In my previous blog posts (linked below), we looked at how to allow or block specific websites using URL filtering. In this post, we'll look into how to use URL filtering with SSL decryption for more granular control.
As always, if you find this post helpful, press the ‘clap’ button on the left. It means a lot to me and helps me know you enjoy this type of content.
Why Do We Need SSL Decryption?
Previously, we saw how to block sites like facebook.com or cnn.com, or allow specific websites blocked by a URL Filtering profile. However, these methods fall short when more granular access is required. Most website traffic today is encrypted with HTTPS, meaning the firewall cannot inspect what's happening within those sessions.
Without SSL decryption, the Palo Alto firewall (or any NGFW) relies on the certificate's SNI or CN to identify the site. For instance, if you want to allow general 'news' sites but block cnn.com/politics, SSL decryption is necessary. Without decrypting the traffic, the firewall cannot see or control what the user accesses within a website.

SSL Decryption Recap
To move forward with our example, let's look at how to block cnn.com/politics (nothing against CNN, this is just for testing, haha) while allowing everything else. To achieve this, we first need to decrypt the traffic. But what exactly should we decrypt?
Decrypting all traffic can lead to unnecessary complications. For this example, I’ll focus on decrypting traffic categorized as 'news.' This way, when a user visits cnn.com, their traffic will be decrypted. As they navigate and click on 'politics,' the firewall can inspect the session and block that specific page.
Create a URL Category
So, first, let’s create a custom URL Category and add the URL we want to block. Navigate to Objects > Custom Objects > URL Category, create a new category, and add the URL *.cnn.com/politics. The wildcard will match URLs like cnn.com/politics or edition.cnn.com/politics.
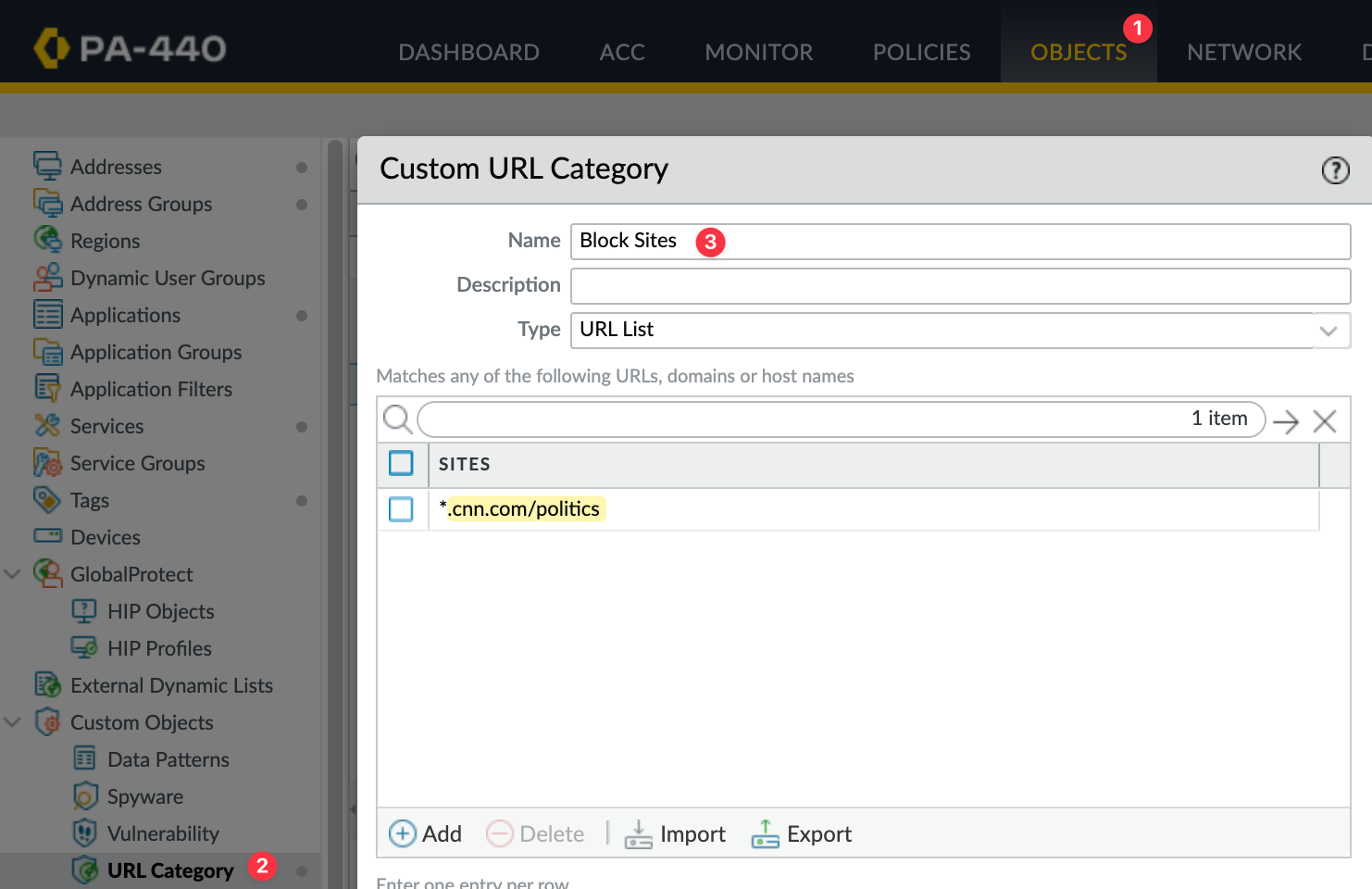
Next, go to the URL Filtering profile attached to the security policy that permits Internet access and set the action for this category to 'block.'
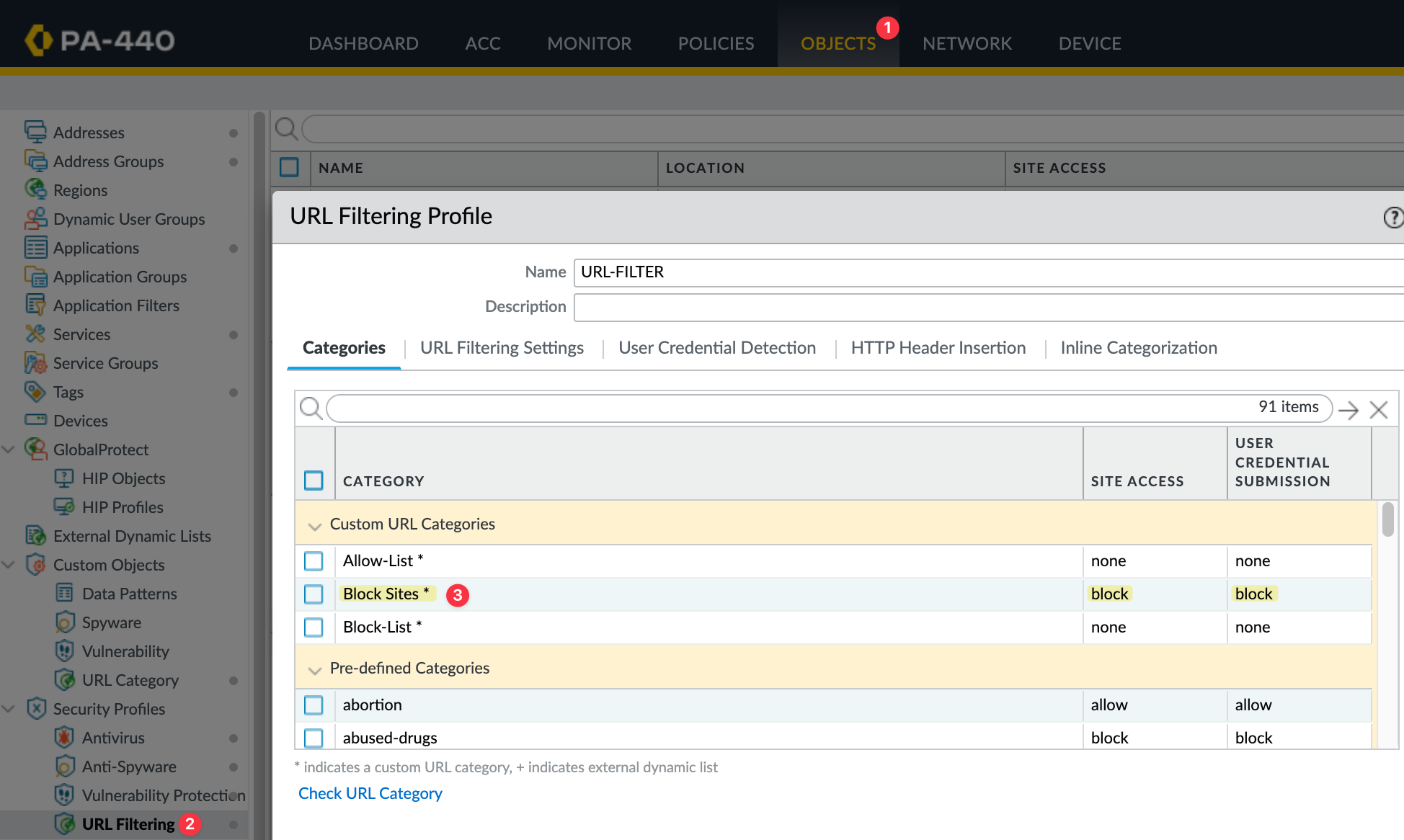

SSL Decryption Policy
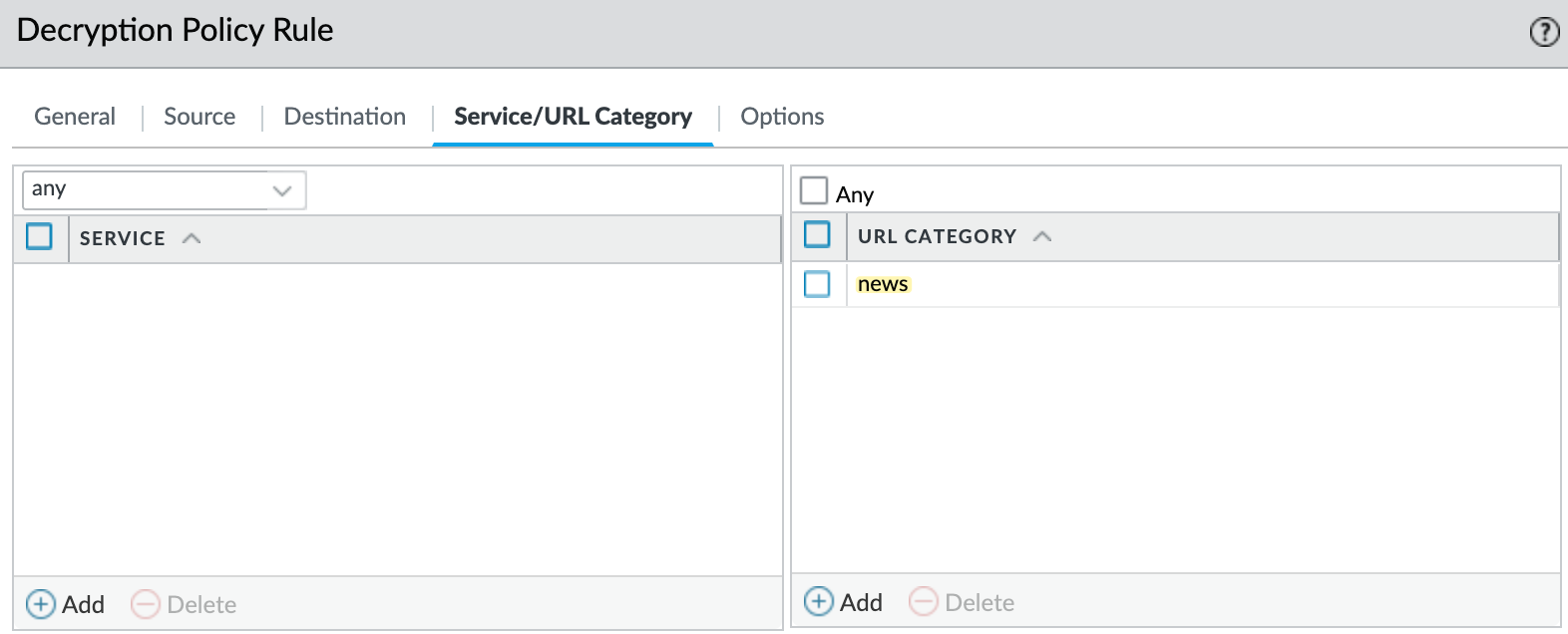
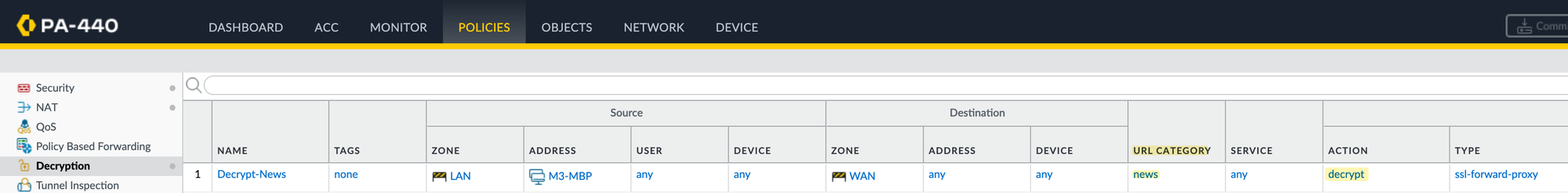
Next, create an SSL Decryption Policy to decrypt traffic categorized as 'news.' If you already have a decryption policy in place, you can skip this step. In this example, I don’t have any existing policy.
Here, you can define the source and destination as needed. Under the URL Category section, select 'news.' This ensures that when a user tries to access any site categorized as 'news' by Palo Alto, the traffic will be decrypted. This includes cnn.com, of course.
Testing and Verification
Now it’s time for testing. Visit cnn.com and then navigate to the 'politics' section to see what happens. As you can see, you can access cnn.com and other subpages, but as soon as you click on 'politics,' the traffic is blocked. Exactly what we wanted!
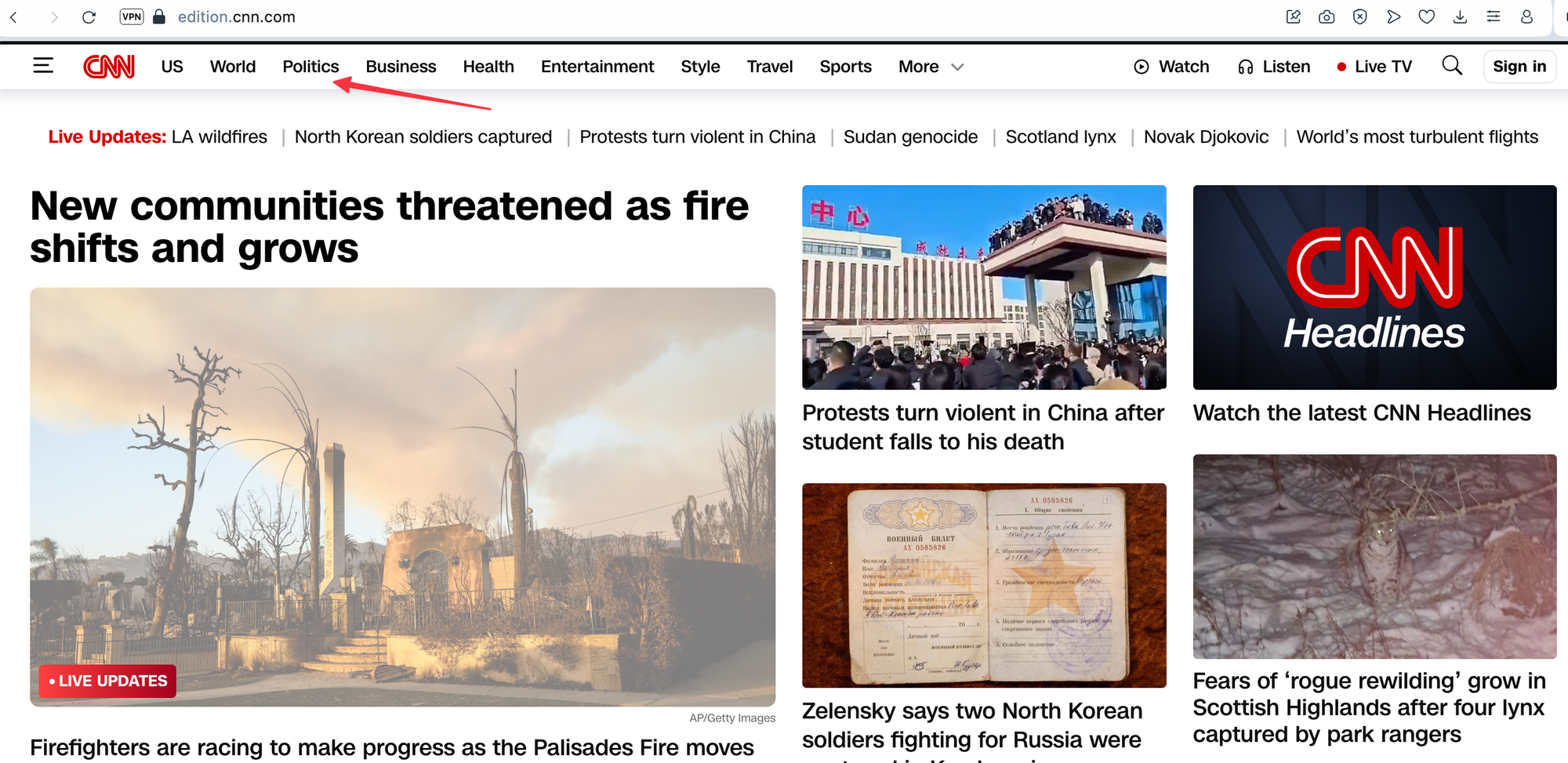
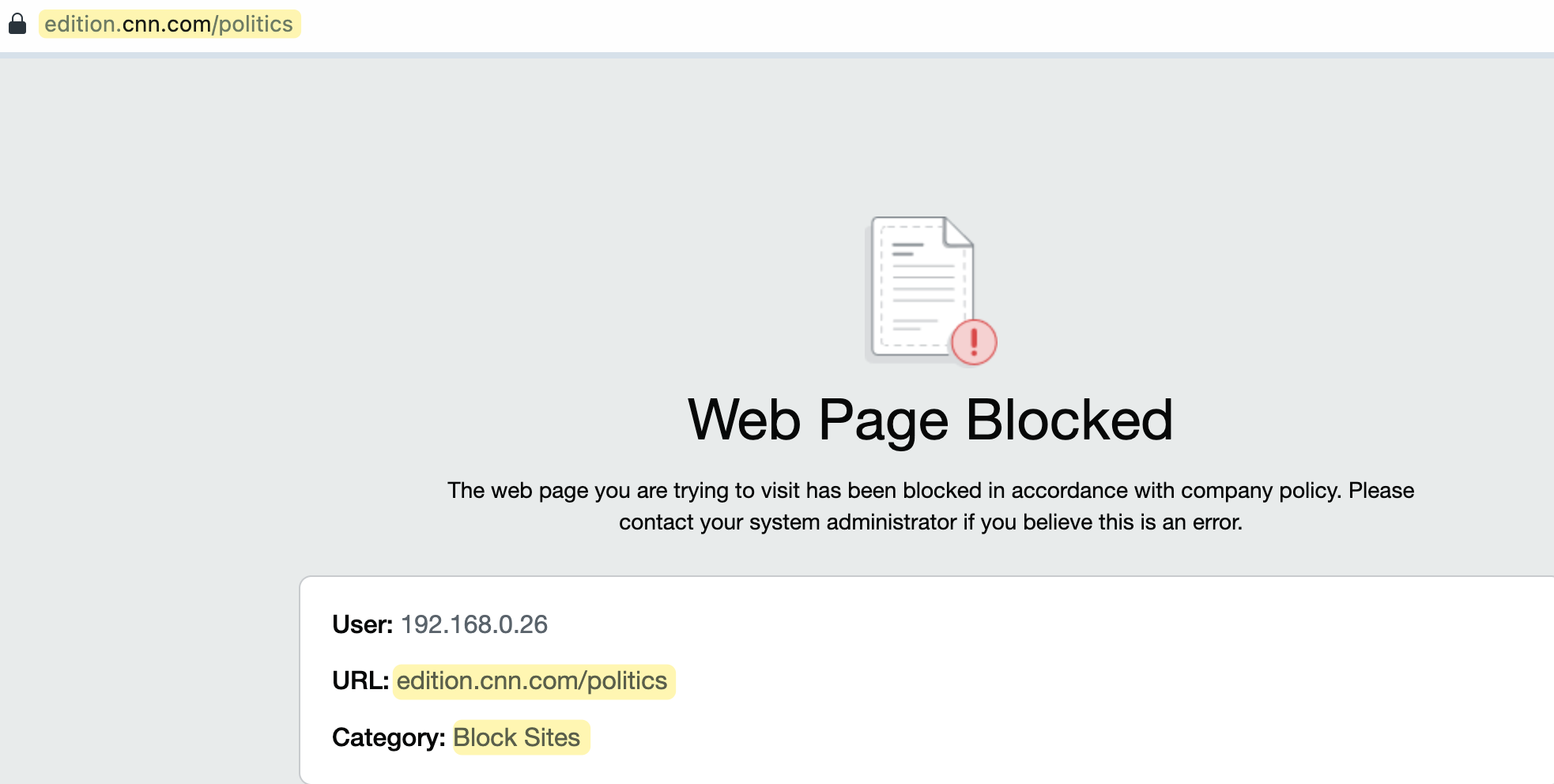
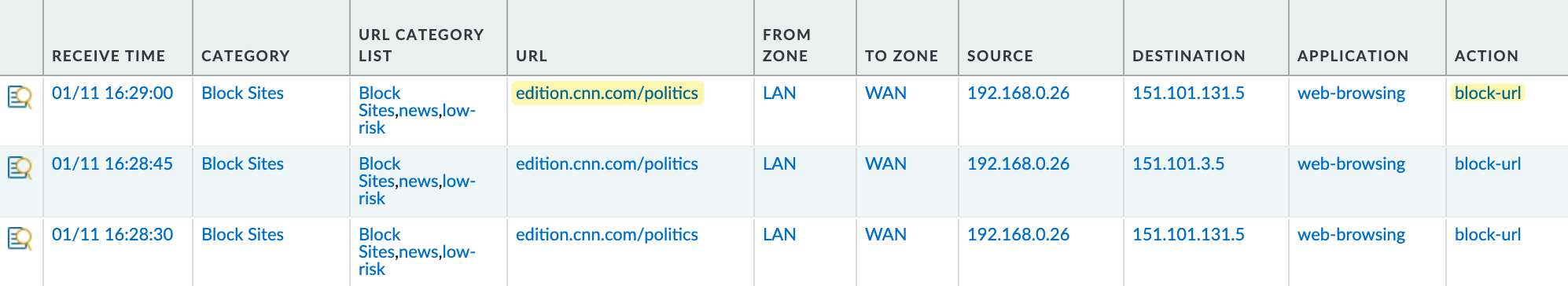
I also recorded my screen to demonstrate the behaviour in action. You can watch the recording to see how cnn.com is accessible, but navigating to the 'politics' section results in the traffic being blocked.
Closing Up
I hope this shows the benefits of using SSL decryption with URL filtering. As mentioned earlier, I’ll cover SSL decryption in greater detail in an upcoming post. Don’t forget to subscribe so you won’t miss any updates!







