In this blog post, let's look at a common scenario where users face two MFA prompts when trying to connect to Global Protect VPN. Typically, this happens because MFA has been set up for both the portal and the gateway.
When a user connects to GP, the user first logs into the portal and completes the MFA, then, they automatically attempt to connect to the gateway, which triggers another prompt. We'll look at how to prevent two MFA prompts using authentication cookies, so the user only needs to complete the MFA once.
Global Protect Cookie Authentication
Cookie authentication simplifies the authentication process for users because they will no longer be required to log in to both the portal and the gateway in succession or complete multiple MFAs to authenticate to each. This improves the user experience by minimizing the number of times the users enter credentials.
To keep things simple, when a user logs into Global Protect, we can configure it to generate a 'cookie.' This cookie allows the user to re-authenticate automatically without having to re-enter their credentials or go through MFA again. It's similar to how web browsers remember your login details for websites; once you're logged in, you can return to the site without having to sign in every single time.
You can configure cookie authentication independently for the portal and for gateways. After the portal or gateways deploy an authentication cookie to the endpoint, the portal and gateways both rely on the same cookie to authenticate the user. When the app presents the cookie, the portal or gateway evaluates whether the cookie is valid based on the configured cookie lifetime. If the cookie expires, GlobalProtect automatically prompts the user to authenticate with the portal or gateway. When authentication is successful, the portal or gateway issues the replacement authentication cookie to the endpoint, and the validity period starts over.
Prevent Multiple MFA Prompts
To prevent getting prompted multiple times for MFA, here’s what you do. Configure the portal to generate a cookie whenever a user logs in. And then configure the gateway to accept these cookies.
You can also set a ‘cookie lifetime’ to ensure it only accepts cookies that were recently generated say within the last 5 minutes.
Portal Configuration
- Navigate to Network > Portal and select the portal you want to modify.
- Navigate to the Agent tab and select the 'agent' config.
- Under the 'Authentication Override' section, tick the first box 'Generate cookie for authentication override'
- Select the certificate to Encrypt/Decrypt the cookies. You need to use the same certificate for both the portal and gateway.
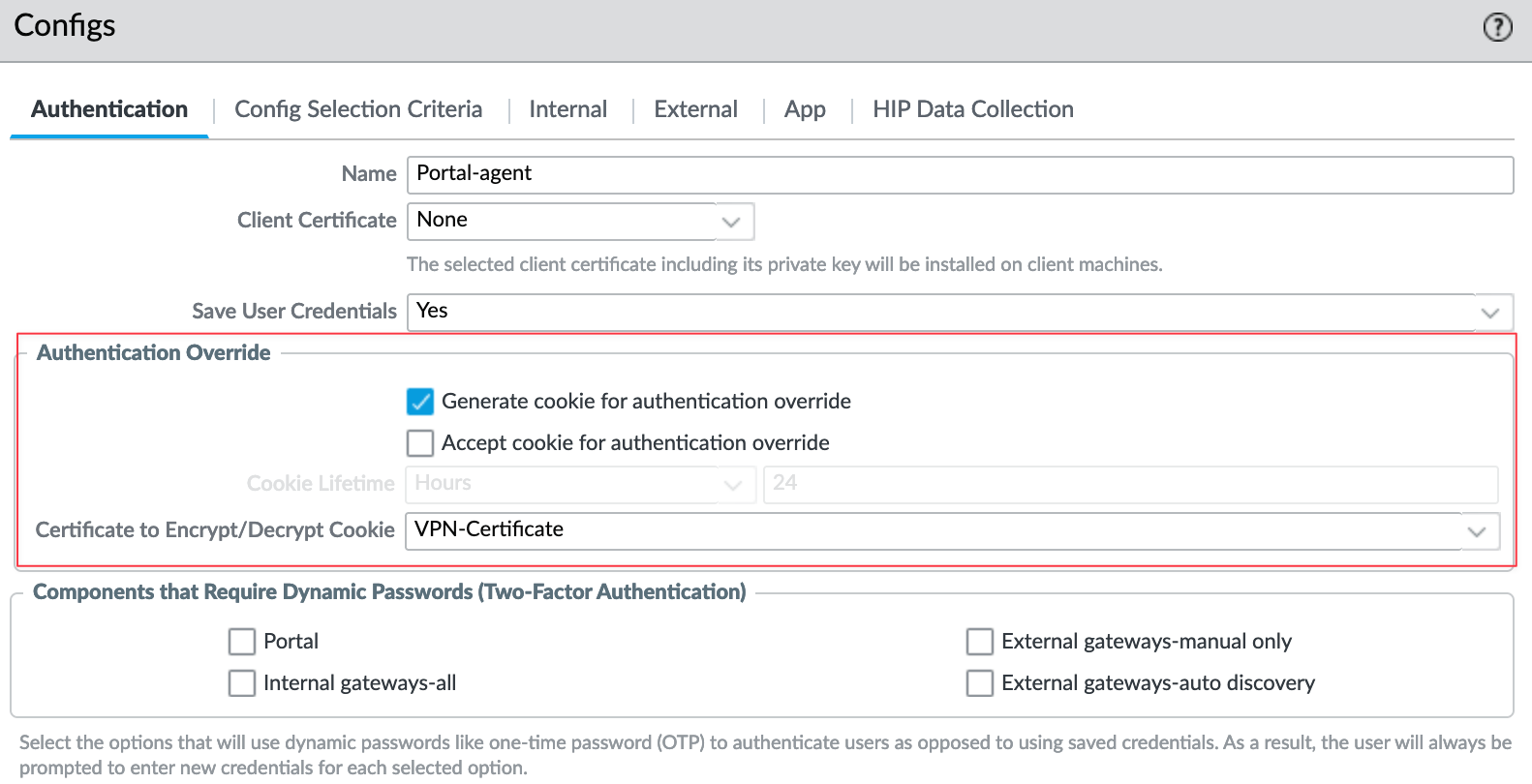
Gateway Configuration
- Navigate to Network > Gateway and select the gateway you want to modify.
- Navigate to Agent > Client Settings tab and select the config.
- Under the 'Authentication Override' section, tick the second box 'Accept cookie for authentication override'
- Select the certificate to Encrypt/Decrypt the cookies. You need to use the same certificate for both the portal and gateway.
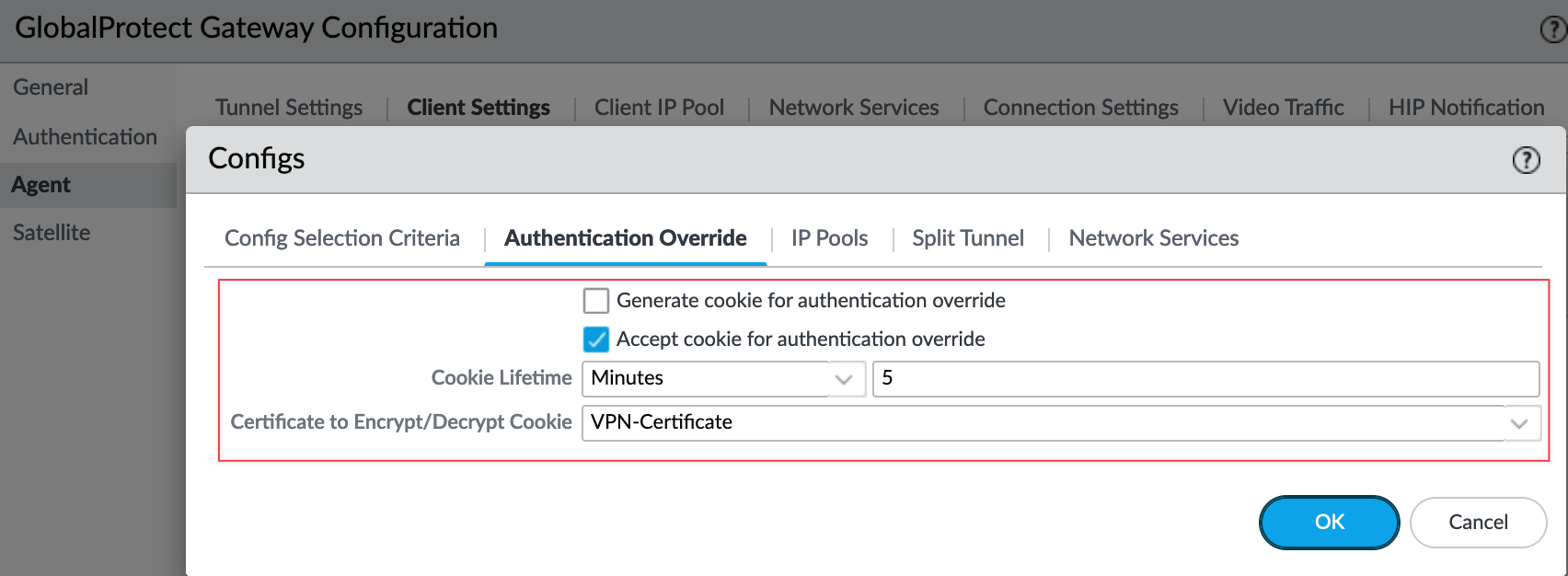
To see how this works, let's assume Bob connects to Global Protect. First, it connects to the portal, so Bob needs to enter his credentials and complete the MFA. Once this is completed, it generates a cookie. Global Protect then connects to the gateway, but because we configured the gateway to accept cookies generated within the last 5 minutes, Bob doesn't need to do anything further. It just connects.
What Happens When You Reconnect?
Now, let’s consider what happens if Bob disconnects from the VPN and tries to reconnect. Typically, he would have to enter his credentials and complete the MFA prompt again. But what if we don’t want Bob to have to re-enter his credentials if he reconnects within, say, 8 hours? For instance, if Bob goes to lunch and disconnects the VPN, when he comes back and reconnects, we want it to just connect.
To make this happen, we can configure the portal to accept the cookies for 8 hours. While we could also set the gateway to generate cookies, setting up the portal this way should work just fine and keep things simple for Bob when he reconnects after short breaks.
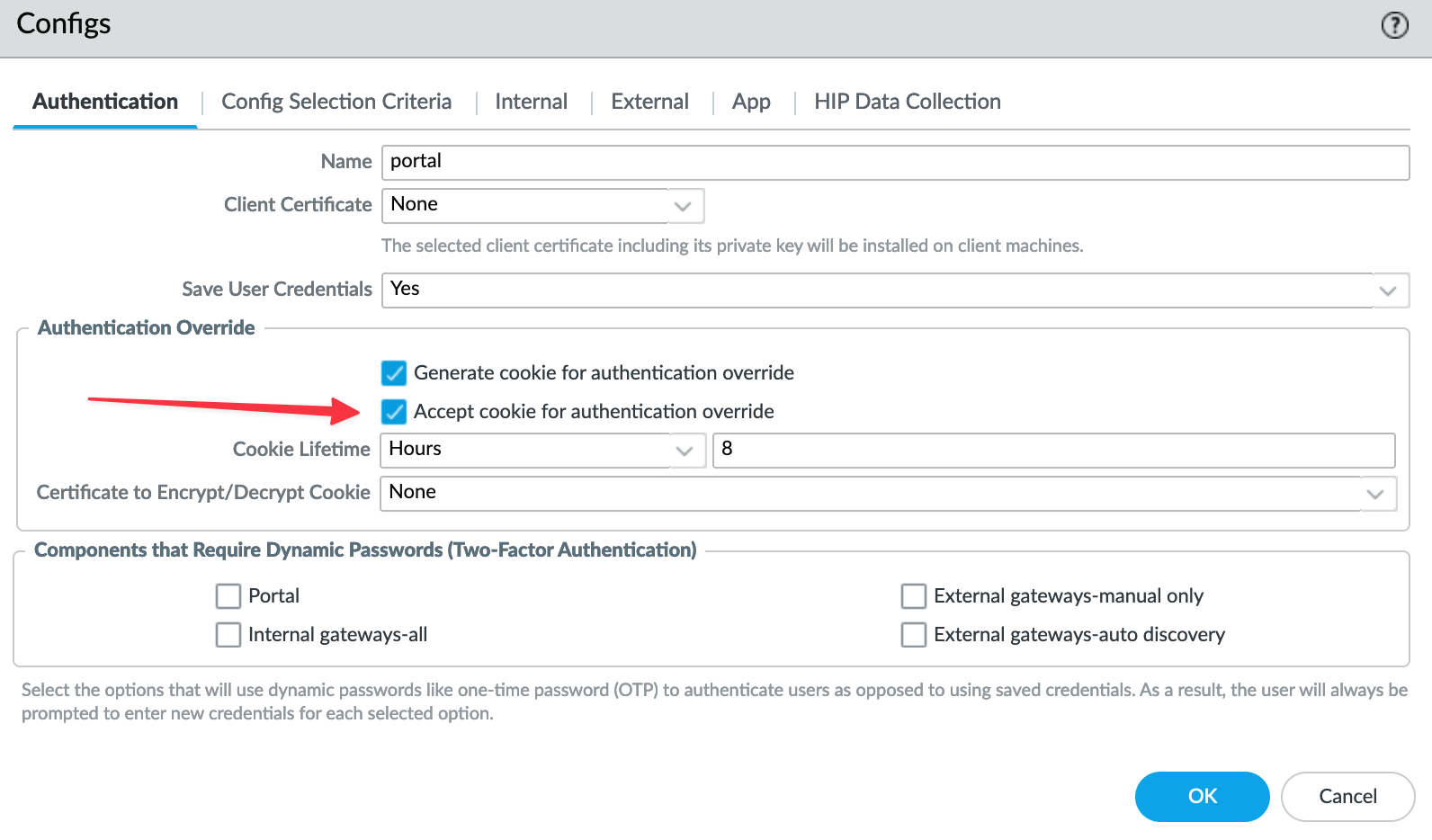
Closing Up
I hope you find this post useful. However, it’s important to remember that all these setups depend on your specific security guidelines. Your company might require users to perform MFA twice or re-enter their credentials for security. So, please make sure to discuss these changes with your wider team before implementing anything. As always, your comments and feedback are welcome, feel free to share your thoughts and experiences.






