I’ve been working with Palo Alto Firewalls and Panorama for a few years now, yet the best ways to use Templates still seem somewhat mysterious. I bet many of you feel the same way. Since every network is unique, there isn’t one “right” way to manage this. In this blog post, I’ll break down what Templates and Template Stacks are in Panorama and share some effective strategies for organizing them. Let’s dive in.
A Quick Note on Panorama
If you’re new to Panorama, it’s a centralized management tool that simplifies managing multiple Palo Alto firewalls from a single place. There are two key concepts in Panorama which are Device Groups and Templates. Device Groups manage the configurations you’d usually find under the Policies and Objects tabs on the firewall, while Templates manage with configurations from the Network and Device tabs.
It’s important to note that Device Groups and Templates serve different purposes and manage different parts of the configurations. This blog post will focus exclusively on Templates. If you need a refresher on Device Groups and Templates, I’ve covered that in a previous post. Feel free to check it out here for a quick recap.
TL;DR
If you don't want to read the whole thing and just want to know the summary, here it is 🙂
- Local Management - Manage firewall management IP, hostname, and HA configs directly on the firewall.
- Panorama Management - Use Panorama to manage all other configurations.
- Global Template - Set up a 'global' template for configurations that apply to all firewalls.
- Regional/Branch/DC Templates - Create these when configurations differ among groups of firewalls (only if required)
- Site-Specific Templates and Stacks - Use individual templates for each firewall or pair of firewalls.
- Template Variables - Use Variables if you want to use a common template or stack among multiple firewalls.
Templates and Template Stacks
As we've discussed before, Templates manage the configuration you find under the ‘Network’ and ‘Device’ tabs on your firewall.
When you want to manage a firewall with Panorama, you don’t add it directly to a Template. Instead, you add it to a Template Stack. A Template Stack can hold several Templates. This stack pulls together all the configurations from its Templates and pushes them to the firewall. The order in which you place Templates in the Stack matters because the Templates at the top have priority. If there’s a conflict in the configuration, the template at the top wins.
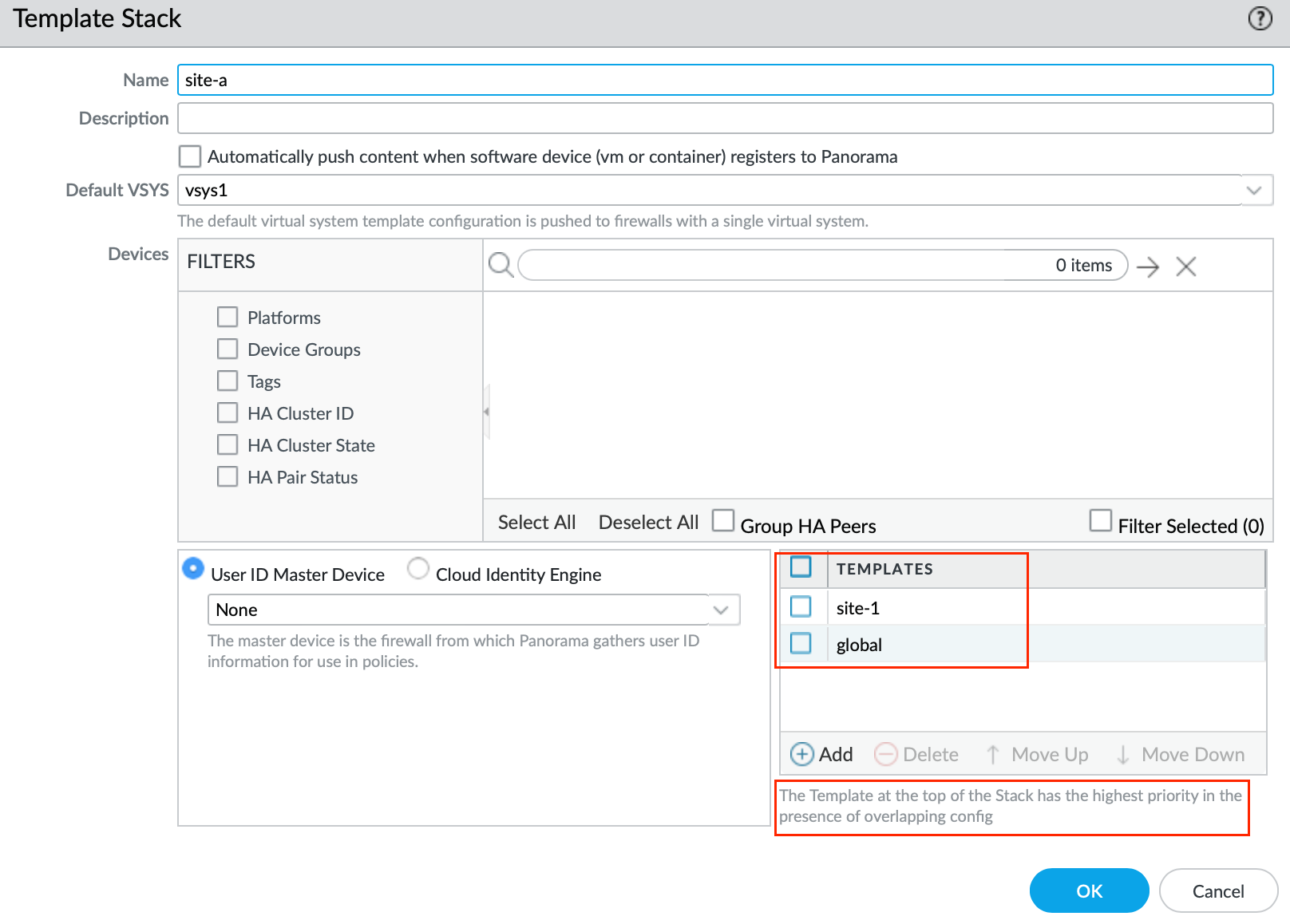
- Imagine you have a 'global' Template with a config like a DNS server set to 1.1.1.1.
- You might also have a region-specific Template, say for 'europe', with a different DNS config, like 8.8.8.8.
- If you’re setting up a firewall in Europe, you’d arrange the 'europe' Template above the 'global' Template in the Stack. This way, the 'europe' configs take priority, using the DNS server 8.8.8.8
Bakery & Co
Let’s consider a scenario with ‘Bakery & Co,’ a company that’s expanding globally and opening new stores worldwide. Managing the configurations for each location individually would be a massive challenge. For instance, if we had to set up SNMP on each firewall individually, it would be inefficient and not scalable. Panorama is the answer to managing multiple firewalls from a single place but there are some nuances that you need to be aware of.
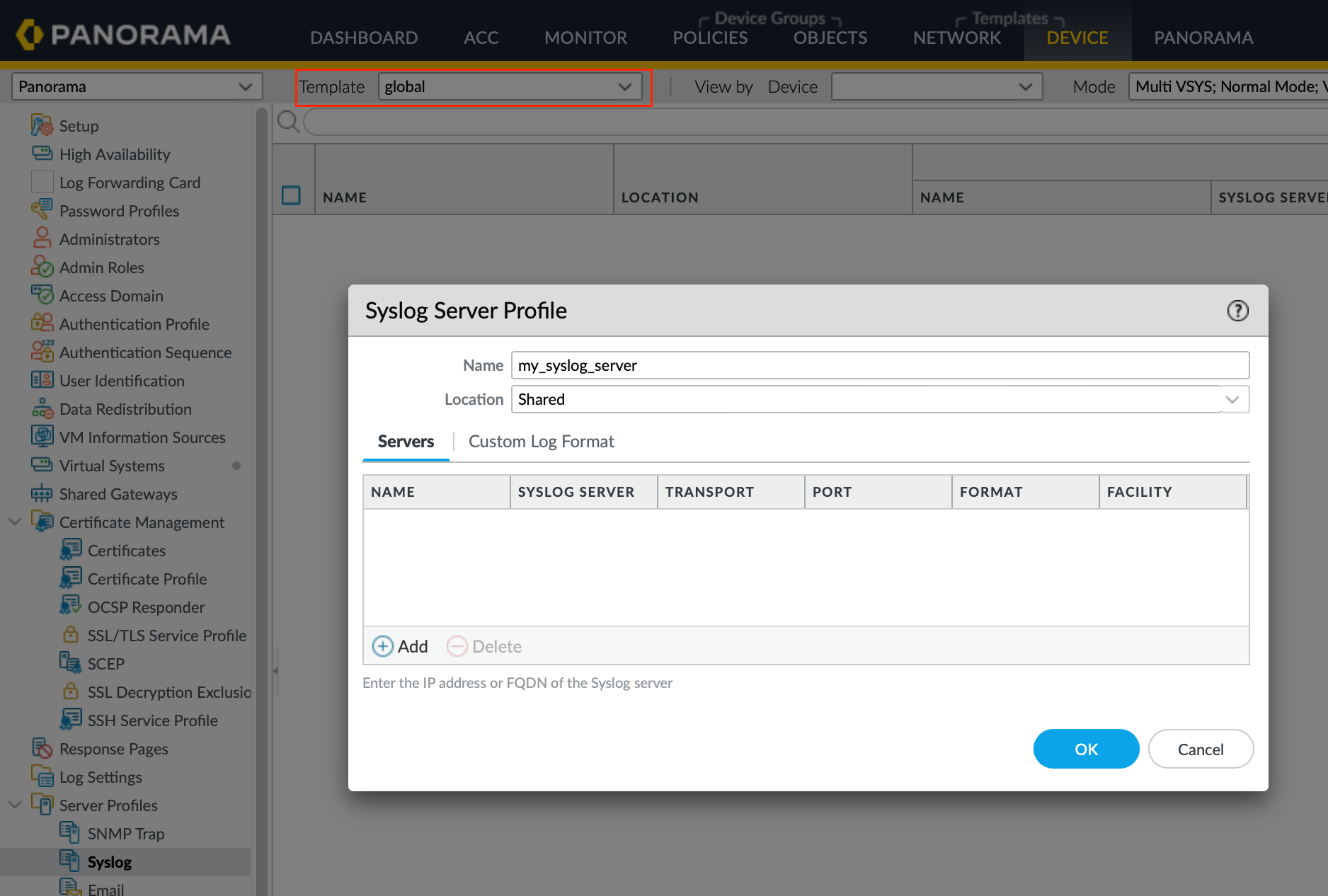
So, how do we handle this using Panorama? A good practice is to always start with creating a ‘global’ template. This is where you define configurations that all firewalls across the company should have. For example, if all firewalls need to use the same syslog server, you would configure these settings in the ‘global’ template.
Setting Up 'Site-1'
Let's say we are launching our first location, 'site-1', for Bakery & Co. My typical approach involves the following.
- Create a New Template Stack - I would start by creating a new template stack named 'site-1-stack'. This is where the actual firewall will be added.
- Develop a Site-Specific Template - Next, I'd create a template called 'site-1-template' and place it at the top of the stack. The 'global' template, which contains settings that apply to all locations, like syslog server configurations, would go at the bottom.
- Configure Site-Specific Configs - For configs unique to 'site-1', such as the firewall’s interface IP and static routes, these are configured in the 'site-1-template'.
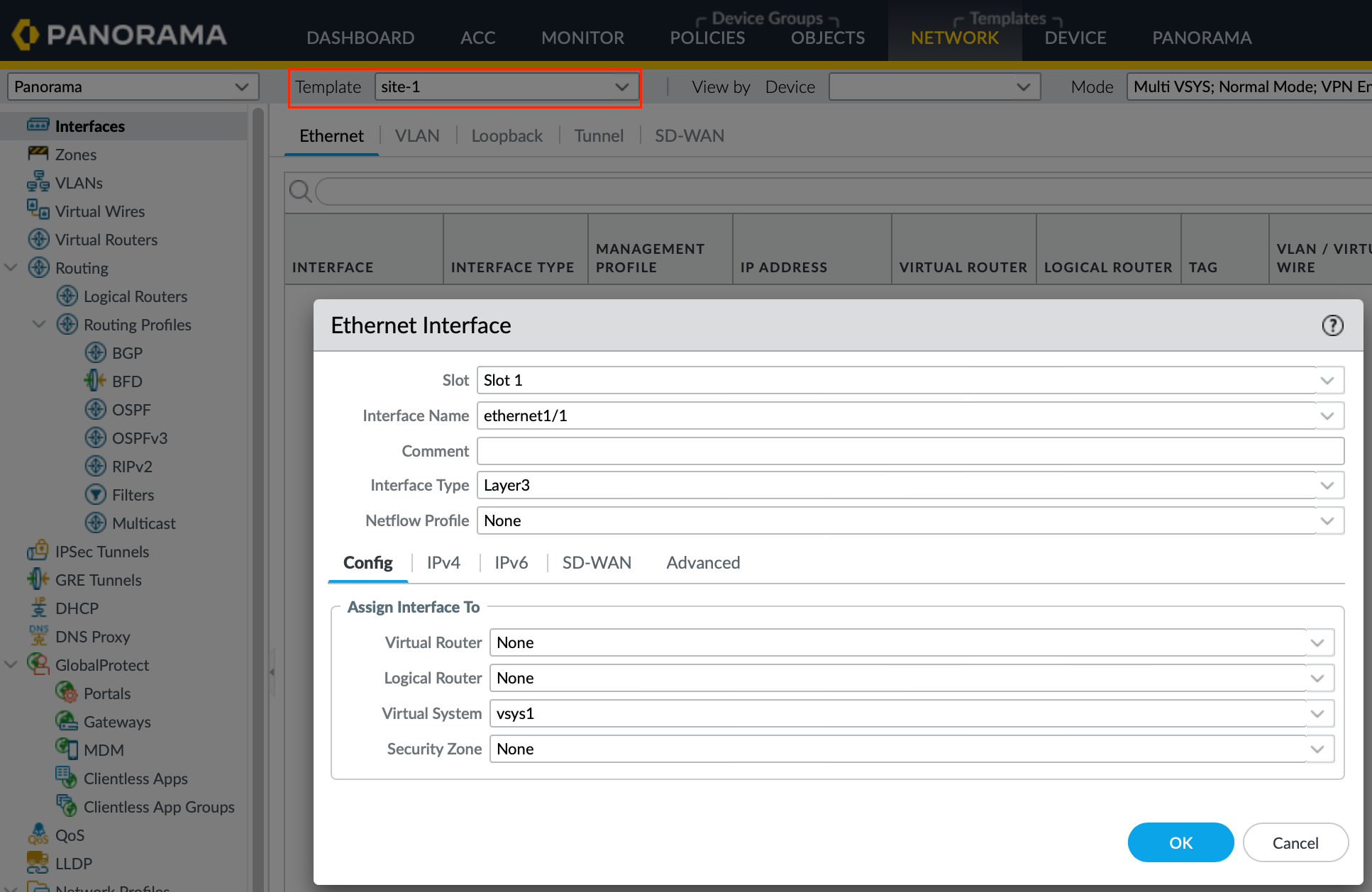
The end result is that the 'site-1-stack' pulls configurations from both the 'site-1-template' and the 'global' template, merges them, and then pushes them to the firewall. This way, the firewall at 'site-1' receives both the site-specific configs (like interface IP and routes) and common configurations (such as the Syslog server).
If you want to have more granular regional-specific configs or if you want to separate the configs between branches and DC, you could also create regional templates or branch/DC templates. You could place them in between the site-specific template and the global template. For example, suppose all the branch firewalls should use a specific syslog server and DC firewalls should use a different one, you can define them separately. So, for the branch firewalls, add the branch templates to their stacks, and for DC firewalls, add the DC templates to their stacks.
Setting Up 'Site-2'
When it’s time to set up ‘Site-2’, the process is straightforward. Simply create a new site-specific template and a corresponding stack. Configure the ‘Site-2’ specific configs in this template.
I prefer this approach because it’s cleaner and simpler to manage. The need for different templates for each site stems from the unique requirements of each location, such as differing IP addresses. This method keeps each site’s configurations tidy and straightforward.
What If We Have 100+ Sites?
Now, let’s consider a scenario where we’re managing over 100 sites. You might wonder if you need to create 100 templates and 100 template stacks, one for each site. It’s a valid concern, and admittedly, it’s not ideal to manage so many individually if the sites share similar designs like the same number of interfaces or similarly named zones.
This is where template Variables come into play. Instead of hard-coding the actual values in each template, you can use Template Variables as placeholders. These placeholders are then replaced with the specific values for each site as needed. This approach allows you to manage large numbers of sites more efficiently by standardizing as much of the configuration as possible and customizing only the necessary details.
Managing Multiple Sites Using Common Templates in Panorama (Variables)
For the sake of simplicity, imagine you have two sites, each with its own firewall. Both sites share a similar design, such as having two interfaces, but require different IP addresses for each. This is how you can use variables to share a common template.
Start by creating a common template, which we’ll call 'london_sites_template', and a corresponding stack named 'london_sites_stack'. Add both firewalls to this common stack.
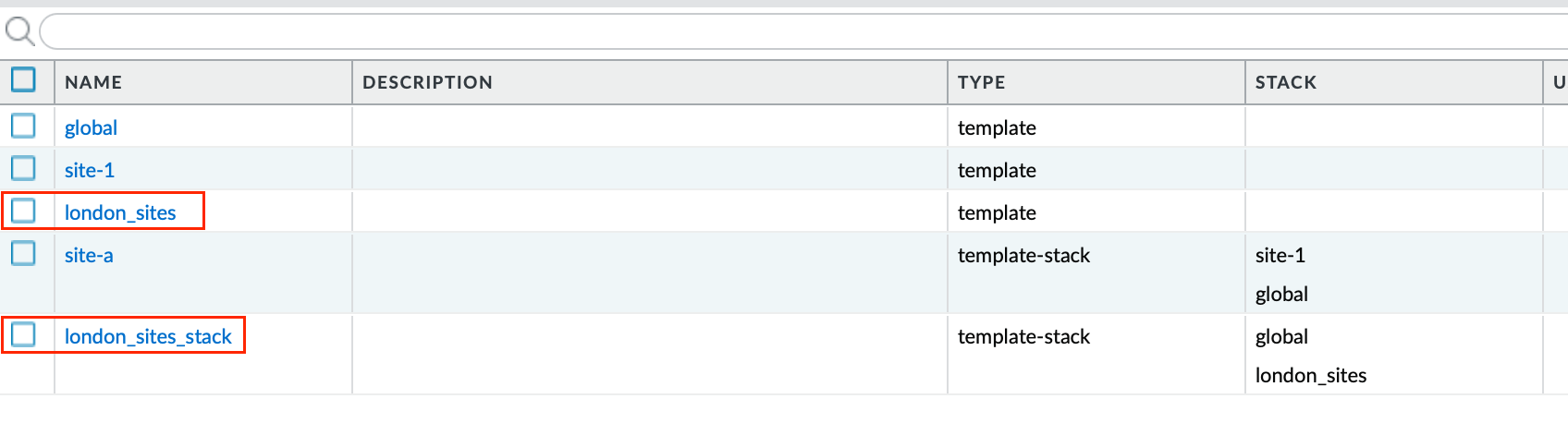
Configure Interface Using Variables - Navigate in Panorama to Network > Interfaces, select the common template 'london_sites_template', and add an interface. Instead of assigning a specific IP address directly to the interface, use a variable. This makes the template flexible, allowing specific values to be assigned later per site.
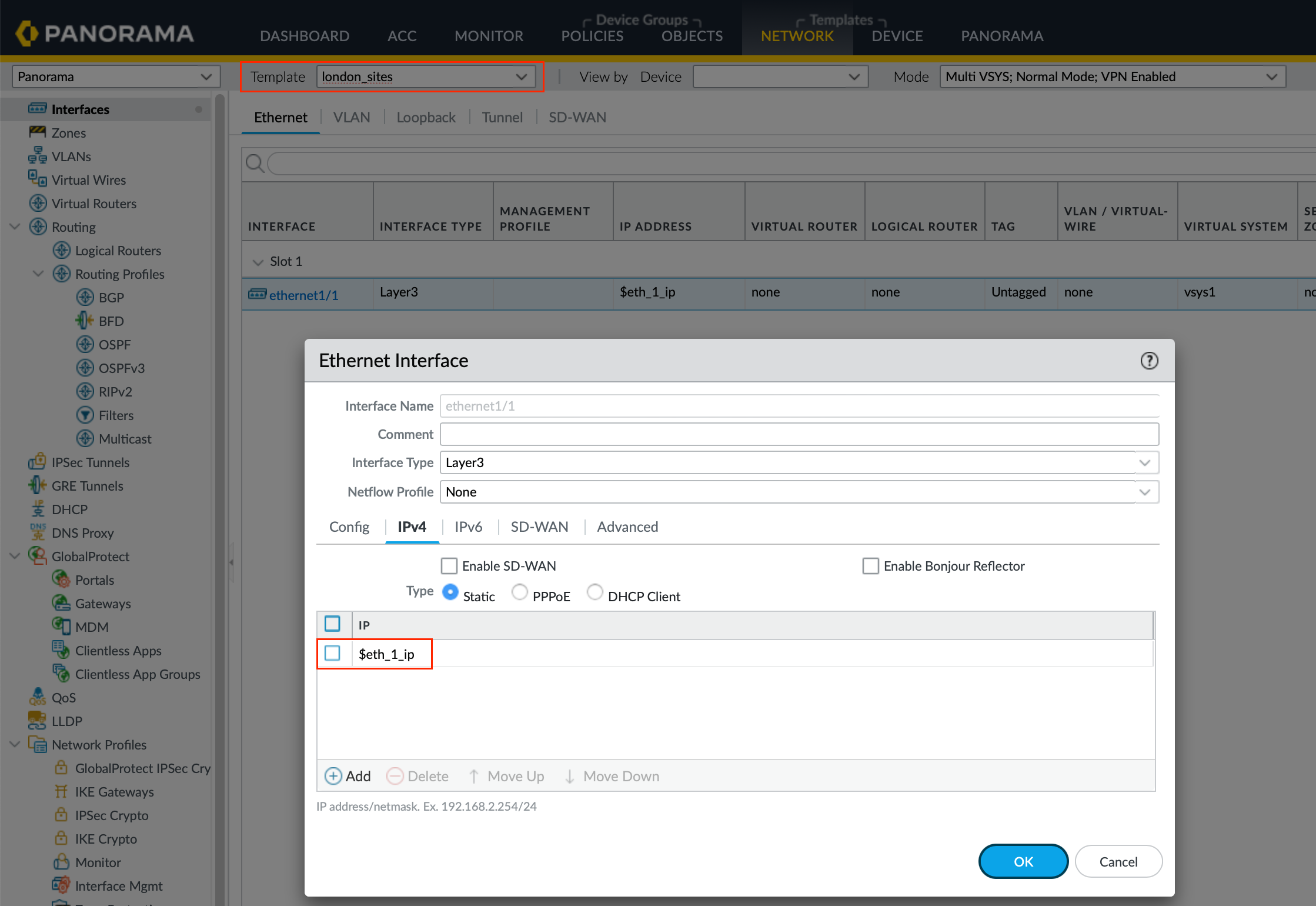
$Export and Edit the Variables CSV File - Next, navigate to Panorama > Templates and select the 'london_sites_stack'. Export the variables to a CSV file. This file allows you to input the specific configurations for each site. You’ll see columns for variable names, the value placeholder, and a column for each firewall to define specific values. Input the actual IP addresses and any other site-specific configurations into the CSV file.
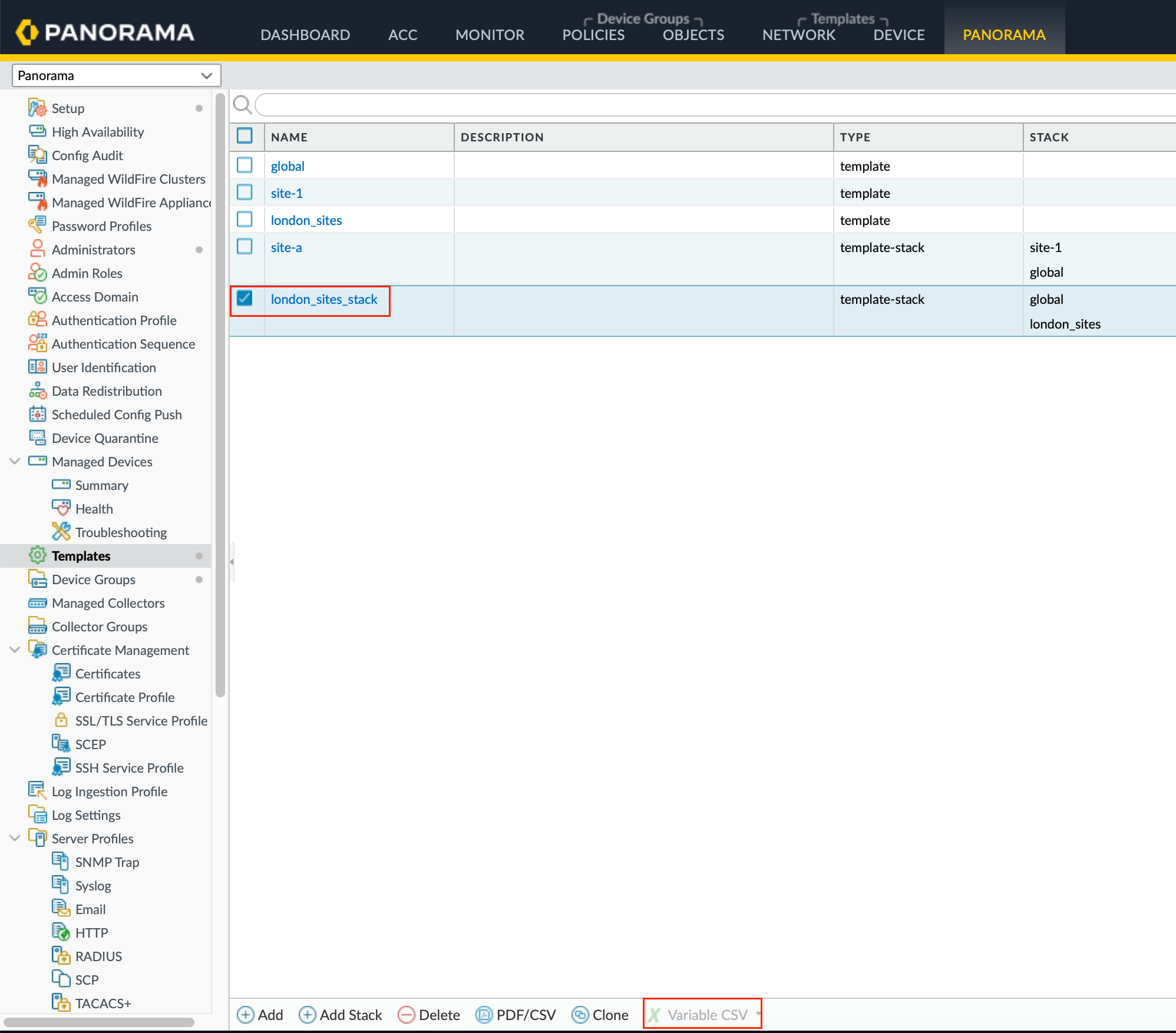
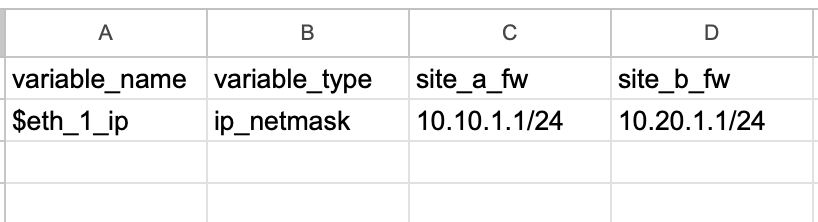
Import the Configurations - Once the CSV file is updated, import it back into Panorama and push the changes to the firewalls. The end result is firewalls receive their own interface IP addresses.
Closing Up
There’s no one-size-fits-all solution, the approach I’ve shared is the one I prefer. I’d love to hear about how you manage your templates. Please share your thoughts in the comments below.






