If you rely heavily on Palo Alto App-IDs, you know the challenge of managing new and modified App-IDs. Palo Alto regularly updates its App-ID database, introducing new App-IDs every month (typically on the third Tuesday) and modifying existing ones more often.
Each release can include hundreds of new and updated App-IDs. It's almost impossible to understand each of them and decide whether or not we are affected by the change. In this blog post, we will look at using Threat Signature Indicators (TSID) to help you get an advanced indication of any impact on your traffic as a result of upcoming App-ID changes.
The Problem with App-ID Changes
Let’s imagine for a moment that currently, Palo Alto doesn’t have a specific App-ID for ‘chatgpt’ (although they do, let’s assume they don’t for this example). If there isn’t an App-ID, the traffic would be identified as ‘ssl’. If Palo Alto decides to introduce a new App-ID for ‘chatgpt’, they will announce this in the new App-ID release notes. However, the challenge is that hundreds of other new App-IDs could be introduced at the same time that we might never have heard of.
So, when I go to Device > Dynamic Updates and select the new release and click ‘Review Apps’, it lists all the modified and new App-IDs, including ‘chatgpt’. Previously, without the TSID approach, it would only highlight all the rules that currently allow ‘ssl’ because ‘chatgpt’ was previously identified under ‘ssl’. We could, of course, go to each rule and allow ‘chatgpt’. But on the other hand, what about the hundreds of other new App-IDs? How do we even know if someone is actually using those applications? We can’t just allow all new App-IDs every time.
Let's Look at an Example
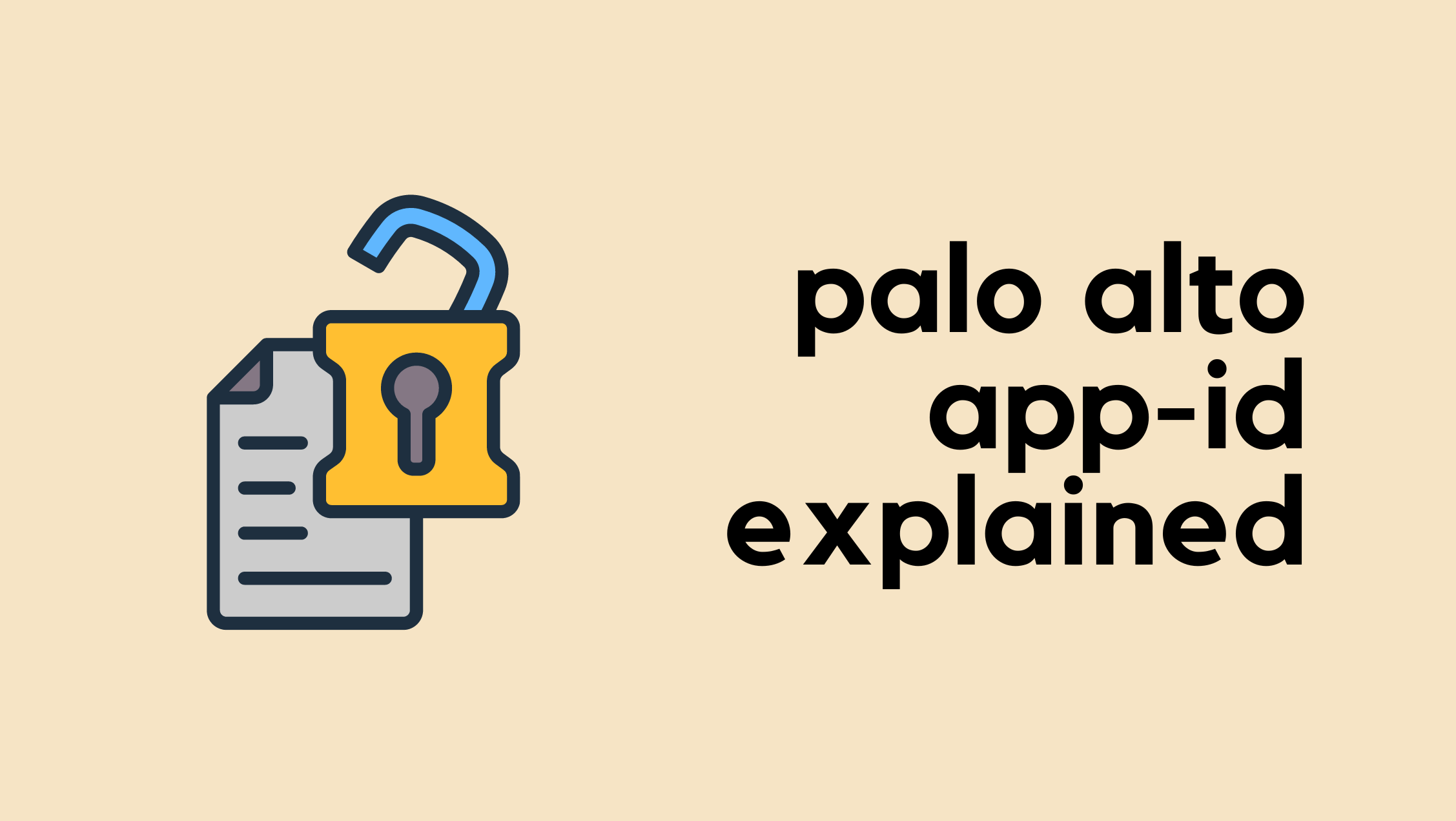
If we look at the Applications and Threats update from September 24th (8896-8979), there are many new and modified App-IDs. One that caught my attention is called ‘copysmith’. To be honest, I had never heard of this App until I saw it here. It appears to be an AI application (ah, not another one, haha). Currently, the application is identified as ‘ssl’, but soon it will be identified specifically as ‘copysmith’.
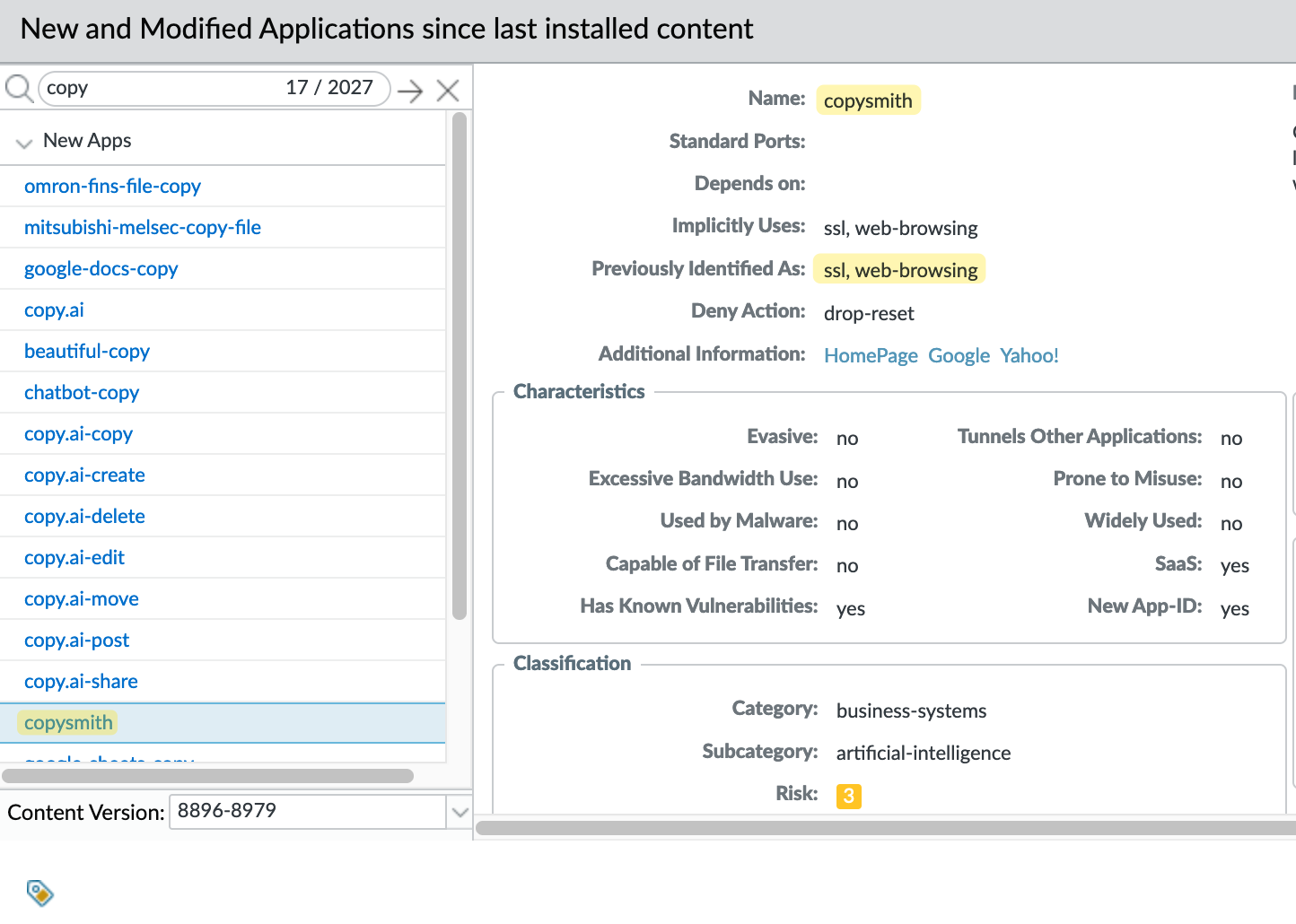
At this point, we can’t determine whether anyone in our company actually uses this application. Of course, an easy fix would be to just allow it in all the policies where we have ‘ssl’, but that’s not ideal.
First, we need to determine if anyone is actually using this or will be affected. We can then review this and decide what to do with it. However, the problem is that there are also hundreds of other new App-IDs, and it would take a significant amount of time to review all of them.
App-ID Change Threat Signature Indicator
Starting in November 2023, Palo Alto introduced a new Vulnerability Signature category called 'app-id-change', which lists all TSIDs (Threat Signature Indicators). These TSIDs are marked with an “Informational” severity level and the default action is set to “Allow.” They are designed not to block any traffic but to serve the purpose of indicating any traffic that will be affected by upcoming App-ID changes. For further details, you can refer to the official announcement.
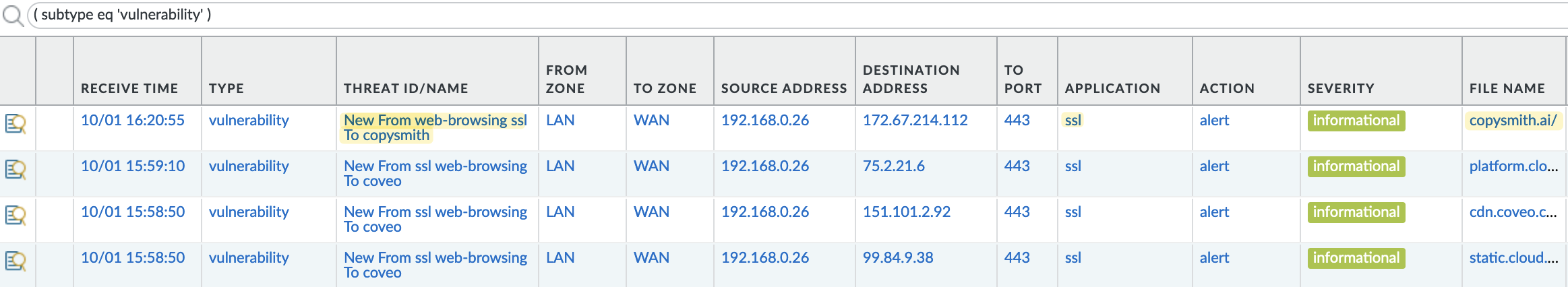
TSIDs are basically Threat Prevention signatures that will trigger on the traffic that will be identified using the App-ID that Palo Alto intends to add or change in the next month’s new App-IDs content update. In other words, these TSIDs will mimic the new associations that the new or modified App-ID will use for that same traffic when the changes are implemented in the next month’s new App-IDs content update.
This means that, after you enable these TSIDs in your Vulnerability Protection profiles, you will see Threat Log events associated with any planned App-ID changes that will impact your network.
Configure App-ID Change Visibility
To configure, navigate to Objects > Security Profiles > Vulnerability Protection and select the profile you currently use or create a new one or use the default one.
Inside the profile, create a new rule (named 'App-ID change' in this example) as shown in the screenshot.
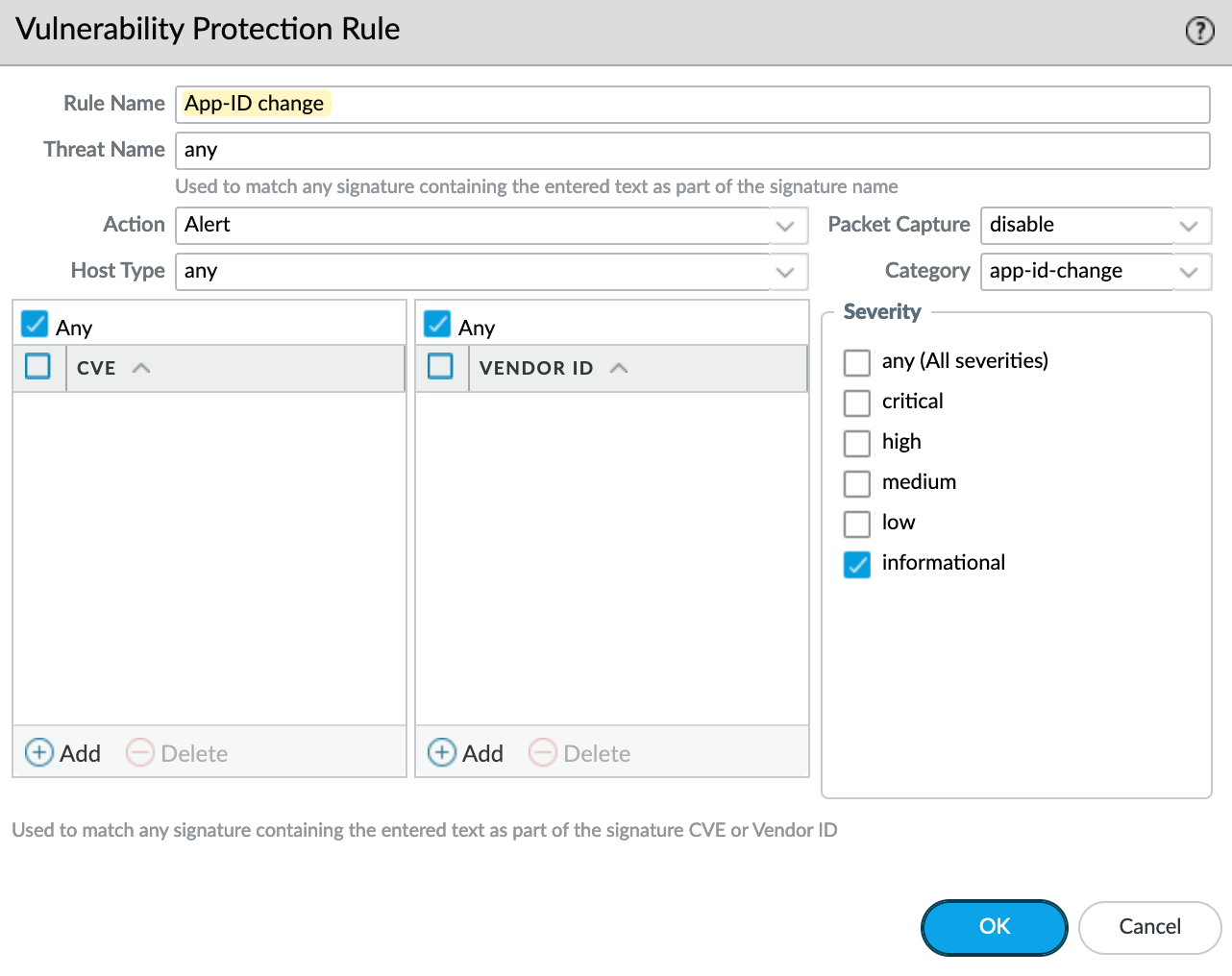
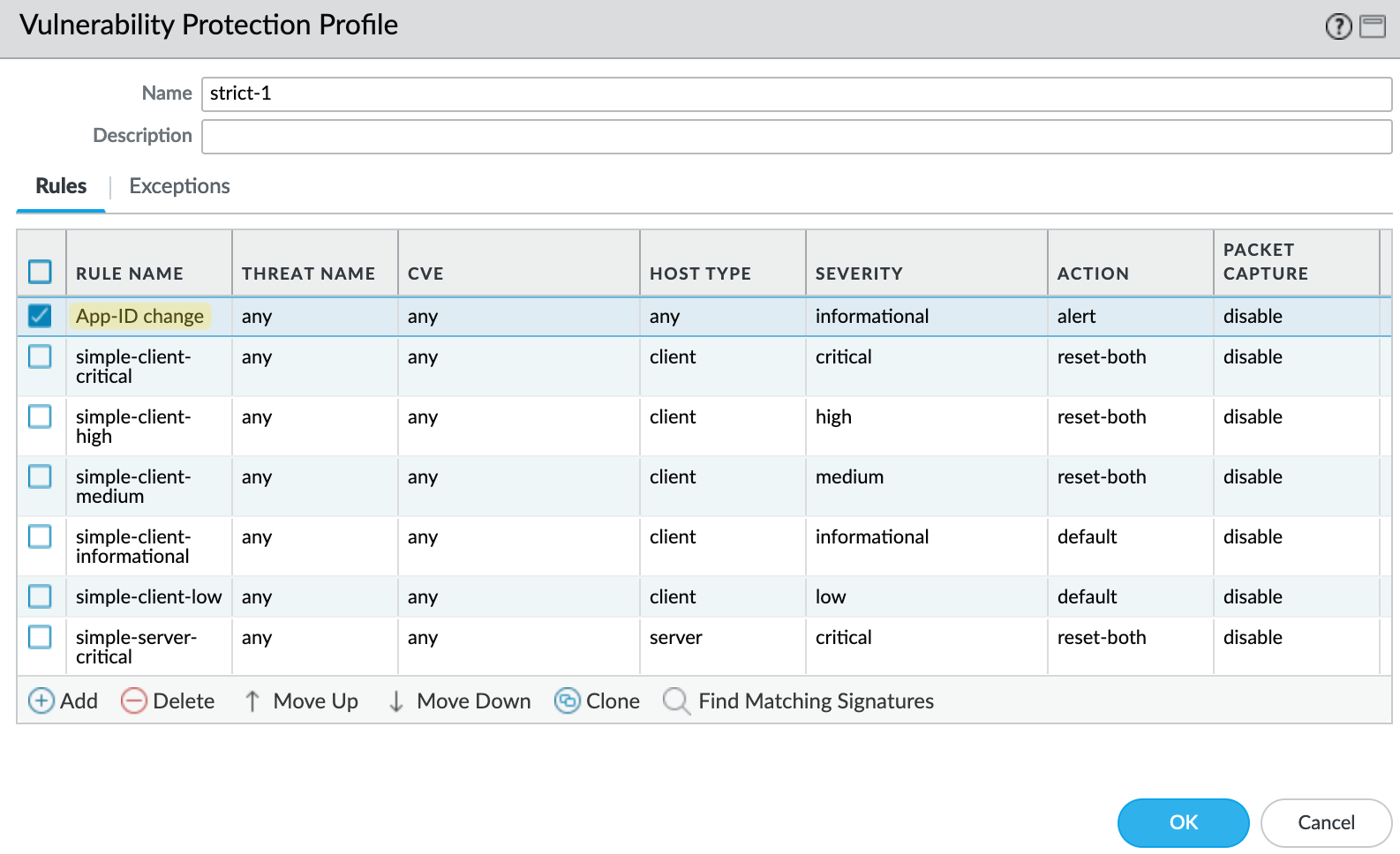
Make sure to move this rule to the very top of your profile.
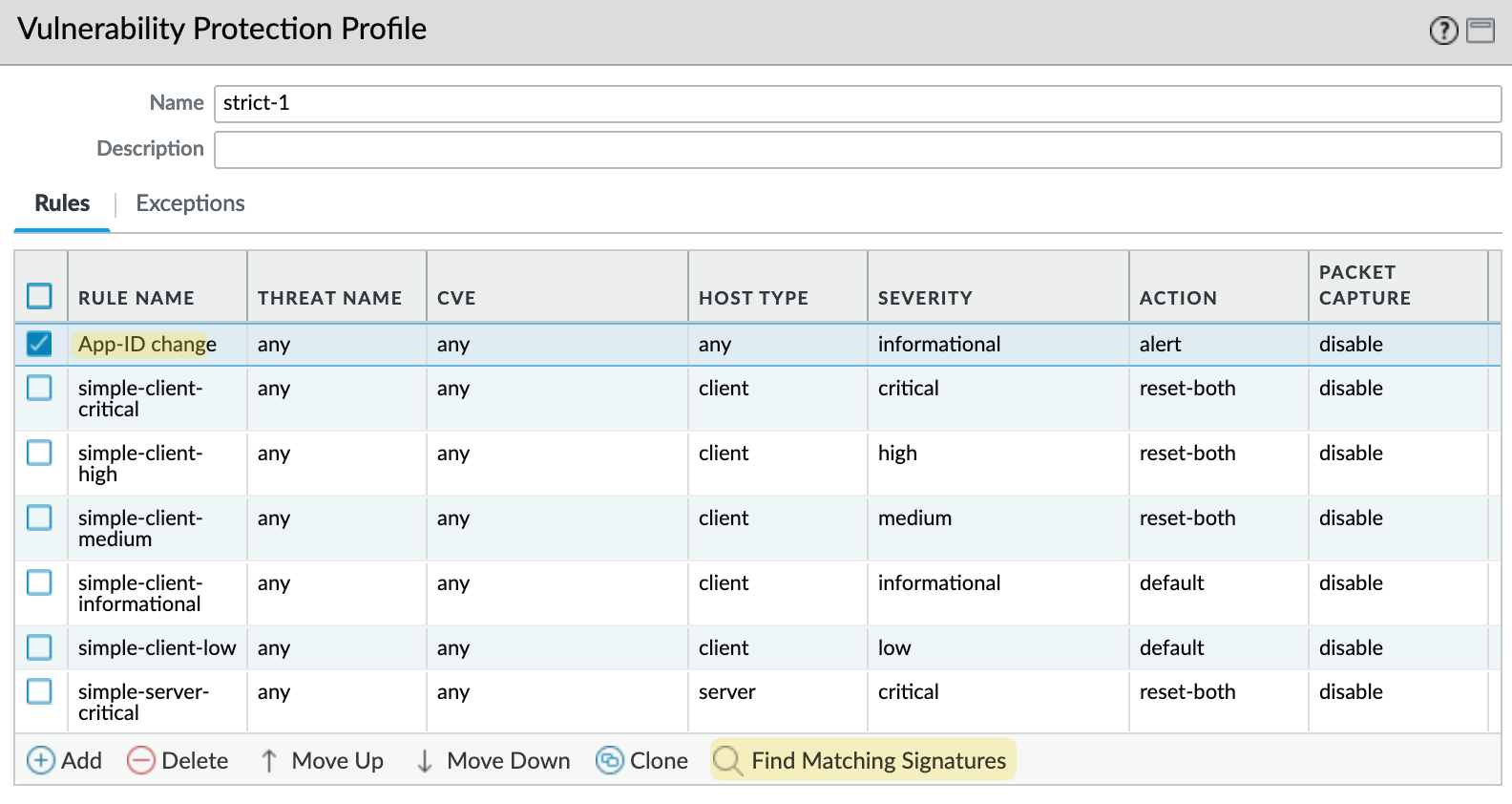
If you click on 'Find Matching Signatures', it will list the upcoming App-ID changes.
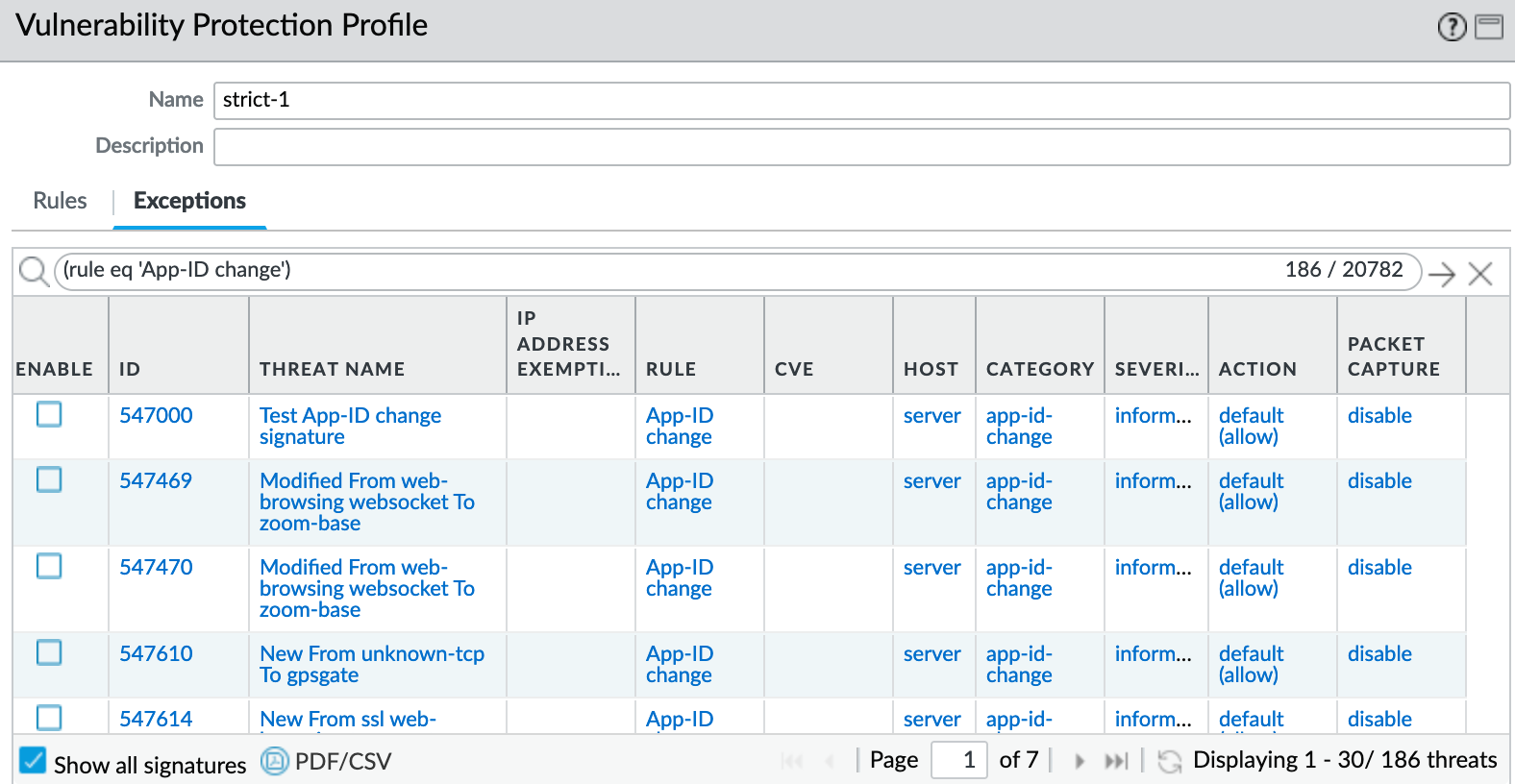
You then need to attach this security profile to all of the security policies that use App-IDs. Here in my example, I use a Security Profile Group and referenced this profile there. I then attached this profile group to all of my security rules.
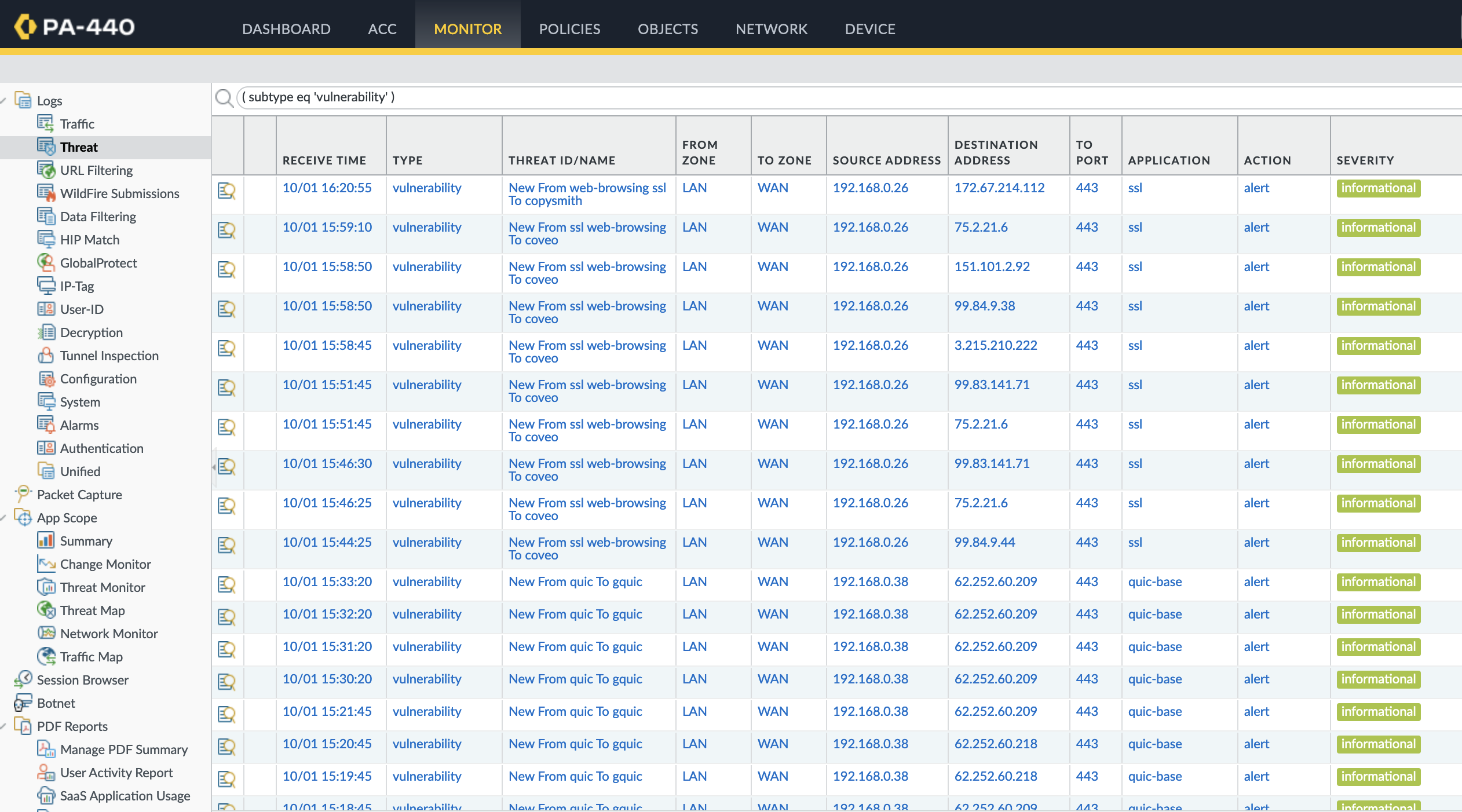
That's all for now. Wait for the traffic to flow and navigate to Monitor > Threat to view all the possible App-ID changes.
Creating Custom Reports
You can also create a custom report to easily view what's going to change. Navigate to Monitor > Custom Report and create a new report as shown below.
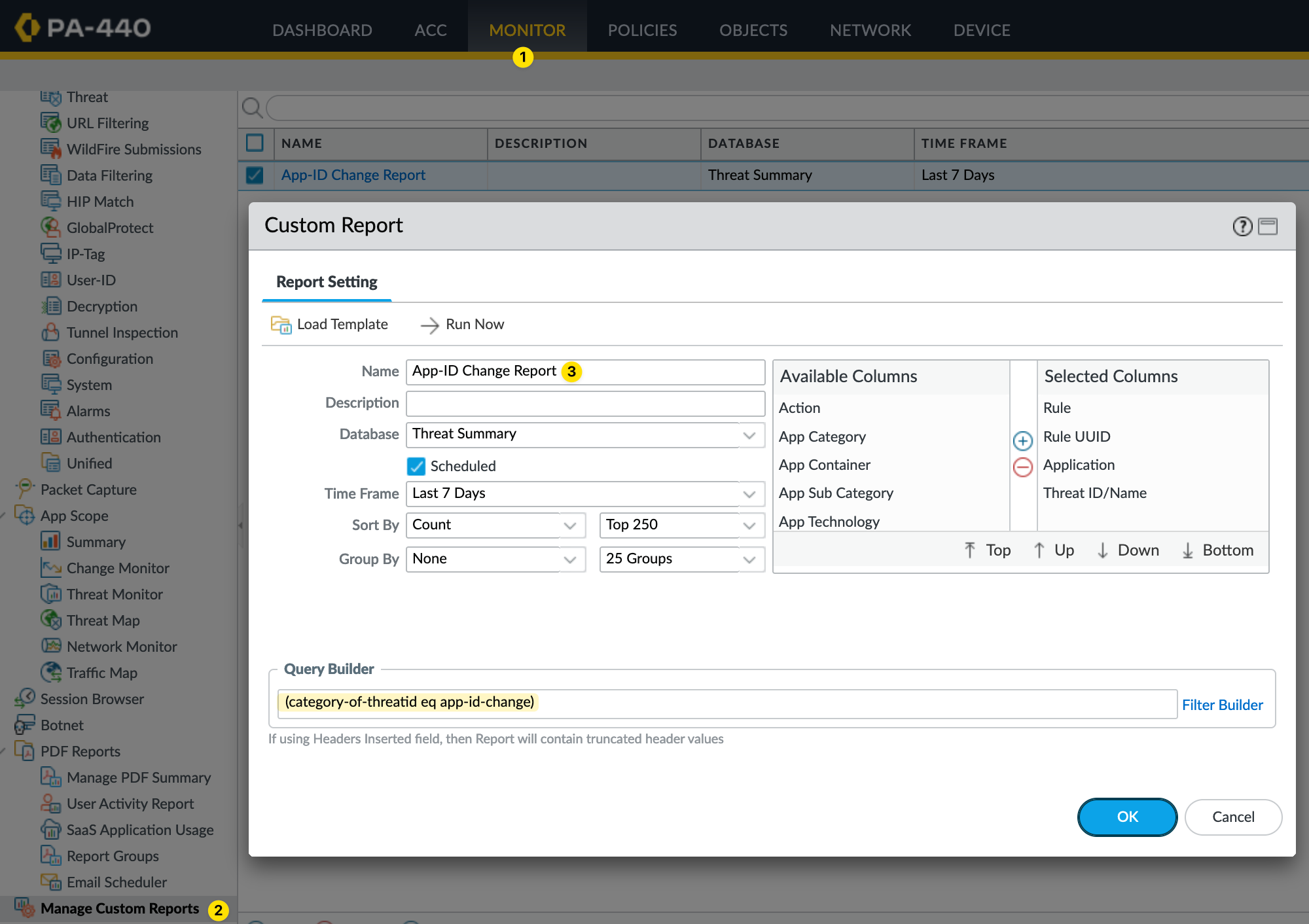
Once the report is set up, wait for the traffic to flow and click on 'Run Now'. This will show you the rules that are affected and what will change with the new App-ID update.