In a simpler form, Network Access Control ensures that only users and devices that are authenticated and authorized can enter the corporate network and restrict unauthorized users and devices from gaining access to it.
NAC solutions enable businesses to apply precisely configured access policies when properly implemented. They can track each user's movements within networks and the resources they have access to.
Importance of NAC
NAC is extremely important for ensuring that users have the appropriate authorizations before they access internal resources. In many cases, this is primarily a security concern, ensuring that sensitive and confidential information does not end up in the hands of someone who might use them maliciously or unintentionally.
NAC ensures that every endpoint connected to a network complies with a security state baseline and gives the network admins the option to permit or deny access as necessary.
NAC comes with a number of benefits and some of them are listed here:
- Control the users and devices entering the corporate network.
- Allow contractors, 3rd parties and guests to access the network as required but restrict their access to a minimum.
- Group employees based on their job function and build role-based access policies.
- Gain visibility
What is 802.1X
802.1X is an IEEE standard for port-based network access control that provides secure network access to corporate networks. You cannot secure if you don't know what's on your network. The 802.1X framework functions as a gatekeeper for entry to enterprise networks (wired and wireless).
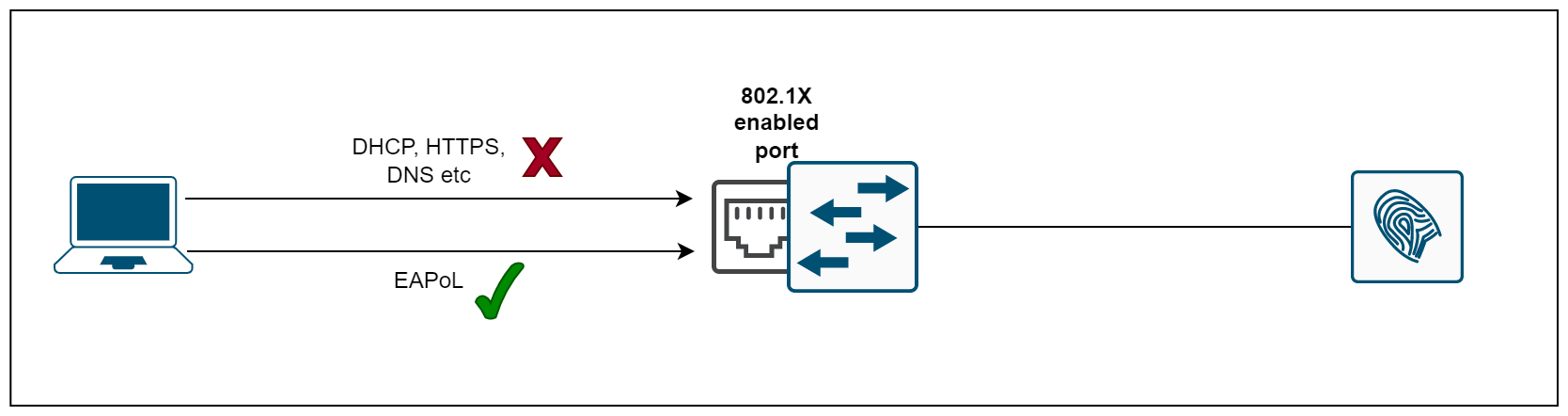
When a user or device wants to gain access to a network, 802.1X acts as a framework that verifies the person/device connecting is who they say they are. When we enable 802.1X on a port, the switch drops all traffic received on that port except EAPoL packets (more on this later). Only after the 802.1X authentication has successfully completed will the switch allow any other traffic on that port.
Are NAC and 802.1X the same?
I often see that both terms are being used interchangeably but they are fundamentally different. NAC offers much more than just authenticating devices into the corporate network using 802.1X.
Various vendors offer various NAC solutions that not only authenticate
a user/device but also scan them for threats and ensure that it complies with security policies before it is allowed into the network. Some NAC solutions even
perform authentication without needing an 802.1X solution by having agents on the client machines.
Back to 802.1X
Now that we understand the correlation between NAC and 802.1X, let's focus on the different components that make 802.1X work.
The Components of 802.1X
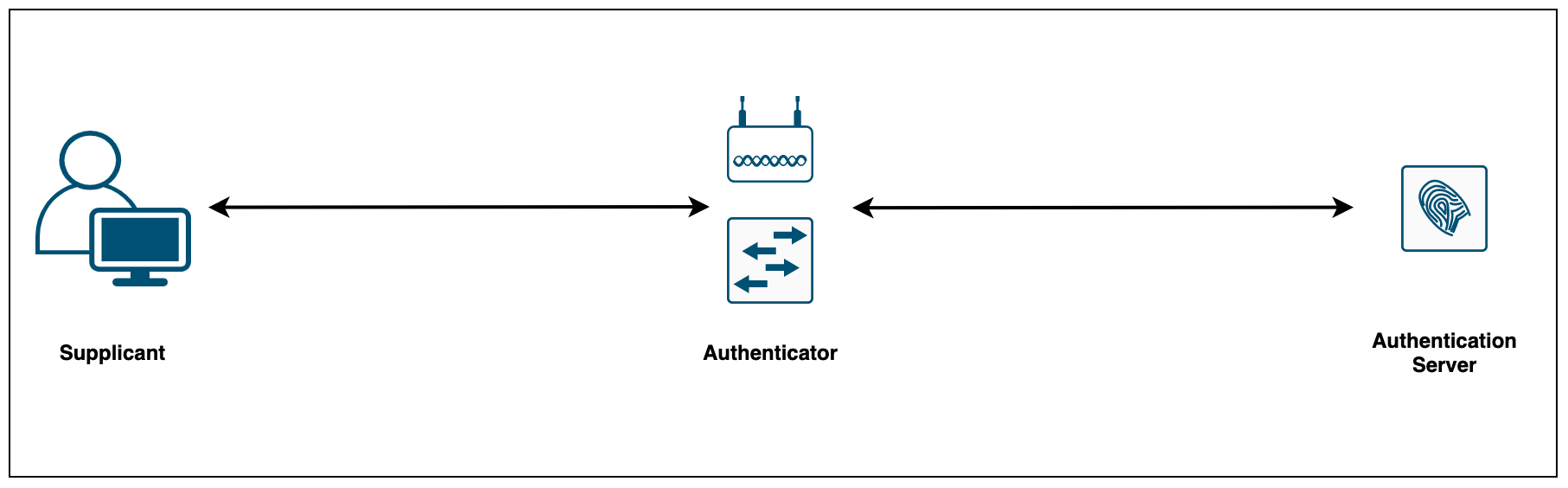
802.1X consists of three components:
- The supplicant (laptop, printer, phone etc) is the device attempting to gain access to the network. The supplicant communicates with the authenticator via 802.1X-encapsulated EAP packets
- The authenticator (Switch or AP) is the gatekeeper to the network and permits or denies access to the supplicants. The authenticator acts as an intermediary (proxy) between the supplicant and the authentication server. The authenticator requests identity information (credentials/certificates) from the supplicant via EAP packets, verifies that information with the authentication server and then relays a response to the supplicant (access permit or deny)
- The authentication server (Cisco ISE or ClearPass) performs the actual authentication of the supplicant. By examining the information in the encapsulated EAP messages relayed from the authenticator, the authentication server validates the identity of the supplicant and responds back to the authenticator whether or not the supplicant is authorized to access the network.
802.1X and EAP
When authenticating users or devices to the network, 802.1X must provide secure ways to send across the user/device credentials. 802.1X uses the Extensible Authentication Protocol (EAP) to exchange messages during the authentication process.
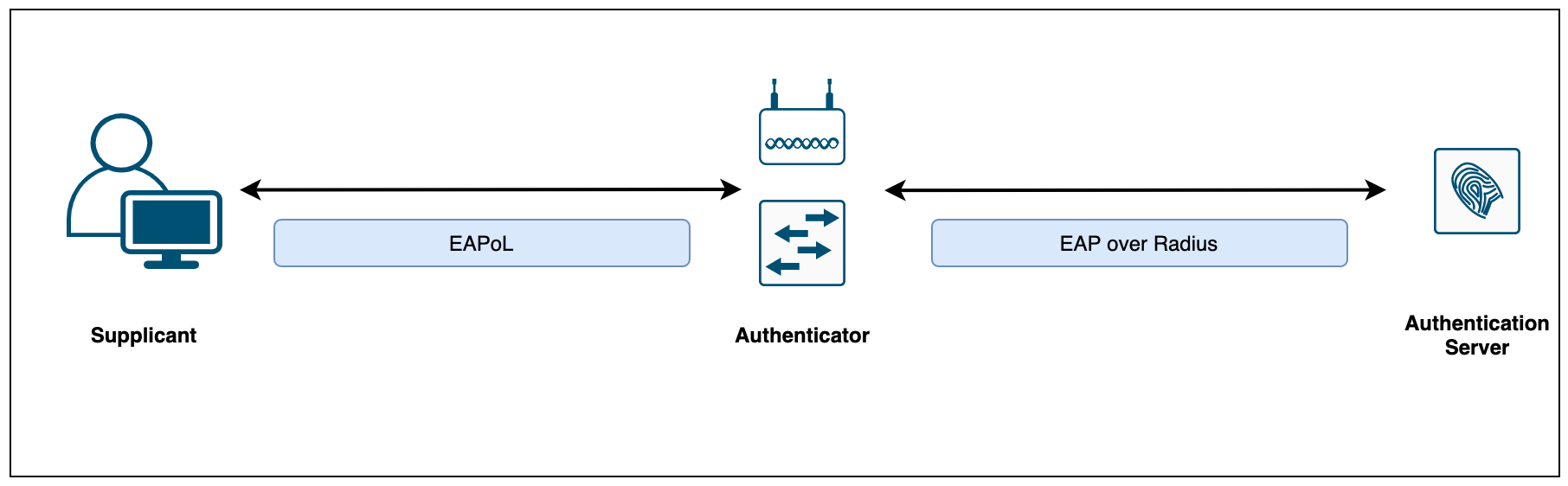
The 802.1X encapsulation between the supplicant and authenticator is referred to as EAP over LAN (EAPoL). The authenticator in turn relays the EAP information to the authentication server using Radius (EAP over RADIUS)
There are many authentication protocols that operate inside the 802.1x framework but the ones used more frequently for 802.1X wired and wireless authentication include EAP-TLS, EAP-PEAP, EAP-FAST and the newcomer TEAP.
Choosing an EAP Method
When deploying 802.1X, it is important to choose an EAP method that meets your organization’s security standards. Choosing which EAP method to use is one of the most important decisions because different EAP methods offer differing levels of security and complexity.
Which EAP type to implement solely depends on the level of security that the organization requires and the administrative overhead. If you are looking for a higher level of security, EAP-TLS is the best choice, providing the strongest authentication method using client and server-side certificates. EAP-PEAP or EAP-FAST on the other hand also offers very good security which uses credentials and only server-side certificates.
Even though there are many EAP types available, I've listed the most popular ones.
- EAP-TLS relies on client-side and server-side certificates to perform mutual authentication. This is considered one of the strongest EAP types however, it requires each and every client to have a certificate pre-installed.
- EAP-PEAP requires only server-side certificates for the client to authenticate the authentication server. PEAP is known as a tunnelled EAP type because it first establishes an outer tunnel using TLS and then sends the credentials via an inner tunnel. The inner tunnel can be virtually any EAP type but the widely used inner method is MSCHAPV2.
- EAP-FAST is very similar to PEAP, it first establishes an outer TLS tunnel. Inside this encrypted tunnel, a secondary inner EAP method (such as MSCHAPv2) is used to authenticate the user.
Mac Authentication Bypass (MAB)
Now imagine a scenario where you are planning on deploying 802.1X authentication across your enterprise but some of the legacy devices such as printers, CCTV cameras, and voice phones don't support 802.1X. Remember, once you enabled 802.1X on a switch port, the clients must be authenticated before gain access to the network. How can they gain access to the network if they don't support/understand 802.1X?
MAB solves this problem by sending the device's Mac address as the username and password to the authentication server. The authentication server verifies the Mac address and sends a response back to the authenticator. We need to ensure that the Mac address has been added to the authentication server beforehand.
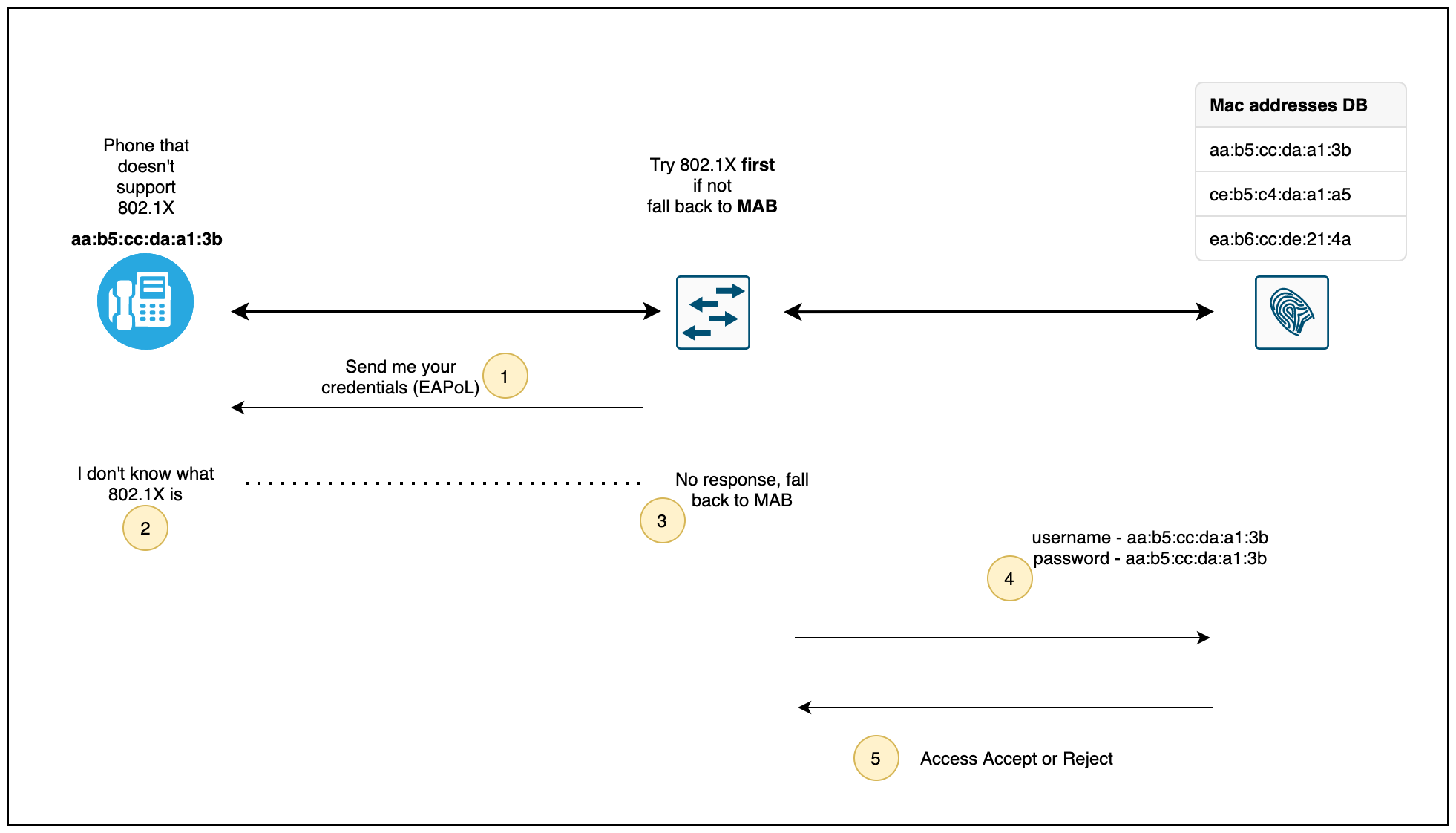
As you can see above, when the phone is connected to a switch port, the switch sends EAPoL packets to the phone but there is no response from the phone. The switch then falls back to using MAB on that port by sending the Mac address of the phone to the Authentication server. The authentication server will check against its policies to ensure that the device is already known and then send an Access-Accept or Access-Reject message back to the switch.
As you may already assume, MAB is not as secure as 802.1X because anyone can spoof that Mac address and connect their own device to the switch and gain access to the network. There is also Admin overhead involved as we need to add the Mac addresses of all the non-802.1X compliant devices to the authentication server beforehand.
Closing up
I think this is the longest post I've written in a while. I hope this post has given you a better understanding of various terms used within the NAC solution. Please let me know in the comments should you have any questions.
If you want to learn more about how to configure 802.1X with ISE, please check out my blog posts here.