In this blog post, we will go through the Juniper SRX NAT configuration examples. We will mainly be focusing on four scenarios that are Source NAT, Destination NAT, Static NAT and Port Forwarding.
This blog post assumes prior knowledge of Junos OS and NAT fundamentals. The example is based on vSRX running Junos 21.3R1.9.
Junos Flow Module
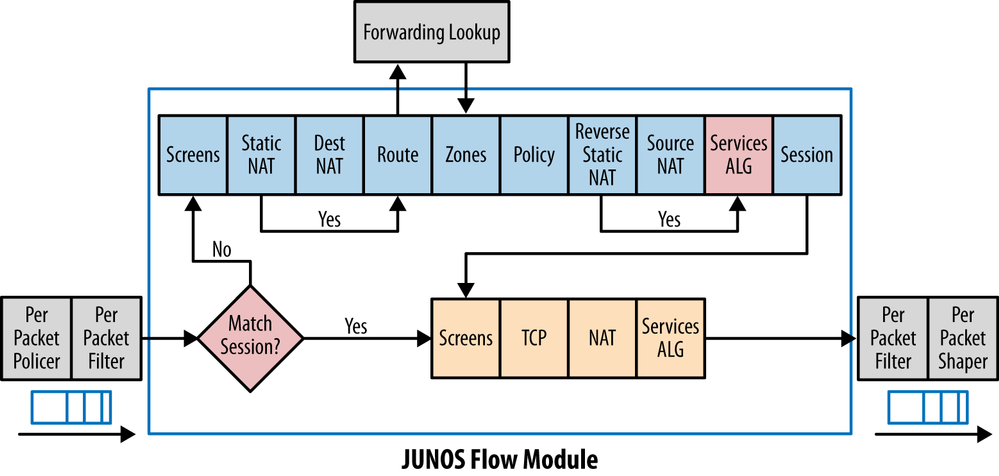
Junos order-of-operation is very important when working with NAT. As you can see on the flow module, Static NAT and Destination NAT happen before the Security Policy so, we need to specify the 'real-IP' on our policies. More on this later.
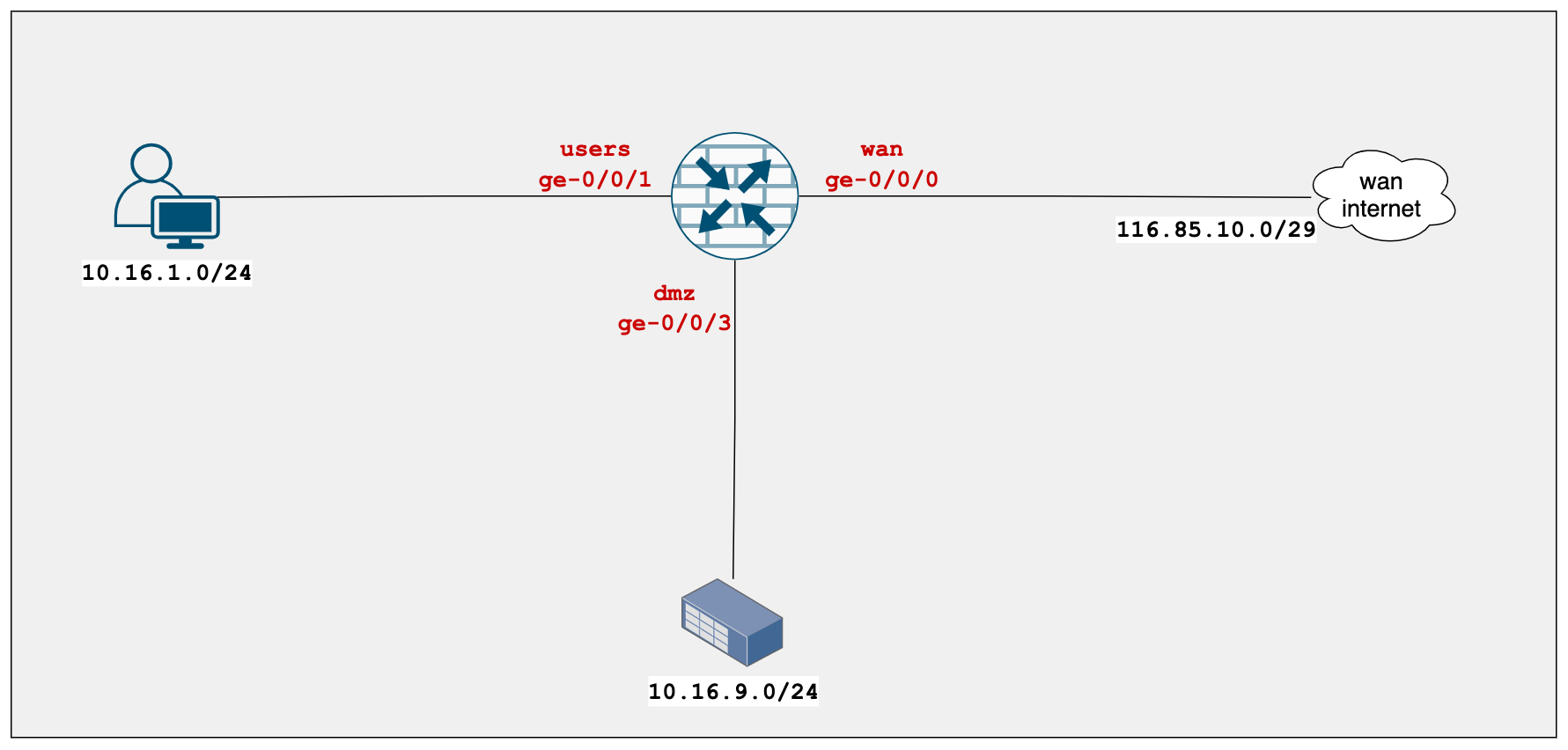
Diagram
The examples are based on the following diagram.
Source NAT
Junos Source NAT or Dynamic PAT (Dynamic Port Adress Translation) is the most commonly used NAT type where multiple internal hosts share the same public IP.
Almost all devices on internal networks don't get public IPs assigned to them (globally routable addresses). One of the main reasons is that there are only a very limited number of public IPs available for us to consume so, devices on internal networks usually have private IP addresses assigned to them (RFC-1918).
Method - 1 Source NAT to Interface IP
In our diagram, we want to translate the source IP address of the users subnet (10.16.1.0/24) to the wan interface IP address (116.85.10.1) of the SRX. For example, when 10.16.1.10 goes out to the Internet, its IP address gets translated to SRX's wan Interface IP 116.85.10.1
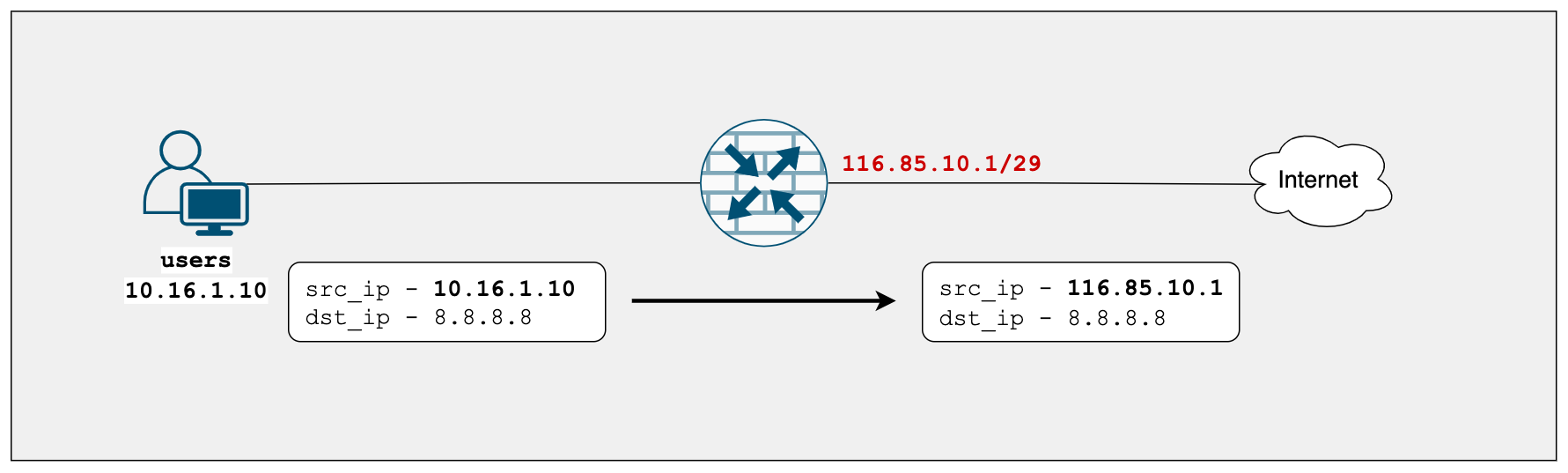
Please remember to configure appropriate security policies as well. I did create a wide-open outbound policy for the sake of this example.
set security policies from-zone users to-zone wan policy user_to_wan match destination-address any
set security policies from-zone users to-zone wan policy user_to_wan match application junos-icmp-ping
set security policies from-zone users to-zone wan policy user_to_wan then permitset security nat source rule-set users_to_wan from zone users
set security nat source rule-set users_to_wan to zone wan
set security nat source rule-set users_to_wan rule snat_pat match source-address 10.16.1.0/24
set security nat source rule-set users_to_wan rule snat_pat match destination-address 0.0.0.0/0
set security nat source rule-set users_to_wan rule snat_pat then source-nat interfaceadmin@branch_srx# show security nat
source {
rule-set users_to_wan {
from zone users;
to zone wan;
rule snat_pat {
match {
source-address 10.16.1.0/24;
destination-address 0.0.0.0/0;
}
then {
source-nat {
interface;
}
}
}
}
}Now that we've configured the NAT, 10.16.1.10 should be able to ping 8.8.8.8. Let's test it out.
10_16_1_10_pc> ping 8.8.8.8
84 bytes from 8.8.8.8 icmp_seq=1 ttl=53 time=29.665 ms
84 bytes from 8.8.8.8 icmp_seq=2 ttl=53 time=33.538 ms
84 bytes from 8.8.8.8 icmp_seq=3 ttl=53 time=25.339 ms
84 bytes from 8.8.8.8 icmp_seq=4 ttl=53 time=29.825 ms
84 bytes from 8.8.8.8 icmp_seq=5 ttl=53 time=28.356 msYou can also use a couple of show commands to verify the status of the NAT.
admin@branch_srx> show security nat source rule snat_pat
source NAT rule: snat_pat Rule-set: users_to_wan
Rule-Id : 1
Rule position : 1
From zone : users
To zone : wan
Match
Source addresses : 10.16.1.0 - 10.16.1.255
Destination addresses : 0.0.0.0 - 255.255.255.255
Action : interface
Persistent NAT type : N/A
Persistent NAT mapping type : address-port-mapping
Inactivity timeout : 0
Max session number : 0
Translation hits : 135
Successful sessions : 135
Number of sessions : 4admin@branch_srx> show security flow session
Session ID: 286, Policy name: user_to_wan/6, State: Stand-alone, Timeout: 2, Valid
In: 10.16.1.10/26726 --> 8.8.8.8/1;icmp, Conn Tag: 0x0, If: ge-0/0/1.0, Pkts: 1, Bytes: 84,
Out: 8.8.8.8/1 --> 116.85.10.1/17322;icmp, Conn Tag: 0x0, If: ge-0/0/0.0, Pkts: 1, Bytes: 84,Method - 2 Source NAT to IP Pool
Instead of using the SRX's interface IP, you can also use another IP within the same subnet. Let's say we want to translate the source IP to 116.85.10.4 for this example.
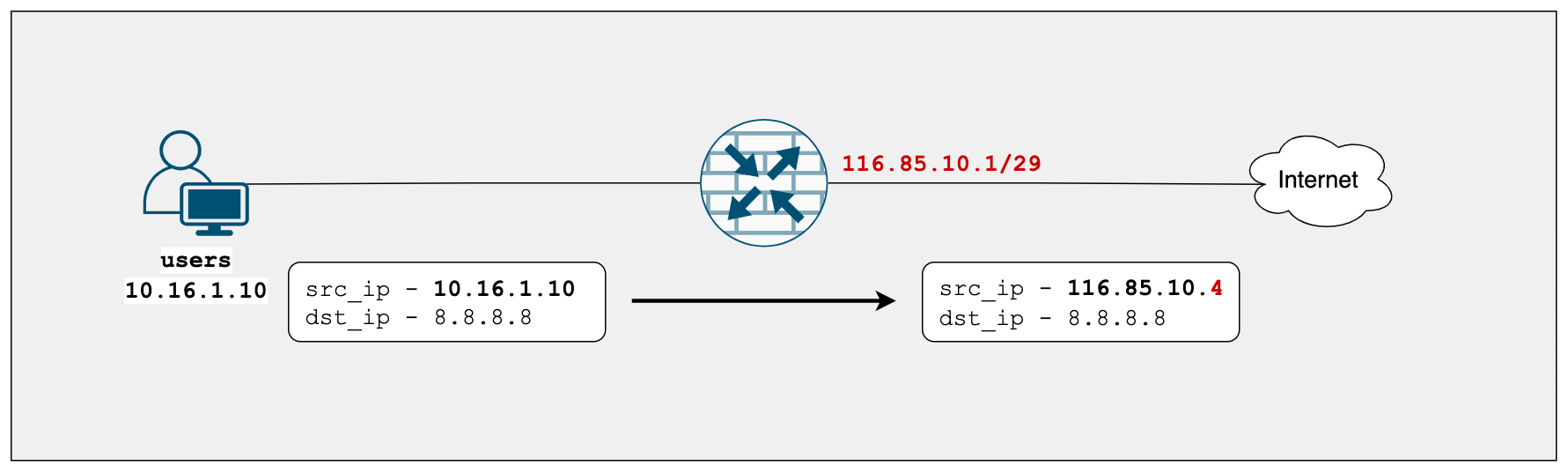
Without Proxy ARP, the SRX will not respond to any ARP requests for 116.85.10.4 as shown below in the Wireshark captures. By default, the firewall will respond to the ARP only if the specific IP is configured on one of its interfaces.
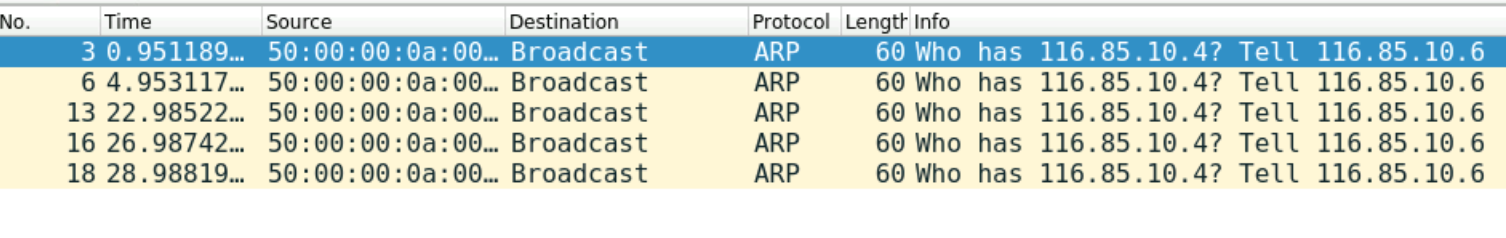
I'm going to amend the configuration to use the IP Pool instead of the Interface IP.
set security nat proxy-arp interface ge-0/0/0.0 address 116.85.10.4set security nat source pool source_nat address 116.85.10.4/32
set security nat source rule-set users_to_wan from zone users
set security nat source rule-set users_to_wan to zone wan
set security nat source rule-set users_to_wan rule snat_pat match source-address 10.16.1.0/24
set security nat source rule-set users_to_wan rule snat_pat match destination-address 0.0.0.0/0
set security nat source rule-set users_to_wan rule snat_pat then source-nat pool source_natsource {
pool source_nat {
address {
116.85.10.4/32;
}
}
rule-set users_to_wan {
from zone users;
to zone wan;
rule snat_pat {
match {
source-address 10.16.1.0/24;
destination-address 0.0.0.0/0;
}
then {
source-nat {
pool {
source_nat;
}
}
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
116.85.10.3/32;
116.85.10.4/32;
}
}
}Destination NAT
Junos Destination NAT is generally used where the traffic destined for a public address is sent to a private address. For example, let's say we have a public-facing web server in our company which is accessible from the Internet and we want to translate the public IP address to the real private IP of the server.
Let's say a user from the Internet initiates a connection to 116.85.10.3 and when the connection arrives at the SRX's wan interface, we want to translate the IP address from 116.85.10.3 to 10.16.9.10 and forward it to the webserver.
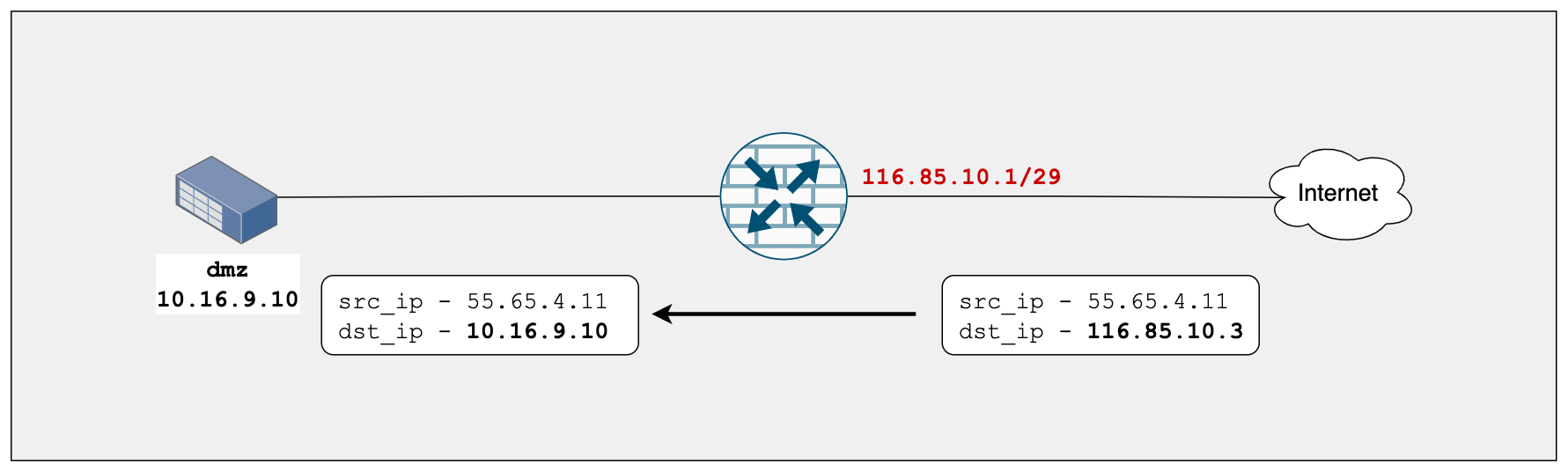
Without Proxy ARP, the SRX will not respond to any ARP requests for 116.85.10.3 as shown below in the Wireshark captures.
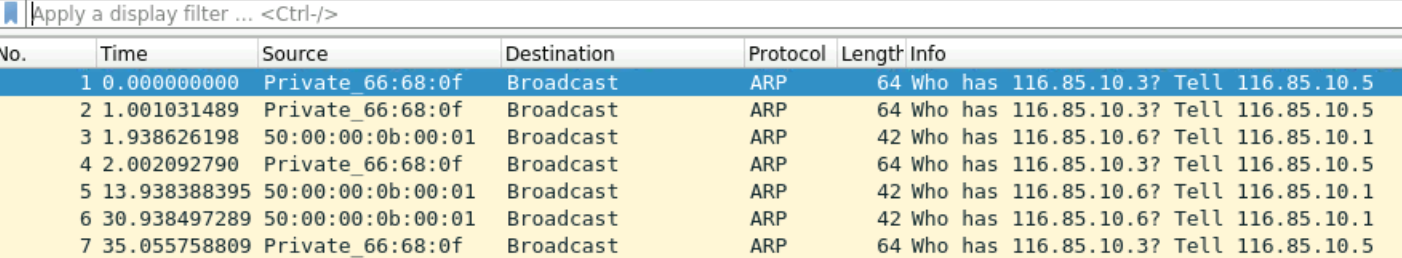
As I mentioned at the beginning of the post, you need to use the real-address on the Security Policies (10.16.9.10) because the NAT translation happens before the security policies.
Please keep in mind that you also need to configure appropriate security policies to allow connections originating from the Internet to your web-server. I allowed any IP address on any application to talk to the web-server.
set security zones security-zone dmz address-book address web_server_ip 10.16.9.10/32
set security policies from-zone wan to-zone dmz policy to_web_server match source-address any
set security policies from-zone wan to-zone dmz policy to_web_server match destination-address web_server_ip
set security policies from-zone wan to-zone dmz policy to_web_server match application any
set security policies from-zone wan to-zone dmz policy to_web_server then permitset security nat proxy-arp interface ge-0/0/0.0 address 116.85.10.3/32set security nat destination pool web_server address 10.16.9.10/32
set security nat destination rule-set to_web_server from zone wan
set security nat destination rule-set to_web_server rule web_server_incoming match destination-address 116.85.10.3/32
set security nat destination rule-set to_web_server rule web_server_incoming then destination-nat pool web_serverdestination {
pool web_server {
address 10.16.9.10/32;
}
rule-set to_web_server {
from zone wan;
rule web_server_incoming {
match {
destination-address 116.85.10.3/32;
}
then {
destination-nat {
pool {
web_server;
}
}
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
116.85.10.3/32;
}
}
}admin@branch_srx> show security nat destination rule all
Total destination-nat rules: 1
Total referenced IPv4/IPv6 ip-prefixes: 1/0
Destination NAT rule: web_server_incoming Rule-set: to_web_server
Rule-Id : 1
Rule position : 1
From zone : wan
Destination addresses : 116.85.10.3 - 116.85.10.3
Action : web_server
Translation hits : 447
Successful sessions : 440
Number of sessions : 5Please note that both Source and Destination NAT are unidirectional meaning the traffic is NATed only in one way. (Due to the Stateful nature of the NAT, the reply traffic is always NATed)
Static NAT
Junos Static NAT is used to create a one-to-one mapping from one IP address to another IP address. The mapping includes destination IP address translation in one direction and source IP address translation in the reverse direction.
Static NAT allows connections to be originated from either side of the network (bidirectional), but translation is limited to one-to-one or between blocks of addresses of the same size. For each private address, a public address must be allocated. To demonstrate static NAT, let's create a static NAT between 10.16.9.20 and 116.85.10.5
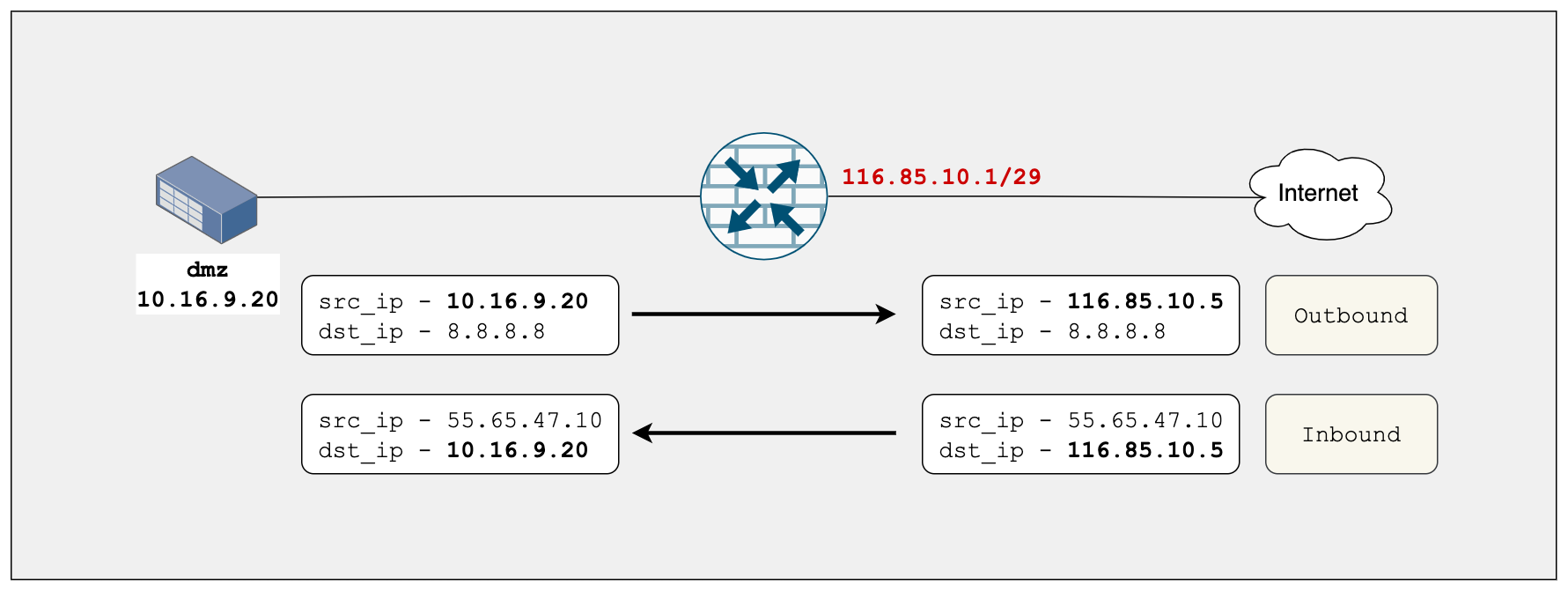
As usual, let's configure security policies, Proxy ARP and finally NAT.
set security zones security-zone dmz address-book address auth_server_ip 10.16.9.20/32
set security policies from-zone wan to-zone dmz policy to_web_server match source-address any
set security policies from-zone wan to-zone dmz policy to_web_server match destination-address auth_server_ip
set security policies from-zone wan to-zone dmz policy to_web_server match application any
set security policies from-zone wan to-zone dmz policy to_web_server then permitset security nat proxy-arp interface ge-0/0/0.0 address 116.85.10.5/32
set security nat static rule-set static_nat_auth_server from zone wan
set security nat static rule-set static_nat_auth_server rule auth_server match destination-address 116.85.10.5/32
set security nat static rule-set static_nat_auth_server rule auth_server then static-nat prefix 10.16.9.20/32static {
rule-set static_nat_auth_server {
from zone wan;
rule auth_server {
match {
destination-address 116.85.10.5/32;
}
then {
static-nat {
prefix {
10.16.9.20/32;
}
}
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
116.85.10.3/32;
116.85.10.4/32;
116.85.10.5/32;
}
}
}
admin@branch_srx> show security nat static rule all
Total static-nat rules: 1
Total referenced IPv4/IPv6 ip-prefixes: 2/0
Static NAT rule: auth_server Rule-set: static_nat_auth_server
Rule-Id : 1
Rule position : 1
From zone : wan
Destination addresses : 116.85.10.5
Host addresses : 10.16.9.20
Netmask : 32
Host routing-instance : N/A
Translation hits : 18
Successful sessions : 8
Number of sessions : 0Port Forwarding
Junos Port-forwarding falls under the Destination NAT hierarchy whereas you can not only translate the destination IP but also the port number. To demonstrate this, let's assume a client on the Internet initiates the connection to 116.85.10.2 on port 8000 and we want to send the traffic to our DMZ server 10.16.9.15 on port 80.
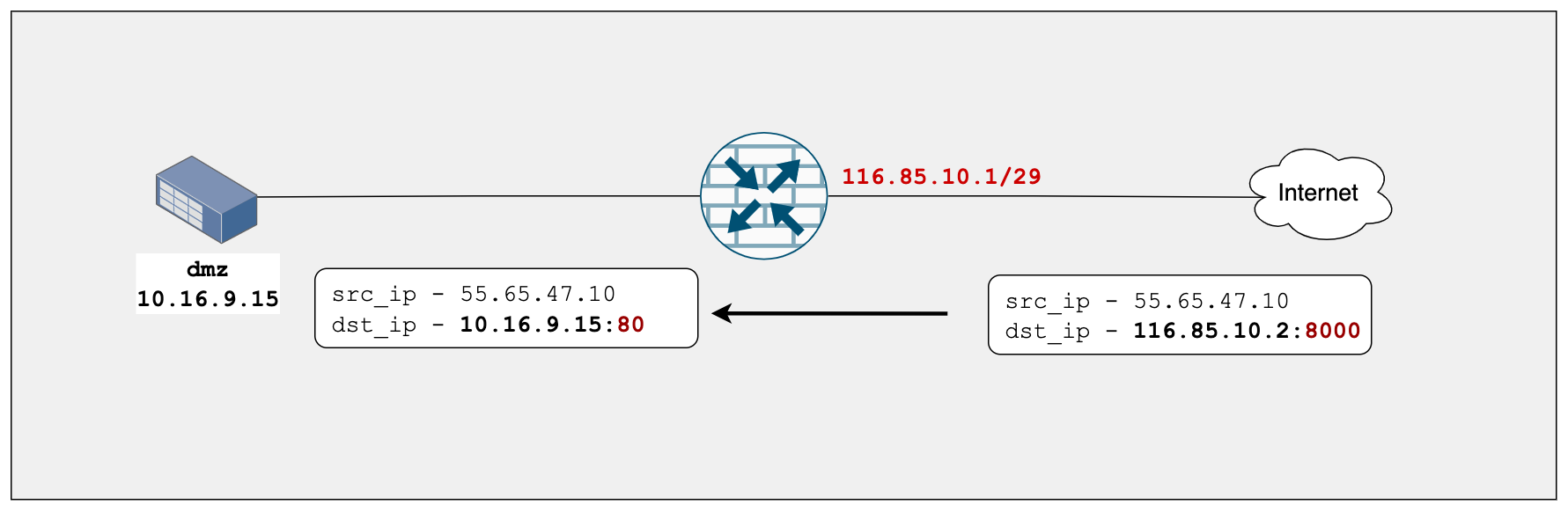
set security nat proxy-arp interface ge-0/0/0.0 address 116.85.10.2/32
set security zones security-zone dmz address-book address port_foward_server_ip 10.16.9.15/32
set security policies from-zone wan to-zone dmz policy port_forward match source-address any
set security policies from-zone wan to-zone dmz policy port_forward match destination-address port_foward_server_ip
set security policies from-zone wan to-zone dmz policy port_forward match application any
set security policies from-zone wan to-zone dmz policy port_forward then permit
set security nat destination pool port_foward_server address 10.16.9.15/32
set security nat destination pool port_foward_server address port 80
set security nat destination rule-set to_web_server rule port_forwarding match destination-address 116.85.10.2/32
set security nat destination rule-set to_web_server rule port_forwarding match destination-port 8000
set security nat destination rule-set to_web_server rule port_forwarding then destination-nat pool port_foward_serveradmin@branch_srx# show | compare
[edit security nat destination]
pool web_server { ... }
+ pool port_foward_server {
+ address 10.16.9.15/32 port 80;
+ }
[edit security nat destination rule-set to_web_server]
rule web_server_incoming { ... }
+ rule port_forwarding {
+ match {
+ destination-address 116.85.10.2/32;
+ destination-port {
+ 8000;
+ }
+ }
+ then {
+ destination-nat {
+ pool {
+ port_foward_server;
+ }
+ }
+ }
+ }
[edit security nat proxy-arp interface ge-0/0/0.0 address]
116.85.10.5/32 { ... }
+ 116.85.10.2/32;
[edit security policies from-zone wan to-zone dmz]
policy to_web_server { ... }
+ policy port_forward {
+ match {
+ source-address any;
+ destination-address port_foward_server_ip;
+ application any;
+ }
+ then {
+ permit;
+ }
+ }
[edit security zones security-zone dmz address-book]
address auth_server_ip { ... }
+ address port_foward_server_ip 10.16.9.15/32;Closing Thoughts
I have to admit that I got caught up by the Proxy ARP when I started working with SRX firewalls. I spent hours trying to figure out why my NAT wasn't working.
I hope you like my blog post. If you have any thoughts or questions about Junos NAT, please feel free to leave a comment or send me a message. I would love to continue the discussion and hear your perspective. Again, thank you for taking the time to read my post and for supporting my writing.







