Recently, I was helping a friend with his FortiGate deployment. One of the tasks we tackled was setting up load-balancing across Dual ISPs using FortiGate's built-in SD-WAN feature. In this blog post, we'll walk you through how we did it, step by step. So if you're dealing with dual internet providers and need to keep your connection smooth and steady, keep reading - this might be just what you need.
Overview
In this guide, we're aiming to use both of our internet connections (WAN1 and WAN2) at the same time. This way, we can spread our internet traffic across both connections, making our internet use more efficient. But we're not stopping there. We also want to keep an eye on both connections to make sure they're working well by using SLAs.
If one of our internet connections starts having problems, we want to be able to switch all our internet traffic to the other, healthier connection. This way, we can keep our internet running smoothly, even if one of our connections isn't at its best.
WAN Interface Configurations
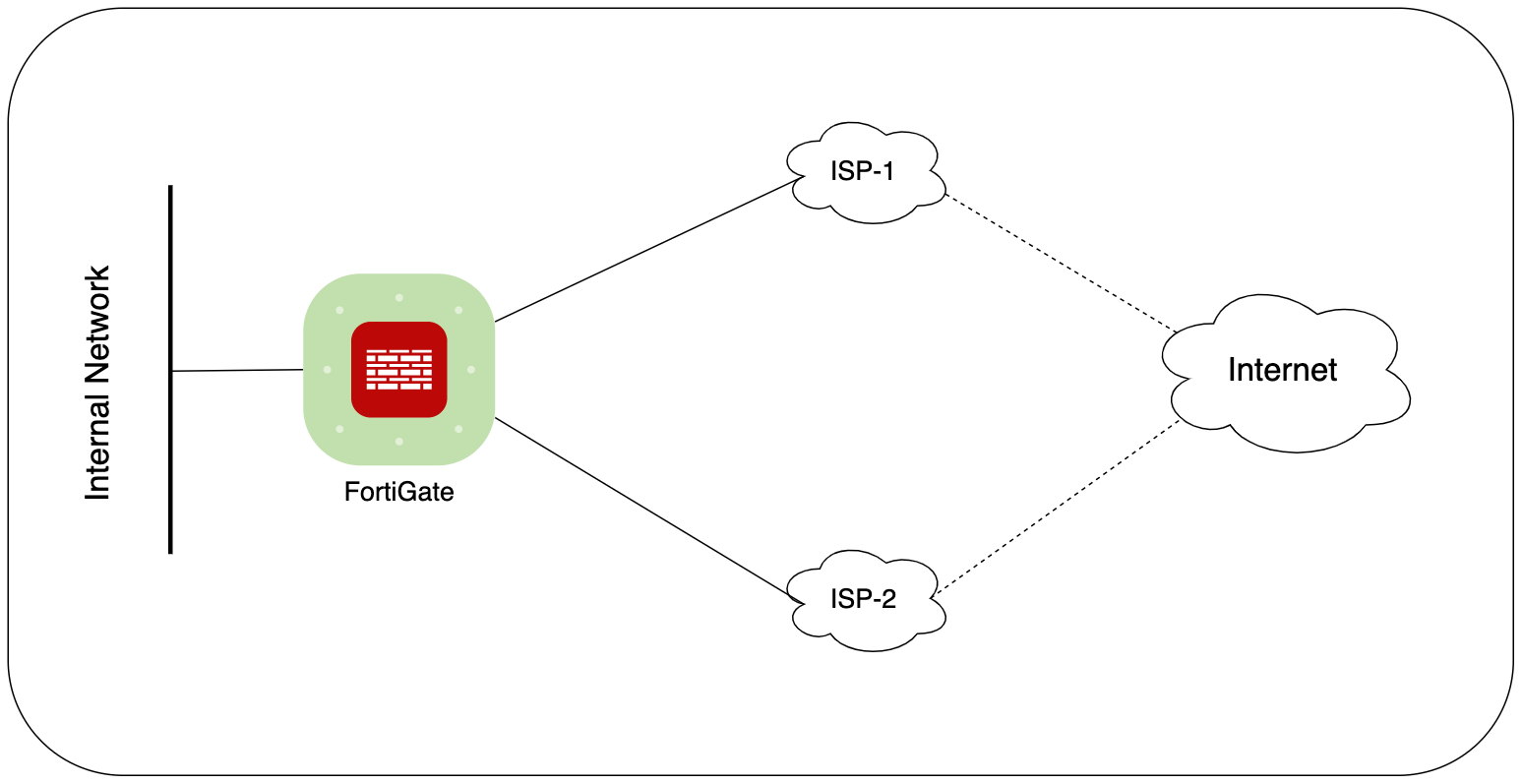
In our FortiGate Dual ISP SD-WAN configuration example, we begin with the configuration of two WAN interfaces, WAN1 and WAN2, which are connected to our ISPs. For this guide, we'll assume that the WAN IPs are received via DHCP from the ISPs.
However, the process remains the same even if you're configuring IPs manually. The initial step involves physically connecting both WAN1 and WAN2 ports to the ISPs. Once these connections are in place, the FortiGate firewall will automatically receive the IP addresses from the ISPs.
SD-WAN Members and Zones
In the realm of SD-WAN configuration, the concepts of 'members' and 'zones' play a crucial role. Essentially, SD-WAN works by bundling interfaces together into what we call 'zones'. Once we've defined our SD-WAN members aka the interfaces, we can assign them to a zone. Zones are incredibly useful because they can be used in policies as source and destination interfaces, in static routes, and in SD-WAN rules. In a nutshell, SD-WAN zones are primarily used to logically group multiple interfaces, in our case WAN1 and WAN2 will be added to the default zone called virtual-wan-link
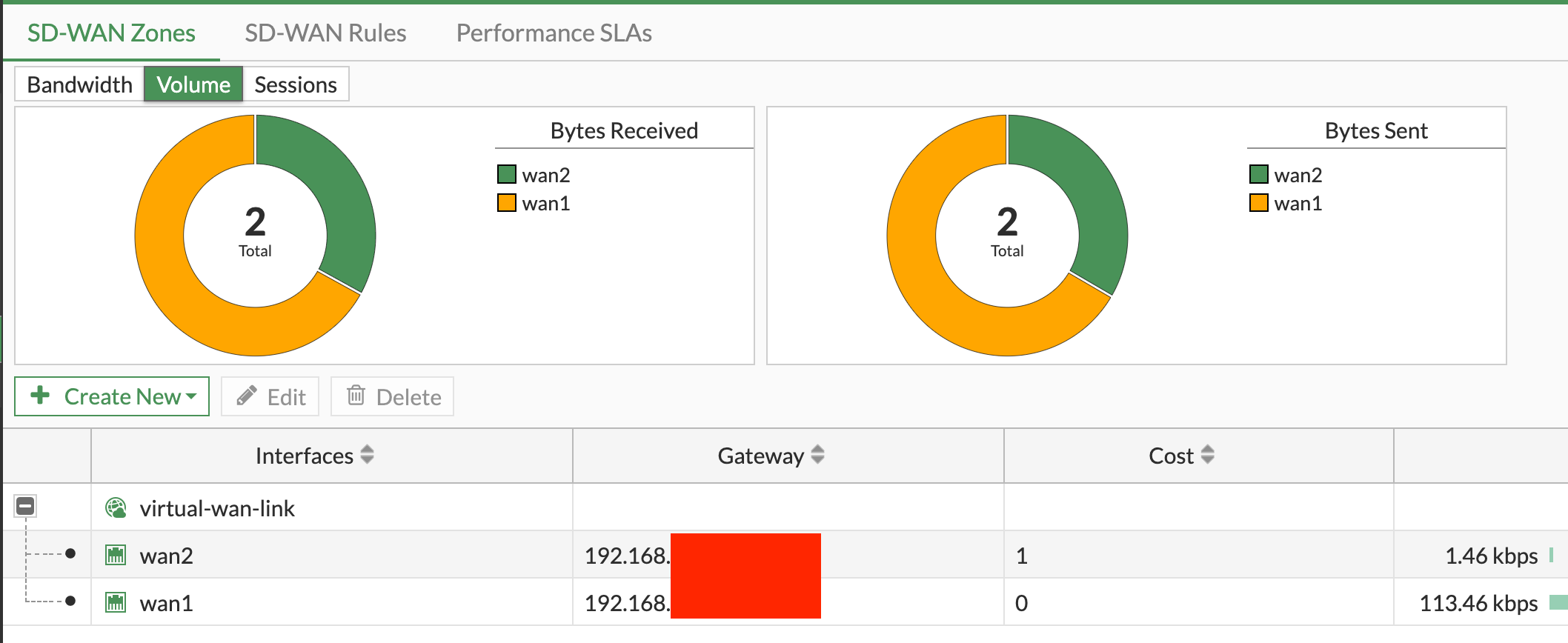
When starting with your SD-WAN configuration, there are a couple of things you need to keep in mind. If a port is being referenced elsewhere in your settings, it won't appear when you try to create an SD-WAN member. For instance, right out of the box, there's a default policy that references the WAN1 interface. To create a member with WAN1, you'll need to remove that policy first.
Another point to remember is that if a port is physically down or not connected, it won't show up when you're setting up your SD-WAN. So, before you start, make sure all your connections are up and running.
Performance SLA
Performance SLAs are like our internet connection's health check-up. They help us understand how well our internet links are working. These checks are done by sending signals through each link to a destination host, 8.8.8.8 for example.
The health of our links is measured based on three things: latency (how long it takes for data to travel), jitter (how much the latency varies), and packet loss (how much data is lost during transmission).
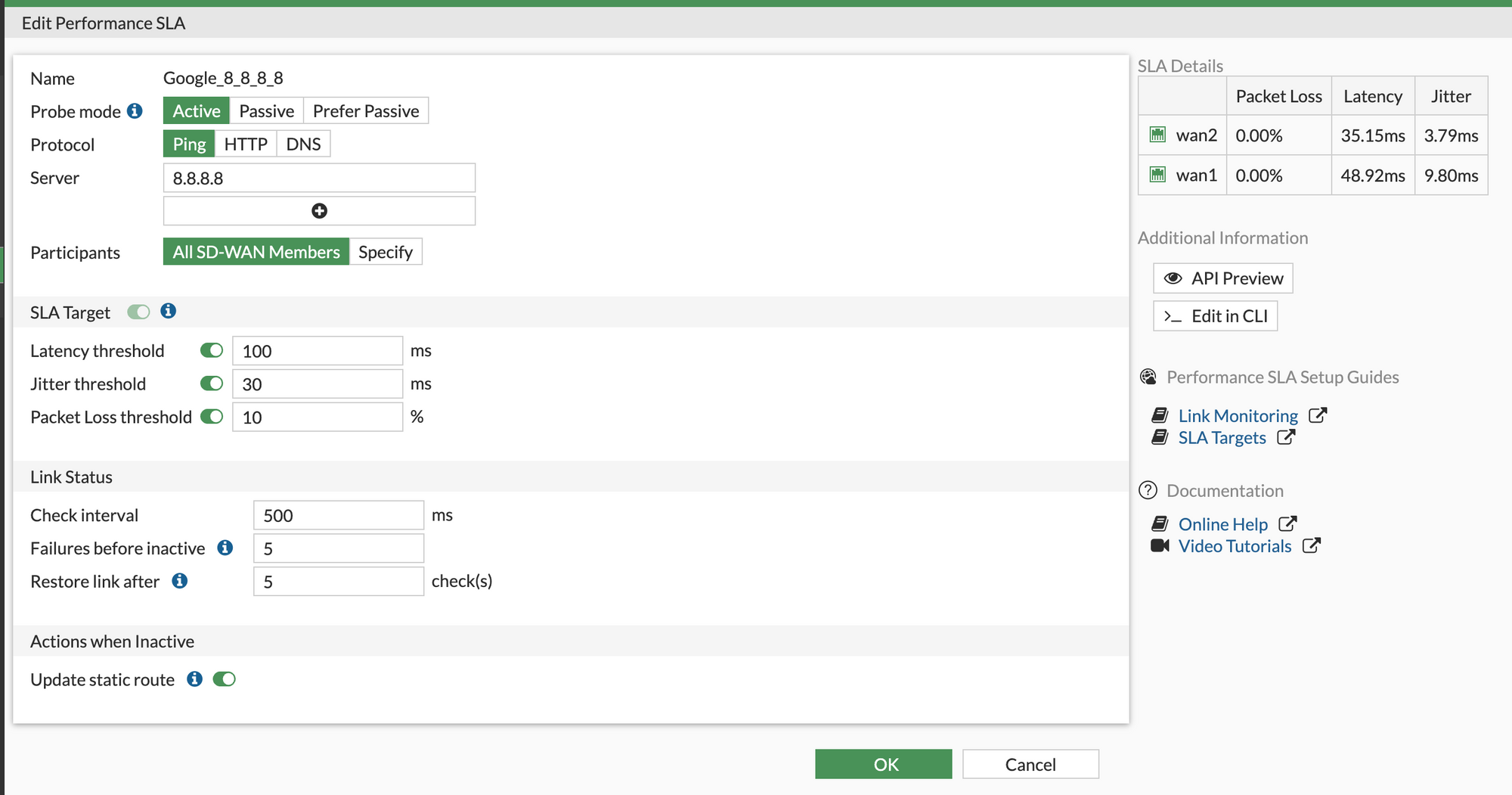
If a link fails these health checks, it's removed from the group of links that are being used to balance our internet traffic. This means that our traffic will be sent through the other, healthier links. But if a link starts passing the health checks again, it's added back into the group. This way, we avoid sending traffic to a broken link where it could get lost, ensuring our internet connection stays smooth and reliable.
SD-WAN Rules
SD-WAN rules are used to control how sessions are distributed to SD-WAN members. Rules can be configured in one of five modes.
auto: Interfaces are assigned a priority based on quality.- Manual (
manual): Interfaces are manually assigned a priority. - Best Quality (
priority): Interface are assigned a priority based on the link-cost-factor of the interface. - Lowest Cost (SLA) (
sla): Interfaces are assigned a priority based on selected SLA settings. - Maximize Bandwith (SLA) (
load-balance): Traffic is distributed among all available links based on the selected load-balancing algorithm.
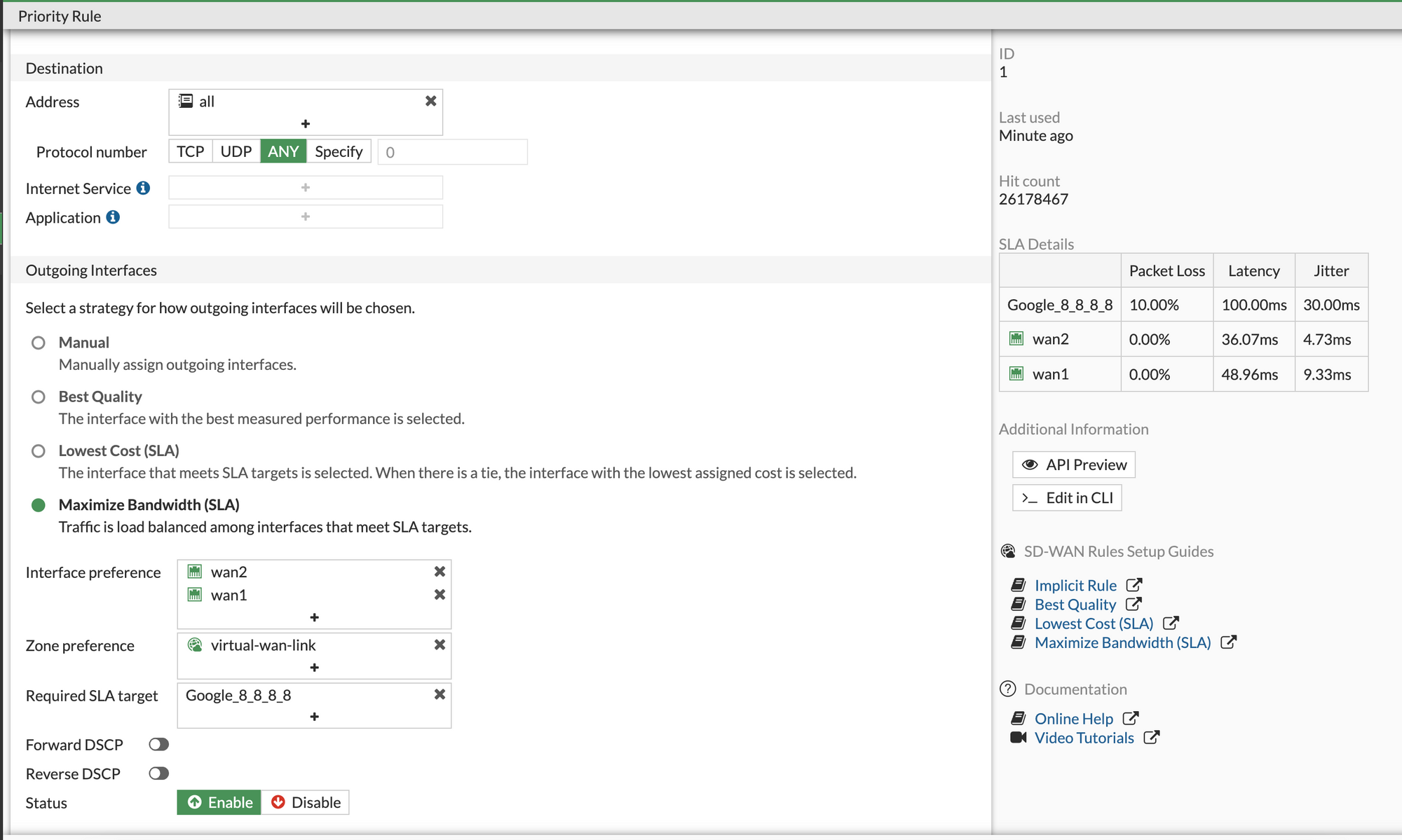
For our example, we are going to use the last option - Maximize Bandwith (SLA). When using Maximize Bandwidth mode, SD-WAN will use all of the links that satisfy the configured SLA to forward traffic based on a round‑robin load balancing algorithm.
Static Route and Policies
Finally, add a static default route that points to the SD-WAN zone virtual-wan-link
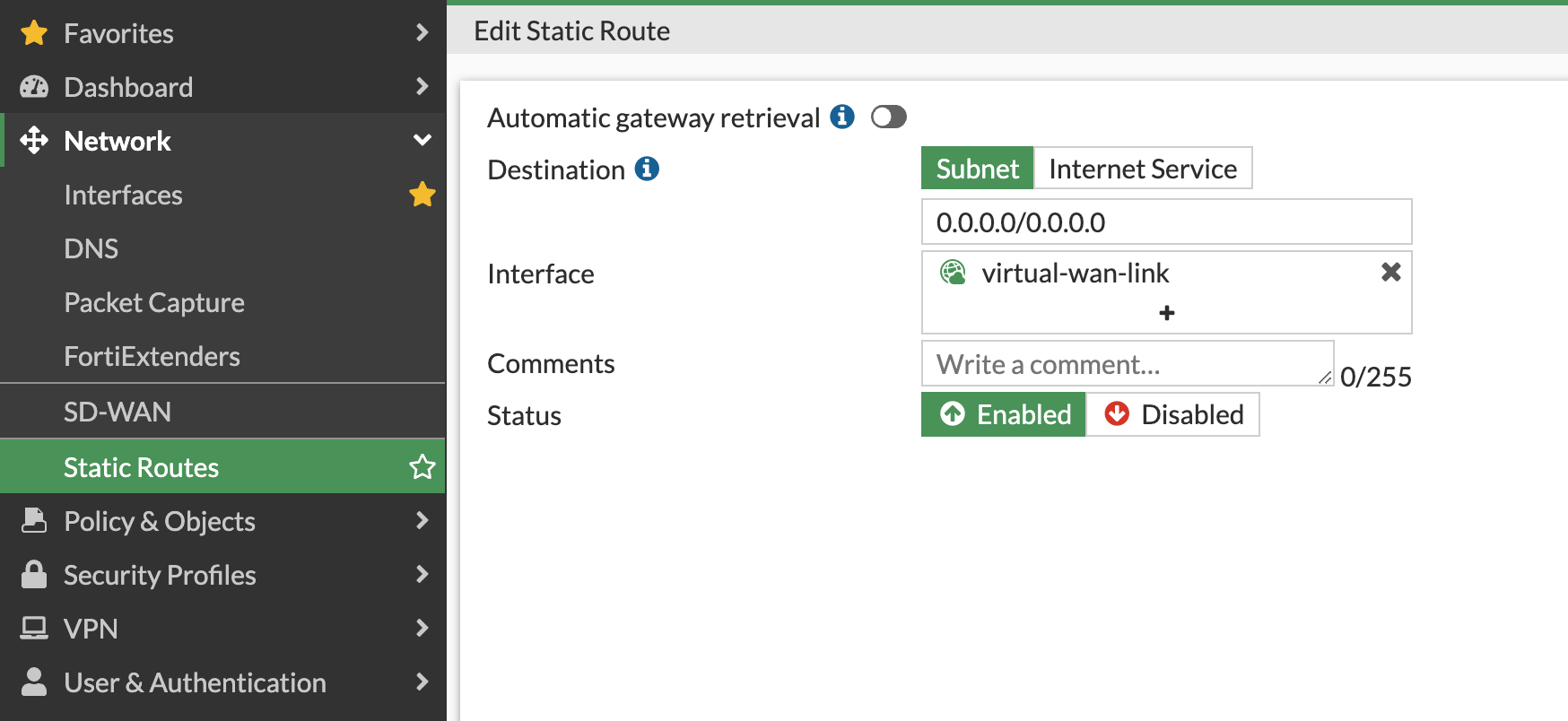
When you create firewall policies, please ensure that the virtual-wan-link is used as the Outgoing Interface.
Closing Up
In conclusion, setting up a dual ISP SD-WAN configuration on a FortiGate firewall is very straightforward and intuitive. Please let me know in the comments if you have any questions or concerns.