Most websites we access today use HTTPS, and to fully leverage a Next-Generation Firewall (NGFW) like Palo Alto, inspecting encrypted HTTPS sessions is crucial. Configuring SSL decryption isn't just a set-it-and-forget-it task. It requires careful consideration and ongoing improvements. In this blog post, we'll explore how to configure SSL decryption in Palo Alto firewalls and highlight some pitfalls to be aware of. So, let's get to it.
As always, if you find this post helpful, press the ‘clap’ button on the left. It means a lot to me and helps me know you enjoy this type of content.

SSL Decryption Considerations
As I mentioned earlier, configuring SSL decryption isn’t as simple as flipping a switch. Decryption allows your firewall to inspect the contents of encrypted sessions. Normally, HTTPS traffic is encrypted from your browser to the server, ensuring the sessions are private. However, with SSL decryption, the firewall acts as a man-in-the-middle, inspecting the traffic in plain text. It’s crucial to be selective about what you decrypt to avoid sensitive areas such as personal finance, law or medical-related sites and to comply with local laws.
You might start by decrypting traffic from a few categories and expand gradually, or exclude certain categories and decrypt the rest. Keep in mind that some sites can detect man-in-the-middle scenarios and may not function correctly. This might lead you to frequently add these sites to your exclusion list.
Nevertheless, SSL decryption enables more detailed traffic inspection. For example, you could permit access to Google Drive but block file uploads, or allow Facebook but disable chat.

Certificates Certificates Certificates
Before we dive into configuring SSL decryption, let's focus on the critical role of certificates. Understanding this will make the setup process much clearer.
When you visit a secure website like bbc.co.uk, the site presents a digital certificate to your browser. This certificate acts as a form of digital identity, issued by a recognized Certificate Authority (CA). Your browser has a pre-installed list of these trusted CAs. If the certificate from bbc.co.uk is signed by one of these trusted CAs, your browser accepts the certificate, confirming that the site is who it claims to be.
With SSL decryption, the setup changes slightly. When you attempt to access a site, like bbc.co.uk, your connection is first intercepted by your firewall. The firewall then establishes its own connection to bbc.co.uk. To maintain trust, the firewall generates a certificate for bbc.co.uk on-the-fly, signs it with an internal CA certificate, and presents it to your browser. It's important to note that this is not the actual certificate from bbc.co.uk, but a substitute that allows the firewall to decrypt and inspect the traffic securely. This means your device also needs to trust the firewall’s CA certificate.
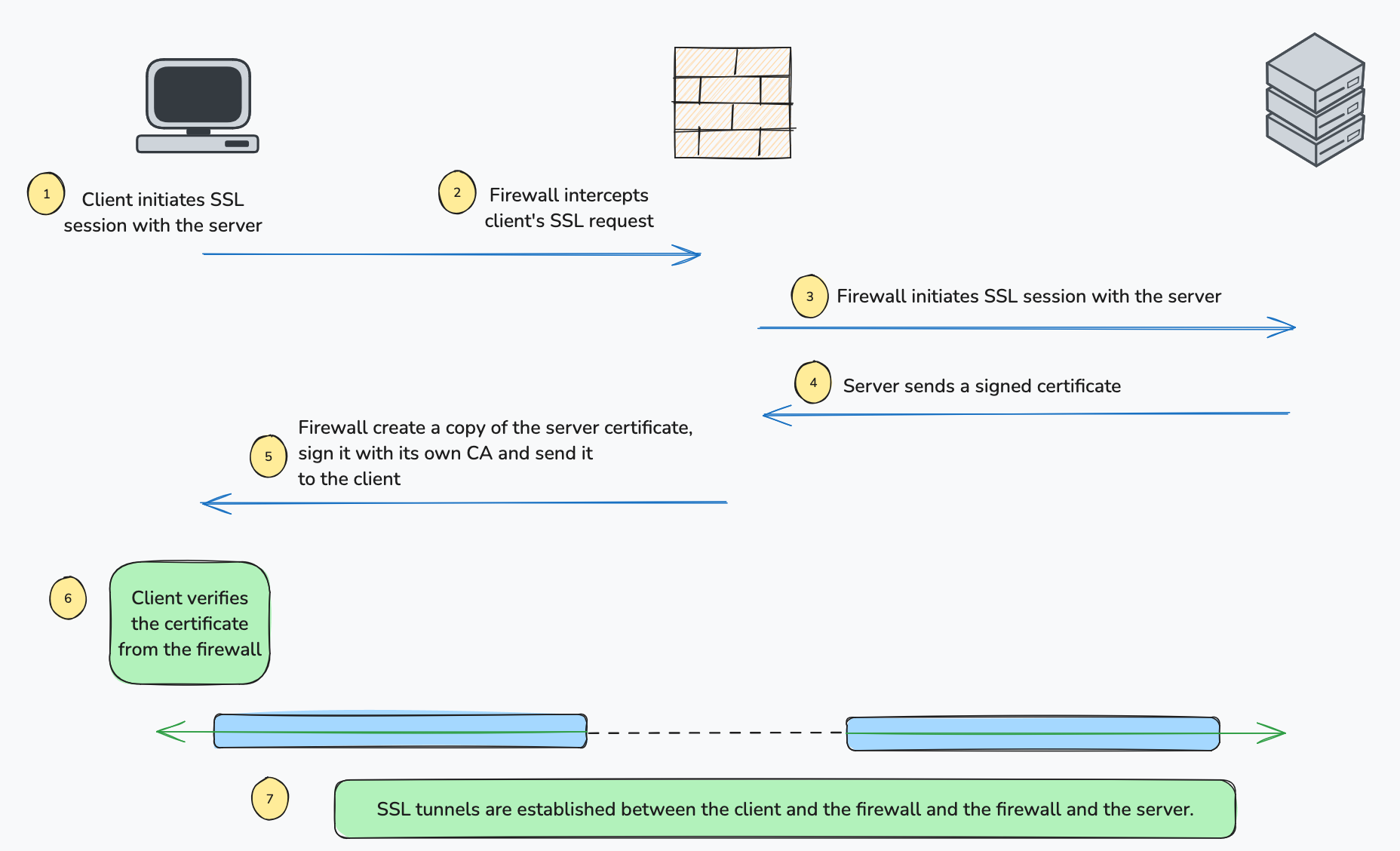
In many enterprises, there's a Public Key Infrastructure (PKI) that manages these certificates. The firewall needs a certificate signed by this private PKI, which needs to be a subordinate CA. This allows the firewall to create and sign certificates. the client devices also need to trust the root CA.
In my home lab, I'll create a root CA directly on the firewall (rather than using an internal PKI) and import this certificate into my client machine, telling it to trust this new CA. From there, I'll also generate a subordinate CA on the firewall and have it signed by the Root CA.
Let's talk about the two types of certificates we need for SSL decryption and why they are important.
Forward Trust
This is the certificate the firewall presents to clients during decryption if the site the client is attempting to connect to has a certificate signed by a CA that the firewall trusts.
Forward Untrust
This is the certificate the firewall presents during decryption if the site the client is trying to connect to has a certificate signed by a CA that the firewall does not trust. You’ve likely come across some sites where the browser does not trust the site’s certificate.
Configure Certificates
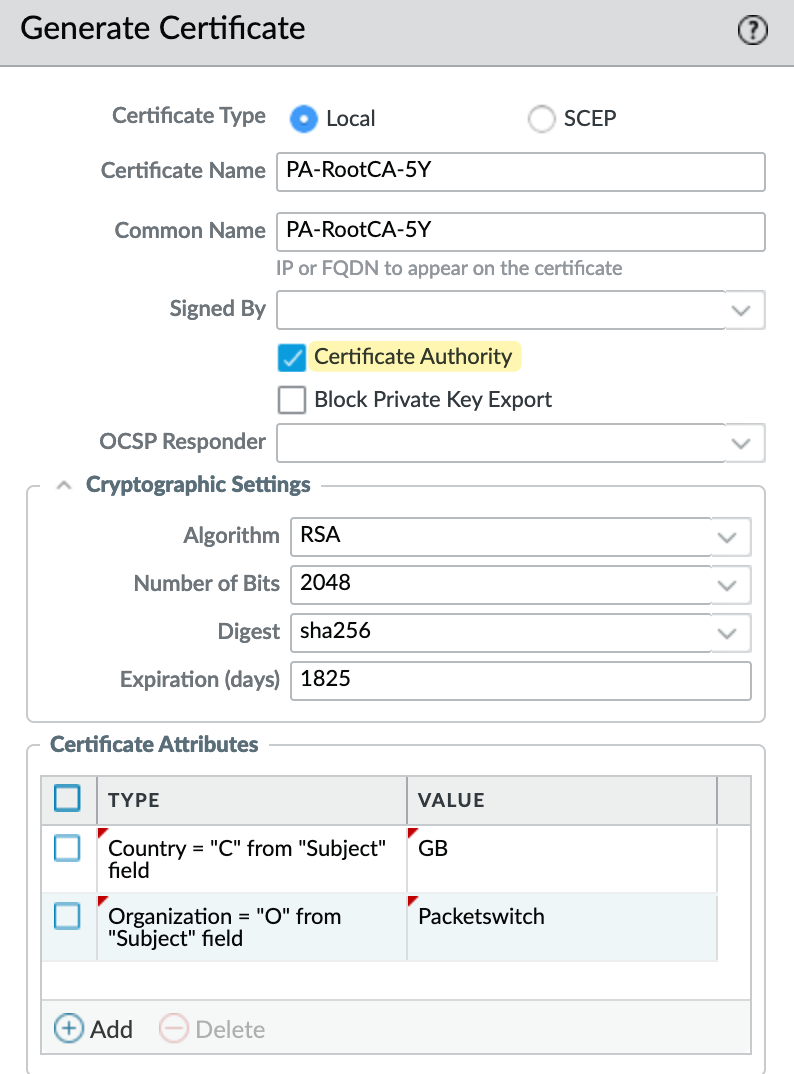
As I mentioned before, I'm generating a root certificate on the firewall, this acts as the top-level CA. Navigate to Device > Certificates and click on Generate
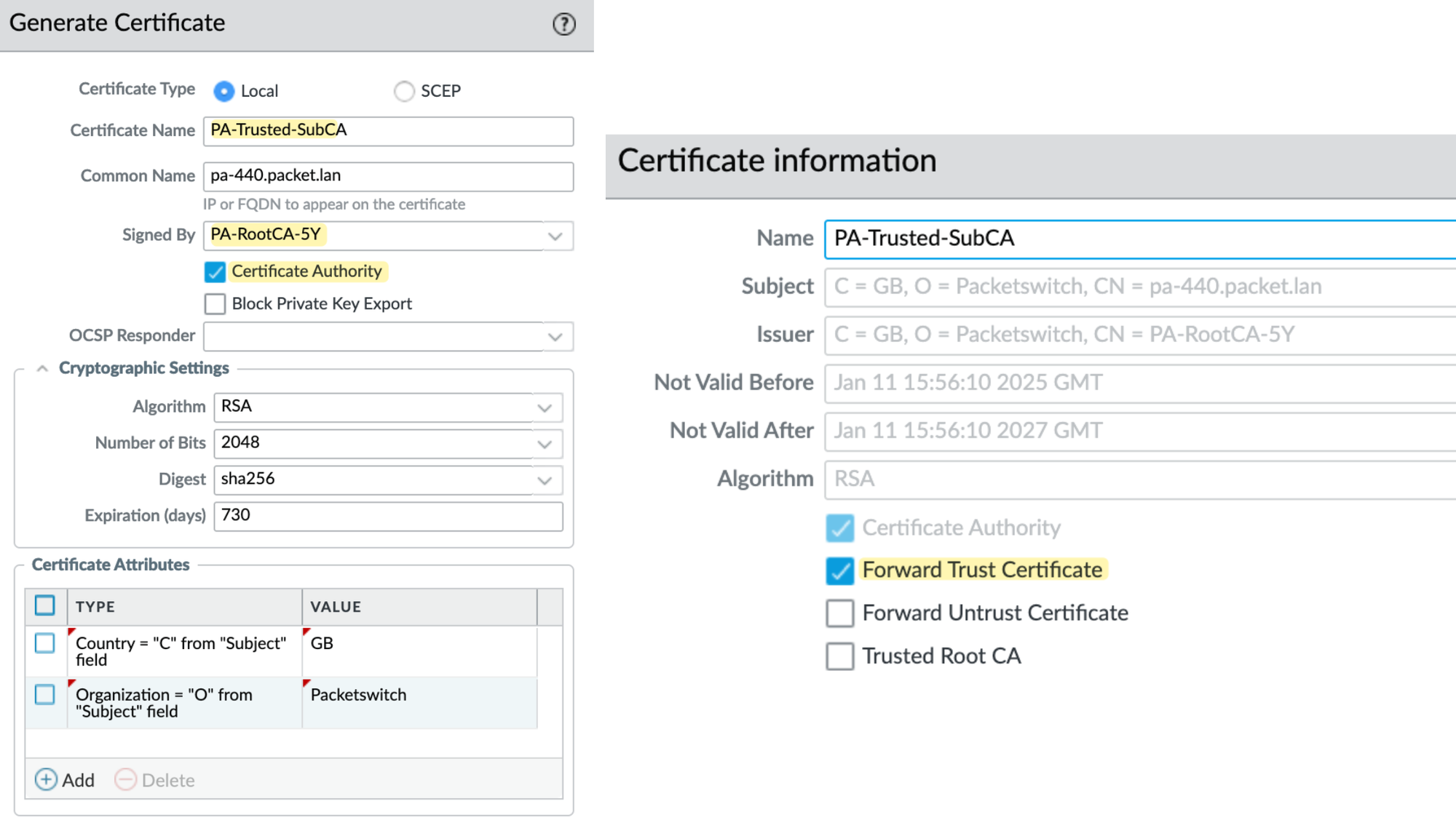
Next, I create a subordinate CA certificate and have it signed by the root CA we created in the previous step. Once the certificate is generated, open it and make it a 'Forward Trust Certificate'
Additionally, we need to create another root certificate specifically for untrusted sites. Once created, mark it as a 'Forward Untrust Certificate'. Navigate to Device > Certificates and click on Generate.
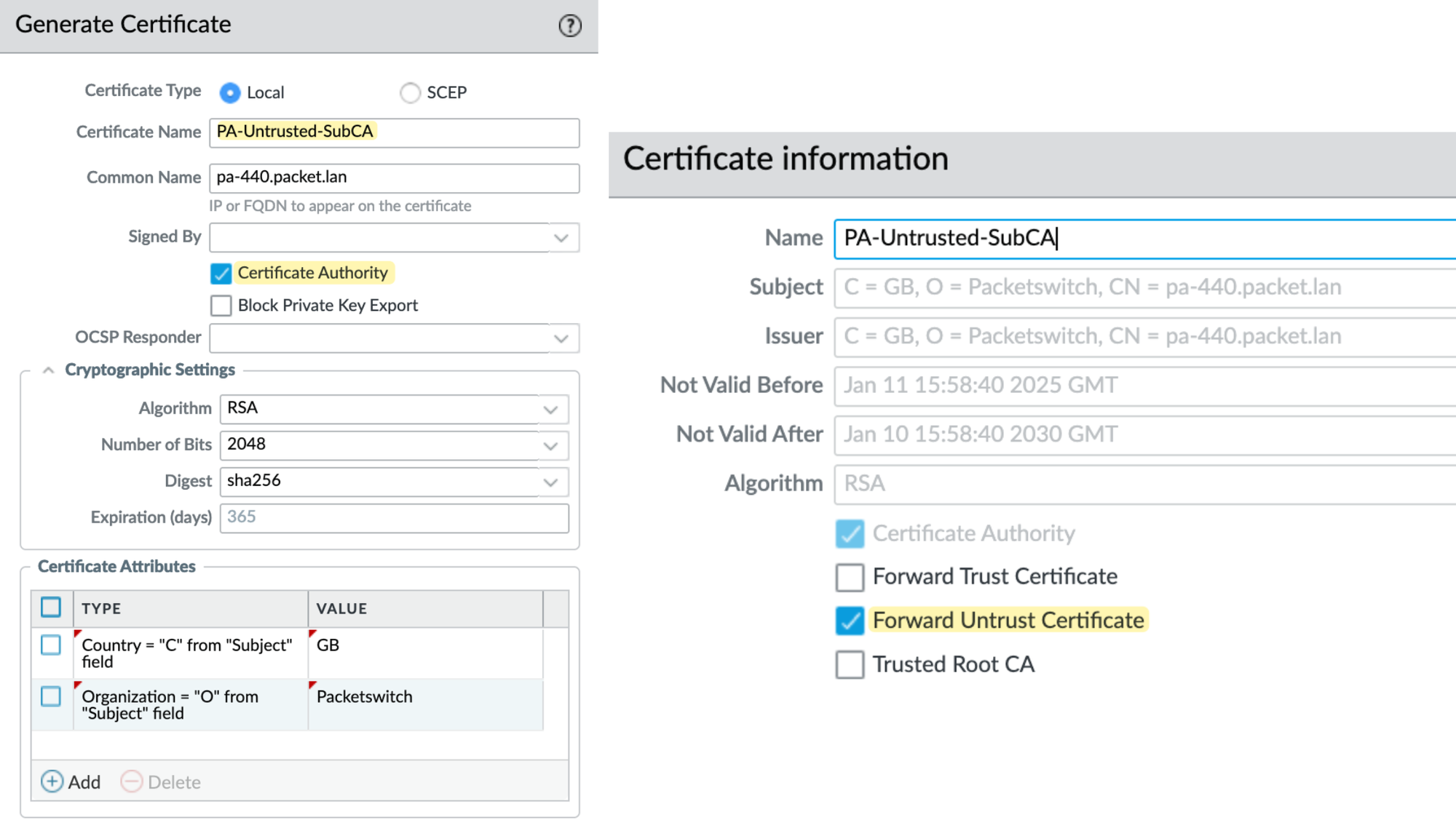
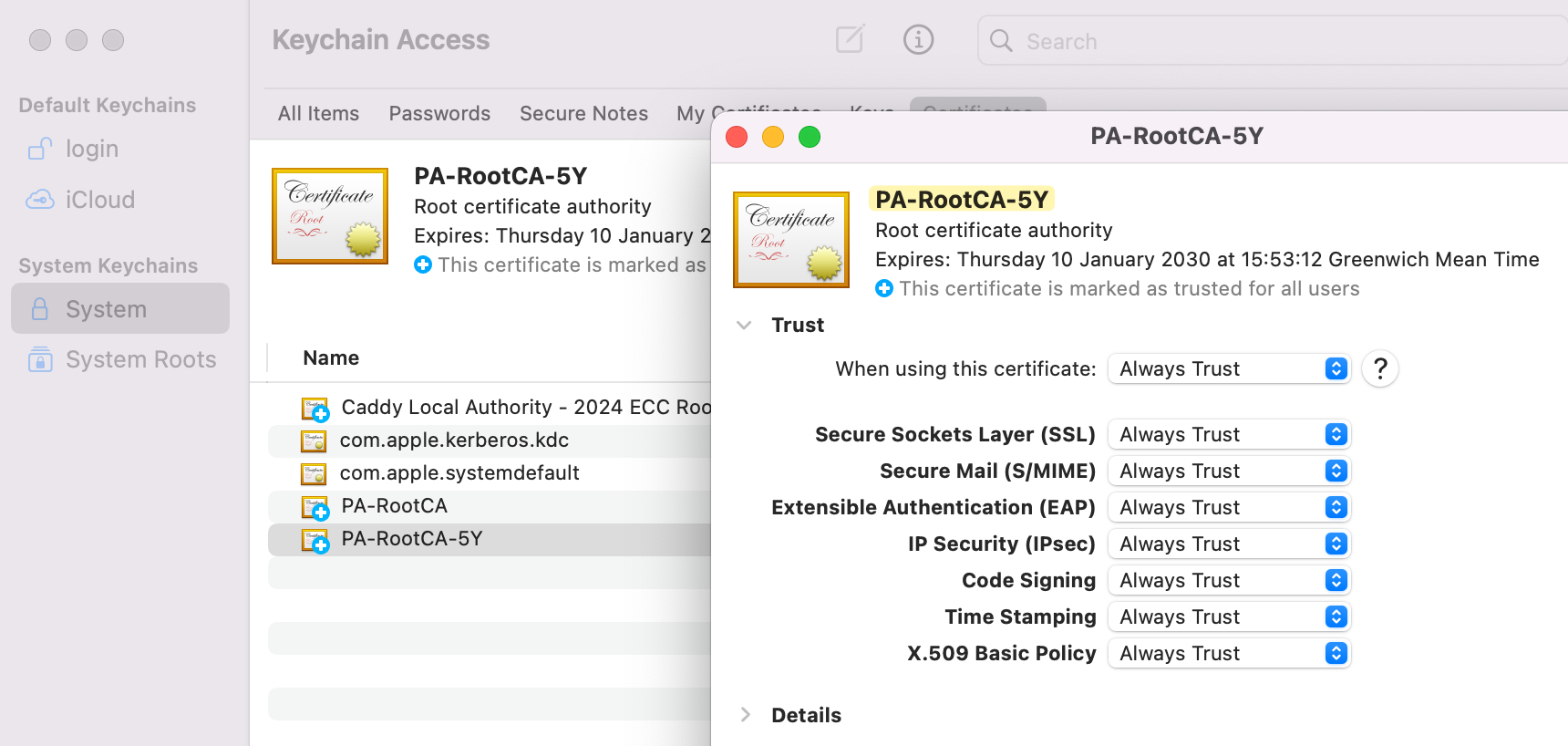
Here is the list of certificates we just created.

Please remember that the root CA (named 'PA-RootCA-5Y' in our example) must be imported to all client machines. In most organizations, if you already have a PKI, the certificates can be pushed to devices via MDM solutions or Group Policy Objects (GPO). This ensures that all devices within the network automatically trust the certificates issued by your firewall. Here in my example, I'm importing this root CA into my MacBook.
Decryption Profile
A decryption profile allows you to perform checks on both decrypted traffic and SSL traffic that you choose to exclude from decryption. I'm just going to create a profile as shown below. You can create a Decryption Profile by navigating to Objects > Decryption > Decryption Profile.
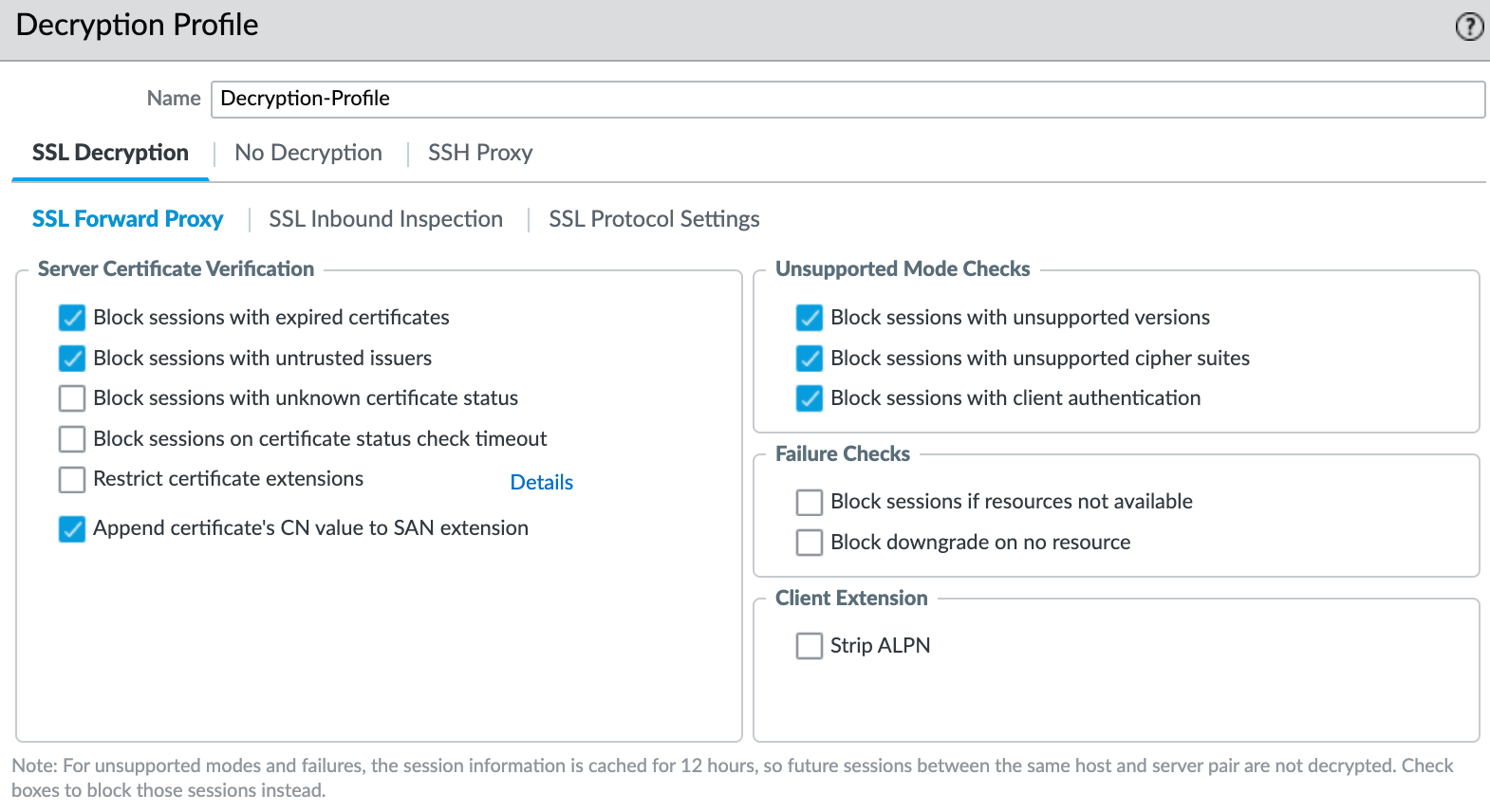
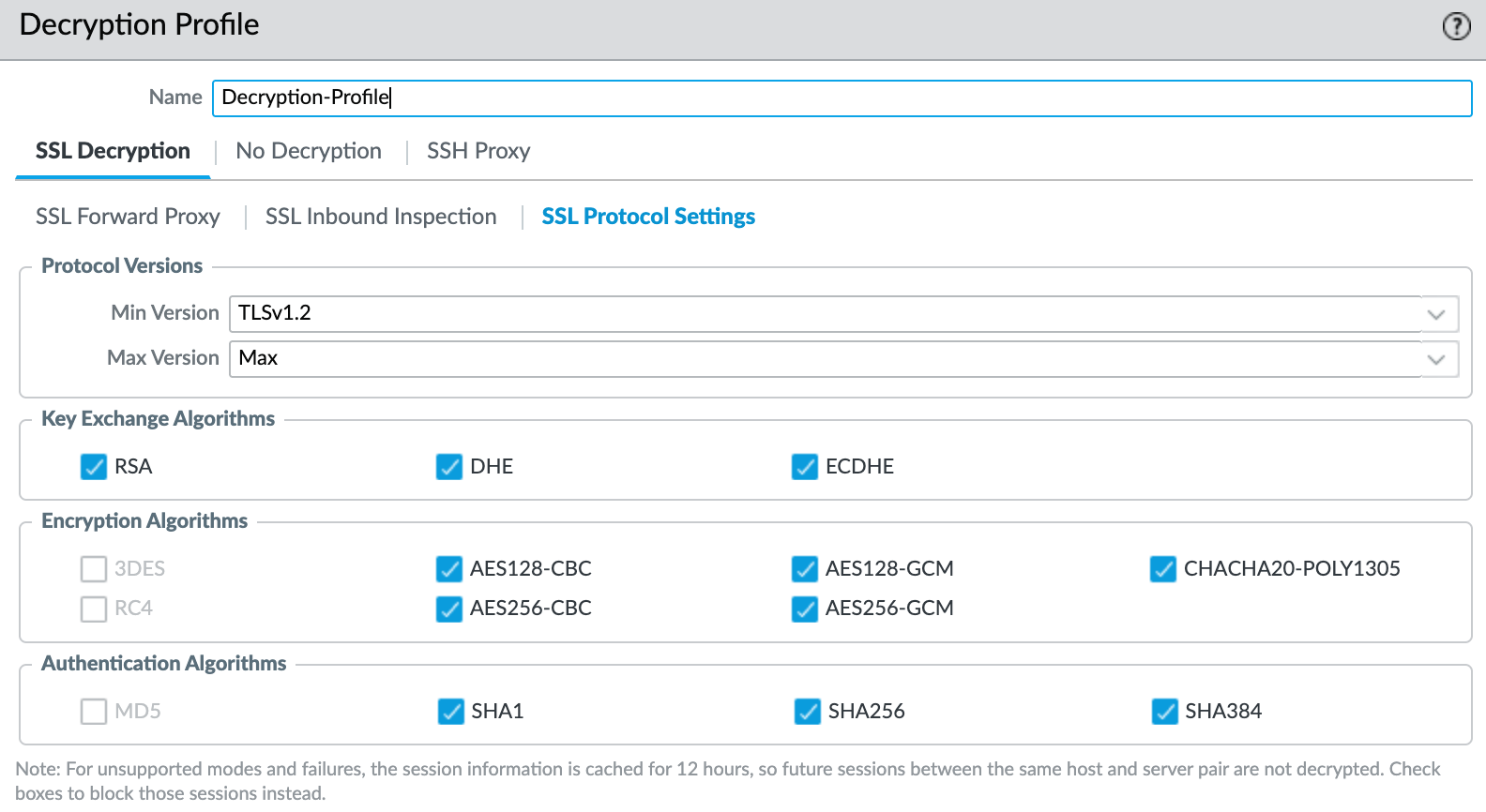
I recommend referring to the official guide to understand what each section does and go with whatever suits your environment.
Decryption Policy
A Decryption Policy rule allows you to define the traffic that you want the firewall to decrypt and to define the traffic that you choose to exclude from decryption. You can create a Decryption Policy by navigating to Policies > Decryption.
In our example, I'm going to decrypt the traffic matching the URL category 'news', 'high-risk, 'medium-risk' and 'questionable'. In the decryption policy, I'll set the source as just my laptop, the destination IP to 'any', and specify the URL category as shown below. The action will be 'decrypt'. For the type, select SSL Forward Proxy and select the decryption profile we created earlier.
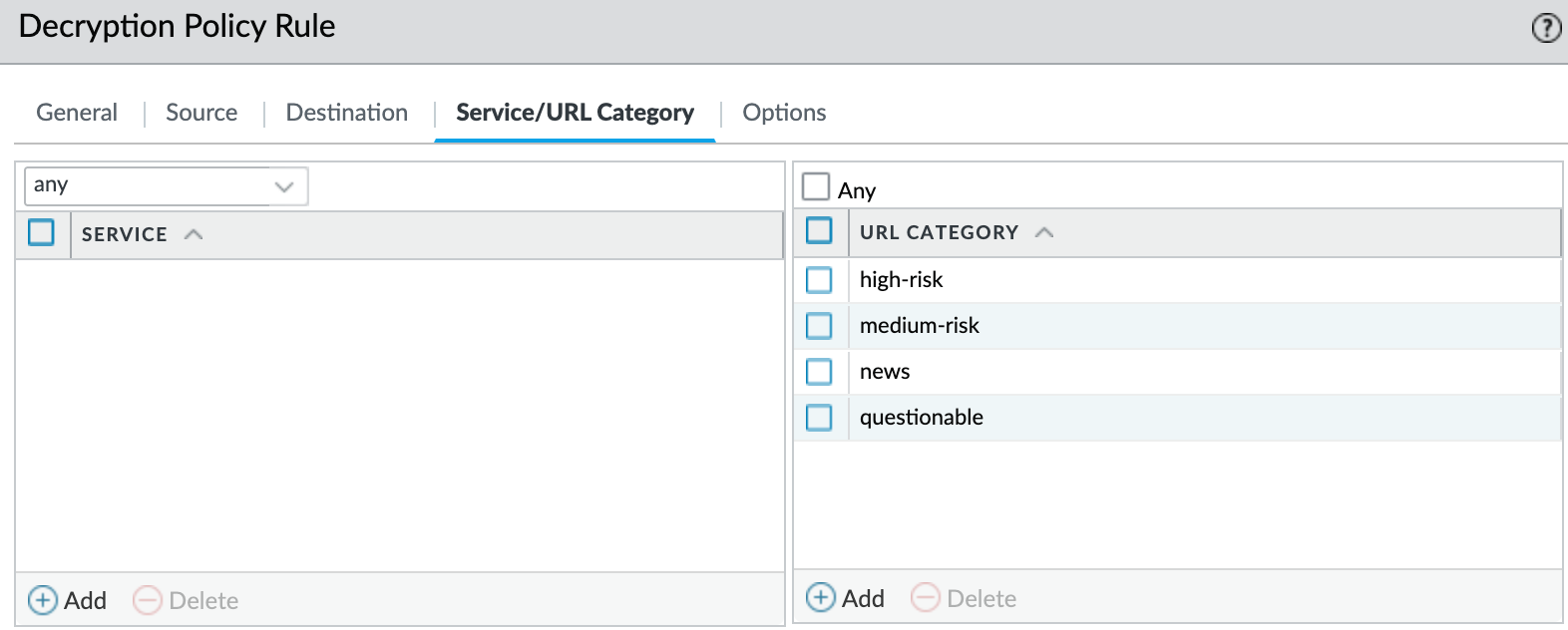
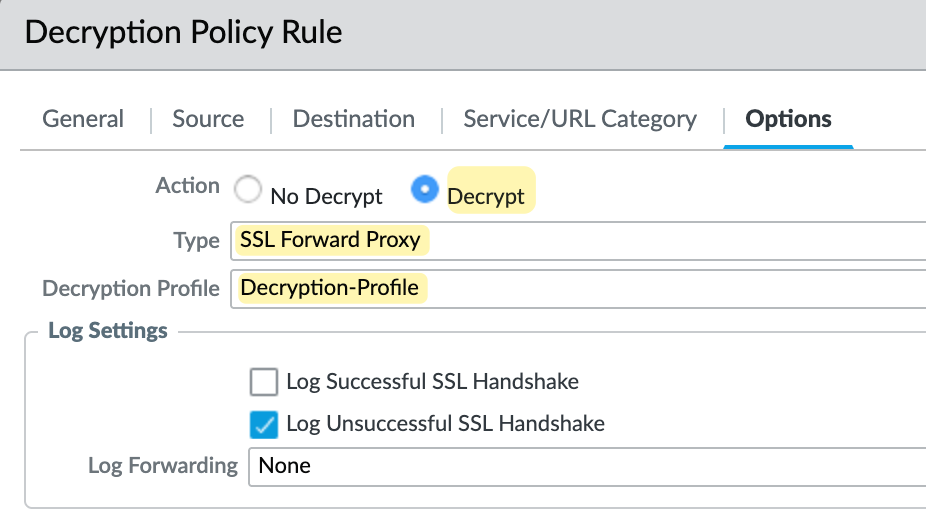
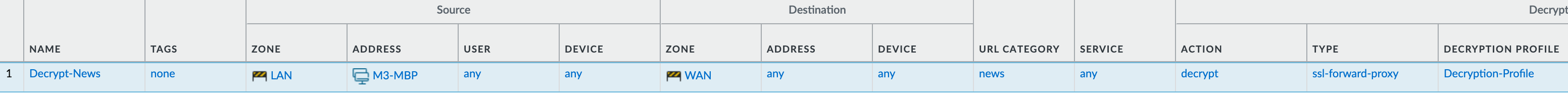
So now, every time I access a site classified as 'news', 'high-risk, 'medium-risk' and 'questionable', the traffic will be decrypted. I can also create a policy with the action 'no decrypt' for certain exclusions, such as personal finance or medical sites. Then, I can create another policy below it to 'decrypt' everything else.
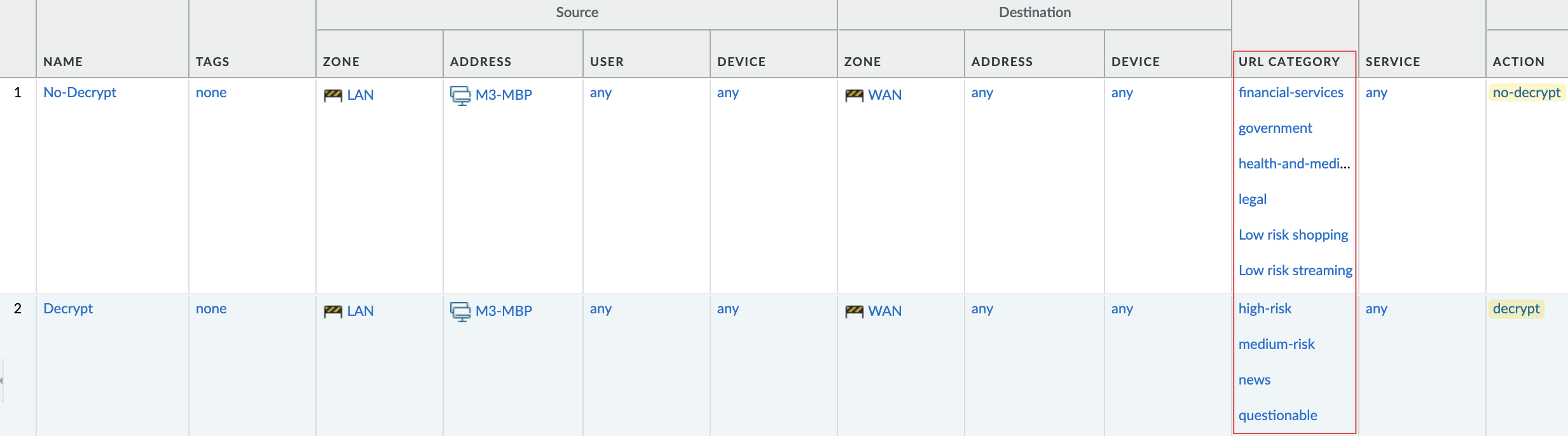
Quic Protocol
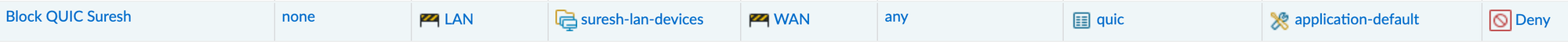
Before proceeding, let's have a quick look at what 'quic' is. QUIC is an experimental transport layer network protocol developed by Google. Palo Alto recommends creating a security policy in the firewall to block the QUIC application.
With the QUIC traffic getting blocked by the Firewall, the Chrome browser will fall back to using traditional TLS/SSL. Note that this will not cause the user to lose any functionality on their browser. Firewall gains better visibility and control of Google applications with or without the SSL decryption enabled.
When I first configured SSL decryption, it wasn't working properly. For example, when I tried to access cnn.com, the traffic was sometimes identified as 'quic'.
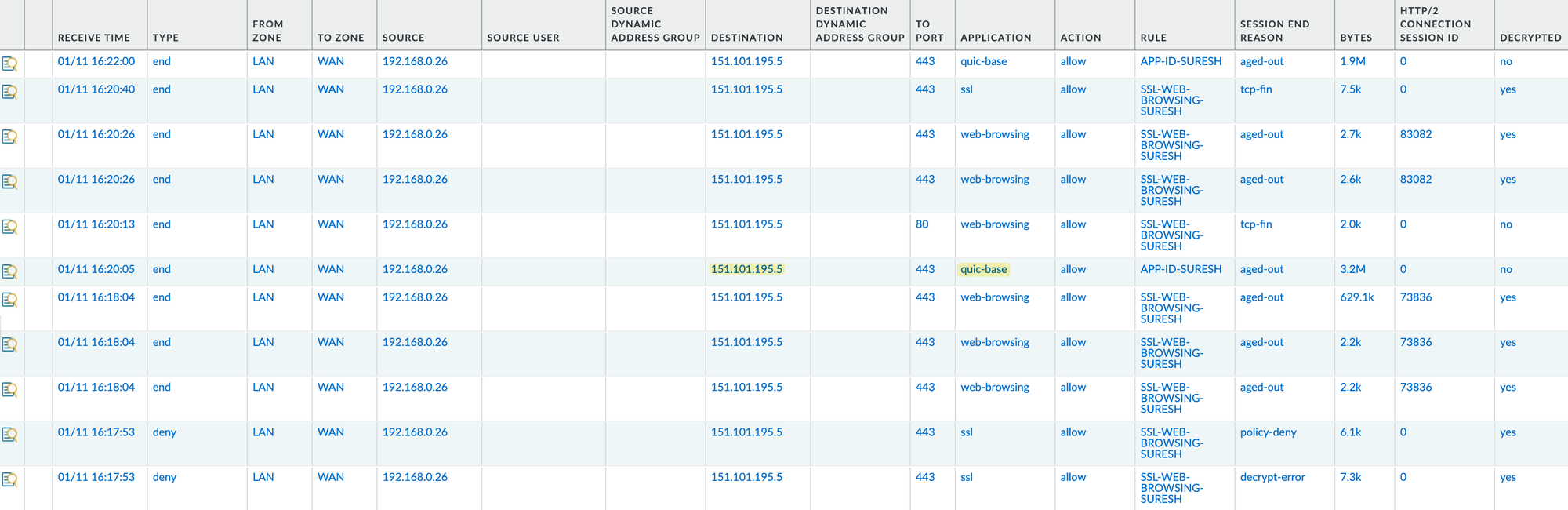
So, I decided to block the 'quic' App-ID as recommended by Palo Alto.

Testing and Verification
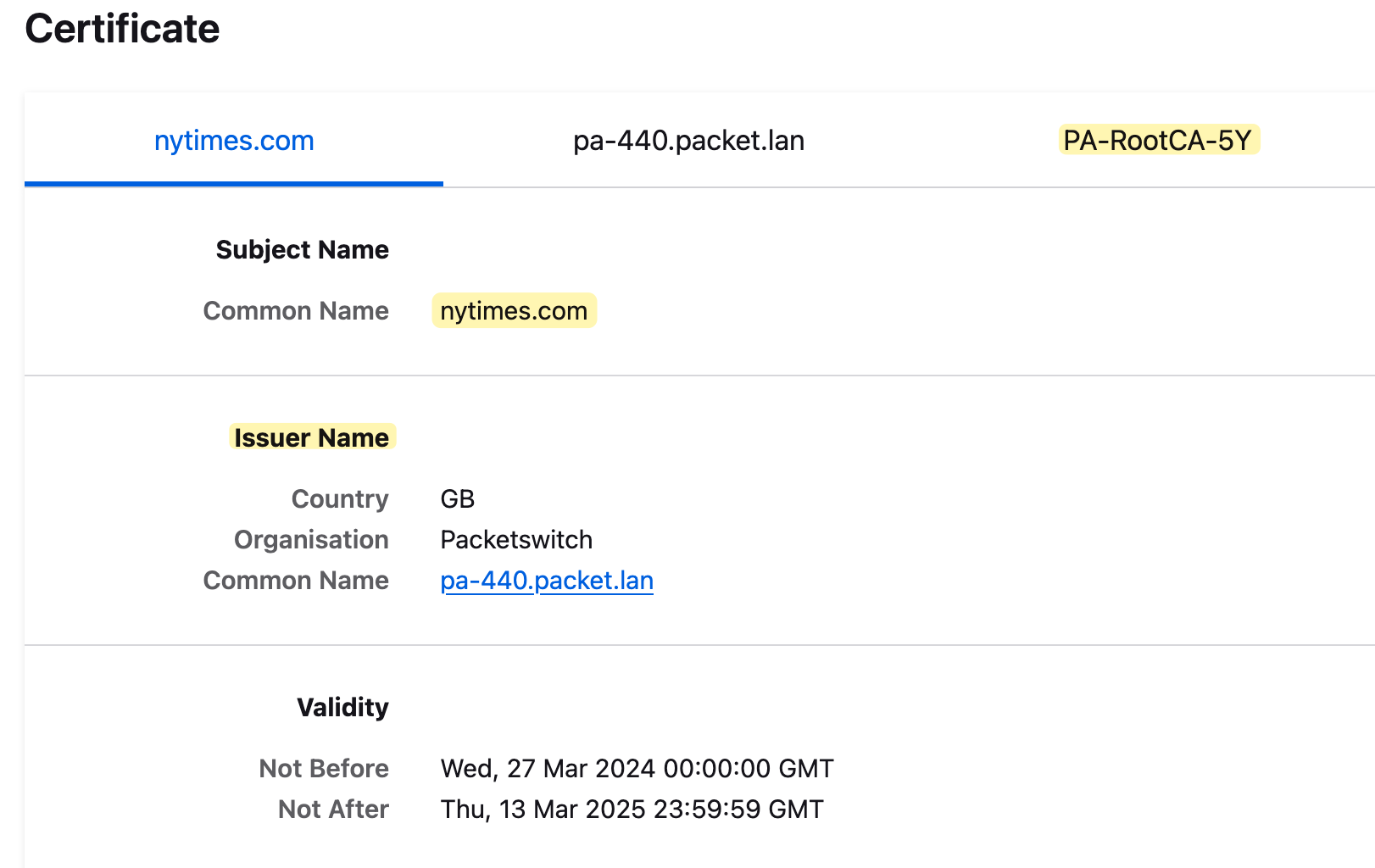
It's time for the tests and verifications. I visited The New York Times, and checking the certificate, we can clearly see that it is signed by the Root CA we created earlier on the firewall. This is not the actual certificate from the New York Times but rather the copied certificate signed by the firewall.
URL Filtering with SSL Decryption
Now that we have SSL decryption working, we can have more granular control. For example, let's allow access to all 'news' sites, but we want to block the cnn.com/politics subpage. Without decryption, we can't block specific subpages because, while the firewall can see the user is on cnn.com, it can't determine the specific pages they are visiting.
To demonstrate this, I'm going to create a custom URL category to block, specifically cnn.com/politics, and set this category to block.
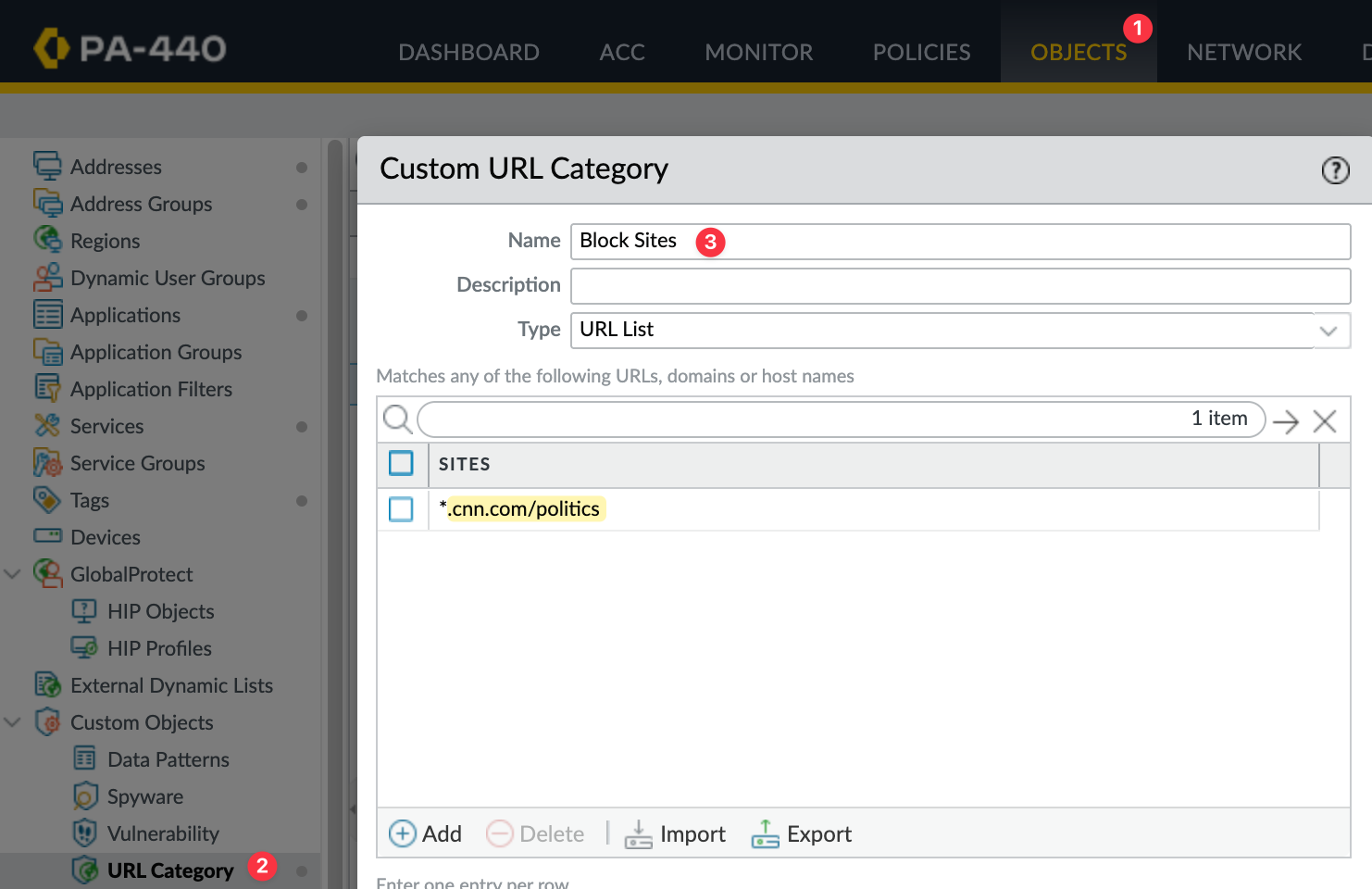
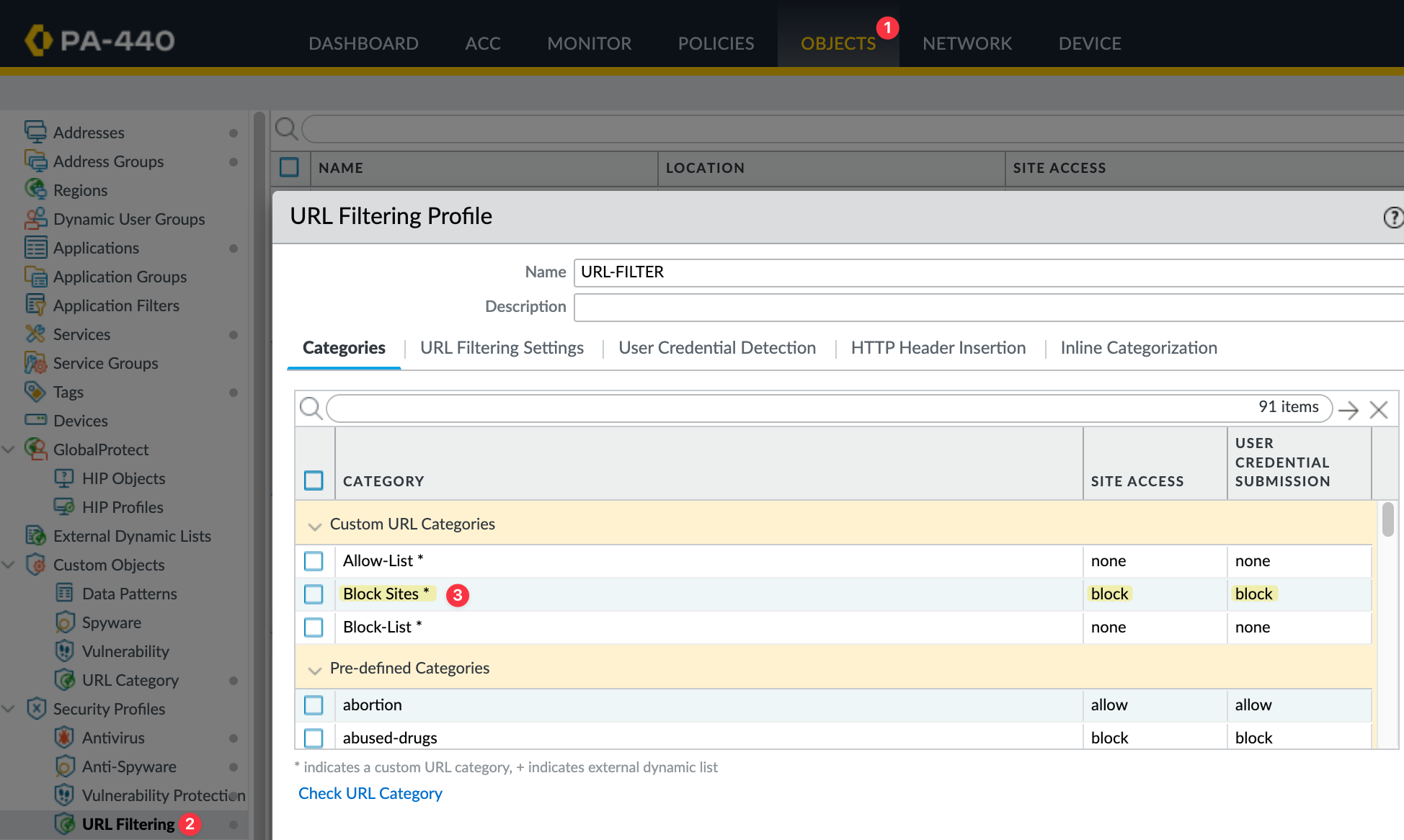
I'll commit my changes and, if I try to navigate to the 'politics' page, the page will be blocked.
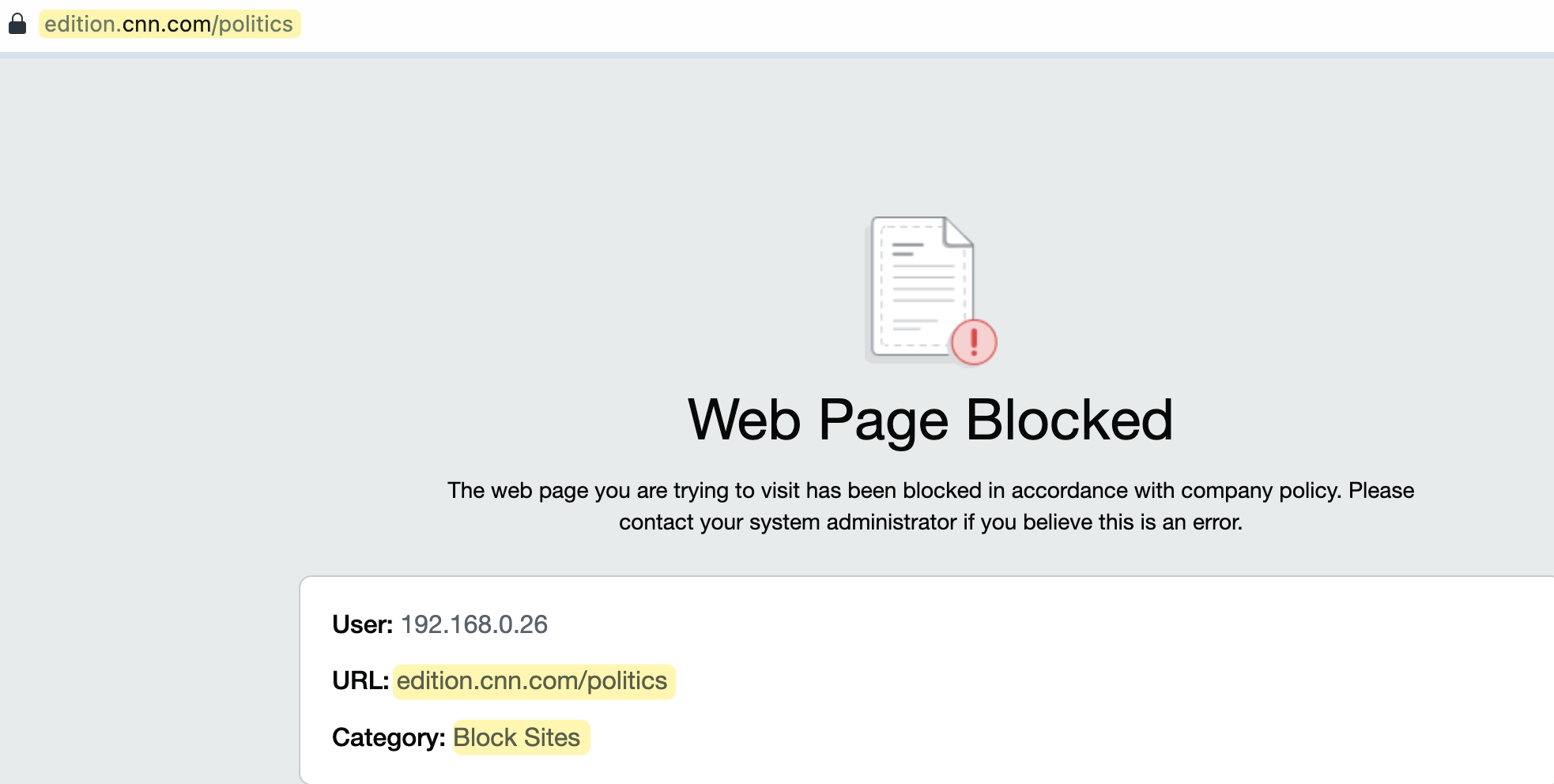
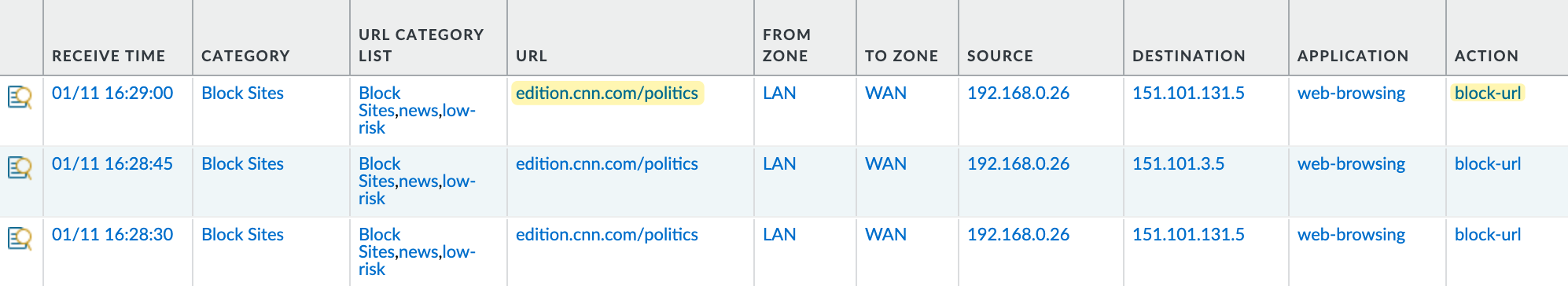
I also recorded my screen to demonstrate the behaviour in action. You can watch the recording to see how cnn.com is accessible, but navigating to the 'politics' section results in the traffic being blocked.
Certificate Pinning
Please note that, as we mentioned at the very beginning, there will be issues with SSL decryption if you don't plan properly. One such issue is certificate pinning, which can significantly interfere with SSL decryption.
Certificate pinning is a security measure where websites hardcode the certificate or public key they expect to connect with, rather than accepting any certificate signed by a trusted authority. This means that even if the firewall presents a valid certificate that your system trusts, the browser will reject it if it doesn't match the hardcoded certificate. This can prevent SSL decryption from working as intended because the browser will not accept the firewall-generated certificate.
Although this prevents malicious actors from intercepting and manipulating sessions, it also prevents SSL decryption because the firewall creates an impersonation certificate instead of the server certificate to present to the client. when a certificate is pinned, the firewall cannot decrypt the traffic because the client does not accept the firewall’s impersonation certificate, the client only accepts the certificate that is pinned to the application.











