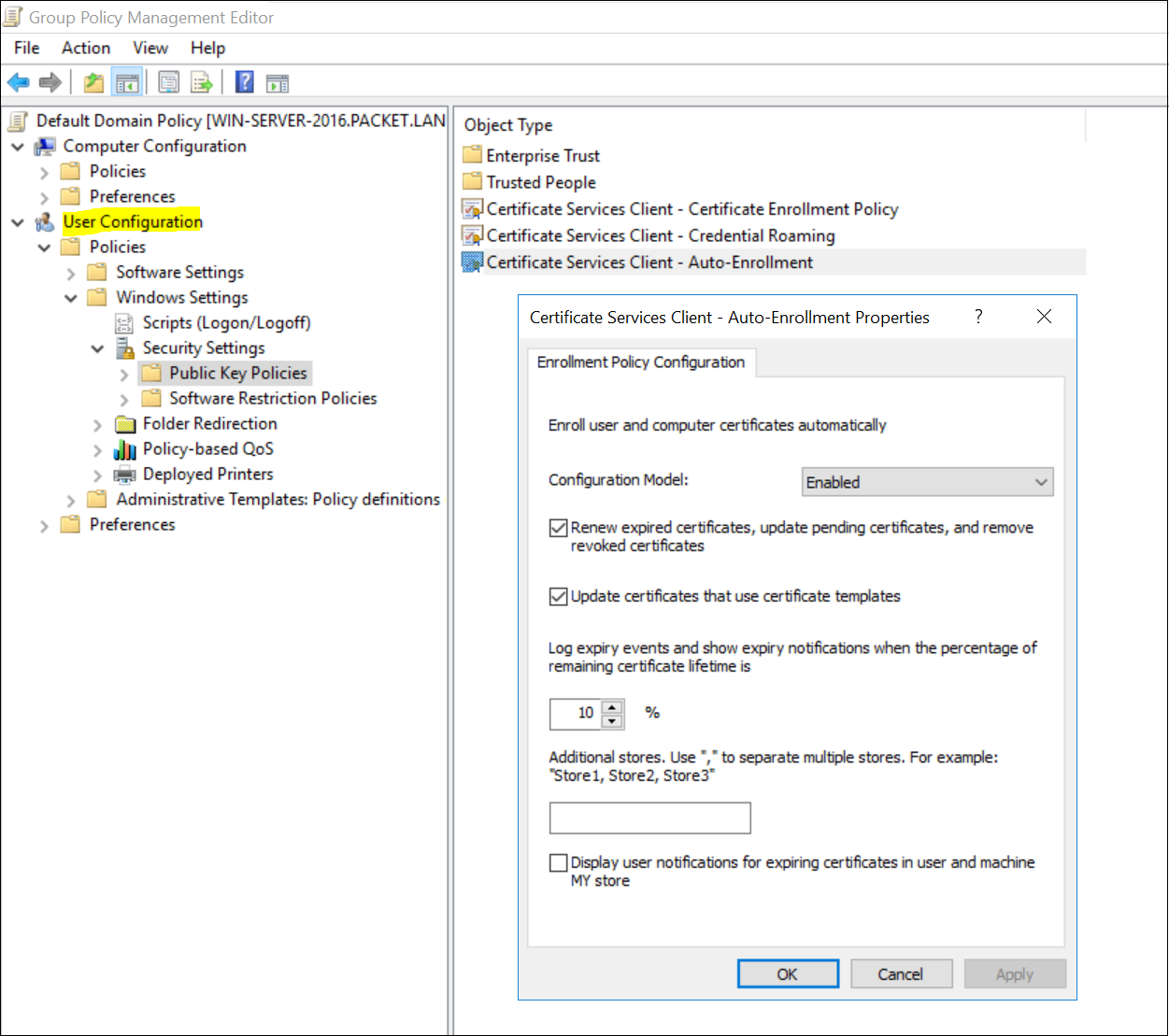
- Navigate to User | Computer Configuration, Policies, Windows Settings, Security Settings, Public Key Policies.
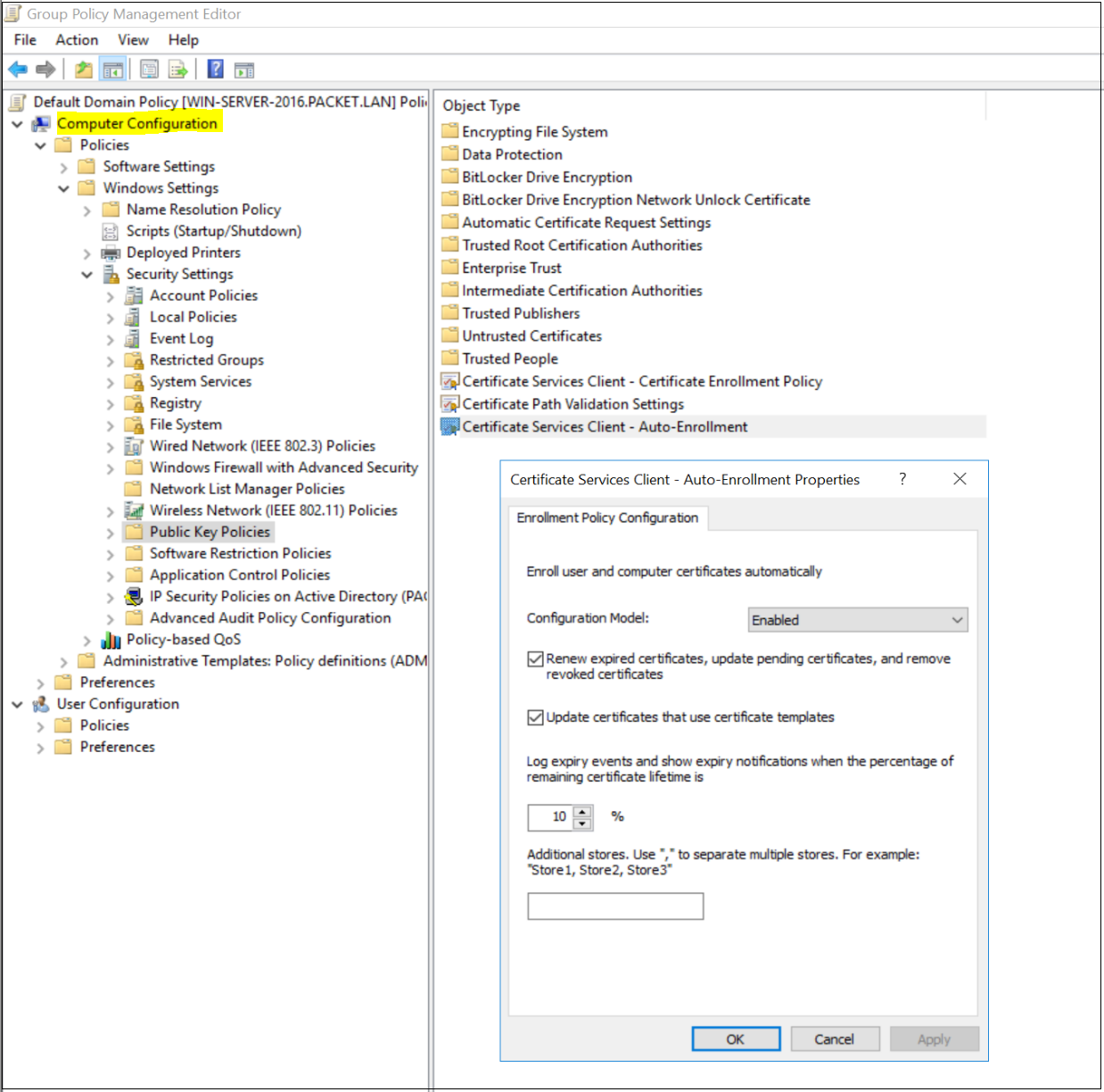
- Double-click Certificate Services Client - Auto-Enrollment.
- Change Configuration Model to Enabled.
- Select both Renew expired certificates and Update certificates that use certificate templates.
- Click OK to save your changes. Workstations apply the GPO and download the certificate the next time Group Policy is refreshed.
Verification
Once all the configurations are completed, you can either reboot your computer or force the GPO update by running gpupdate /force on the command line to receive the certificates. You can view the certificates on the MMC console.
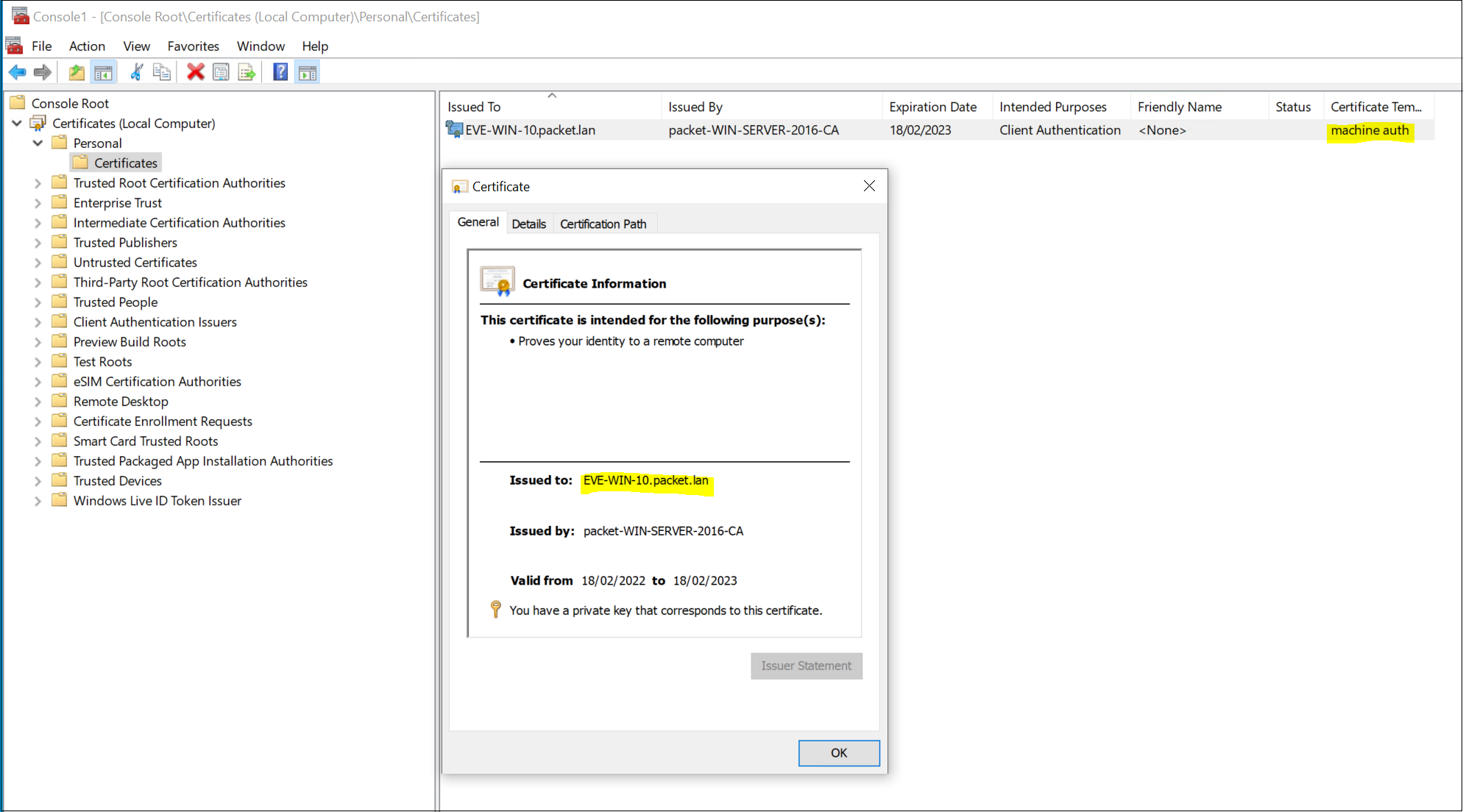
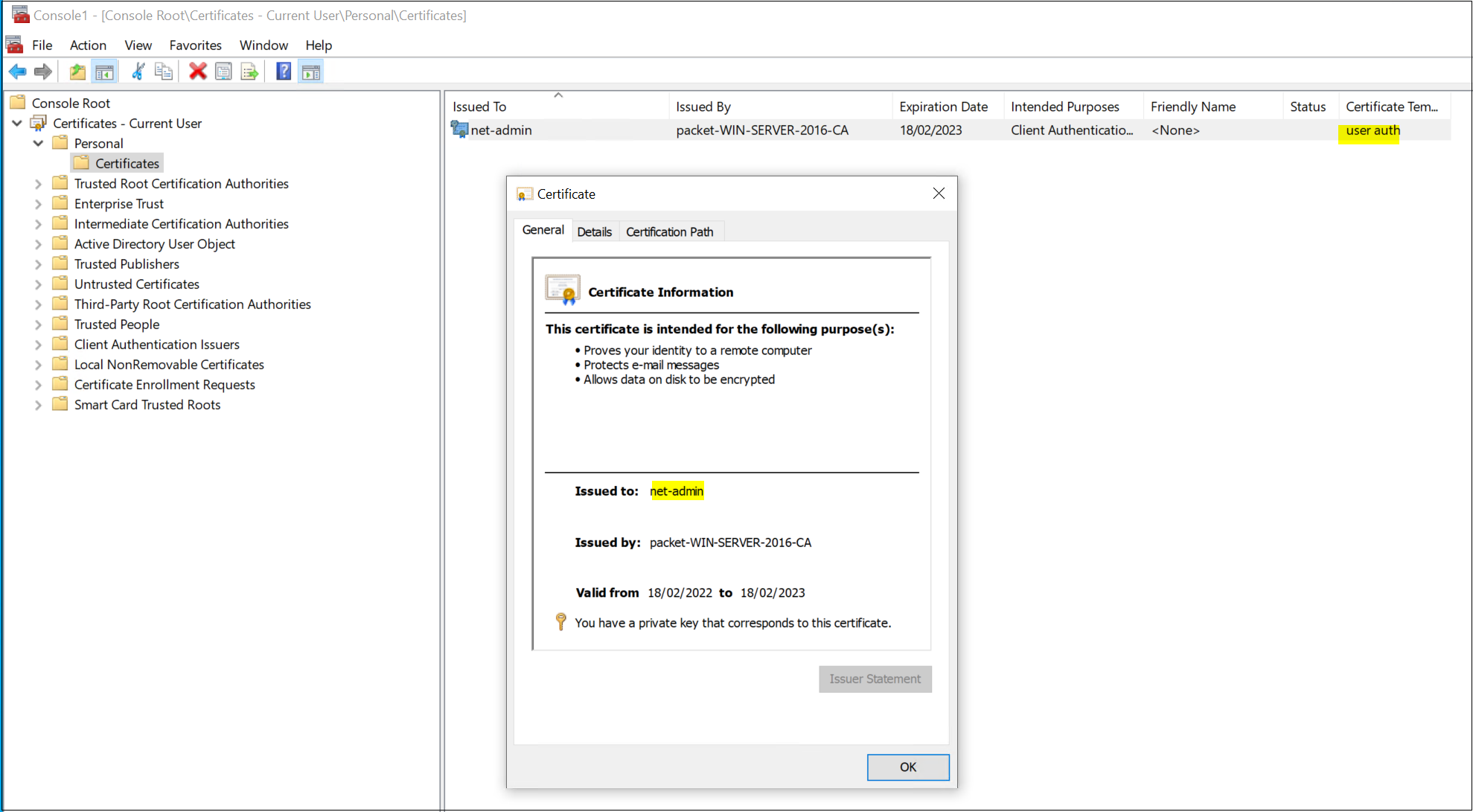
Now we have the certificates in place, we can use them for 802.1x authentications which I will explain in the next post.
If you want to learn more about how to configure 802.1X with ISE, please check out my blog posts here.