In today's blog post, let's look at how to share User-ID information between Palo Alto firewalls using Panorama. We will use a simple example so that you can easily follow along.
It's important to remember that while Panorama primarily manages your firewalls, using it for User-ID redistribution ties it more closely into your network's operations. Typically, you wouldn't need to worry about Panorama going down because the firewalls can function without Panorama. However, when you start using Panorama for User-ID redistribution, it becomes a crucial part of your network. Fortunately, most setups include a backup Panorama, so downtime shouldn't be a concern. Let’s get started and see how this works in practice.
Diagram and Scenario
In this example, let's consider a scenario where we have a main headquarters firewall (HQ-FW) that collects User-ID mappings in various ways, either by reading directly from the Domain Controller or by receiving Syslog messages. This firewall could also have users connecting through Global Protect VPN.
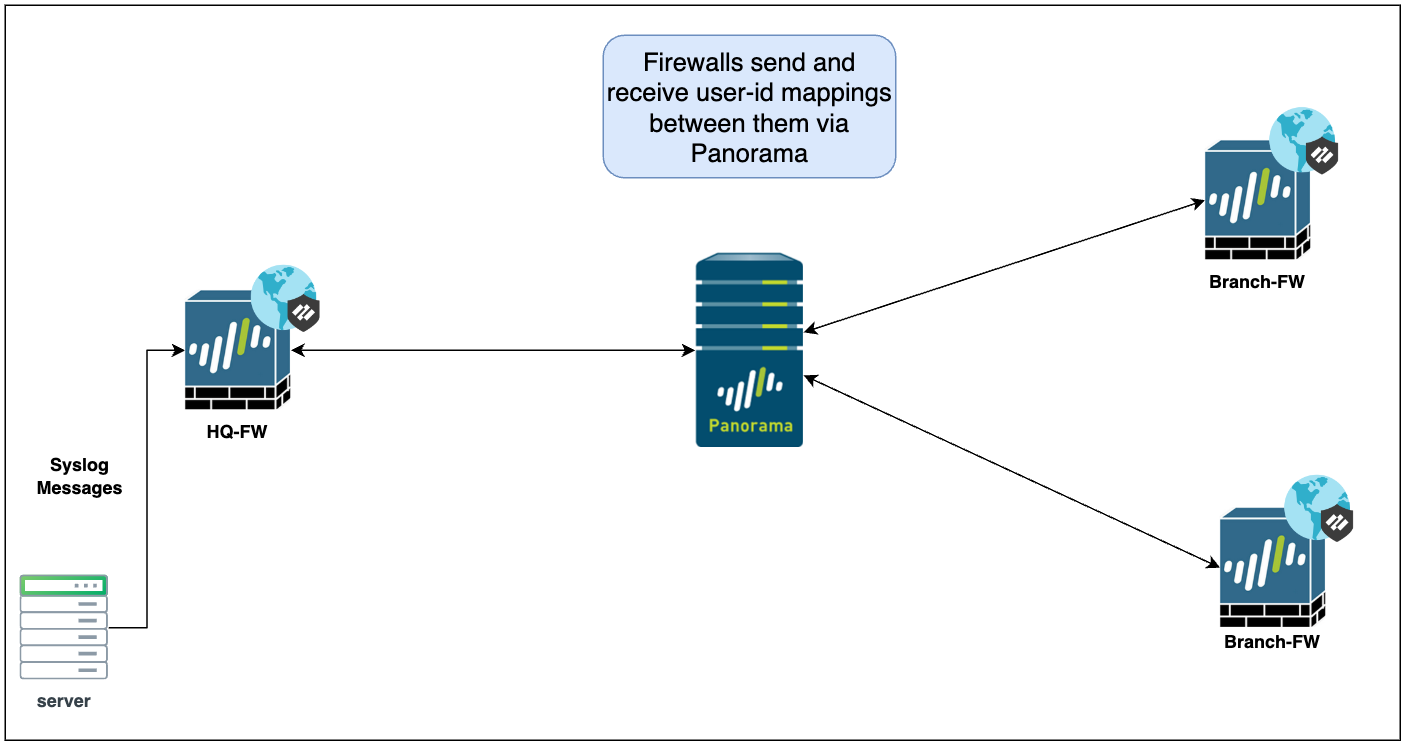
Now, imagine users working from branch offices and connecting to their respective branches via Global Protect VPN as well. If we want to allow access to resources regardless of where the user is located, it makes sense to create rules based on User-ID instead of just IP addresses.
Here's the challenge, if a user connects to a branch firewall and tries to access a resource at HQ, how will the HQ firewall recognize this user? This is where User-ID redistribution becomes essential.
We can configure our firewalls so that all of them send their User-ID mappings to Panorama. Additionally, the firewalls can also be configured to receive User-ID mappings from Panorama. This creates a hub-and-spoke topology rather than a full mesh-like topology. In a full mesh, every firewall would need to send mappings to every other firewall, which can get quite complex.
This hub-and-spoke approach simplifies the architecture by centralizing the distribution of User-ID information through Panorama.
In summary, we want every firewall to send its user-id mappings to Panorama and also we want every firewall to receive the mappings from Panorama.
Configure Firewalls to Send User-ID Mappings to Panorama
To set up the redistribution of User-ID mappings to Panorama, you’ll need to configure both the individual firewalls and Panorama itself.
Configure Firewalls to Send Mappings to Panorama
- Navigate to Device > Data Redistribution > Collector Settings
- Configure Collector Settings by entering a Collector Name and a Pre-Shared Key.
- Remember these details as you’ll need them for Panorama setup. The name and the PSK have to match on both sides.
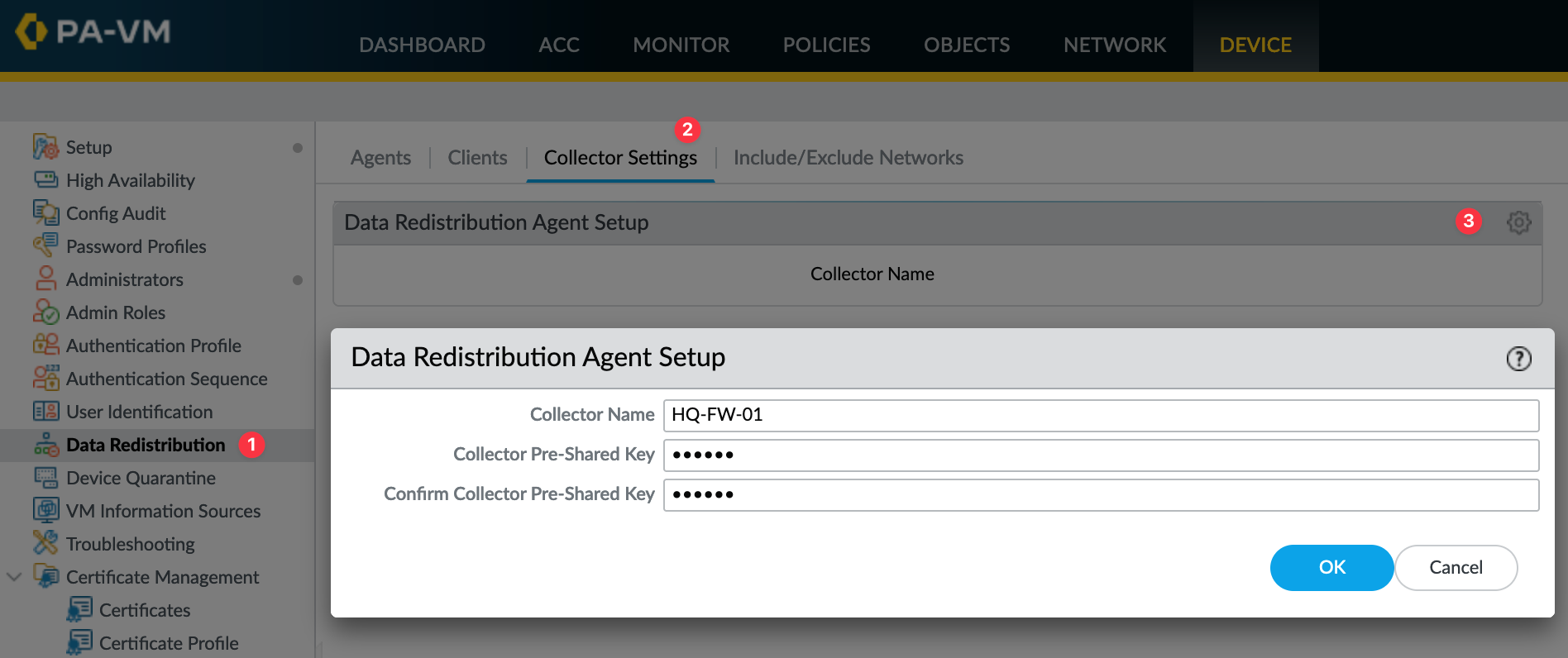
After you have configured all firewalls to send their User-ID mappings, you will need to configure Panorama to receive these mappings.
Panorama Configuration to Receive the Mappings
Now that we’ve set up the firewalls to send their User-ID mappings to Panorama, let’s configure Panorama to receive these mappings.
Navigate to Panorama > Data Redistribution > Agents. Here, add a new agent by filling out the details. Please ensure that the collector name and the Pre-Shared Key (PSK) are exactly the same as you configured on the firewalls. Repeat this step for each firewall.
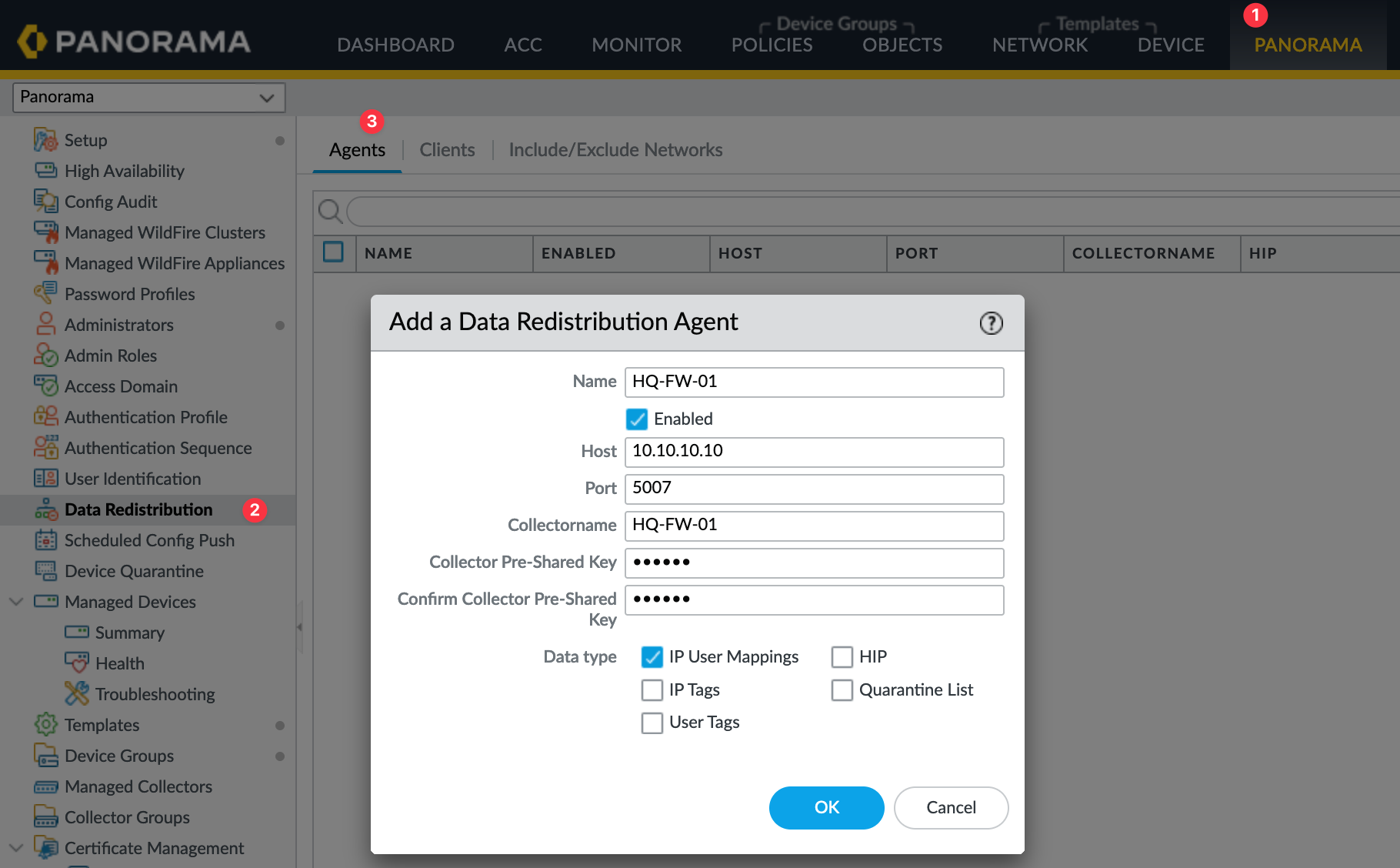
Once Panorama is configured to receive the mappings from all firewalls, the next step is to configure the firewalls to receive User-ID mappings from Panorama. This completes the loop.
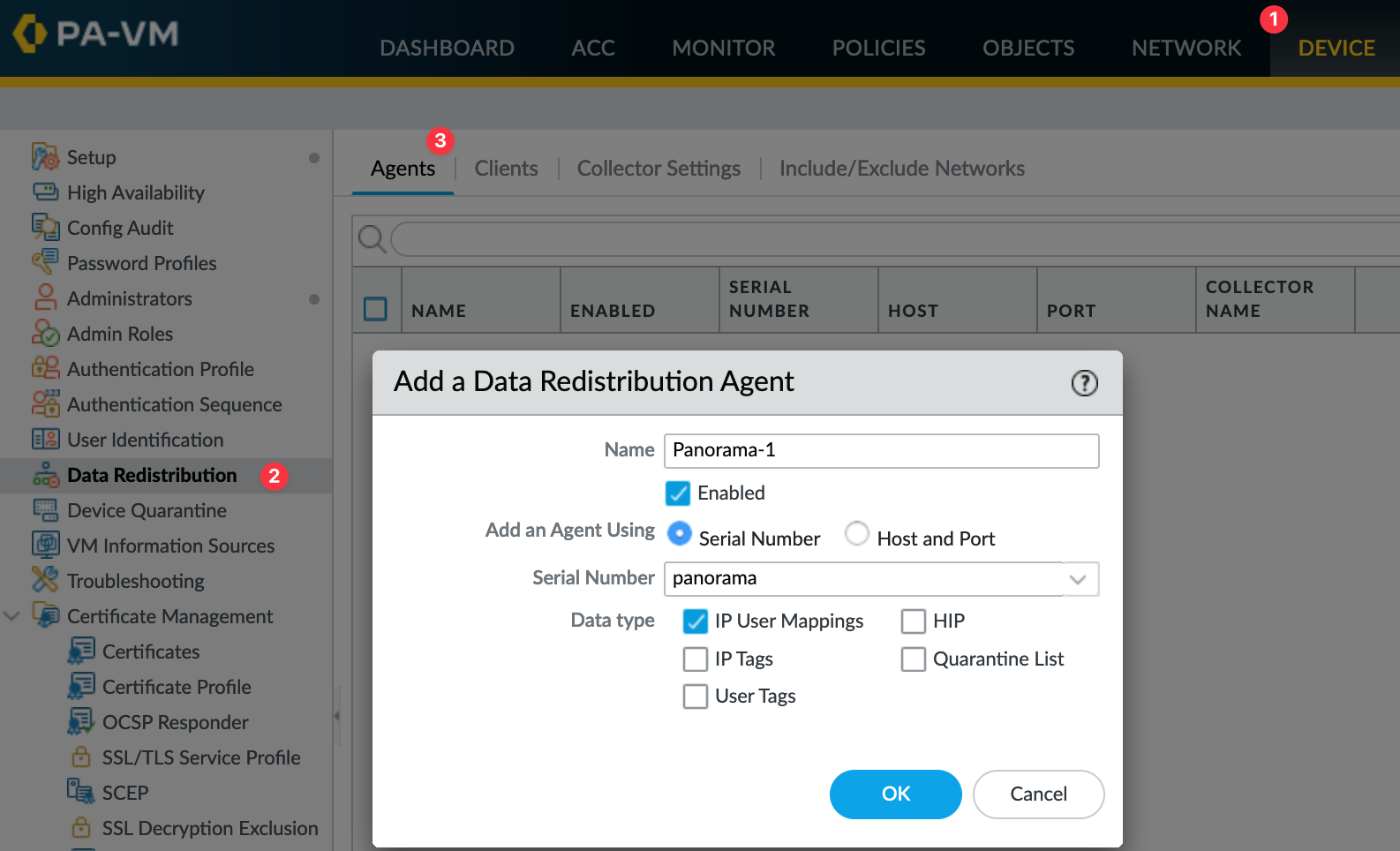
Configure The Firewalls to Receive User-ID Mappings From Panorama
For the final step in setting up User-ID redistribution, go to each firewall and navigate to Data Redistribution > Agents. Here, add Panorama as a new agent. If your setup includes two Panoramas in an active/passive configuration, make sure to repeat this process for the secondary Panorama as well.
Closing Up
That wraps up our post on configuring User-ID redistribution with Panorama across multiple firewalls. Now, when a user connects to Global Protect VPN through a branch firewall, all connected firewalls will be aware of the User-IP mappings. This also works with Active Directory logins.






