Hi all, welcome back to another blog post on VyOS. In the previous post, we covered how to install VyOS and set up the initial configurations. In this blog post, we'll cover how to configure firewall rules in VyOS. To demonstrate, we'll create a hypothetical office setup with a VyOS router/firewall. The router will have two interfaces - one facing the Users and another facing the Internet. Our goal is to allow the Users subnet to access the Internet for ICMP, DNS, and general web traffic.
Diagram
Our example is based on the following diagram. I don't have a public IP address on my lab but just play along and pretend that 10.10.0.7 is a public IP 😊 (This IP is behind my ISP's router)
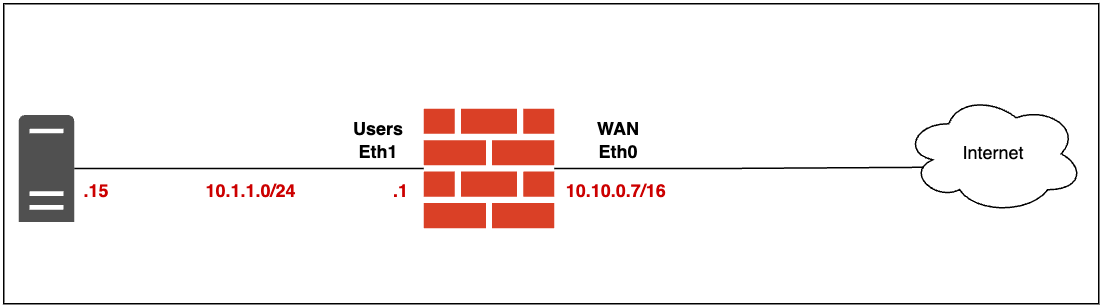
As you can see in the diagram, the VyOS router has two interfaces. The interface connected to the Users subnet (Eth1) has an IP address of 10.1.1.1/24. There's also a test machine in this subnet with the IP address 10.1.1.15. Our goal is to ensure that this test machine can successfully ping an Internet IP address and browse the general Internet.
VyOS Firewall Basics
I won't be going in-depth on how firewalling works, but if you're interested in learning more, feel free to check out the official guide here. What we will cover today is inspecting traffic that is going through the firewall. We can also control the traffic destined to the firewall or originating from the firewall, but that's a topic for another day.
When I say traffic going through the firewall, I mean traffic where neither the source nor destination IP belongs to the firewall. In our example, if I ping from my test machine to 8.8.8.8, the traffic will pass through the firewall. We want to inspect this traffic and create policies to either 'accept' or 'drop' it. VyOS (or iptables) refers to this as the 'forward' stage because the firewall forwards the traffic.
VyOS Default Behaviour
When you set up VyOS for the first time, you'll notice that by default, it allows all traffic. In other words, the 'forward' stage (as well as other stages like 'input' or 'output') is set to 'accept' traffic by default. If you want to use VyOS as a proper firewall, you need to change this behaviour and set the default action to 'drop'.
set firewall ipv4 forward filter default-action 'drop'Static Route and NAT
Please note that in our example, you will also need to create a NAT policy. This is necessary so that the internal network's IP addresses get translated to the IP address of the WAN interface when accessing the Internet. I've also created a static route as shown below.
set protocols static route 0.0.0.0/0 next-hop 10.10.0.1set nat source rule 1 outbound-interface name 'eth0'
set nat source rule 1 source address '10.1.1.0/24'
set nat source rule 1 translation address 'masquerade'What I’m saying here in the NAT policy is that if the traffic’s outbound interface is eth0 (WAN) and the source is 10.1.1.0/24 (Users subnet), change the source IP of the traffic to the IP address of eth0. This ensures that the traffic leaving your network appears to come from the WAN interface's IP.
Allow Return Traffic (Established)
If you’ve worked with other firewall vendors like Palo Alto, FortiGate, or ASA, you might be used to creating rules in only one direction because these firewalls are stateful. This means they automatically allow return traffic. For example, if a machine on the internal network sends a DNS query to 8.8.8.8, and the firewall has a rule to allow this outbound traffic, the return DNS response from 8.8.8.8 is automatically allowed through. You don’t have to do anything extra for this to work.
However, with VyOS, you have to explicitly allow ‘established’ sessions. Simply put, an ‘established’ session is when the firewall recognizes that a connection has already been set up (like the DNS query in the previous example), so it allows the returning traffic as part of that established session.
set firewall ipv4 forward filter rule 100 action 'accept'
set firewall ipv4 forward filter rule 100 state 'established'Configuring VyOS Firewall Rules
Now that we’ve covered all the prerequisites, let’s dive into configuring the firewall rules. I’m going to create three rules.
- Allow DNS traffic to 1.1.1.1.
- Allow ICMP traffic to ‘any’ IP.
- Allow HTTP and HTTPS traffic to ‘any’ IP.
set firewall ipv4 forward filter rule 1 action 'accept'
set firewall ipv4 forward filter rule 1 description 'Allow-DNS'
set firewall ipv4 forward filter rule 1 destination address '1.1.1.1/32'
set firewall ipv4 forward filter rule 1 destination port '53'
set firewall ipv4 forward filter rule 1 inbound-interface name 'eth1'
set firewall ipv4 forward filter rule 1 log
set firewall ipv4 forward filter rule 1 outbound-interface name 'eth0'
set firewall ipv4 forward filter rule 1 protocol 'udp'
set firewall ipv4 forward filter rule 1 source address '10.1.1.0/24'set firewall ipv4 forward filter rule 2 action 'accept'
set firewall ipv4 forward filter rule 2 description 'Allow-ICMP'
set firewall ipv4 forward filter rule 2 destination address '0.0.0.0/0'
set firewall ipv4 forward filter rule 2 icmp type-name 'echo-request'
set firewall ipv4 forward filter rule 2 inbound-interface name 'eth1'
set firewall ipv4 forward filter rule 2 log
set firewall ipv4 forward filter rule 2 outbound-interface name 'eth0'
set firewall ipv4 forward filter rule 2 protocol 'icmp'
set firewall ipv4 forward filter rule 2 source address '10.1.1.0/24'set firewall ipv4 forward filter rule 5 action 'accept'
set firewall ipv4 forward filter rule 5 description 'Allow-Internet'
set firewall ipv4 forward filter rule 5 destination address '0.0.0.0/0'
set firewall ipv4 forward filter rule 5 destination port 'http,https'
set firewall ipv4 forward filter rule 5 inbound-interface name 'eth1'
set firewall ipv4 forward filter rule 5 log
set firewall ipv4 forward filter rule 5 outbound-interface name 'eth0'
set firewall ipv4 forward filter rule 5 protocol 'tcp'
set firewall ipv4 forward filter rule 5 source address '10.1.1.0/24'Verification
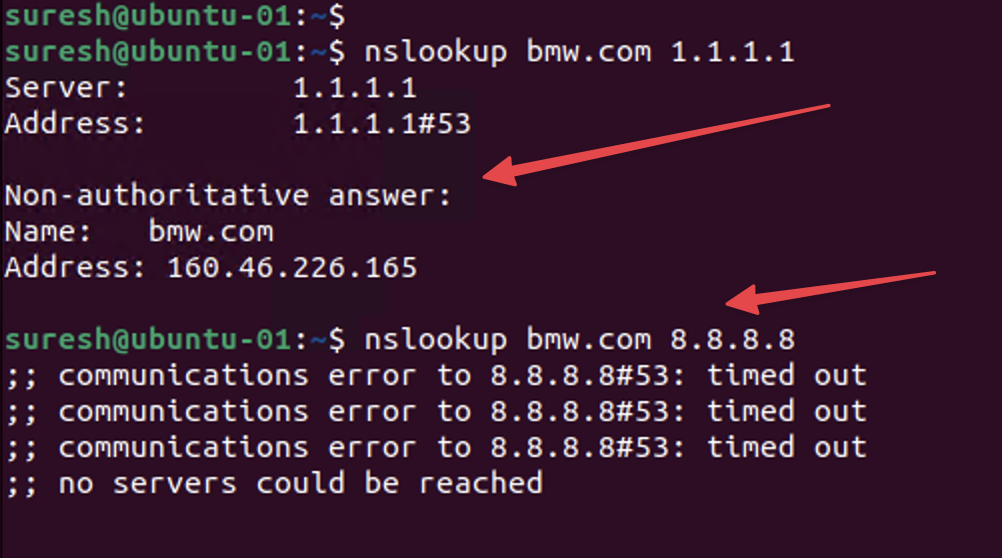
I'm going to resolve a domain using 1.1.1.1 which should work but if I try 8.8.8.8, it should fail.
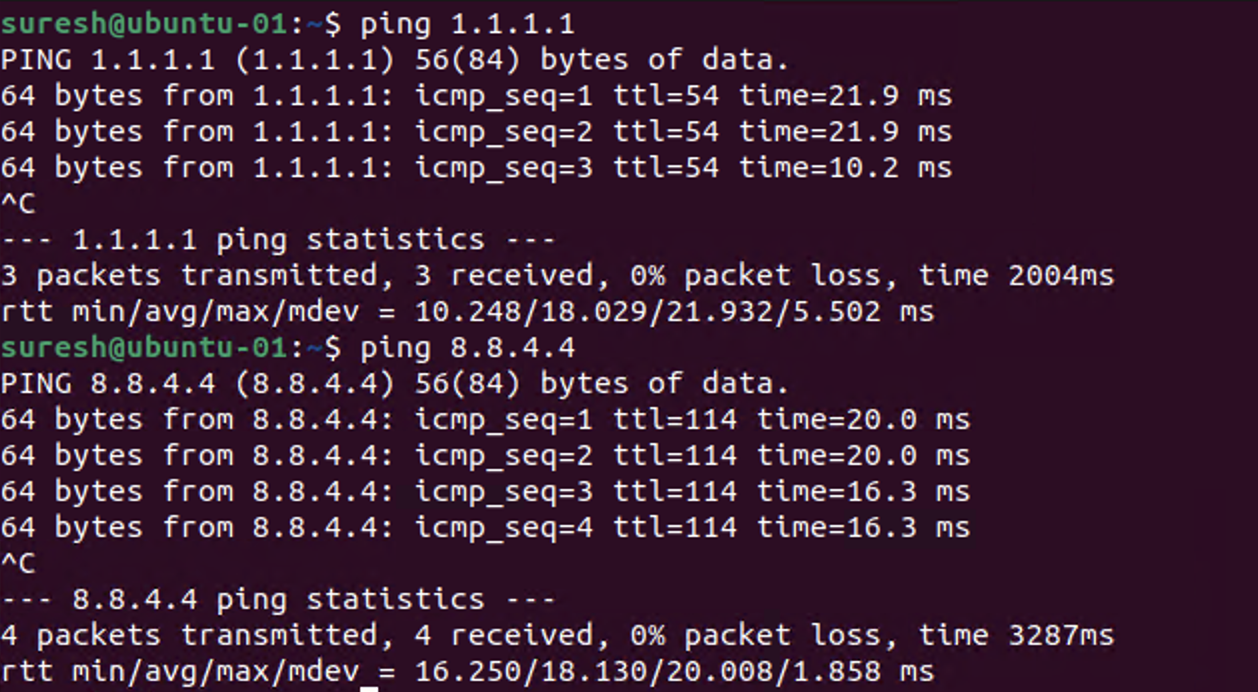
I should also be able to ping any IP address, I'm just going to try a couple.
General Internet access should also work, I'm just going to browse to my blog (why not 🙂)
You can also view the traffic logs by running the show log command. If you want to see logs related to a specific rule, you can pass the rule ID as shown below.
show log firewall ipv4 forward filter rule 1Aug 17 16:41:09 kernel:
[ipv4-FWD-filter-1-A]
IN=eth1 OUT=eth0
MAC=00:0c:29:bc:2b:1f:00:0c:29:0f:30:e1:08:00
SRC=10.1.1.15 DST=1.1.1.1
LEN=77 TOS=0x00 PREC=0x00 TTL=63 ID=37626
PROTO=UDP SPT=33073 DPT=53 LEN=57ipv4-FWD-filter-1-A means, this is an IPv4 forward filter. The 'A' means the traffic was 'accepted' (or allowed). If you see 'D' means the traffic was 'dropped'