What is it?
AWS Network Firewall is a managed firewall service for our VPC. We can use Network Firewall to filter traffic at the perimeter of our VPC. Network Firewall includes filtering traffic going to and coming from IGW, NAT Gateway, VPN and Direct Connect.
Network Firewall components
- Firewall
- Firewall Policy
- Rule Group
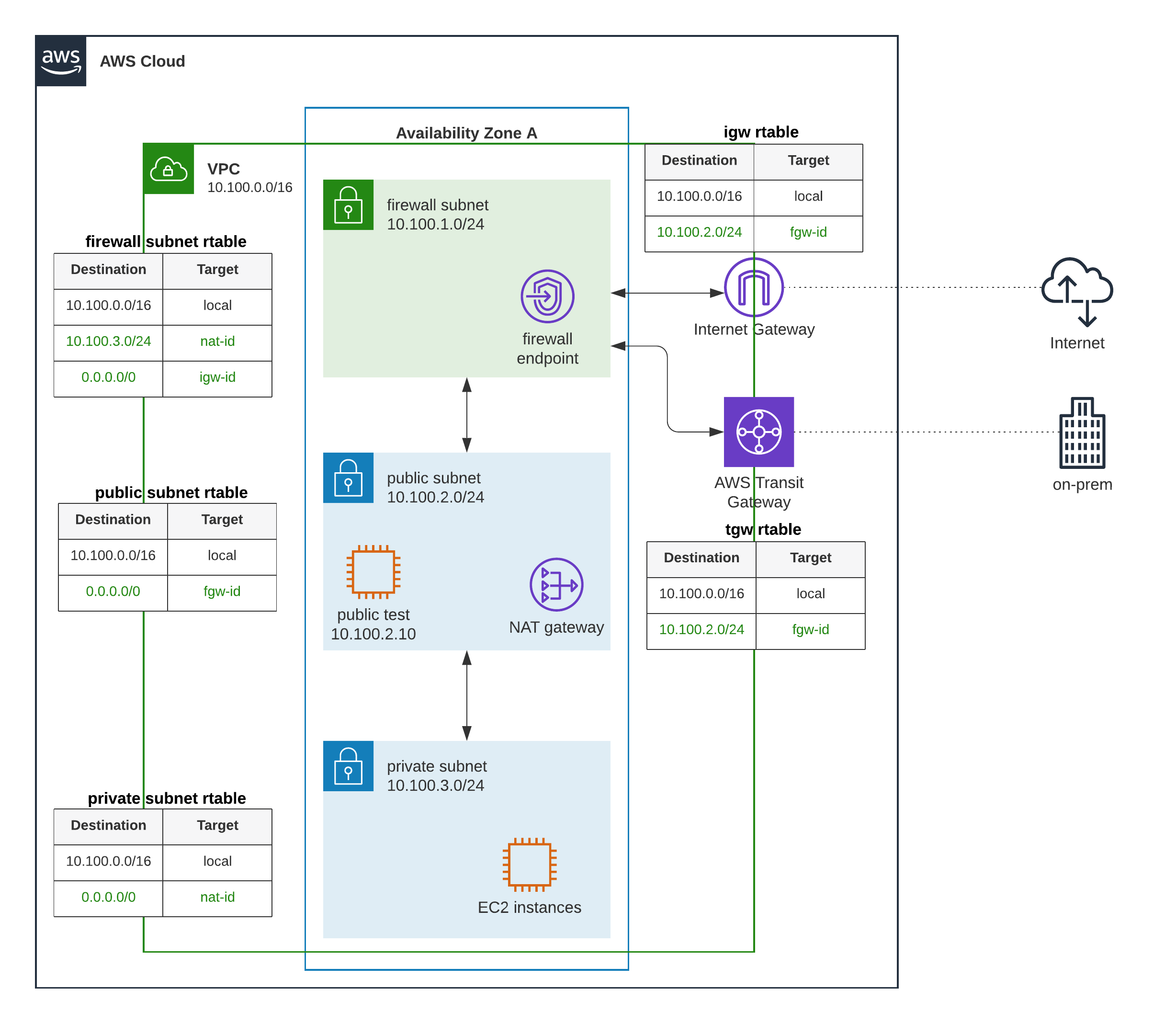
Diagram
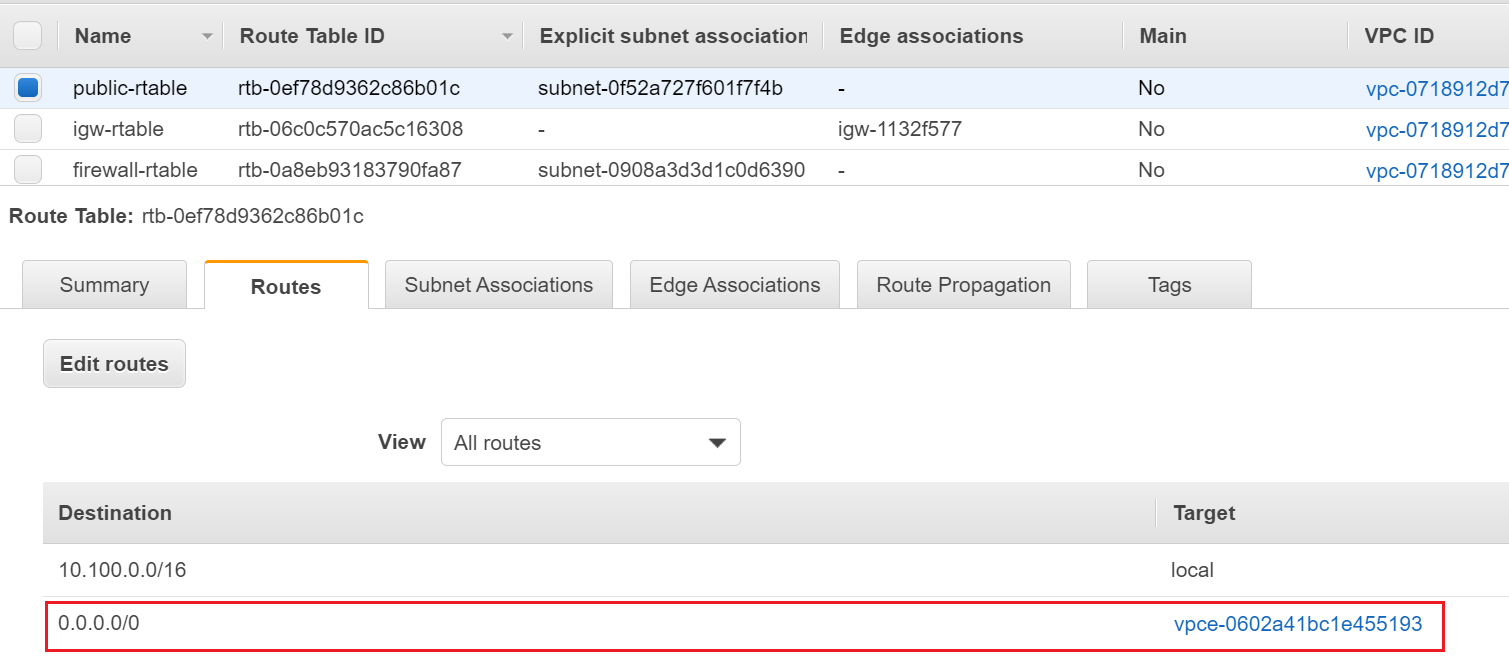
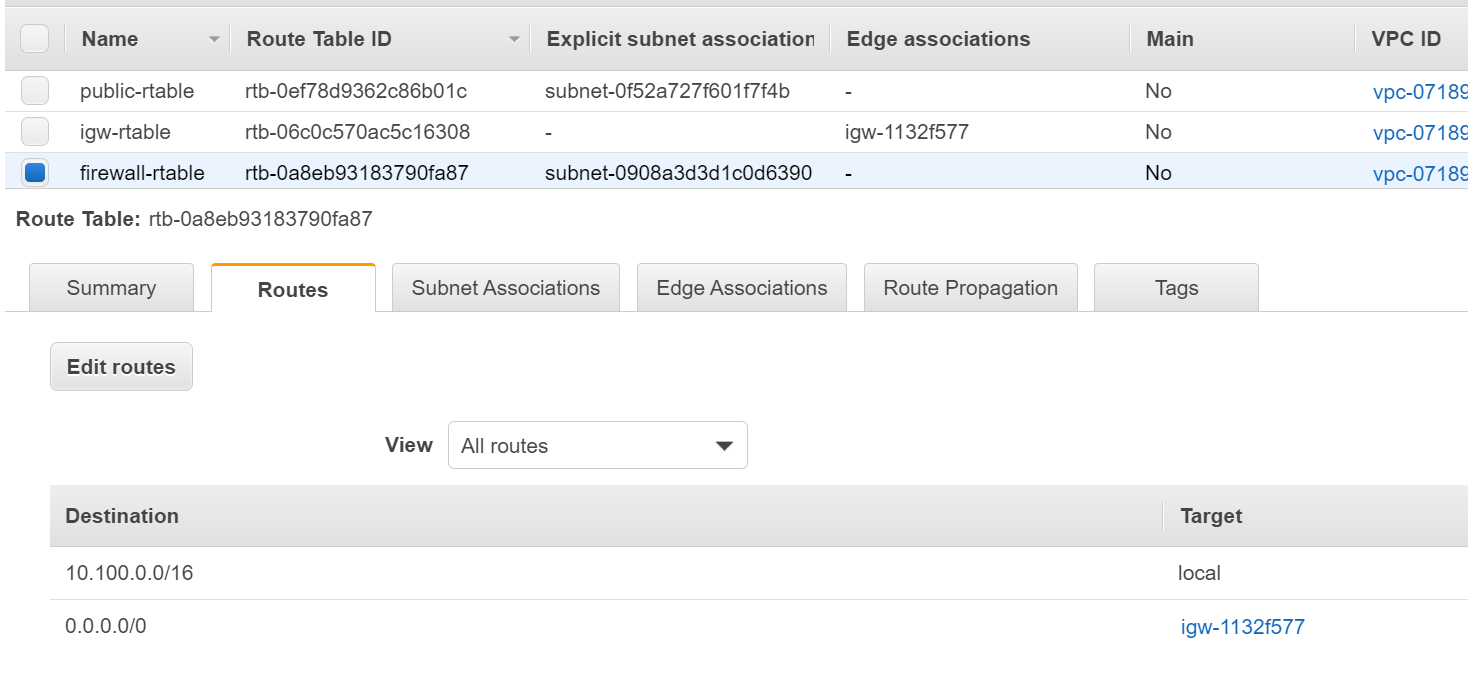
Route Table Configuration
- Public subnet route table routes traffic destined for 10.100.0.0/16 to the local address. Routes traffic destined for 0.0.0.0/0 (ANY) to the Firewall subnet. (figure-1)
- Firewall subnet route table routes traffic destined for 10.100.0.0/16 to the local address. Routes traffic destined for 0.0.0.0/0 (ANY) to the Internet Gateway (IGW) (figure-2)
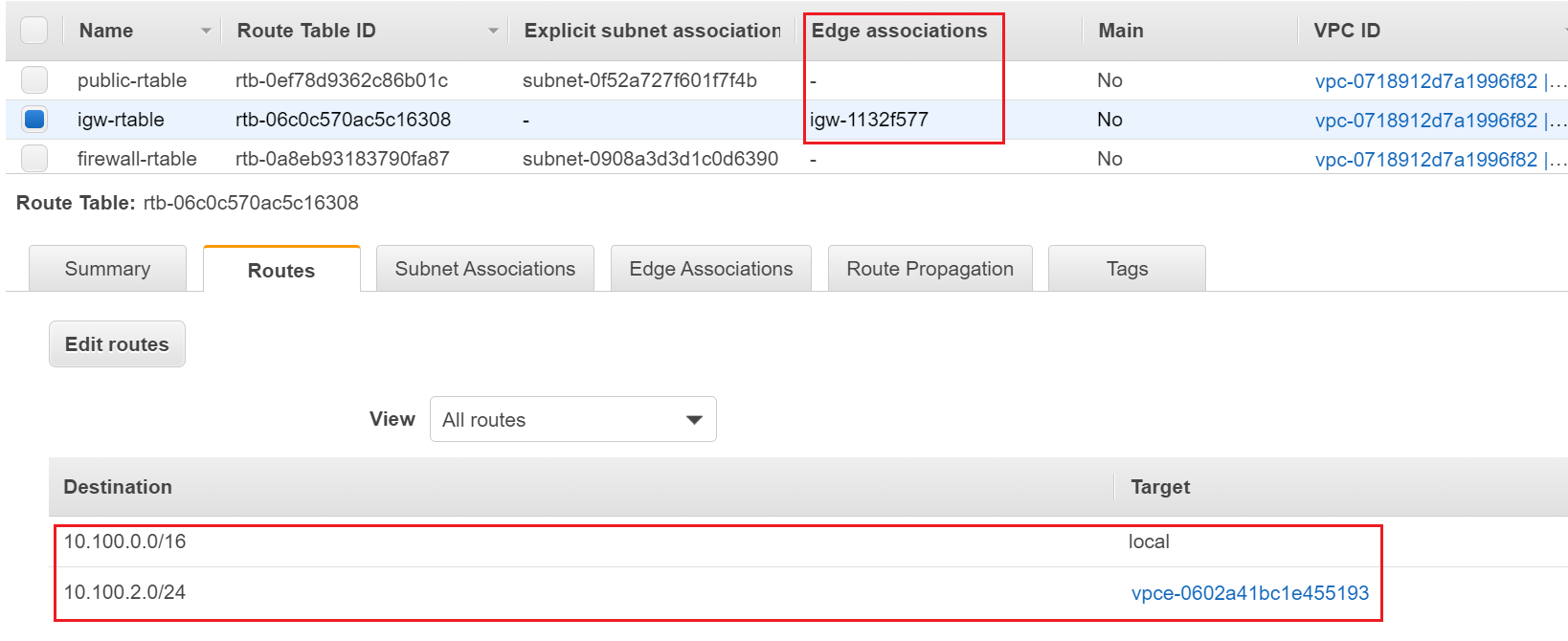
- IGW route table routes traffic destined for 10.100.0.0/16 to the local address. Routes traffic destined for 10.100.2.0/24 to the Firewall subnet. (figure-3)
- TGW route table routes traffic destined for 10.100.0.0/16 to the local address. Routes traffic destined for 10.100.2.0/24 to the Firewall subnet.
- Private subnet route table routes traffic destined for 10.100.0.0/16 to the local address. Routes traffic destined for 0.0.0.0/0 (ANY) to the Firewall subnet.
In our example, we will only focus on the test-machine located in public subnet. Private subnet, NAT gateway and TGW are not covered in this example.
Let's configure the Route Tables.
Agenda
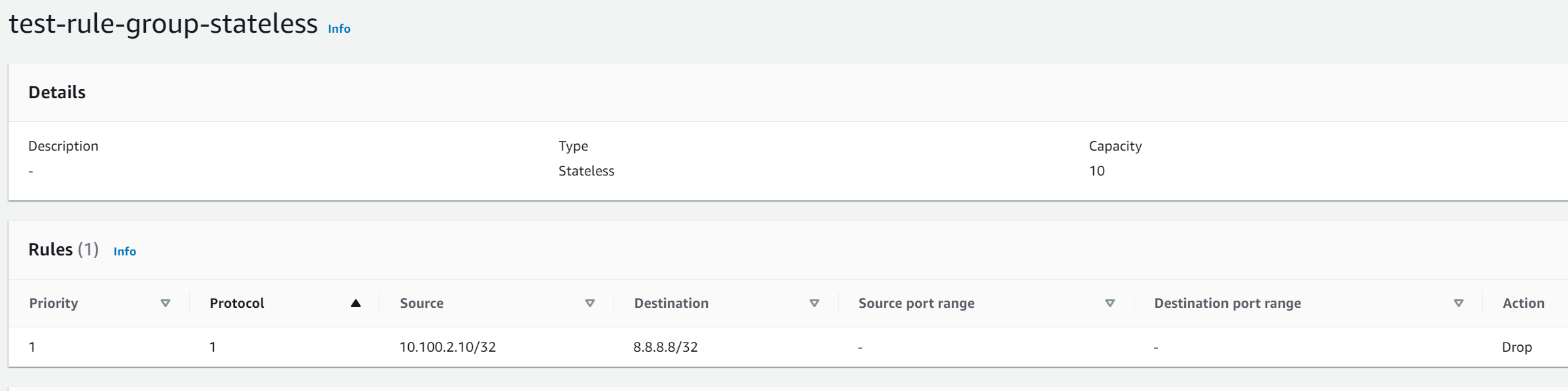
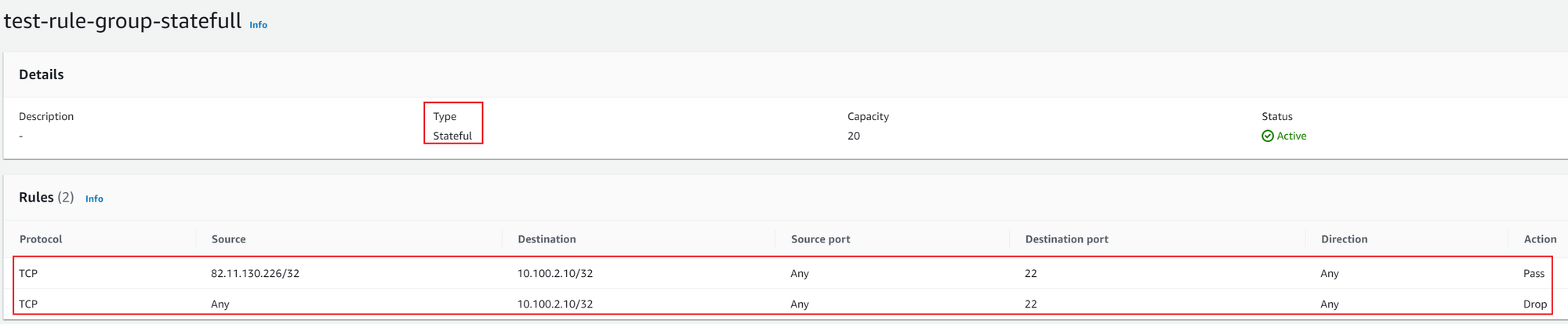
- Permit SSH access to 10.100.2.10 (test machine in the public subnet) only from 82.11.130.226
- Block ICMP from 10.100.2.10 to 8.8.8.8
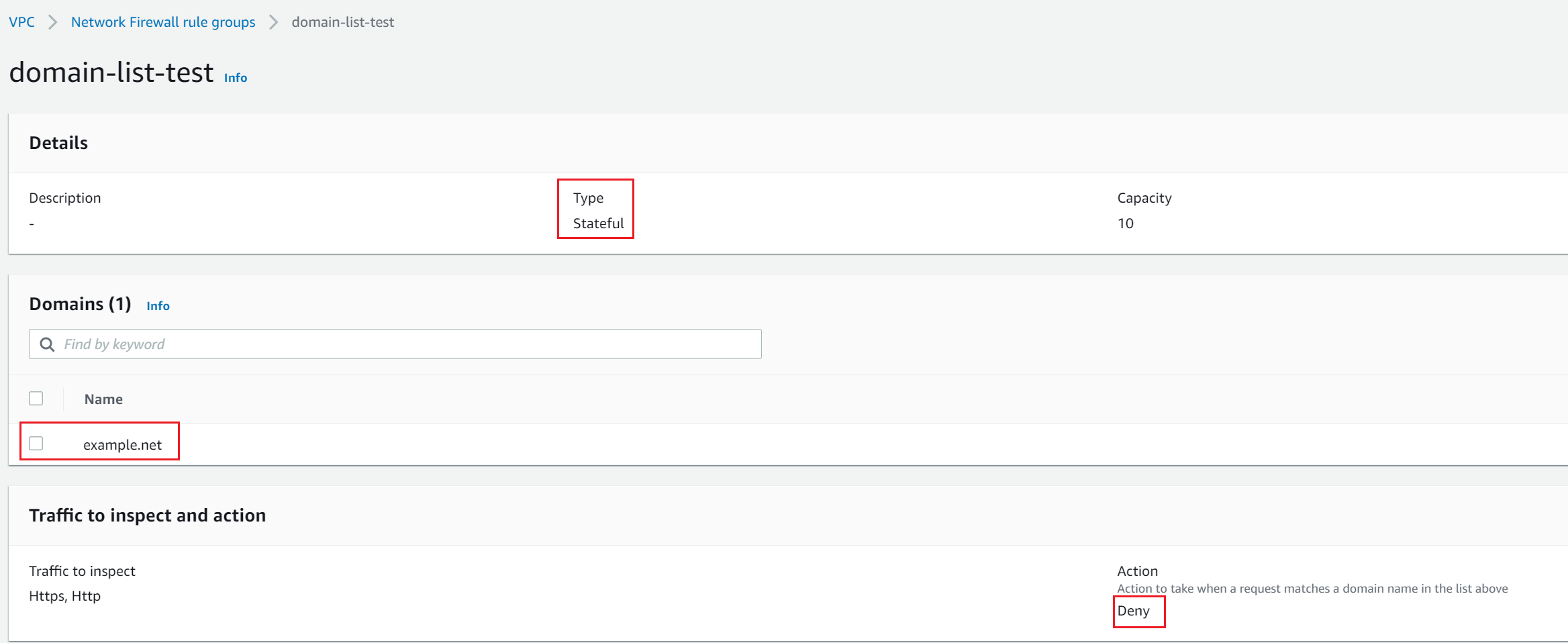
- Block access to example.net
- Permit everything else
Setup AWS Network Firewall
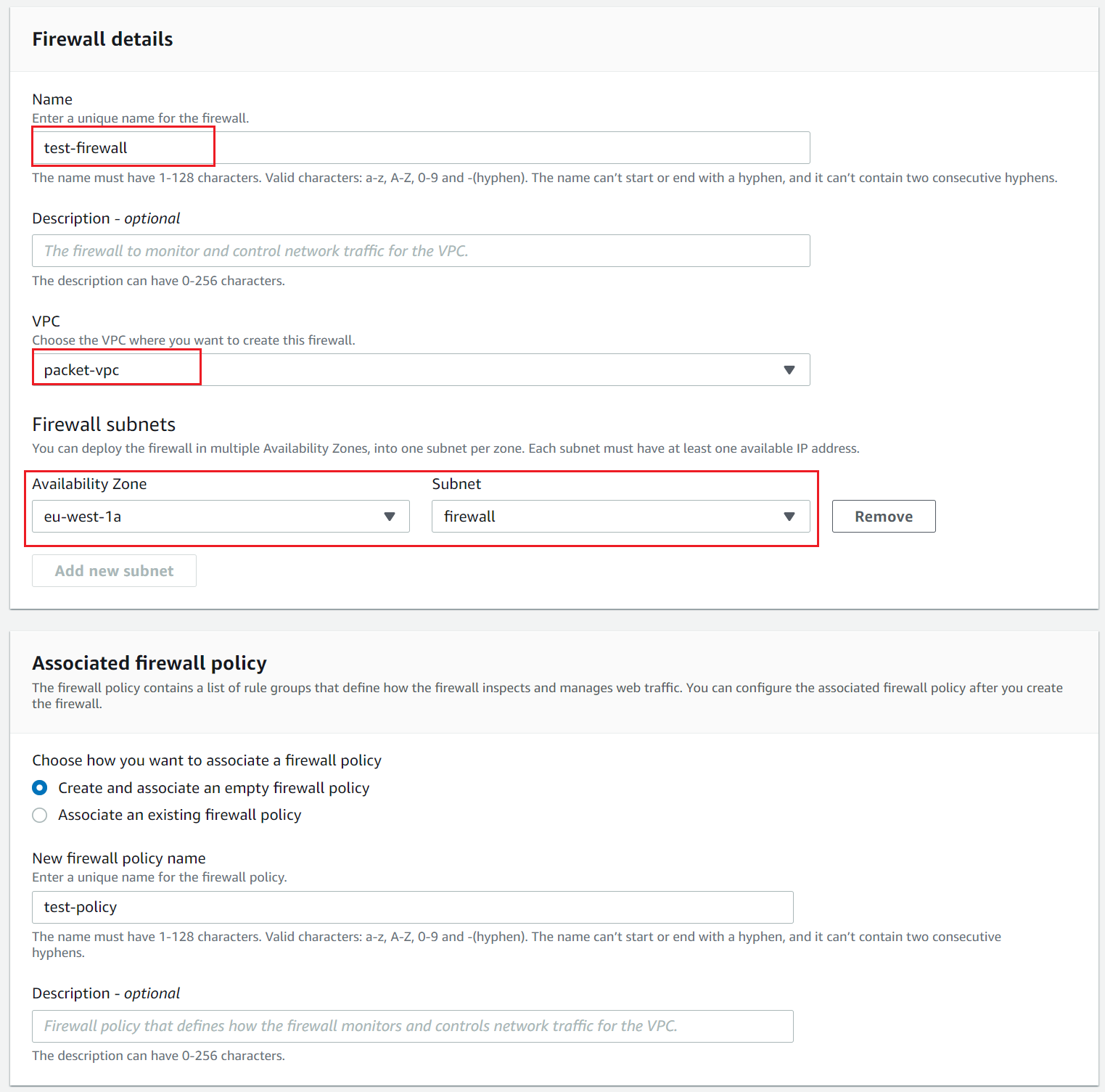
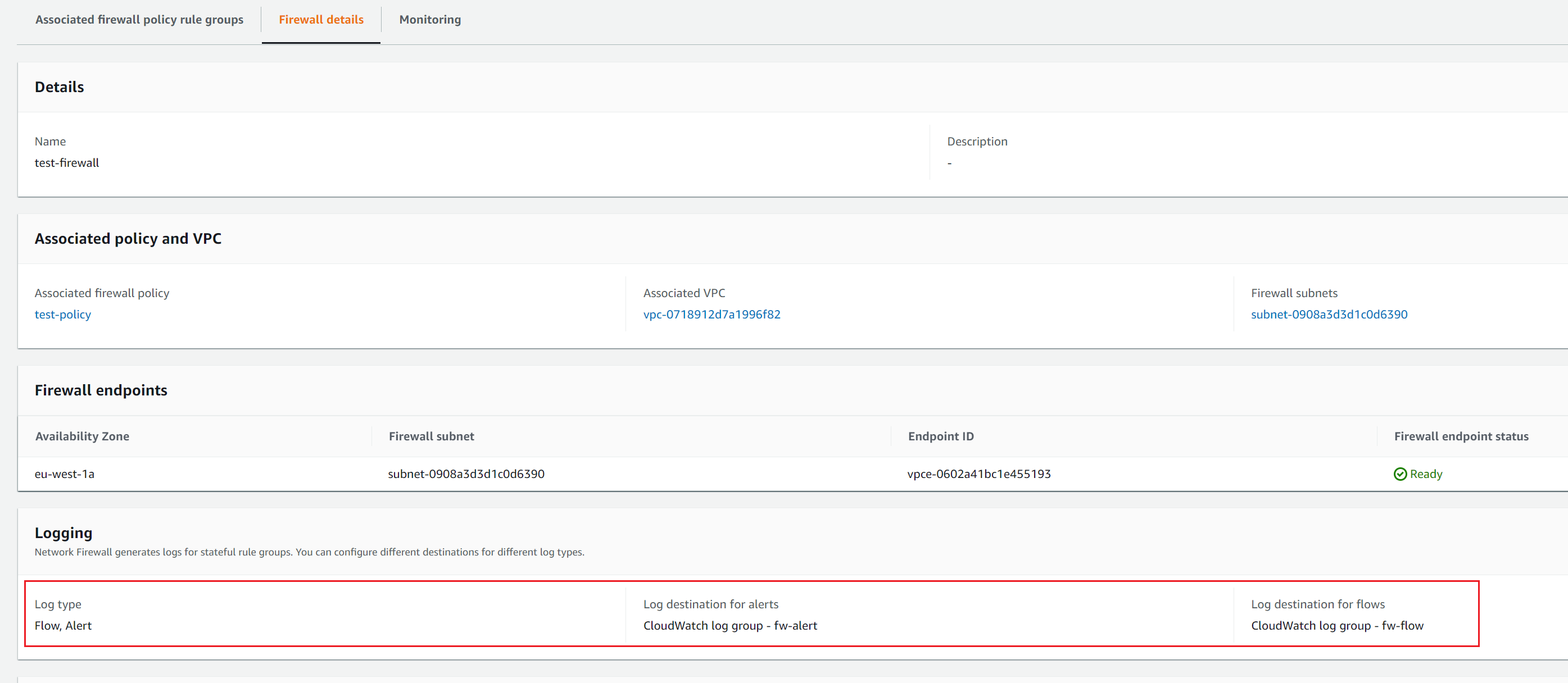
Firewall
Firewall connects a firewall policy, which defines network traffic monitoring and filtering behaviour, to the VPC that we want to protect.
Let's create a Firewall.
Firewall Policies
An AWS Network Firewall firewall policy defines the monitoring and protection behaviour for a firewall. The details of the behaviour are defined in the rule groups that add to the policy.
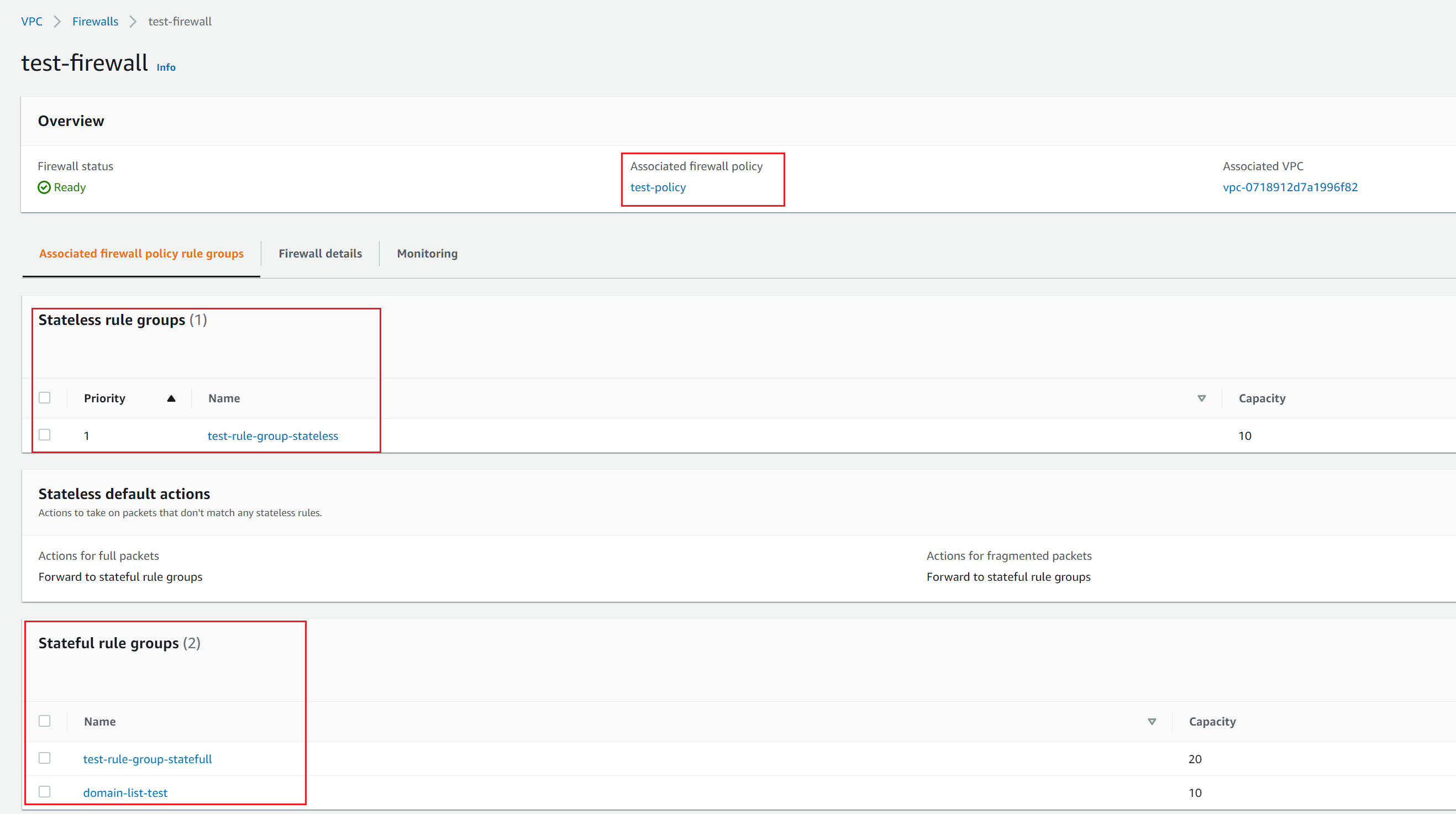
I created a policy called test-policy and associated with the Firewall we created in the previous step. The next step is to add some Rule Groups into it.
To create a Firewall Policy:
- In the navigation pane, under Network Firewall, choose Firewall policies.
- Choose Create firewall policy
Rule Groups
A rule group is a reusable set of criteria for inspecting and handling network traffic. We can add one or more rule groups to a firewall policy as part of policy configuration.
- Stateless rule group - Network Firewall stateless rules engine examines each packet in isolation. It doesn't consider context such as traffic direction or traffic flow.
- Stateful rule group - Stateful rules engine examines the full state of active traffic. It does consider the complete context of traffic and data packets.
- Domain list rule group - We can create allow/deny lists with domain names that the stateful rules engine looks for in a packet.
I have also set thestateless default actiontoforward to stateful rule groupso, any packet doesn't match the stateless rule group is sent out to the stateful rule group.
Verification
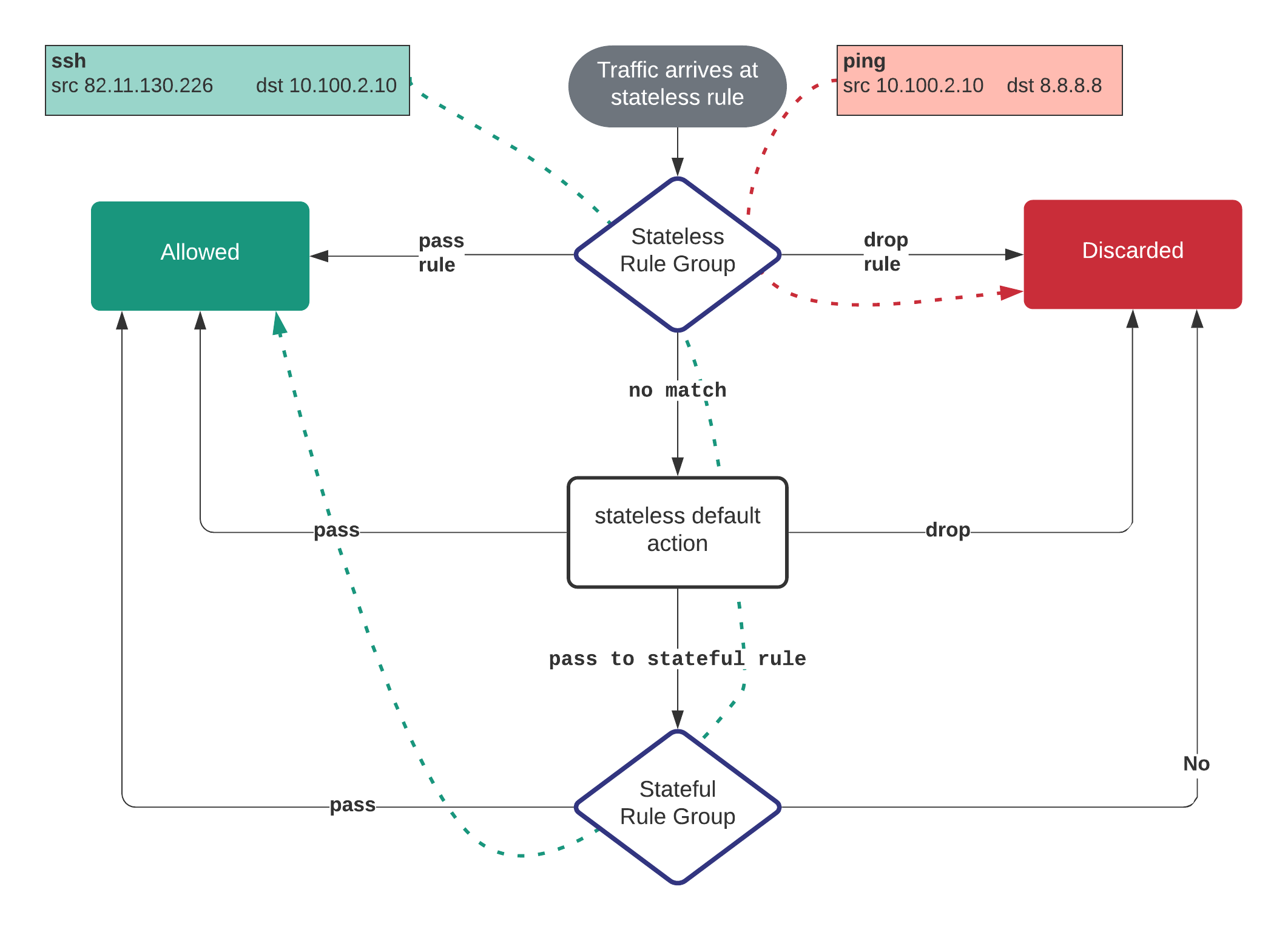
As you can see below pinging 8.8.8.8 and browsing example.net are getting blocked.
ubuntu@ip-10-100-2-10:~$ ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
^C
--- 8.8.8.8 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2028ms
ubuntu@ip-10-100-2-10:~$ ping 1.1.1.1
PING 1.1.1.1 (1.1.1.1) 56(84) bytes of data.
64 bytes from 1.1.1.1: icmp_seq=1 ttl=49 time=12.3 ms
64 bytes from 1.1.1.1: icmp_seq=2 ttl=49 time=14.6 ms
64 bytes from 1.1.1.1: icmp_seq=3 ttl=49 time=8.62 ms
^C
--- 1.1.1.1 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 8.621/11.856/14.649/2.483 msubuntu@ip-10-100-2-10:~$ links example.net
Rquest sent <<< The page doesn't loadLogging and Monitoring
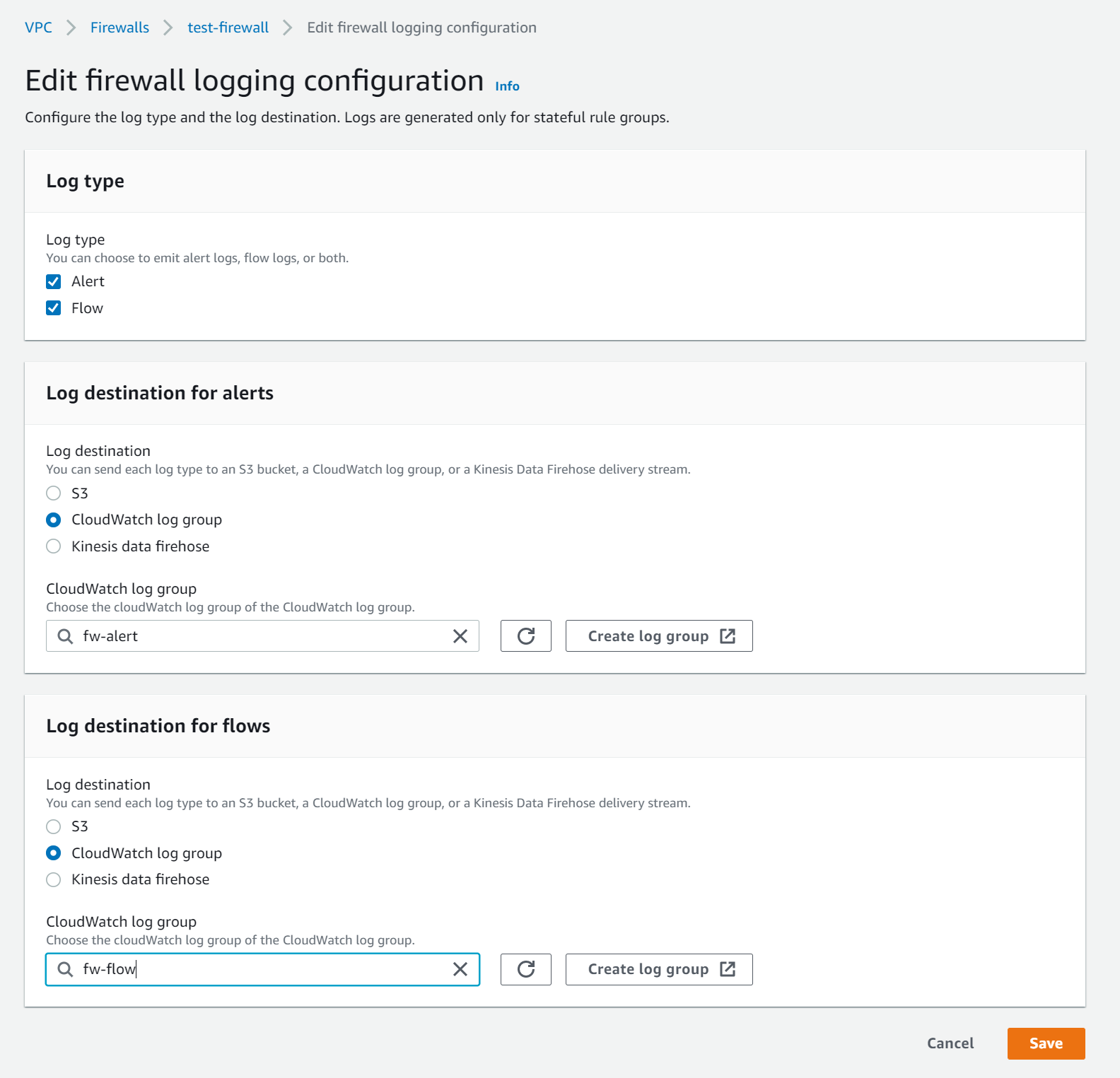
There are multiple ways where you can store and view the logs generated by the Networks Firewall. I will show you how to use CloudWatch in this example.
To send logs to CloudWatch:
- Create a CloudWatch Logs log group.
- Provide the log group name to the Network Firewall
- AWS Network Firewall now delivers logs to the CloudWatch log group in log streams.
- Each log stream contains an hour of log records.
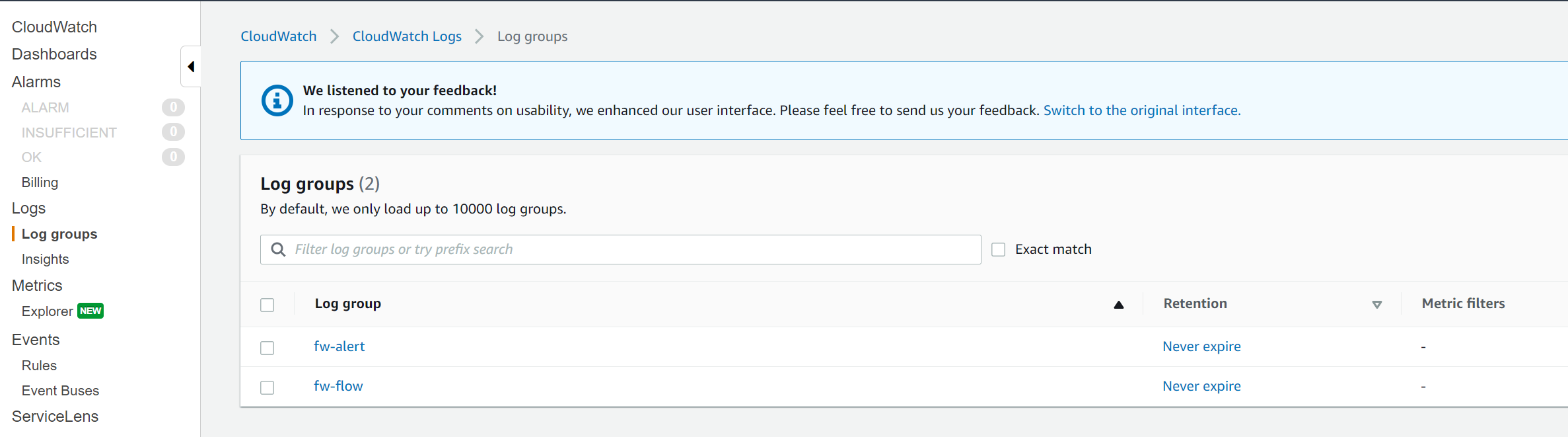
As you can see below that the traffic to both example.net and 8.8.8.8 are blocked and the logs are stored in CloudWatch.
{
"firewall_name": "test-firewall",
"availability_zone": "eu-west-1a",
"event_timestamp": "1605805211",
"event": {
"timestamp": "2020-11-19T17:00:11.487618+0000",
"flow_id": 276083259410786,
"event_type": "alert",
"src_ip": "10.100.2.10",
"src_port": 52086,
"dest_ip": "93.184.216.34",
"dest_port": 80,
"proto": "TCP",
"tx_id": 0,
"alert": {
"action": "blocked", <<<<<<
"signature_id": 2,
"rev": 1,
"signature": "matching HTTP denylisted FQDNs",
"category": "",
"severity": 1
},
"http": {
"hostname": "example.net", <<<<<<
"url": "/",
"http_user_agent": "Links (2.14; Linux 5.4.0-1029-aws x86_64; GNU C 7.3; text)",
"http_method": "GET",
"protocol": "HTTP/1.1",
"length": 0
},
"app_proto": "http"
}
}example.net blocked
{
"firewall_name": "test-firewall",
"availability_zone": "eu-west-1a",
"event_timestamp": "1605792702",
"event": {
"timestamp": "2020-11-19T13:31:42.770484+0000",
"flow_id": 175749856149940,
"event_type": "alert",
"src_ip": "10.100.2.10",
"dest_ip": "8.8.8.8", <<<<<<<<
"proto": "ICMP", <<<<<<<<
"icmp_type": 8,
"icmp_code": 0,
"alert": {
"action": "blocked",
"signature_id": 1,
"rev": 0,
"signature": "",
"category": "",
"severity": 3
}
}
}icmp blocked
Thanks for reading.
As always, your feedback and comments are more than welcome.