If you work with Palo Alto firewalls, you might have heard of App-ID. They work well and let us create security policies based on 'applications' rather than TCP/UDP port numbers. For example, instead of allowing UDP/53, we can allow the application 'DNS'. In this blog post, we will look at how App-ID works with and without SSL Decryption. Let's get to it.
If you are new to App-ID and want to know how it works, feel free to check out my introductory post below.
As always, if you find this post helpful, press the ‘clap’ button. It means a lot to me and helps me know you enjoy this type of content.
App-ID Recap
When you have an NGFW like Palo Alto, you don't want to rely on port numbers for your security policies. Instead of allowing TCP/3389, TCP/389, or UDP/514, you want to use RDP, LDAP, or Syslog. Using specific port numbers, like TCP/3389, can be risky because someone could create a custom application that uses TCP/3389, and the firewall would just allow it. However, with App-ID, the firewall can detect what exactly the traffic is using various methods. So, if someone tries to tunnel some other traffic using TCP/3389, the firewall will block the traffic.
App-ID and SSL Decryption
Now, if you navigate to Objects > Applications and search for 'facebook' for example, you will see the 'facebook' container and beneath it, there are sub-applications like 'facebook-video', 'facebook-uploading', 'facebook-reactions', and so on. Does that mean if I create a security policy to block 'facebook-video', the firewall will block only 'facebook-video' and allow everything else? Not really, without using SSL Decryption.

But why, you may ask? Without SSL decryption, when you open facebook.com, the firewall knows that you are visiting Facebook and will identify the traffic as 'facebook-base'. It won't know exactly what you are viewing or doing inside Facebook because Facebook (and the majority of websites) use HTTPS, which is encrypted end-to-end, and the firewall can't see inside the HTTPS session.
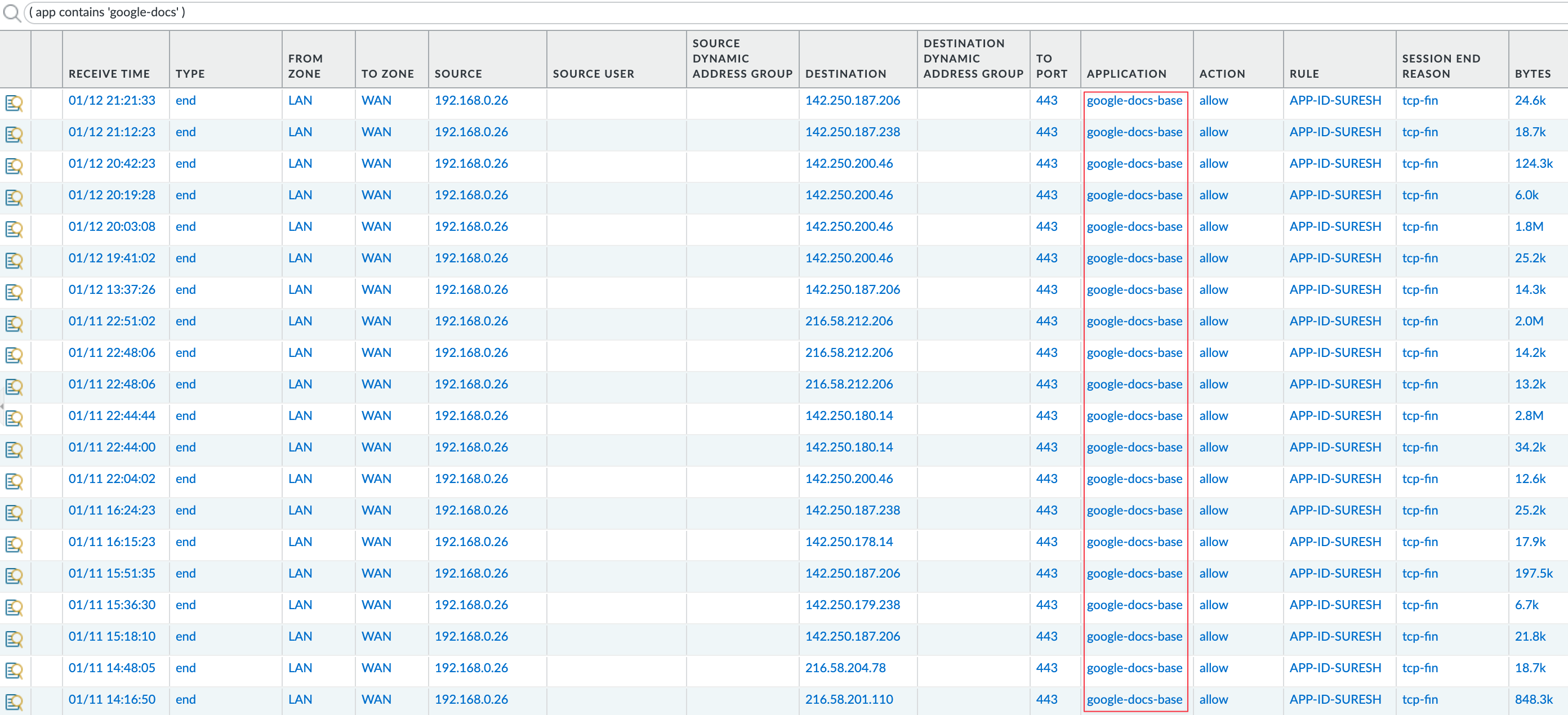
So, without SSL Decryption, you can only block Facebook entirely. This applies to most other App-IDs, such as Google Docs, where you have sub App-IDs like 'google-docs-create', 'google-docs-delete', and so on. Similarly, without decryption, the firewall will only see that the user is using Google Docs but nothing else.

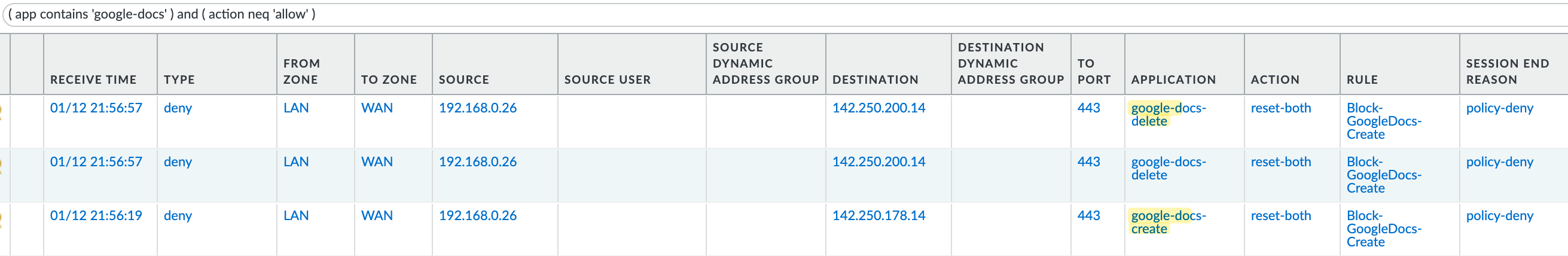
I went to docs.google.com and created a new file, copied an existing file, and then deleted a file. If I check the logs, the firewall can only see that I was on docs.google.com but can't determine the specific actions I took. Therefore, the log categorizes all this activity under the App-ID 'google-docs-base'.
App-ID with SSL Decryption Enabled
Now, if we configure SSL decryption, the firewall can see inside the HTTPS session, so it knows exactly what the user is doing. To demonstrate this, I'm going to configure SSL Decryption and create a security policy to block the 'google-docs-create', 'google-docs-delete', and 'facebook-video' App-IDs.
With this setup, I should be able to access Google Docs, but as soon as I try to create a new file/doc or attempt to delete a Doc, the action should fail. Similarly, I should be able to access Facebook, but the videos shouldn't load.

SSL Decryption
Please note that configuring SSL Decryption is outside the scope of this blog post, but I have a dedicated blog on this topic; feel free to check it out.
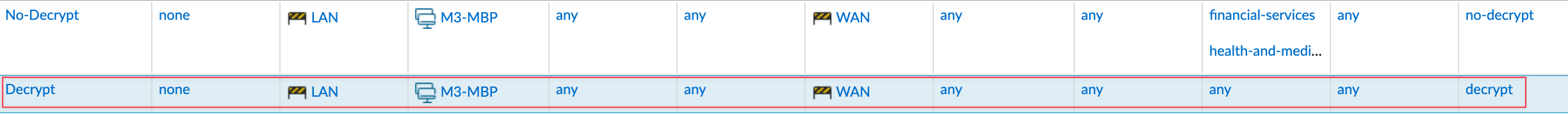
Here, I create a Decryption Policy that decrypts all traffic from my laptop.
Security Policy
Next, let's create a security policy to block the App-IDs 'facebook-video', 'google-docs-create' and 'google-docs-delete'.

Testing and Verification
Let's test this out. First, I'm going to test Google Docs. Even though I can visit Google Docs and open files, if I click on 'Create Blank Document,' the page doesn't load, as shown below. Similarly, if I try to delete one of the files, even though I get a prompt to delete the file and the file vanishes when I refresh the page, the files come back and didn't actually get deleted.
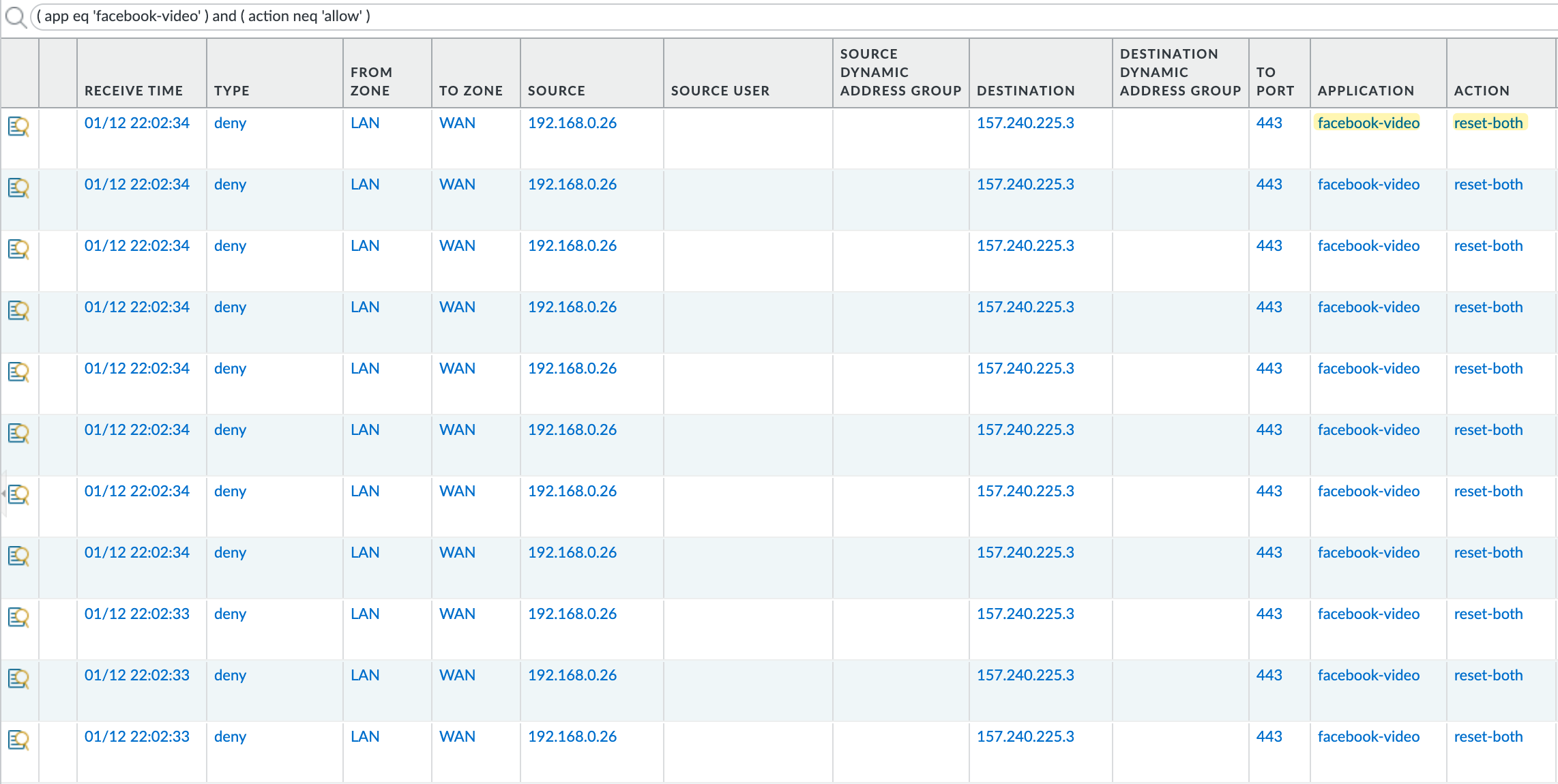
Now, with Facebook, I can visit the site and see everything except the videos, as shown in the screenshot below.
Here are also the traffic logs that clearly show the specific App-IDs that are being identified by the firewall and getting blocked.
Closing Up
In conclusion, SSL decryption is crucial for utilizing the full functionality of App-ID in Palo Alto firewalls. Without decrypting SSL, the firewall can only see and control traffic at a very basic level, such as allowing or blocking access to entire applications.
However, with SSL decryption enabled, you gain the ability to fine-tune your security policies. You can specify actions within an application, like blocking specific activities in Google Docs or preventing videos from playing on Facebook.










