In today's post, we're going to explore Prisma Access Mobile Users and understand how it works/compares with Global Protect. I've observed several discussions in various forums where there seems to be some confusion between the two. This is a great opportunity to clarify these concepts. For those who are just stepping into the world of Prisma Access, I recommend checking out my introductory post on the topic linked below. It'll set a solid foundation for what we're about to discuss.

TL;DR
If you're short on time and can't dive into the full post right now, here's a quick summary for you. Traditionally, with your own firewall setup, you'd have both Portal and Gateways on the firewall you manage. Users would connect to this firewall using the Global Protect app to access internal resources.
Prisma Access Mobile Users changes the game slightly. The core idea remains the same, but this time, Palo Alto takes care of managing the firewalls and infrastructure for you. You're relieved of managing the physical firewall, yet you still manage the Security Policies, Objects, Security Profiles, and all the other aspects you'd usually manage in a traditional setup.
What is Prisma Access Mobile Users - The Long Answer?
With Prisma Access Mobile Users, you connect to a Cloud Firewall (MU-SPN to be precise) that Palo Alto manages. We are still responsible for configuring all sorts of Global Protect configurations such as the subnet, split-tunnelling, security policies etc. Palo Alto just manages the infrastructure and the firewalls. If there is a sudden increase in demand, Palo Alto spins up additional nodes in the background and ensures the load is managed appropriately. The nodes are also globally distributed so, if a user is in the UK, he/she will be connecting to a firewall that is closer to the UK.
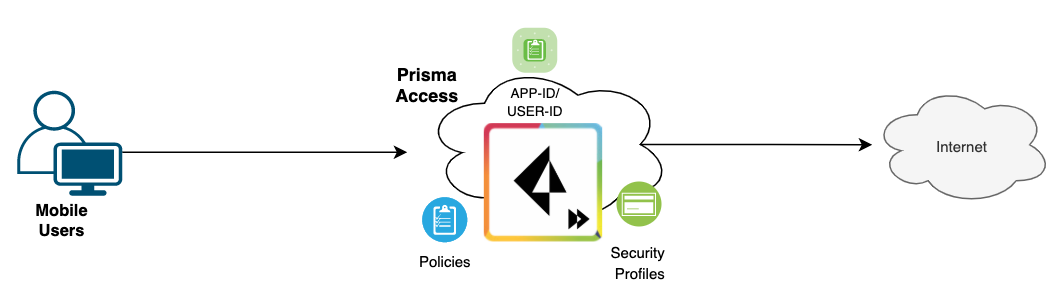
Traffic from the mobile endpoint to the Internet traverses the VPN tunnel (SSL or IPSec) to the Mobile Users Security Processing Node (MU-SPN) and then directly to the Internet. The node automatically translates the source IP address of the traffic to its external IP address, ensuring all return traffic flows through the node.
In a nutshell, you will still use the Global Protect application to connect to the VPN but behind the scenes, the VPN terminates on the Prisma Access node instead of your own on-premise firewall.
What Problem Does Mobile Users Solve?
Let's say you're part of a global company with branches spread across the world, and your employees need to connect to Global Protect. Imagine your Data Center or HQ is in the UK. It wouldn't make much sense for a user in the USA to route their traffic all the way back to the UK, right? To address this, you might consider deploying physical firewalls in the USA, allowing users there to connect to a local gateway. But wait, what about your users in Asia?
This is where it gets tricky. You could end up managing multiple firewalls across different regions. More importantly, you need to ensure that you're applying consistent security policies, regardless of where your users are located. This is a significant challenge in terms of management and consistency.
With Prisma Access Mobile Users, the process becomes much more easier. When you set Prisma Access initially, one of the key steps involves specifying your preferred Prisma Access Locations. Palo Alto deploys firewalls in these specified locations on your behalf.

So, when a user connects to the VPN, they're automatically routed to the nearest firewall. This means a user in the USA would connect to a firewall in the USA, and similarly, a user in Asia would connect to a firewall in Asia. The best part? All these firewalls and the associated infrastructure are fully managed by Palo Alto. This approach not only simplifies the geographical challenges but also takes a huge load off your shoulders. You no longer need to worry about managing the physical aspects of these firewalls spread across different regions. Palo Alto Networks ensures that they're all up and running, secure, and updated.
How Do I Manage the Configuration?
Now, you might be wondering, "If Palo Alto Networks manages the infrastructure, what's left for me to do?" Well, as a customer, you still play a crucial role in managing the configuration. You handle this through Panorama or Strata Cloud Manager.
Here's how it works, you'll still set up Portals and Gateways, but instead of pointing them to a physical location, you'll direct them to a cloud endpoint. This typically looks like mycompany.gpcloudservice.com. So, while the heavy lifting of maintaining the infrastructure is off your plate, the responsibility of creating and managing Security Policies, Objects, and Security Profiles remains yours.
Additionally, Gateway/Portal-specific configurations are also managed by you. This includes aspects like split-tunneling and IP Pools. Essentially, you're managing the same elements as you would in a traditional setup, but the context is now shifted to a cloud-based environment.
Things to Consider
Before wrapping up, there are a few important points to keep in mind regarding Prisma Access.
- Limited Direct Access for Troubleshooting - Since you don't manage the physical firewalls, direct access for tasks like taking packet captures isn't possible. If you need to troubleshoot, you'll have to raise a support ticket with Palo Alto, which can add some time to your problem-solving process.
- Dependence on Prisma Access Uptime - Remember, your VPN access is reliant on Prisma Access's performance. While it's designed to be highly available, no service can promise 100% uptime. There have been instances, like the issue with the
gpcloudservice.comdomain, which led to VPN outages for several customers. - Cost Considerations - Lastly, weigh the costs. Prisma Access might offer a more streamlined and efficient management of your network security, but it's crucial to ensure it aligns with your company's budget and cost-benefit analysis. The convenience and management ease need to justify the investment.
Closing Thoughts
In conclusion, Prisma Access Mobile Users simplifies network security for global companies, offering the convenience of cloud-managed infrastructure by Palo Alto Networks, while still providing you complete control over your security configurations. It's a blend of efficiency and control, ensuring security without the complexity of managing physical firewalls across multiple locations.






