If you use URL filtering on your Palo Alto firewalls, you may come across situations where a specific URL category is set to block, but you need to allow certain sites. For example, you might block the 'social networking' category but still want to allow access to Facebook. Similarly, you may block 'newly registered domains,' but need immediate access to a site categorized as such. While you can request Palo Alto to re-categorize the site, sometimes you need a quicker solution.
In this blog post, we'll look at how to allow access to specific URLs that match a blocked URL category. There are two ways to achieve this, and I’ll cover both.

A Quick Recap on URL Filtering
This blog post assumes you have some familiarity with URL filtering. In a typical setup, you create a URL Filtering profile, configure the categories to allow or block, and attach this profile to your security policies. For instance, if you block the 'proxy-avoidance' category and try to access a site like expressvpn.com, the traffic will be blocked.
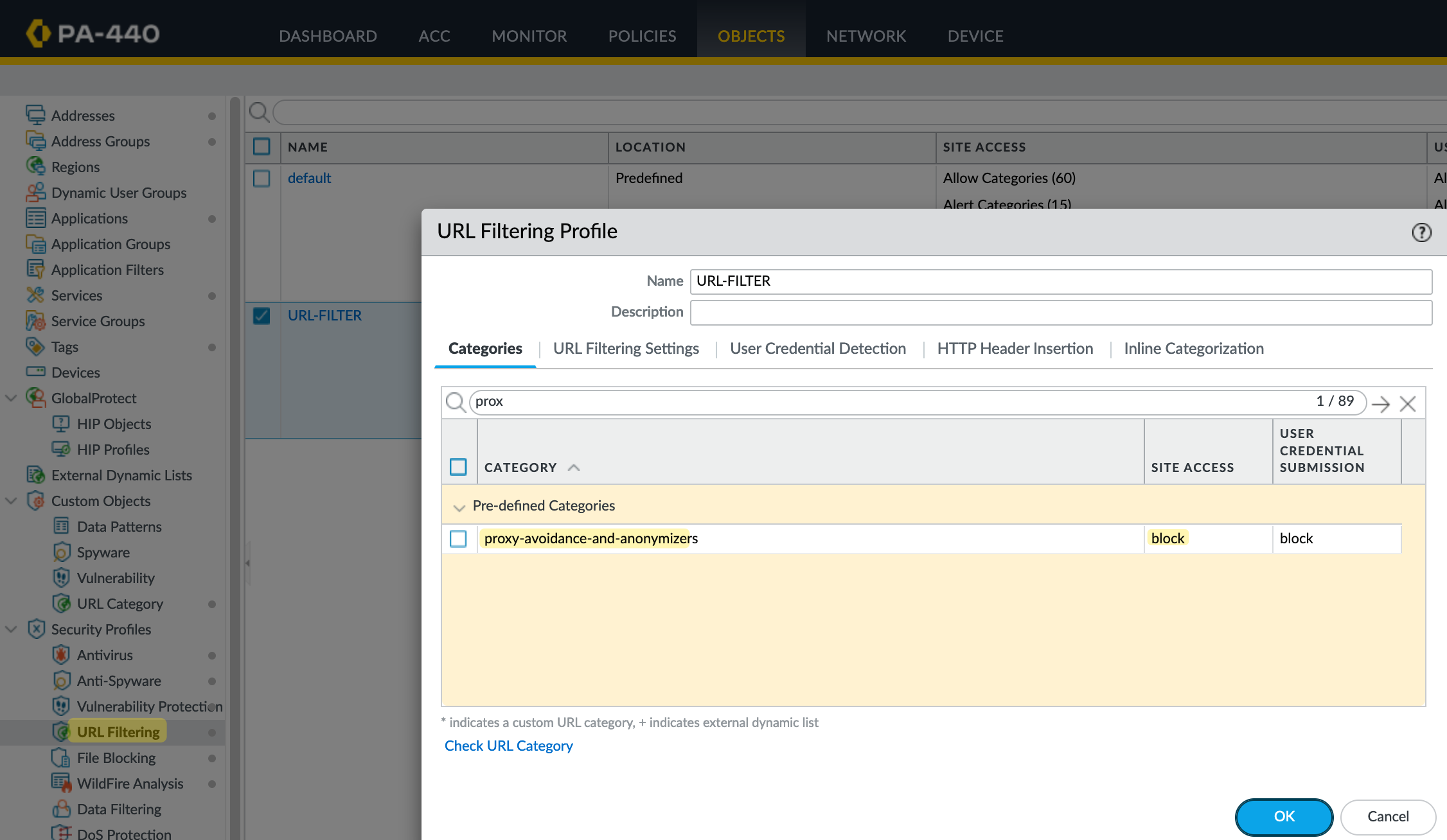
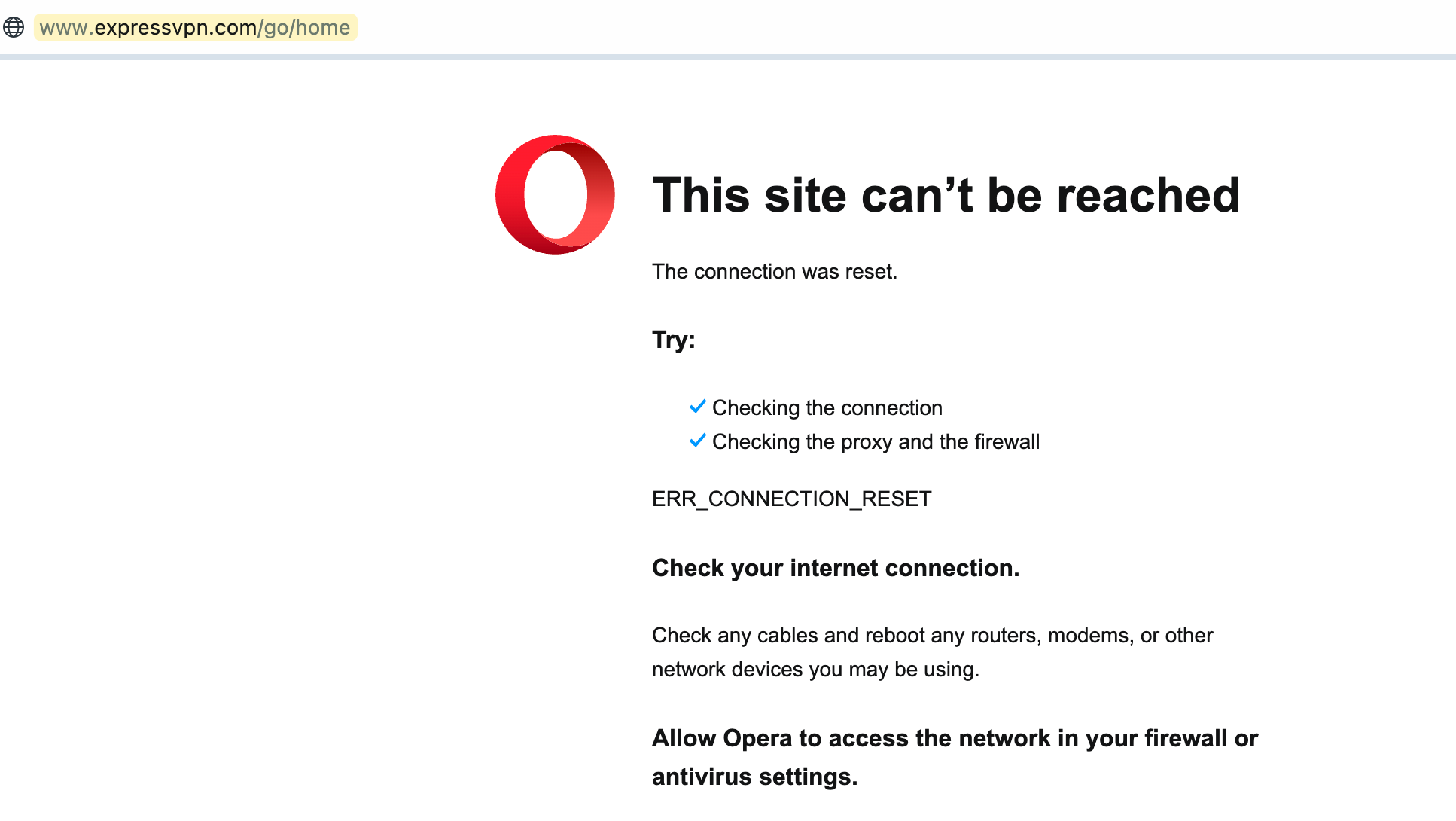
To demonstrate this, I'll set the 'proxy-avoidance' category to block. This means that if I try to access expressvpn.com, it will be blocked. Next, we'll look at how to allow this specific site while keeping the rest blocked. As mentioned earlier, there are two ways to achieve this, but I usually prefer the first method. Let’s explore both examples.
Method 1 - Allow the Site in URL Filtering Profile
First, define the URL in a URL Category. To do this, navigate to Objects > Custom Objects > URL Category. Regardless of the method you choose, this step is required.
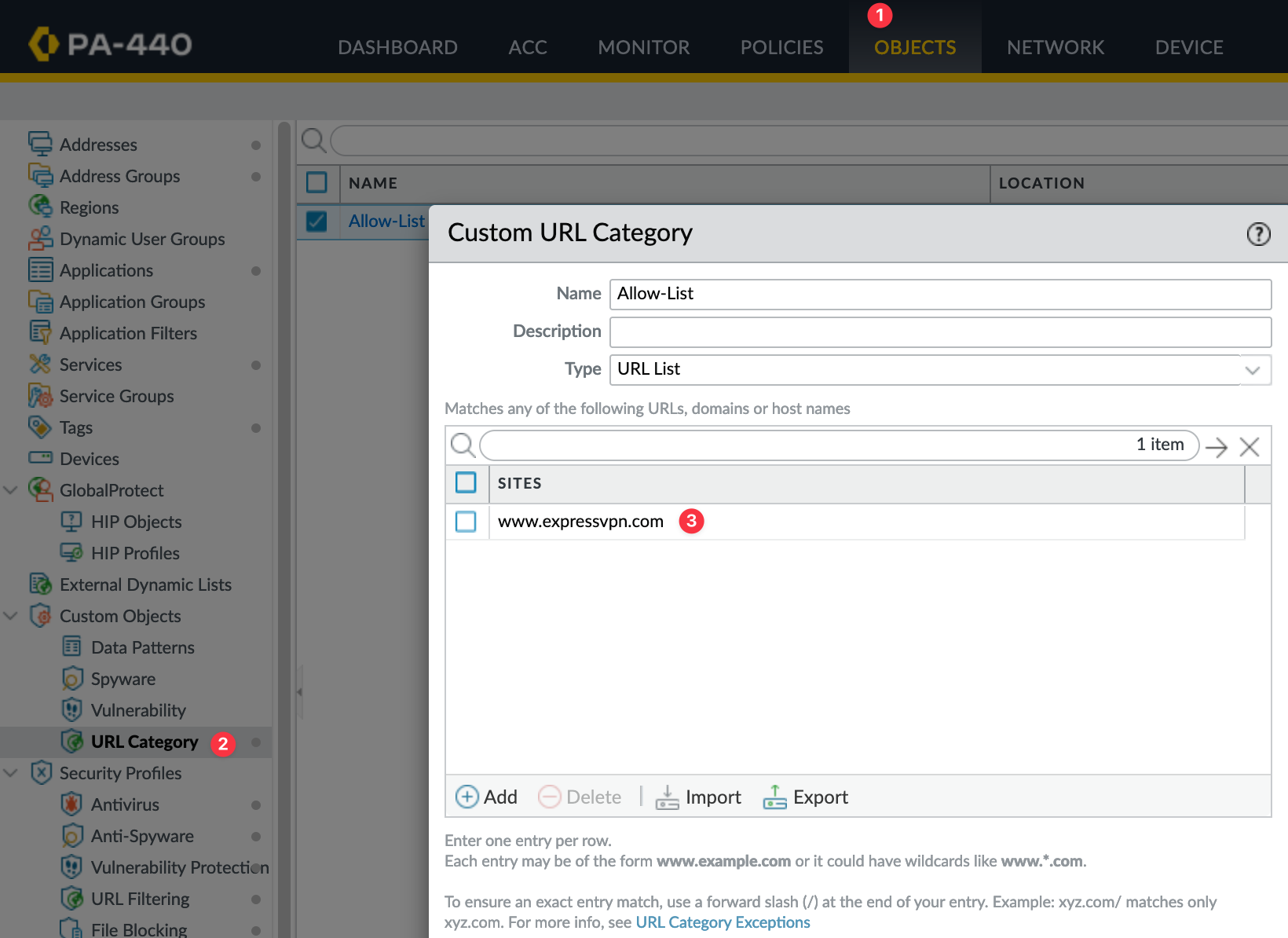
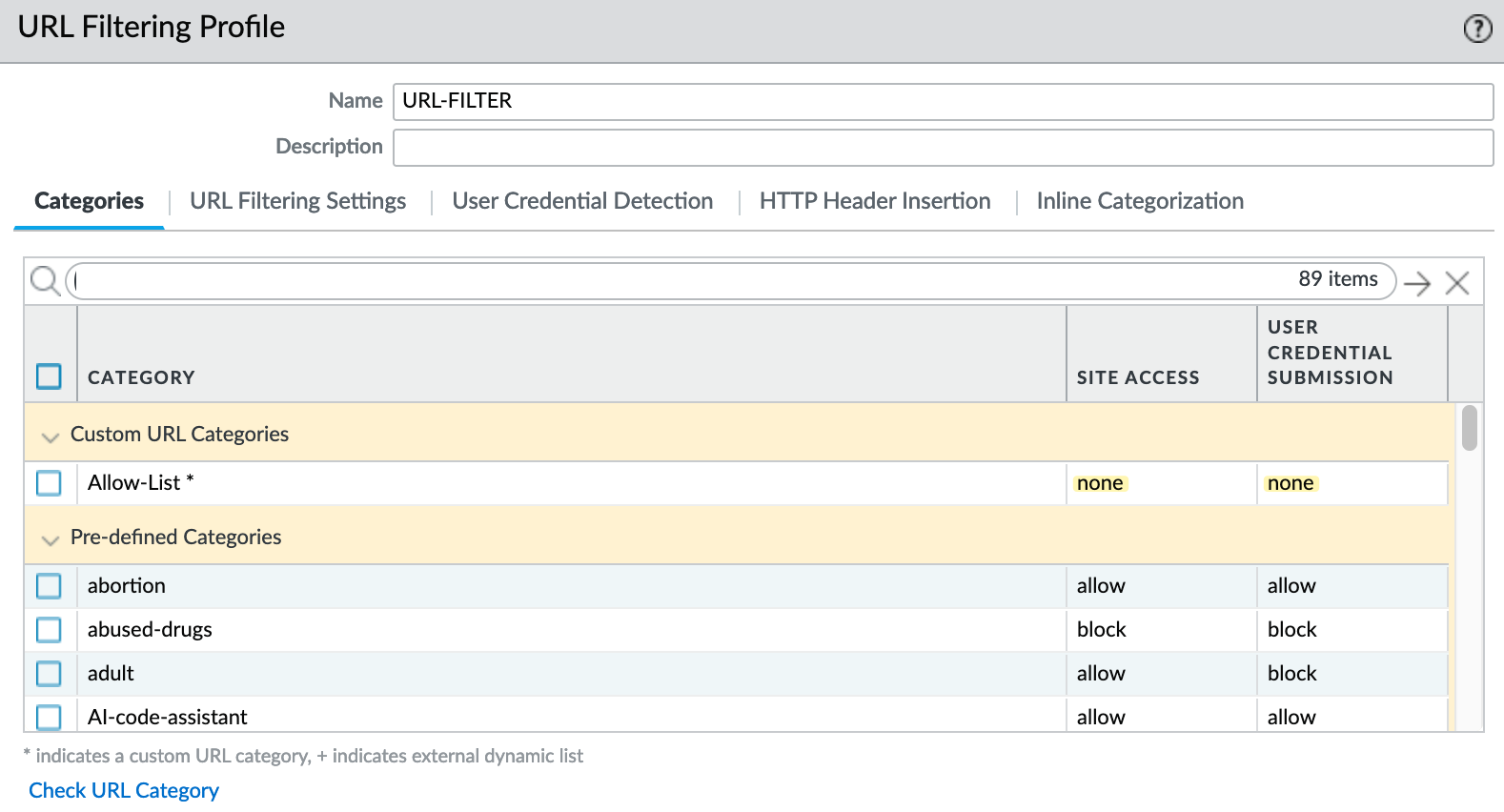
Here, create a new Custom URL Category. I usually name it 'Allow List' and include all exceptions here, but you can also maintain multiple lists if needed. Add expressvpn.com to this list. You can also use a wildcard, like *.expressvpn.*, for broader matches. If you want to match a specific URL, such as www.expressvpn.com/, you can include the forward slash at the end.
Once the custom URL category is created, it will appear in your URL Filtering profile. By default, the access is set to 'none.' Change this to 'allow,' and users will now have access to expressvpn.com.
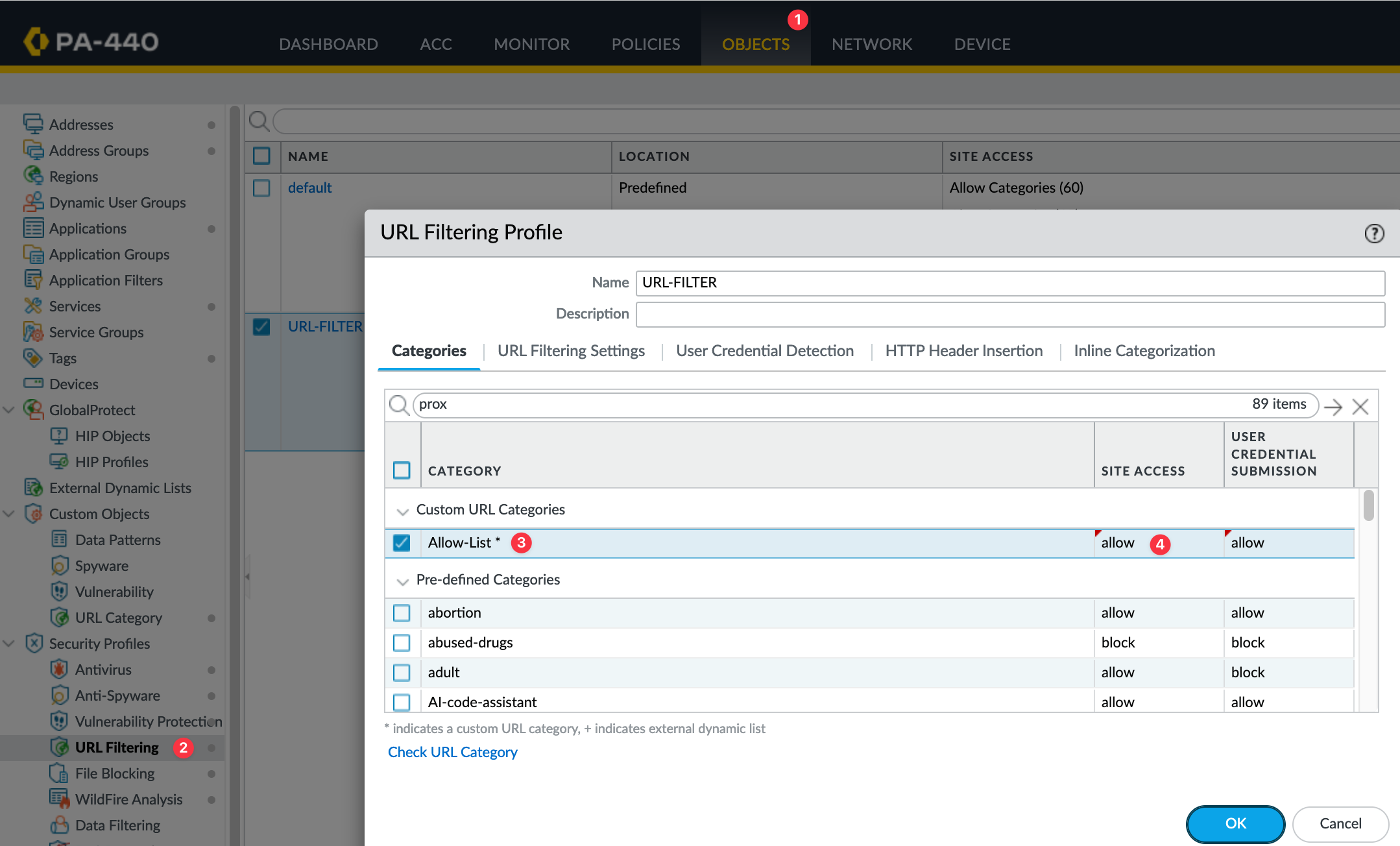
In the future, if you need to allow additional sites, simply add them to the Custom URL Category list.

Method 2 - Create a New Security Policy
The second method involves creating a new security policy, which should be placed above your existing one. You’ll still need the Custom URL Category created in the first method. However, you can revert the access setting for the category in the URL Filtering profile back to 'none.'
Next, create a new security policy where you can define the Source and Destination as usual. Under Service/URL Category, add the custom URL category. Make sure not to apply the URL Filtering profile to this rule. This way, when someone tries to access expressvpn.com, the traffic will match this policy and be allowed through.
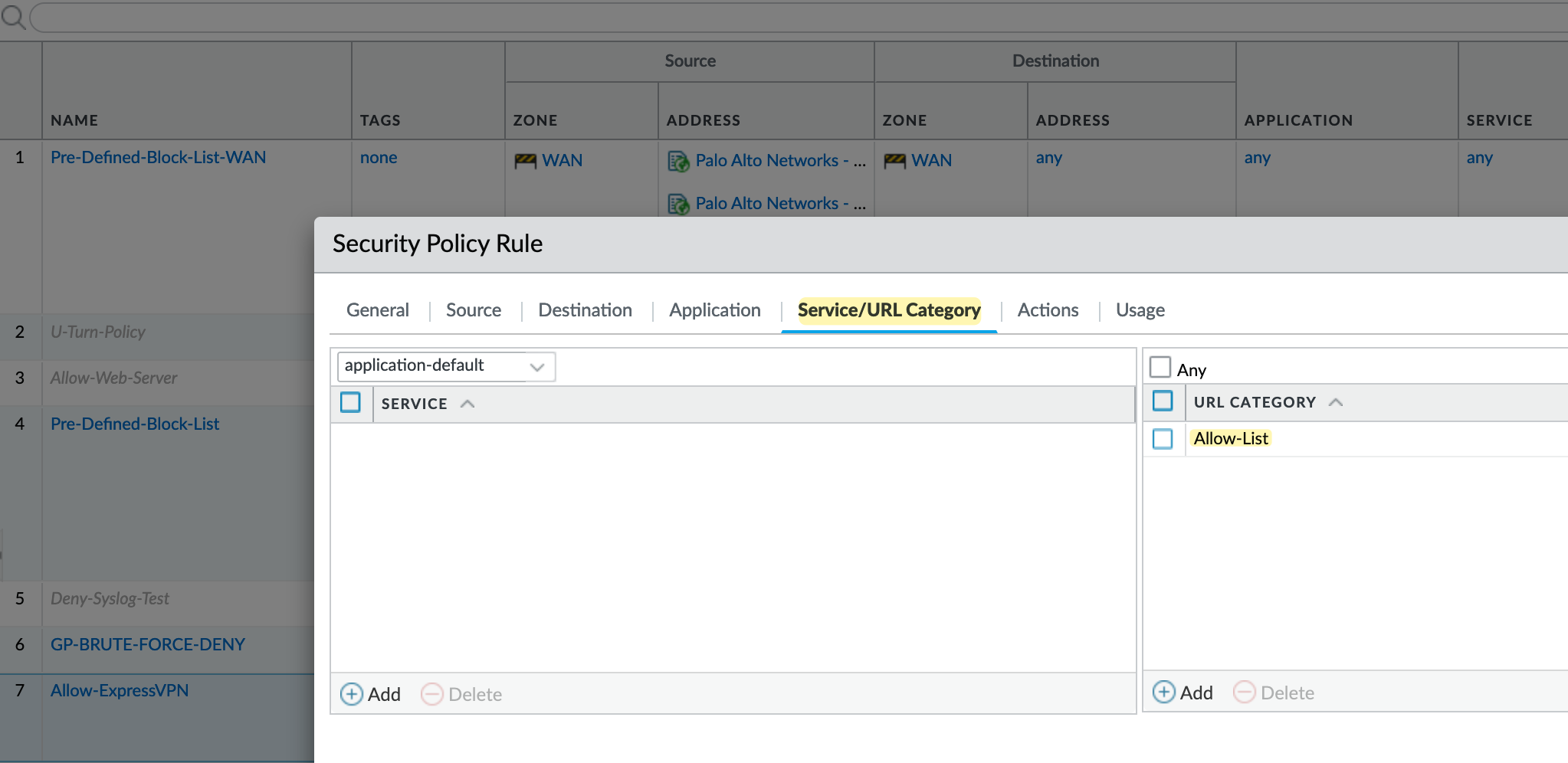
If you attach the URL Filtering profile to this rule, the traffic will still be blocked, even if the custom URL category is added, due to the URL filtering profile's settings.










