In this blog post, I will show you how to configure NAT on Palo Alto Firewalls. One of the main functions of the NAT is to translate private IP addresses to globally-routable IP addresses, thereby conserving an organization’s routable IP addresses.
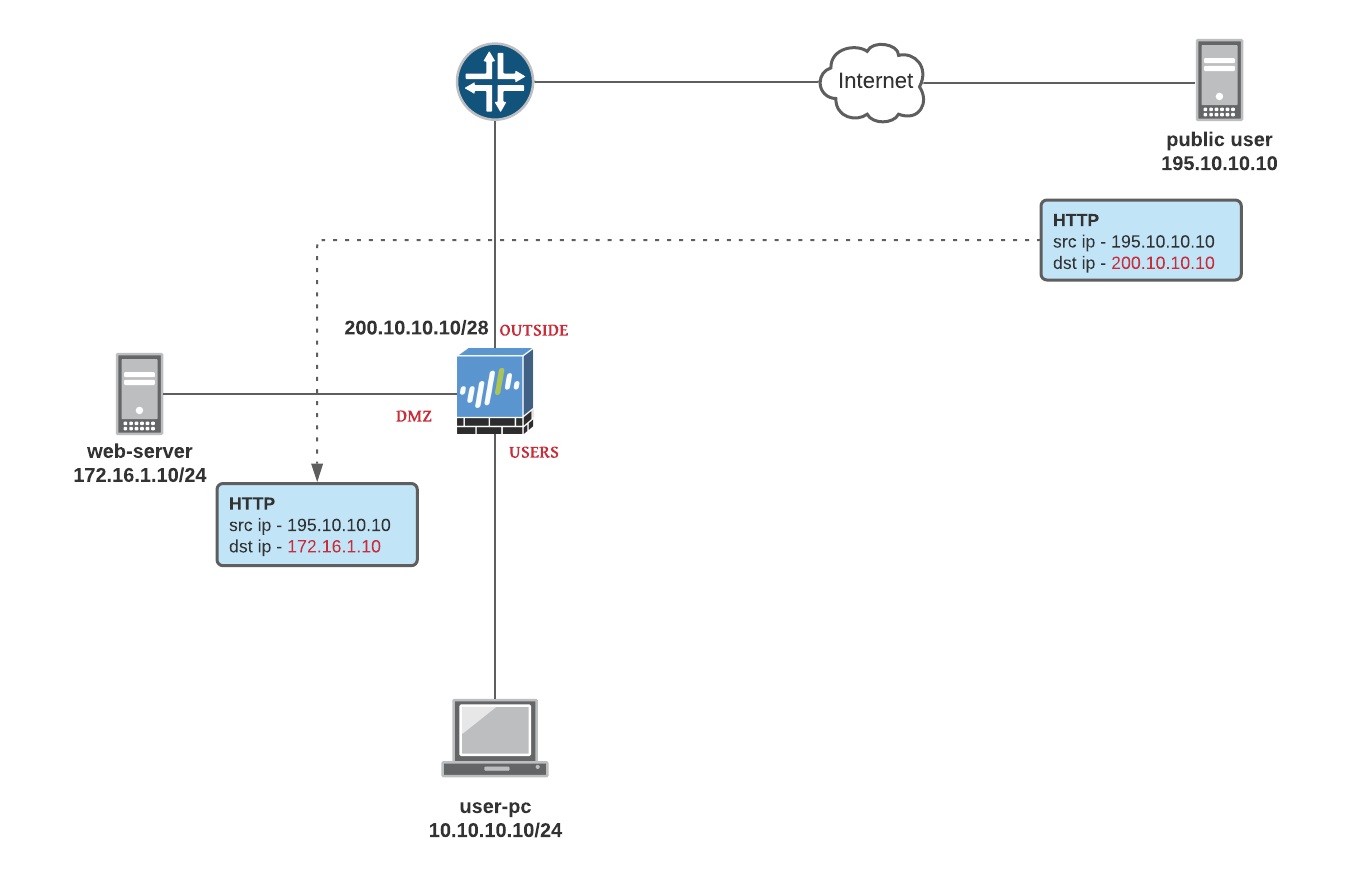
NAT examples in this section are based on the following diagram.
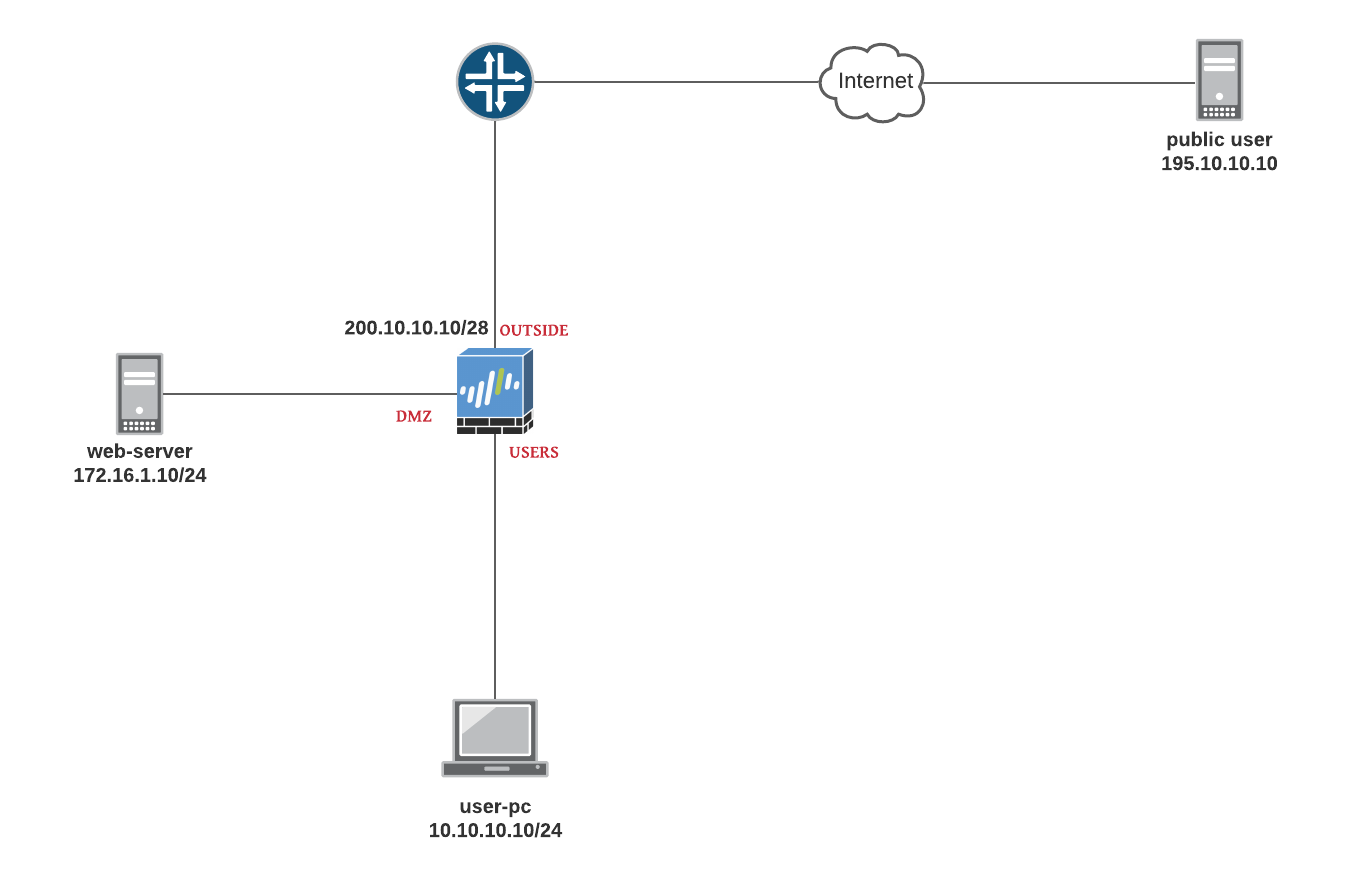
Palo Alto Configurations
- USERS zone : 10.10.10.0/24
- DMZ zone : 172.16.1.0/24
- OUTSIDE zone : 200.10.10.0/28
- public user has an IP of 195.10.10.10
Source NAT - Dynamic IP and Port
Source NAT is used for translating a private IP address to a public routable address by changing the source address of the packets that pass through the Firewall.
Source NAT allows connections to be initiated only for outgoing network connections for example, from a private network to the Internet.
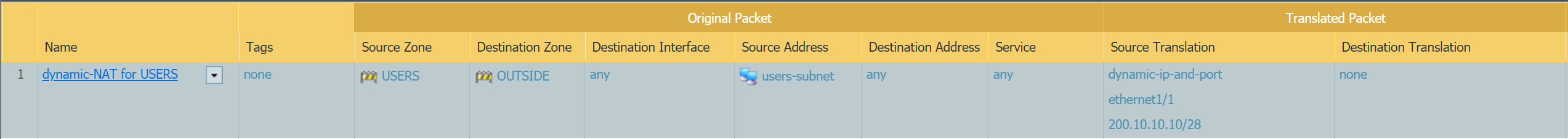
Let's configure source NAT, so the users can go out to the Internet
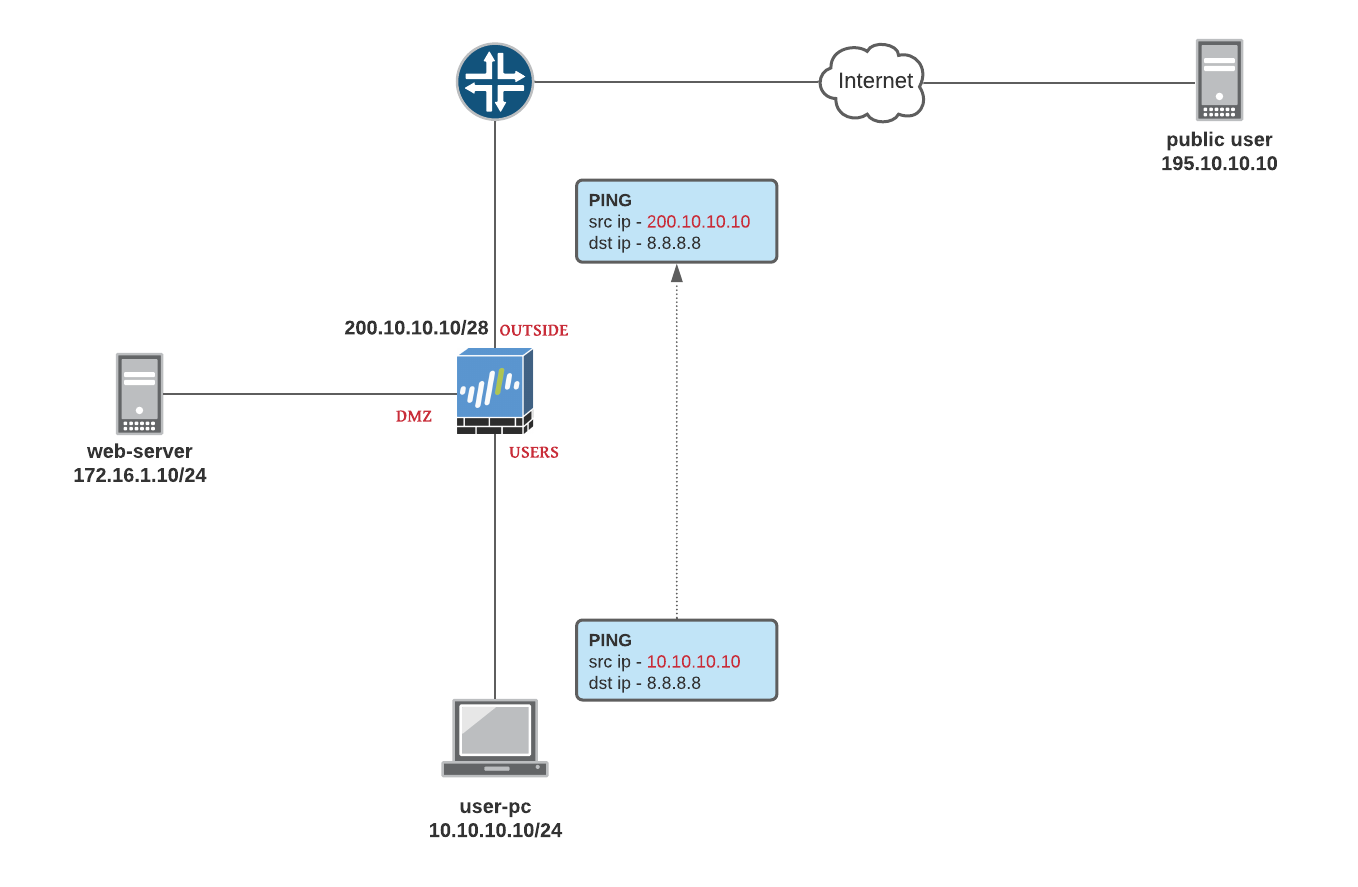
- Source NAT with Dynamic IP and port - When the traffic leaves the firewall the
source IPis translated from10.10.10.xto theOUTSIDE IP addressof the Firewall (200.10.10.10) - Security rule allowing
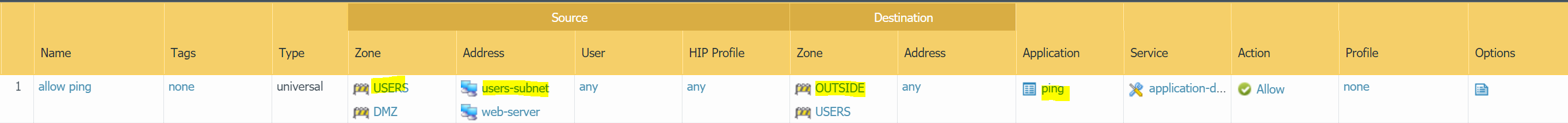
PING
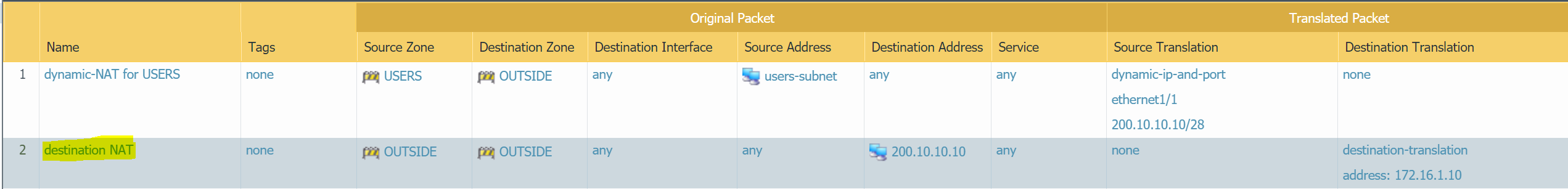
Destination NAT
Destination NAT is performed on incoming packets when the firewall translates a public destination address to a private destination address.
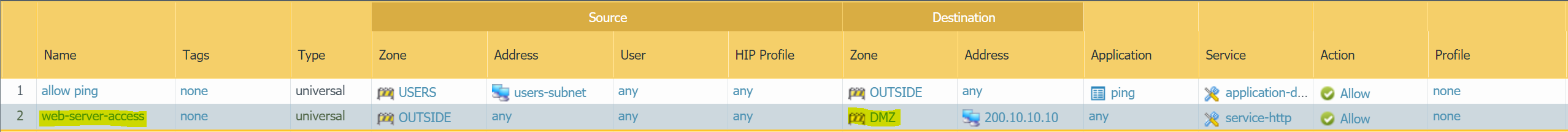
In this example, we have a web-server that is reachable from the Internet via Firewall's OUSIDE IP of 200.10.10.10. When the traffic hits the Firewall, the destination IP is translated to the private IP of 172.16.1.10
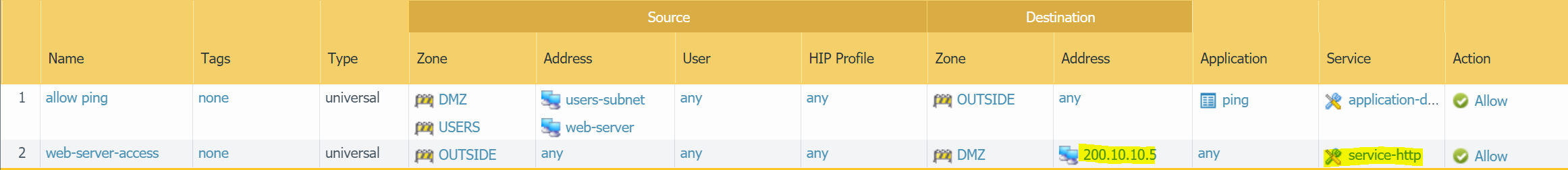
Please remember that you also need a corresponding Security Rule to allow http traffic from the Internet to the web-server
Let's configure Destination NAT, so the public users can access the web-server
- Destination NAT - When the traffic arrives on the firewall the
destination IPis translated from200.10.10.10to172.16.1.10 - Security rule allowing
httptraffic from the Internet.
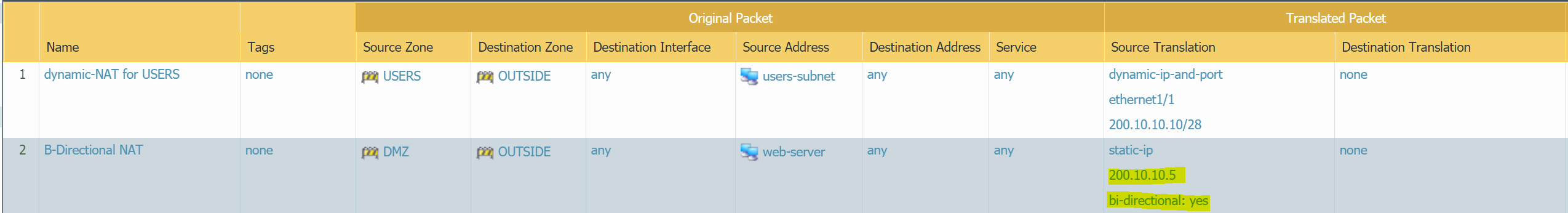
Bi-Directional NAT
Please note that I deleted the destination NAT I created in the previous step to demonstrate Bi-Directional NAT.Let's assume that the webserver needs Internet access to update the packages from time to time. So, we need to create a Source NAT (either Dynamic IP and port or static NAT). The webserver also needs to be accessible from the Internet which requires Destination NAT.
We can either create two separate NAT rules or use Bi-Directional NAT. Bi-Directional NAT rule creates two rules, one for Source NAT and one for Destination NAT. So, when the web server goes out to the Internet, the source IP is translated to the Public IP of the Firewall. On the other hand, if anyone initiates an inbound connection to the web-server's public IP, the destination IP is translated to the private IP assigned to the web-server's NIC.
In this example, instead of using Firewall's OUTSIDE interface IP, I'm going to use a different IP - 200.10.10.5
Verification
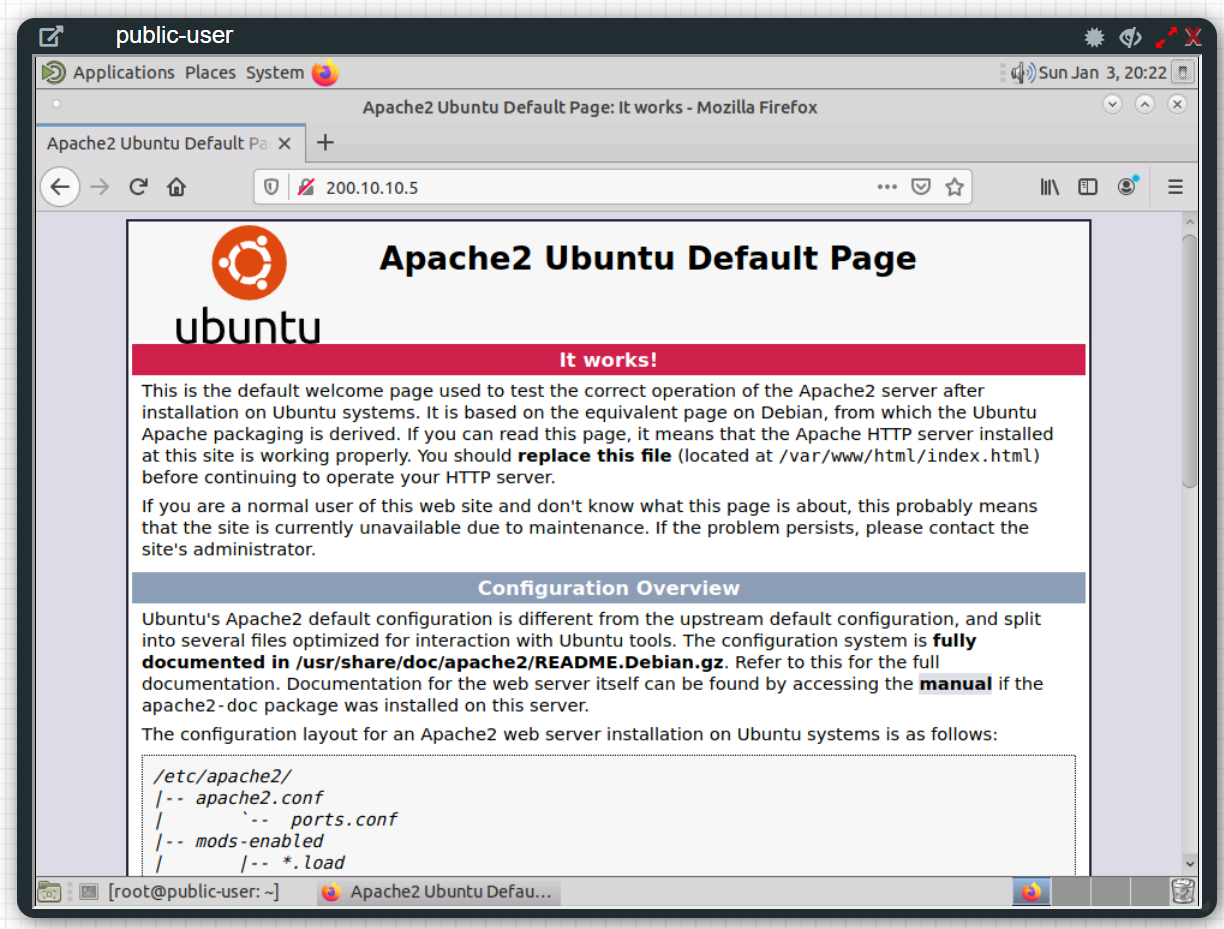
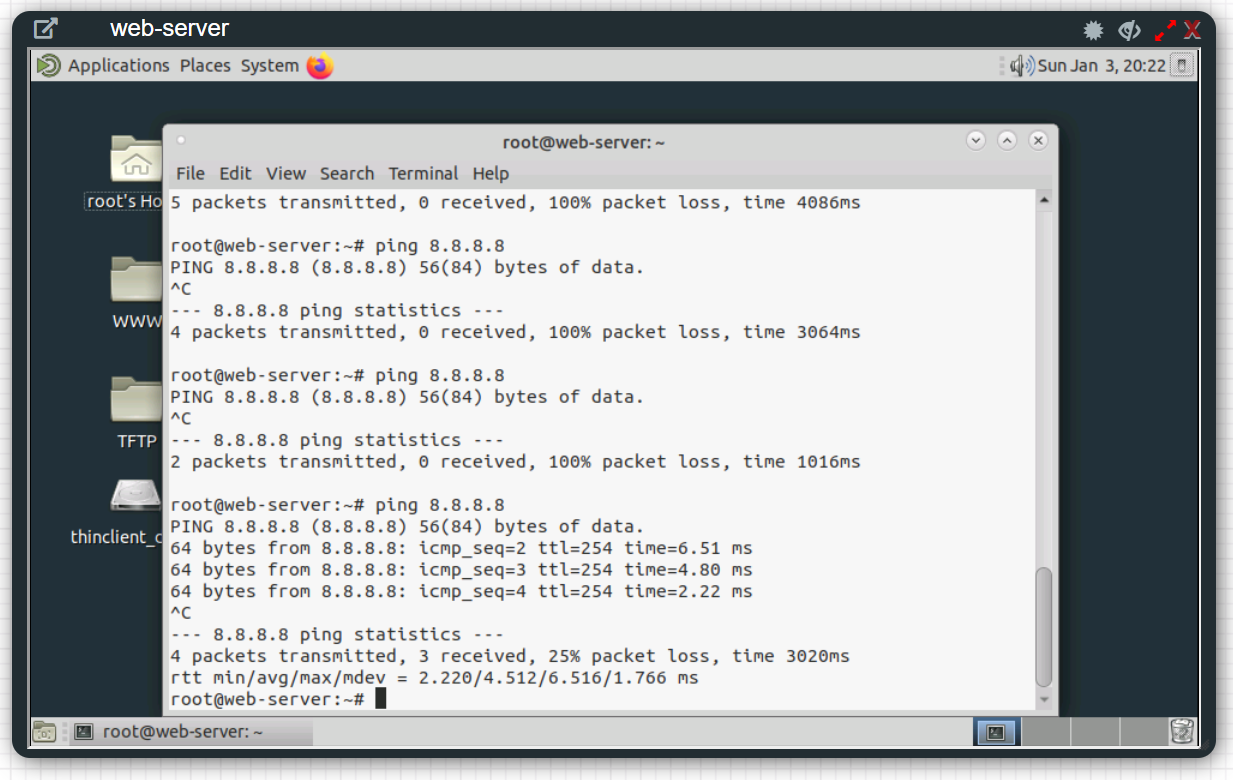
As you can see above, web-server can reach out to the Internet and public users can access the web-server on port 80.
U-Turn NAT
U-Turn NAT refers to a Network where Internal users need to access an Internal server using the server’s external public IP address.
Let's say the users in the USERS zone need to access the web-server using its public IP address of 200.10.10.5
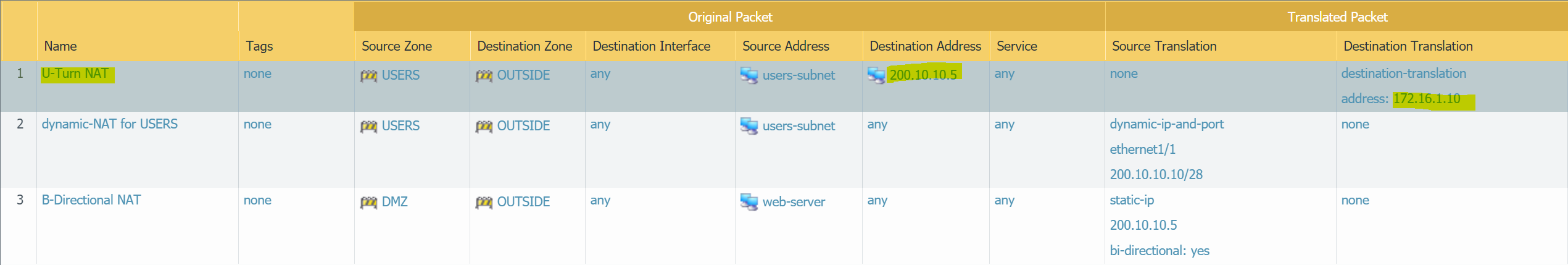
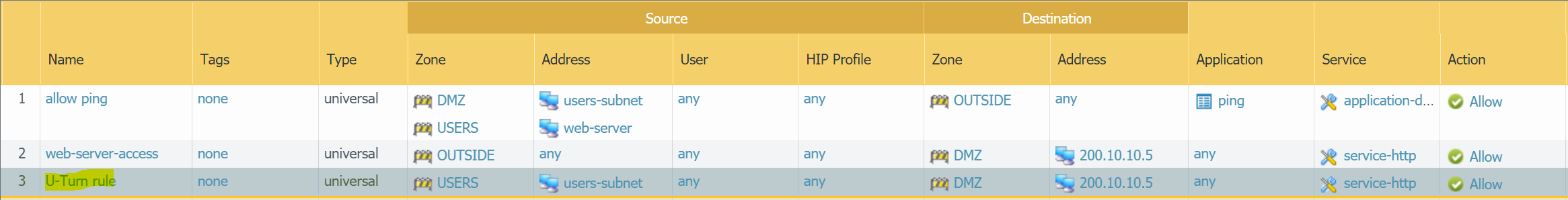
Please note that you may have to move the U-Turn NAT to the top, otherwise the traffic will match against the dynamic-NAT for USERS NAT policy.
Reference
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/networking/nat/configure-nat
Thanks for reading. As always, your feedback and comments are more than welcome.