What are VPN filters?
VPN Filters consist of rules that determine whether to allow or reject tunnelled data packets that come through the ASA, based on criteria such as source address, destination address, and protocol. You can configure ACLs in order to permit or deny various types of traffic.
Why do we need VPN filters?
In a typical scenario, you will have multiple L2L VPNs terminating on the ASA. Some of them you don't trust fully, you can filter traffic traversing via these tunnels using two methods.
- Using ACLs - You can apply inbound ACLs on the outside interface to filter incoming traffic and apply outbound ACLs on the inside interface to filter outgoing traffic.
- Using VPN filters - You can use a special kind of ACL applied to the tunnel instead of interfaces. VPN filter is even more useful when you have sysopt connection configured on the ASA.
The sysopt connection permit-vpn command allows all the traffic that enters the security appliance through a VPN tunnel to bypass interface access lists. Group policy access lists still apply to the traffic.
A vpn-filter is applied to post-decrypted traffic after it exits a tunnel and to pre-encrypted traffic before it enters a tunnel.
When a vpn-filter is applied to a group-policy that governs an L2L VPN connection, the ACL should be configured with the remote network in the src_ip position of the ACL and the local network in the dest_ip position of the ACL. I know it's weird.
This blog post assumes that you have a basic understanding of site-to-site VPNs. If you are not familiar, please check out my other post here.

Example
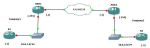
Let's assume that we have a site-to-site VPN between our ASA and a supplier Firewall. With the vpn-filter, what we can do is, restrict the traffic traversing the VPN tunnel.

Traffic restrictions
- Our local subnet (10.10.10.0/24 ) can only access 10.10.20.200 on port 443
- Supplier subnet (10.10.20.0/24) can only access 10.10.10.101 on port 22.
- Deny everything else.
Create objects and NAT
object-group network LOCAL
network-object 10.10.10.0 255.255.255.0
object-group network SUPPLIER
network-object 10.10.20.0 255.255.255.0
nat (inside,outside) 1 source static LOCAL LOCAL destination static SUPPLIER SUPPLIER no-proxy-arp route-lookupIf you need to learn more about Cisco ASA NAT, please check out my post here

Define interesting traffic
Define the interesting traffic which will trigger the creation of the VPN tunnel.
access-list VPN-TO-SUPPLIER extended permit ip object LOCAL object SUPPLIER
Create tunnel-group and crypto map entry
tunnel-group 2.2.2.2 type ipsec-l2l
tunnel-group 2.2.2.2 ipsec-attributes
ikev1 pre-shared-key 12345678
crypto map VPN 10 match address VPN-TO-SUPPLIER
crypto map VPN 10 set pfs group2
crypto map VPN 10 set peer 2.2.2.2
crypto map VPN 10 set ikev1 transform-set AES-SHA
crypto map VPN 10 set security-association lifetime seconds 3600Configure group policy and vpn-filter
access-list VPN-FILTER extended permit tcp host 10.10.20.200 eq 443 object LOCAL
access-list VPN-FILTER extended permit tcp object SUPPLIER host 10.10.10.101 eq 22
access-list VPN-FILTER extended deny ip any any
group-policy 2.2.2.2 internal
group-policy 2.2.2.2 attributes
vpn-filter value VPN-FILTER
tunnel-group 2.2.2.2 general-attributes
default-group-policy 2.2.2.2Important things to consider.
- All interesting traffic will trigger the tunnel, whether it is allowed or not on the vpn-filter
- if you deny something by changing vpn-filter ACL while a tunnel is up - it is in effect immediately
- if you permit something by changing vpn-filter ACL while a tunnel is up - you MUST rebuild the tunnel
Reference